Carding 4 Carders
Professional
- Messages
- 2,724
- Reaction score
- 1,579
- Points
- 113
And what does WordPress and Chrome updates have to do with it, we'll find out now...
Specialists of the information security company Guardio Labs told about a new campaign that began in August, during which attackers began using Binance Smart Chain (BSC) smart contracts to place malicious code.
An interesting twist is the latest version of the campaign, which uses compromised WordPress sites to prompt unsuspecting visitors to update their browsers before accessing the sites. A fake update downloaded eventually leads to the deployment of information-stealing malware such as Amadey, Lumma, or RedLine.
The initial method of hosting code on Cloudflare Workers hosts was eliminated, but the attackers quickly switched to using the decentralized, anonymous, and public nature of the blockchain. As noted by security researchers, the campaign has become more difficult to detect and eliminate.
Not surprisingly, hackers attacked WordPress sites through malicious plugins, and also used publicly available vulnerabilities of popular plugins to hack sites, which makes it possible to completely capture infected sites.
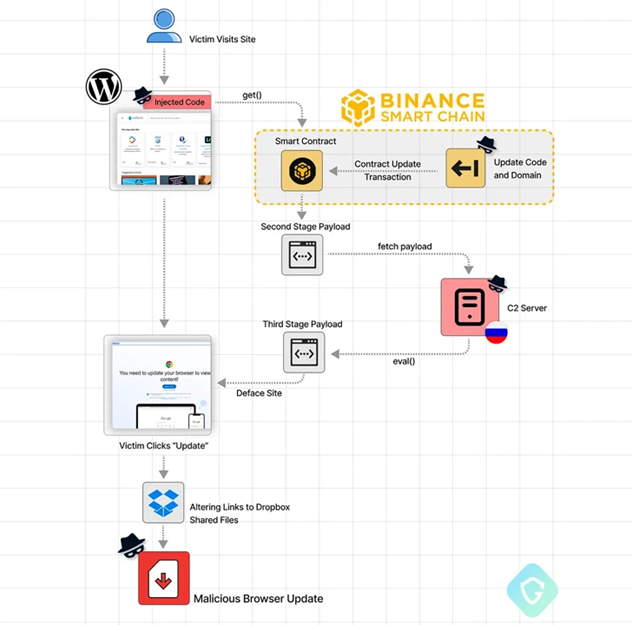
Chain of attacks
In the latest series of attacks, cybercriminals implemented obfuscated Javascript codes designed to create a smart contract with a blockchain address controlled by the attackers.
The goal is to get a script for the second stage that retrieves the payload of the third stage from the Command and Control server (C2). The extracted code then displays fake browser update notifications to the user. If the victim clicks the update button on the fake overlay, they will be redirected to download the malicious executable file from legitimate file services, including Dropbox.
Placing a bitcoin address and associated contract on a decentralized service gives fraudsters an advantage, as there is currently no way to interfere and interrupt the chain of attacks. It is recommended that users who rely onWordPress adhere to best cybersecurity practices, update their systems regularly, remove unwanted administrators, and set strong passwords.
Specialists of the information security company Guardio Labs told about a new campaign that began in August, during which attackers began using Binance Smart Chain (BSC) smart contracts to place malicious code.
An interesting twist is the latest version of the campaign, which uses compromised WordPress sites to prompt unsuspecting visitors to update their browsers before accessing the sites. A fake update downloaded eventually leads to the deployment of information-stealing malware such as Amadey, Lumma, or RedLine.
The initial method of hosting code on Cloudflare Workers hosts was eliminated, but the attackers quickly switched to using the decentralized, anonymous, and public nature of the blockchain. As noted by security researchers, the campaign has become more difficult to detect and eliminate.
Not surprisingly, hackers attacked WordPress sites through malicious plugins, and also used publicly available vulnerabilities of popular plugins to hack sites, which makes it possible to completely capture infected sites.

Chain of attacks
In the latest series of attacks, cybercriminals implemented obfuscated Javascript codes designed to create a smart contract with a blockchain address controlled by the attackers.
The goal is to get a script for the second stage that retrieves the payload of the third stage from the Command and Control server (C2). The extracted code then displays fake browser update notifications to the user. If the victim clicks the update button on the fake overlay, they will be redirected to download the malicious executable file from legitimate file services, including Dropbox.
Placing a bitcoin address and associated contract on a decentralized service gives fraudsters an advantage, as there is currently no way to interfere and interrupt the chain of attacks. It is recommended that users who rely onWordPress adhere to best cybersecurity practices, update their systems regularly, remove unwanted administrators, and set strong passwords.

