Tomcat
Professional
- Messages
- 2,687
- Reaction score
- 1,038
- Points
- 113
Good reading, dear readers of Habr.
I have recently read a number of articles, including on Habré, on digital fingerprints of browsers and surveillance of users on the Internet. For example, the article Anonymous identification of browsers and Traps on the Internet in Forbes magazine, section “technology” - “Big Data”.
Or maybe I don’t want to be taken into account! Only, I'm afraid, the irony is that this is also a fingerprint, and, moreover, apparently, the main reason for the appearance of fingerprints. IMHO, there is only one way. In relation to FireFox - if all the foxes in chorus and each one individually start yapping that they are ordinary standard foxes, and not torus, not chrome and not makos.
But, out of academic interest, to preserve the individuality of the foxes and in response to the latest machinations of wild capitalism, I want to propose the following cunning plan for the consideration of the respected Habracommunity.
I would like to make a reservation right away - I am not an expert in the field of network security or anonymity, I was not a member of anonymous groups, I was not convicted of anonymity, I swear by Thor, the age of the darknet has not been seen.
Windows 10 x64 and Firefox 62.0.3.
The fact that Windows sends telemetry and everything related to setting up Windows itself, as well as issues of antiviruses and firewalls, still does not fit into the article. As well as surfing the Internet at night, from under the table and from the refrigerator, through the Tor browser, through VirtualBox with Tails, through Quad VPN and also Whonix (above).
I suggest, for the purity of the experiment, to create a new FireFox profile
In order to see how the proposed upgrade affects the fox’s performance
I suggest installing this: Page Speed Monitor

(this is the page loading time). If you click on it, there is detailed information.

On the following points. There, in two cases, it is suggested to clear the history and profile cookies. Be careful if you are logged in to Habré!
1. Cut out banal surveillance technology. Redirect
Yandex, however, wrote that it’s the other way around, for the purposes of encryption and anonymity, it seems like it’s really proof, but so as not to stumble over any bullshit at every step:
In Clean Links settings
— IMHO it’s better to uncheck “highlight cleared links” and you can temporarily check “show messages” to observe the effect.
— You can enable the option “make non-clickable links clickable”
— Replace the line “Skip Links...” with\/ServiceLogin|imgres\?|searchbyimage\?|watch%3Fv|auth\?client_id|signup|bing\.com\/widget|oauth|openid\.ns|\.mcstatic\.com|sVidLoc|[Ll]ogout|submit\?url=|magnet:|(?:google|yandex)\.(?:com|ru)\/\w*captcha\w*[\/?]|(?:google|yandex)\.(?:com|ru)\/.+\.(?:google|yandex)
— Add to exceptions — comma, then google.com, google.ru, yandex.ru, ru.wikipedia.org, en.wikipedia.org, passport.yandex.ru
It is necessary to remember that it may still not work on some sites, then there will be no redirect to the right place, but still this is part of good protection, incl. from phishing, you can turn off problematic sites or add them to the white list
2. Cut out traditional surveillance technology. Cookies
2.1. You must install the First Party Isolation add-on .
A button will appear
 . Do not click it until you are on the test site. Before you return here, it should be restored to its original condition.
. Do not click it until you are on the test site. Before you return here, it should be restored to its original condition.
True, the author here broke the system. When pressed it is pale (on), but when pressed it is not (off).
2.2. Go to the Cookie Tester website.
Set Cookie.

“Press” the installed button. And click on “Refresh” on the site.

Here you can read Improving privacy in Firefox .
A la sandbox. When the button is pressed, the insulation is turned on, when pressed it turns off (and for some reason it is indeed turned off by default).
Two states “isolated” and “not isolated”. At the same time, “not isolated” is the same for all sites, but “isolated” is individual for each site and one site does not have access to another.
The same is true for one site - if you press the button here now, Habr will not see the cookie. But it will calculate the second input. Therefore, he will be fired without severance pay.
But, on the other hand, cookies will no longer be transmitted across different sites; when the button is turned on, sites will no longer see other people’s cookies, so surveillance will be difficult + it will be much more difficult to steal them. Although Evercookies and other nanotechnologies are not affected, I found out.
Suggestion for use:
Leave the button enabled. As far as I’ve read, there may be a case when problems arise with authorization (sometimes the site forwards to another, but its own, that is, “legally”). Then you will need to disable it on this site (if you log in, turn it on, you will be logged out). But I haven’t come across such sites yet.
3. Cut out innovative surveillance technology. Evercookies
3.1. You need to install the Multi-Account Containers
3.2 add-on. Get into trouble (not a single Fox will get hurt)
Good description of Evercookie on Habré .
Cookies are cross-domain, but some of them will no longer help - the previous completed step will not. And with HTML5 canvas, etc. The fox cannot do anything (or rather, it can, but in a very sophisticated way and it would be better not to - see below). By the way, CCleaner completely demolishes them, but along with history, cookies and other useful things.
Website with Evercookie. You need to press the top button first, then the bottom button.

Snatched:

On the FireFox panel you need to click:
 . Skip any welcome messages (the “Next” button) and wait.
. Skip any welcome messages (the “Next” button) and wait.
Then, onthe ruins of the chapel , select the tab:
Generally speaking, any container, they are the same, the names are different.
Ever-ik fail:

Suggestion for use:
Alternatively, isolate all social networks, payments, etc. from everything else by assigning them a default container. It’s just inconvenient that all links clicked inside the container open in the same container.
By the way, there is one more benefit from this technology, although this is obvious, but still.
If you distribute everything into containers both in mail (if FireFox is the default browser or the web mail form is open) and on the Internet, you can check whether you got where you wanted, if something important:
There is another technology, on top of this temporary-containers, focused on tabs, not domains (although you can add a dependency, isolate a domain in one container, or even subdomains).
And when closed, it can erase the entire history. And now I would remove Evercookie from the canvas, whether they are there or not (I checked, sir). But IMHO it’s still a bit damp. FierFox tabs jump around, sometimes close, etc. and so on. And it slows down.
Evercookie, on the site, it’s better to click to delete it
until the next time.
4. Clean up the previously cut
The previously mentioned addon “Cookie-AutoDelete” did not justify itself.
Cause
“Cookies-AutoDelete” turned out to be, although quite implicitly, incompatible with the first part isolation level technology.
As everyone understands, isolation is achieved through isolation (that’s not what you’re talking about), incl. and cookies, in connection with which FireFox sets the appropriate “marks” in the cookies.sqlite database. And Cookies-AutoDelete beats it with its “CookiesAutoDelete” label (tested using SQLiteStudio)
To replace “Cookies-AutoDelete” I can suggest Cookiebro
- It is compatible
- Although in English, it is easy to configure
There is a Cookies editor
For carefully stored favorite cookies, there are security settings
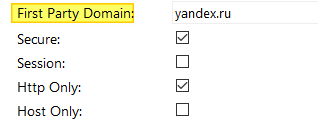
Highlighted - this implies proof of compatibility
Secure - transmit only via https
Http Only - transmit only via http. This doesn't mean https! see above. This means not giving access to Java and other potentially dangerous junk, but transmitting it only the old fashioned way, in the http
Host Only header - not giving subdomains access to the goodies (in the example, only yandex.ru would have access, but Yandex.Music and etc. - no)
The downside is that in order for your favorite cookies to be preserved, you need to add the site to the white list, and the number of cookies for the site can be over 9000. This is probably also somehow avoided, but I haven’t looked.
Another minus is that wherever you are registered, you need to add it to the white list (at first, Habr logged you out every 5 minutes, because the cookie was deleted with this frequency, until this pandemonium got tired of it).
Reliably cuts out the E-tag along with the updated one from step 5 (if you enable the “Limit tab history” option added in step 5)
Suggestion for use:
Set up all the previous ones and this item, and it seems like you can forget about cookies and so on, this whole design You have to remove them yourself. And you don’t need to train every site you come across. Plus upgrade CCleaner according to the instructions in the article about “forensics” and configure it so that it deletes everything else and compresses the database.
5. Cut out ETag and other half-cut nanotechnologies
Addon Chameleon. WebExtension from Random Agent Spoofe.
The text has been changed due to the update of the proposed addon.
I would suggest the following settings:
Options tab
- Set Enable script injection - otherwise half of the functionality will not work.
— Set protect window.name — BUT! the enabled option breaks the “I’m not a robot” captcha, either don’t turn it on or remember and turn it off in such cases
- Enable tracking protection - probably not necessary, it’s better to install uBlock later and hide it (see below). Otherwise, “adblocked” sites will start to snap back.
- Disable WebSockets - IMHO not necessary, then half of the services do not work.
— Set Limit tab history — Limits sites’ access to history (presumably up to 2 visits)
— Spoof Client Rects — can be omitted, the next add-on can do this too
— Screen size spoofing — I suggest selecting “Custom” and setting the resolution manually (see. below “average temperature for a fox”)
- Enable 1st party isolation - this is the same as that set in point 1. button.
— Resist fingerprinting , IMHO — not worth it (see fingerprints below). FireFox, instead of pretending to be a rag, for some reason begins to pretend to be a Tor browser.

And, as you know, very few people like Tor + half of the other functionality of the add-on will stop working + the window when starting the browser stops expanding to full screen, it suits someone, no less.
Headers tab
- Set to Disable Authorization - The browser allows you to send hidden authentication data to third-party sites; enabling this option stops this mess. But there may be difficulties with authorization on some sites.
— Enable DNT (Do Not Track) — Enable message sending (do not track). Sites, of course, either ignore it or pretend not to. IMHO - set it (according to various sources - it is sometimes recommended, sometimes not, depending on the number of browsers that have passed the test and collected statistics on this parameter, since the choice to set it or not is from the point of view of “not standing out”, not functionality)
- Set Spoof If-None-Match - Write a random number to ETags
- Spoof X-Forwarded-For- If you set, for example, the IP of the Netherlands, it will add it to the HTTP header and the site will decide that this is the IP of the computer, based on what poorly configured proxies add to the header. Those. It’s like the IP of the computer is the IP of the proxy, and the IP in the header is the other way around and the IP from the header will be included in the site log. But here, in my opinion, it’s better not to, the IP provider will be banned as a left-wing proxy. Another question is that when using a proxy, this may be relevant, so that if it’s crappy, it won’t show the real IP in the header.
— Disable Referer — IMHO not necessary. Disables referrers, you will not be able, for example, to return when turning pages on a site to the previous page
- Set Spoof Source Referer (puts a referrer to it when you go to the site)
- Set Upgrade Insecure Requests - automatically request the site via https if it works in in both modes (http and https)
- Referer X Origin Policy - transfer the base domain in the referrer. "Match base domain" is recommended (but not sure it won't break anything if for some reason inside the domain it matters which subdomain you changed from). Example: for example.com, news.example.com, blog.example.com - the referrer example.com will be transmitted
- Rferer Trimming Policy - trim the transmitted referr. "Scheme, host, port, path" is recommended. Example: for the link example.com :8080/page?privacy=false&trackingid=XYZ, it will be transmitted - example.com :8080/page
- Set Spoof Accept-Encoding - will replace HTTP_ACCEPT_ENCODING with gzip, deflate. It seems to be no problem
- Spoof Accept-Language - language, "eu-US" is recommended, but sites may try to display content in this language.
I suggest choosing the average fox temperature as follows: switch user agents within versions of the source OS and within versions of FireFox (why - see next article). I think a couple of versions of fox 61 and 62 and Windows 7 with Windows 10 , screen size 1366x768 or “any” will do , you can get more specific here StatCounter .
It should be taken into account that changing the user agent with an indezhkt - all sorts of addons, such as “Google Translate”, hand over a real user agent, because packages slip past the chameleon.
Costs of camouflage
— If you impersonate a mobile phone, the consequences, I think, are known to everyone
— Impersonating Google Chrome is fraught, Google will accept you as one of its own (and it will even stop adding redirects), but at the same time it will begin to secretly feed the disguised fox something inedible for it, why would it will start to lag, and on YouTube, who knows what happens, everything will be lost except for the video that was opened
- Client-oriented M$ will persistently sell installation packages for the OS that is set in the user agent, even if it is KolibriOS
- Attempts to replace fonts are a surefire way to be left without Google Doc
- Attempts to cast an IP address through headers permanently lead to an awkward situation: Google is not allowed, in Yandex the content is cut out with primordial Russian hospitality, and in DakDak-Go and StartPage it is not interesting, you can get there without such tricks
6. Saw out the remaining spherical Schrödinger cats in Faraday cages
Install CanvasBlocker . Return to the site with EverCookie, create problems for yourself again, but while they are being created:
And now you can (attention, authorization on Habré!) clear the FireFox history in the usual way (i.e., the way Cookie-AutoDelete works in this scheme) . Return to that site and click restore cookies.
It gave him noodles when he asked for a canvas, but it was racially correct and with a slight difference from what he expected.
Difference:
Replaces canvas, audio, history, window, domRect. Just changing it for each request is IMHO like starting to change clothes in the middle of the street (there is a frequency in the settings).
You can test it on the BrowserLeaks website and on the add-on website.
There is another add-on like NoScript - ScriptSafe. It also adds random noise to the keyboard fingerprint. But with 10-finger typing, no ice.
7. Privatize the Fox and wean her from loving her foreign homeland
IMHO, the main problem with the fox’s privacy is in bugs, more precisely in their use, and in geolocation. And it doesn’t even depend on FireFox or Google, but onthe very sewing of the collar itself, the geolocation itself. Especially when using a VPN, it’s a failure; by IP you’re Leo Tolstoy, but by MAC you’re a simple Muscovite. The rest is just that, throwing pitchforks at GCLI screenshots is somehow not constructive.
The reason for the trouble with geolocation: this one and something similar to this one. Therefore, I would suggest not to disable geolocation in FireFox, but to use secure connections, to cheat somethingwith the MAC address, especially since it may already be built in, despite all sorts of research by British militaryscientists - since a) find protection against this bypass ( it also already exists, but you need to google and study) and don’t customize the MAC - I think everything is clear b) not everyone uses all sorts of wunderwaffles and other neural networks, but they are completely tied to the MAC. And disabling access to geolocation in FireFox will only disorient the fox and cut out the search in Google Map, but the problem of snatching hooded underpants at half the price on every corner
IMHO - it won't solve
Disabling geolocation can only be prevented by the following option (exaggerated for clarity): we went to the tourist office, while we were waiting we went to the site, geolocation quietly turned on, the location and login details were recorded, the next time we entered this site the banner “Gathered in vacation? Let's go to the boa constrictors! - as a result, Comrade Stalin personally came under suspicion from the KGB.
By the way, the main reason for such failures with browsers and the epoch-making battle between hedgehogs and snakes is not due to the non-trivial machinations of enemy intelligence, but because of crooked innovations such as the ping attribute in HTML5, which can potentially expose the user to all advertisers and intelligence agencies in the world if they are entered there through space, and adding navigator functionality wherever you go . Hence all this gimmick with unexpected access of sites to batteries, sensors, languages, user agents and other liver, and, which is typical for such osmium-187, it manages to work without any connection with geolocation and even where there is a Wi-Fi adapter by definition, it is not and cannot be, suddenly piercing the user via IP and returning data via Geolocation, which blows the minds of novice programmers.
Privatization option for users
Please pay attention to ainu's comment. I’ll definitely post a separate file regarding the safe privatization of a fox,check back in the week . But at the moment you can:
1. Go to the profile folder (there, instead of x there are numbers\letters), something like this: C:\Users\User\AppData\Roaming\Mozilla\Firefox\Profiles\xxxxx.defalut
2. See if there is a user.js
3 file there. If there is one, you need to open it, if not, create it.
4. From the code below, move the blocks there:
5. Save the file, restart the fox.
6. This file - user.js can be saved and used after reinstalling FireFox.
But there are two ambushes:
Number one. We must remember that it takes precedence over the settings, that is, if the value is set there = true for something, you won’t be able to prove to FireFox through about:config that it is = false. You will need to edit the file.
Number two . Deleting a file will not lead to the expected deprivatization of the fox, but to predictable attempts to remember what was changed there and thinking about how to live with it now. Therefore, I wrote “default settings” in the file. In order to “roll back” these changes, if something happens, you will need to change the settings in this file to those specified by default.
But there is a point in this : every time you start FireFox, smelling this file, reads it and changes its settings. They remain changed this way, even if there is no file, but malicious attempts to change these settings in the fox itself will not work; it reads them again from the file when loading.
6. If the Internet fails, you will need to open the file again, find the entry and change true to false:
user_pref("network.dns.disableIPv6", <b>false</b>);
(which, in fact, is very unlikely, especially if you don’t know what it is. This protocol is promising, but not widespread)
7. And open the SiteSecurityServiceState file there, delete the contents, close and save. Set the read-only attribute. To be sure, it would be nice to remove the user rights to it, but this, in principle, is unnecessary.
Disclaimer
I apologize to the respected educated Habra community, during the research process I read a lot of forums, there is a suspicion that the matter may smell of kerosene.
After such “optimization”, if you do not remove unnecessary things, for example, DRM playback (on YouTube and Netflix), Lisa will become extremely private, but no one needs it. For 127.0.0.1 you won’t be able to kick her out with a stick, and if you kick her out, her paw will either break or her tail will fall off, especially if you have DNS configured for ipv6. And if this happens on a mobile device (where the sensors are turned off, it’s not anonymous, but for a desktop PC) it will, in addition, become non-traditionally oriented. Please check everything carefully and if you test, it is better to use a test profile.
user.js
Go to the fox profile folder, something like this: \User\AppData\Roaming\Mozilla\Firefox\Profiles\xxxxx.defalut. Clear the SiteSecurityServiceState (supercookie) file, set it to read-only and reset the user's rights for it.
Configure DNS over HTTP.
Test everything properly on IpLeak .
And go out hunting for hunters. To do this:
1. Download Lightbeam
2. The profile must be clean (no banner cutters!). Lay out the route Yandex-Google-OK-Vk-YouTube
3. Look at the result. Something like that.
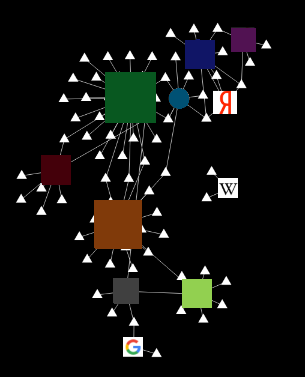
Here you just need to take into account that Lightbeam brings everything together, even if it has nothing to do with surveillance. All APIs, access to shared resources, etc. And unites sites that share them. And most importantly, do not try to add anything to the rules based on this picture. The second question on Google for the query “yastatic” is “how to remove it.” This is static, not statistics. And now Lightbeam is wondering why their rating has dropped, and users are wondering why their “pictures are not loading.”
4. Install uBlock Origin, cover it with Nano Defender, otherwise when you go to qaru the content suddenly turns around and thus reverses the image, install HTTPS Everywhere (which is also true for Zombie cookies), Decentraleyes, Privacy Badger, add, IMHO, Malwarebytes, of all the free add-ons, it seems to be the best at blocking phishing sites on the list.
Configure Malwarebytes
1. In the “Enable protection” settings, disable “Enable advertising/tracker protection”. It may cut out something that is not at all what is needed, and this is clearly superfluous for an “antivirus”.
2. Add to the exceptions the sites that will be needed for testing in the next chapter (they are not dangerous, but, of course, they take fingerprints, etc.): browserprint.info, ipcheck.info, iphones.ru, ip-check.info lolzteam.net
Set up uBlock Origin
A separate article is expected
After running between Yandex and Google, I got the result:

I was glad that I had broken the system, but I suspected Badger of treason; in Google, he became suspiciously quiet. I re-read the article, it seems like everything was cut out. But at the end of writing the article, I ended up here, and realized that it’s all vanity of vanities and vexation of spirit, we’re unlikely to become much more private, unless in a village, in the wilderness, in Saratov, but maybe at least it will be safer with all this. uBlock can handle advertising, and even if I’m suddenly offered my favorite type of coffee in a dark gateway, oh well.
But if the passport data falls into the wrong hands, and even with the help of a bigdata, it will be compared with what gateways we go through at what time. In general, I see that one patch has been released against abuse. Now let's wait for the service pack.
I have recently read a number of articles, including on Habré, on digital fingerprints of browsers and surveillance of users on the Internet. For example, the article Anonymous identification of browsers and Traps on the Internet in Forbes magazine, section “technology” - “Big Data”.
Or maybe I don’t want to be taken into account! Only, I'm afraid, the irony is that this is also a fingerprint, and, moreover, apparently, the main reason for the appearance of fingerprints. IMHO, there is only one way. In relation to FireFox - if all the foxes in chorus and each one individually start yapping that they are ordinary standard foxes, and not torus, not chrome and not makos.
But, out of academic interest, to preserve the individuality of the foxes and in response to the latest machinations of wild capitalism, I want to propose the following cunning plan for the consideration of the respected Habracommunity.
I would like to make a reservation right away - I am not an expert in the field of network security or anonymity, I was not a member of anonymous groups, I was not convicted of anonymity, I swear by Thor, the age of the darknet has not been seen.
Target operating system and browsers
Windows 10 x64 and Firefox 62.0.3.
NOTHING TO TALK ABOUT
The fact that Windows sends telemetry and everything related to setting up Windows itself, as well as issues of antiviruses and firewalls, still does not fit into the article. As well as surfing the Internet at night, from under the table and from the refrigerator, through the Tor browser, through VirtualBox with Tails, through Quad VPN and also Whonix (above).
I suggest, for the purity of the experiment, to create a new FireFox profile
In order to see how the proposed upgrade affects the fox’s performance
I suggest installing this: Page Speed Monitor

(this is the page loading time). If you click on it, there is detailed information.

On the following points. There, in two cases, it is suggested to clear the history and profile cookies. Be careful if you are logged in to Habré!
1. Cut out banal surveillance technology. Redirect
Yandex, however, wrote that it’s the other way around, for the purposes of encryption and anonymity, it seems like it’s really proof, but so as not to stumble over any bullshit at every step:
- install Google and Yandex search link fix for major search engines
- install Clean Links for everything else.
In Clean Links settings
— IMHO it’s better to uncheck “highlight cleared links” and you can temporarily check “show messages” to observe the effect.
— You can enable the option “make non-clickable links clickable”
— Replace the line “Skip Links...” with\/ServiceLogin|imgres\?|searchbyimage\?|watch%3Fv|auth\?client_id|signup|bing\.com\/widget|oauth|openid\.ns|\.mcstatic\.com|sVidLoc|[Ll]ogout|submit\?url=|magnet:|(?:google|yandex)\.(?:com|ru)\/\w*captcha\w*[\/?]|(?:google|yandex)\.(?:com|ru)\/.+\.(?:google|yandex)
— Add to exceptions — comma, then google.com, google.ru, yandex.ru, ru.wikipedia.org, en.wikipedia.org, passport.yandex.ru
It is necessary to remember that it may still not work on some sites, then there will be no redirect to the right place, but still this is part of good protection, incl. from phishing, you can turn off problematic sites or add them to the white list
2. Cut out traditional surveillance technology. Cookies
2.1. You must install the First Party Isolation add-on .
A button will appear

True, the author here broke the system. When pressed it is pale (on), but when pressed it is not (off).
2.2. Go to the Cookie Tester website.
Set Cookie.

“Press” the installed button. And click on “Refresh” on the site.

Here you can read Improving privacy in Firefox .
A la sandbox. When the button is pressed, the insulation is turned on, when pressed it turns off (and for some reason it is indeed turned off by default).
Two states “isolated” and “not isolated”. At the same time, “not isolated” is the same for all sites, but “isolated” is individual for each site and one site does not have access to another.
The same is true for one site - if you press the button here now, Habr will not see the cookie. But it will calculate the second input. Therefore, he will be fired without severance pay.
But, on the other hand, cookies will no longer be transmitted across different sites; when the button is turned on, sites will no longer see other people’s cookies, so surveillance will be difficult + it will be much more difficult to steal them. Although Evercookies and other nanotechnologies are not affected, I found out.
Suggestion for use:
Leave the button enabled. As far as I’ve read, there may be a case when problems arise with authorization (sometimes the site forwards to another, but its own, that is, “legally”). Then you will need to disable it on this site (if you log in, turn it on, you will be logged out). But I haven’t come across such sites yet.
3. Cut out innovative surveillance technology. Evercookies
3.1. You need to install the Multi-Account Containers
3.2 add-on. Get into trouble (not a single Fox will get hurt)
Good description of Evercookie on Habré .
Cookies are cross-domain, but some of them will no longer help - the previous completed step will not. And with HTML5 canvas, etc. The fox cannot do anything (or rather, it can, but in a very sophisticated way and it would be better not to - see below). By the way, CCleaner completely demolishes them, but along with history, cookies and other useful things.
Website with Evercookie. You need to press the top button first, then the bottom button.

Snatched:

On the FireFox panel you need to click:

Then, on
Generally speaking, any container, they are the same, the names are different.
Ever-ik fail:

Suggestion for use:
Alternatively, isolate all social networks, payments, etc. from everything else by assigning them a default container. It’s just inconvenient that all links clicked inside the container open in the same container.
By the way, there is one more benefit from this technology, although this is obvious, but still.
If you distribute everything into containers both in mail (if FireFox is the default browser or the web mail form is open) and on the Internet, you can check whether you got where you wanted, if something important:
There is another technology, on top of this temporary-containers, focused on tabs, not domains (although you can add a dependency, isolate a domain in one container, or even subdomains).
And when closed, it can erase the entire history. And now I would remove Evercookie from the canvas, whether they are there or not (I checked, sir). But IMHO it’s still a bit damp. FierFox tabs jump around, sometimes close, etc. and so on. And it slows down.
Evercookie, on the site, it’s better to click to delete it

until the next time.
4. Clean up the previously cut
The previously mentioned addon “Cookie-AutoDelete” did not justify itself.
Cause
“Cookies-AutoDelete” turned out to be, although quite implicitly, incompatible with the first part isolation level technology.
As everyone understands, isolation is achieved through isolation (that’s not what you’re talking about), incl. and cookies, in connection with which FireFox sets the appropriate “marks” in the cookies.sqlite database. And Cookies-AutoDelete beats it with its “CookiesAutoDelete” label (tested using SQLiteStudio)
To replace “Cookies-AutoDelete” I can suggest Cookiebro
- It is compatible
- Although in English, it is easy to configure
There is a Cookies editor
For carefully stored favorite cookies, there are security settings

Highlighted - this implies proof of compatibility
Secure - transmit only via https
Http Only - transmit only via http. This doesn't mean https! see above. This means not giving access to Java and other potentially dangerous junk, but transmitting it only the old fashioned way, in the http
Host Only header - not giving subdomains access to the goodies (in the example, only yandex.ru would have access, but Yandex.Music and etc. - no)
The downside is that in order for your favorite cookies to be preserved, you need to add the site to the white list, and the number of cookies for the site can be over 9000. This is probably also somehow avoided, but I haven’t looked.
Another minus is that wherever you are registered, you need to add it to the white list (at first, Habr logged you out every 5 minutes, because the cookie was deleted with this frequency, until this pandemonium got tired of it).
Reliably cuts out the E-tag along with the updated one from step 5 (if you enable the “Limit tab history” option added in step 5)
Suggestion for use:
Set up all the previous ones and this item, and it seems like you can forget about cookies and so on, this whole design You have to remove them yourself. And you don’t need to train every site you come across. Plus upgrade CCleaner according to the instructions in the article about “forensics” and configure it so that it deletes everything else and compresses the database.
5. Cut out ETag and other half-cut nanotechnologies
Addon Chameleon. WebExtension from Random Agent Spoofe.
The text has been changed due to the update of the proposed addon.
I would suggest the following settings:
Options tab
- Set Enable script injection - otherwise half of the functionality will not work.
— Set protect window.name — BUT! the enabled option breaks the “I’m not a robot” captcha, either don’t turn it on or remember and turn it off in such cases
- Enable tracking protection - probably not necessary, it’s better to install uBlock later and hide it (see below). Otherwise, “adblocked” sites will start to snap back.
- Disable WebSockets - IMHO not necessary, then half of the services do not work.
— Set Limit tab history — Limits sites’ access to history (presumably up to 2 visits)
— Spoof Client Rects — can be omitted, the next add-on can do this too
— Screen size spoofing — I suggest selecting “Custom” and setting the resolution manually (see. below “average temperature for a fox”)
- Enable 1st party isolation - this is the same as that set in point 1. button.
— Resist fingerprinting , IMHO — not worth it (see fingerprints below). FireFox, instead of pretending to be a rag, for some reason begins to pretend to be a Tor browser.

And, as you know, very few people like Tor + half of the other functionality of the add-on will stop working + the window when starting the browser stops expanding to full screen, it suits someone, no less.
Headers tab
- Set to Disable Authorization - The browser allows you to send hidden authentication data to third-party sites; enabling this option stops this mess. But there may be difficulties with authorization on some sites.
— Enable DNT (Do Not Track) — Enable message sending (do not track). Sites, of course, either ignore it or pretend not to. IMHO - set it (according to various sources - it is sometimes recommended, sometimes not, depending on the number of browsers that have passed the test and collected statistics on this parameter, since the choice to set it or not is from the point of view of “not standing out”, not functionality)
- Set Spoof If-None-Match - Write a random number to ETags
- Spoof X-Forwarded-For- If you set, for example, the IP of the Netherlands, it will add it to the HTTP header and the site will decide that this is the IP of the computer, based on what poorly configured proxies add to the header. Those. It’s like the IP of the computer is the IP of the proxy, and the IP in the header is the other way around and the IP from the header will be included in the site log. But here, in my opinion, it’s better not to, the IP provider will be banned as a left-wing proxy. Another question is that when using a proxy, this may be relevant, so that if it’s crappy, it won’t show the real IP in the header.
— Disable Referer — IMHO not necessary. Disables referrers, you will not be able, for example, to return when turning pages on a site to the previous page
- Set Spoof Source Referer (puts a referrer to it when you go to the site)
- Set Upgrade Insecure Requests - automatically request the site via https if it works in in both modes (http and https)
- Referer X Origin Policy - transfer the base domain in the referrer. "Match base domain" is recommended (but not sure it won't break anything if for some reason inside the domain it matters which subdomain you changed from). Example: for example.com, news.example.com, blog.example.com - the referrer example.com will be transmitted
- Rferer Trimming Policy - trim the transmitted referr. "Scheme, host, port, path" is recommended. Example: for the link example.com :8080/page?privacy=false&trackingid=XYZ, it will be transmitted - example.com :8080/page
- Set Spoof Accept-Encoding - will replace HTTP_ACCEPT_ENCODING with gzip, deflate. It seems to be no problem
- Spoof Accept-Language - language, "eu-US" is recommended, but sites may try to display content in this language.
I suggest choosing the average fox temperature as follows: switch user agents within versions of the source OS and within versions of FireFox (why - see next article). I think a couple of versions of fox 61 and 62 and Windows 7 with Windows 10 , screen size 1366x768 or “any” will do , you can get more specific here StatCounter .
It should be taken into account that changing the user agent with an indezhkt - all sorts of addons, such as “Google Translate”, hand over a real user agent, because packages slip past the chameleon.
Costs of camouflage
— If you impersonate a mobile phone, the consequences, I think, are known to everyone
— Impersonating Google Chrome is fraught, Google will accept you as one of its own (and it will even stop adding redirects), but at the same time it will begin to secretly feed the disguised fox something inedible for it, why would it will start to lag, and on YouTube, who knows what happens, everything will be lost except for the video that was opened
- Client-oriented M$ will persistently sell installation packages for the OS that is set in the user agent, even if it is KolibriOS
- Attempts to replace fonts are a surefire way to be left without Google Doc
- Attempts to cast an IP address through headers permanently lead to an awkward situation: Google is not allowed, in Yandex the content is cut out with primordial Russian hospitality, and in DakDak-Go and StartPage it is not interesting, you can get there without such tricks
6. Saw out the remaining spherical Schrödinger cats in Faraday cages
Install CanvasBlocker . Return to the site with EverCookie, create problems for yourself again, but while they are being created:

And now you can (attention, authorization on Habré!) clear the FireFox history in the usual way (i.e., the way Cookie-AutoDelete works in this scheme) . Return to that site and click restore cookies.
It gave him noodles when he asked for a canvas, but it was racially correct and with a slight difference from what he expected.
Difference:

Replaces canvas, audio, history, window, domRect. Just changing it for each request is IMHO like starting to change clothes in the middle of the street (there is a frequency in the settings).
You can test it on the BrowserLeaks website and on the add-on website.
There is another add-on like NoScript - ScriptSafe. It also adds random noise to the keyboard fingerprint. But with 10-finger typing, no ice.
7. Privatize the Fox and wean her from loving her foreign homeland
IMHO, the main problem with the fox’s privacy is in bugs, more precisely in their use, and in geolocation. And it doesn’t even depend on FireFox or Google, but on
The reason for the trouble with geolocation: this one and something similar to this one. Therefore, I would suggest not to disable geolocation in FireFox, but to use secure connections, to cheat somethingwith the MAC address, especially since it may already be built in, despite all sorts of research by British military
IMHO - it won't solve
Disabling geolocation can only be prevented by the following option (exaggerated for clarity): we went to the tourist office, while we were waiting we went to the site, geolocation quietly turned on, the location and login details were recorded, the next time we entered this site the banner “Gathered in vacation? Let's go to the boa constrictors! - as a result, Comrade Stalin personally came under suspicion from the KGB.
By the way, the main reason for such failures with browsers and the epoch-making battle between hedgehogs and snakes is not due to the non-trivial machinations of enemy intelligence, but because of crooked innovations such as the ping attribute in HTML5, which can potentially expose the user to all advertisers and intelligence agencies in the world if they are entered there through space, and adding navigator functionality wherever you go . Hence all this gimmick with unexpected access of sites to batteries, sensors, languages, user agents and other liver, and, which is typical for such osmium-187, it manages to work without any connection with geolocation and even where there is a Wi-Fi adapter by definition, it is not and cannot be, suddenly piercing the user via IP and returning data via Geolocation, which blows the minds of novice programmers.
Privatization option for users
Please pay attention to ainu's comment. I’ll definitely post a separate file regarding the safe privatization of a fox,
1. Go to the profile folder (there, instead of x there are numbers\letters), something like this: C:\Users\User\AppData\Roaming\Mozilla\Firefox\Profiles\xxxxx.defalut
2. See if there is a user.js
3 file there. If there is one, you need to open it, if not, create it.
4. From the code below, move the blocks there:
- potential security gaps;
- potential leaks;
- potential fingerprints;
- perhaps - an extra load (I don’t think that the functionality of sending Mozill statistics is relevant for you);
5. Save the file, restart the fox.
6. This file - user.js can be saved and used after reinstalling FireFox.
But there are two ambushes:
Number one. We must remember that it takes precedence over the settings, that is, if the value is set there = true for something, you won’t be able to prove to FireFox through about:config that it is = false. You will need to edit the file.
Number two . Deleting a file will not lead to the expected deprivatization of the fox, but to predictable attempts to remember what was changed there and thinking about how to live with it now. Therefore, I wrote “default settings” in the file. In order to “roll back” these changes, if something happens, you will need to change the settings in this file to those specified by default.
But there is a point in this : every time you start FireFox, smelling this file, reads it and changes its settings. They remain changed this way, even if there is no file, but malicious attempts to change these settings in the fox itself will not work; it reads them again from the file when loading.
6. If the Internet fails, you will need to open the file again, find the entry and change true to false:
user_pref("network.dns.disableIPv6", <b>false</b>);
(which, in fact, is very unlikely, especially if you don’t know what it is. This protocol is promising, but not widespread)
7. And open the SiteSecurityServiceState file there, delete the contents, close and save. Set the read-only attribute. To be sure, it would be nice to remove the user rights to it, but this, in principle, is unnecessary.
Disclaimer
I apologize to the respected educated Habra community, during the research process I read a lot of forums, there is a suspicion that the matter may smell of kerosene.
After such “optimization”, if you do not remove unnecessary things, for example, DRM playback (on YouTube and Netflix), Lisa will become extremely private, but no one needs it. For 127.0.0.1 you won’t be able to kick her out with a stick, and if you kick her out, her paw will either break or her tail will fall off, especially if you have DNS configured for ipv6. And if this happens on a mobile device (where the sensors are turned off, it’s not anonymous, but for a desktop PC) it will, in addition, become non-traditionally oriented. Please check everything carefully and if you test, it is better to use a test profile.
user.js
Code:
/*
TESTED ON FIREFOX QUANTUM 62.0.3 (64-BIT)
*/
//------------------------------------------------ -------------------------------------------------- -----------------------
/* POTENTIAL SECURITY GAPS */
//------------------------------------------------ -------------------------------------------------- -----------------------
/*
Prevents sites from accessing the local machine, which would allow them to analyze the list of open ports.
Possible problems: it will become impossible to access addresses such as http://127.0.0.1:631, used to configure printers via CUPS and other devices:
Default: localhost, 127.0.0.1
*/
user_pref("network.proxy.no_proxies_on", "");
/*
Prevent connection to device on Firefox OS for Wi-Fi debugging
Possible problems:
Default: true
*/
user_pref("devtools.remote.wifi.scan", false);
/*
Remove default permissions (it seems that they allow you to read some data from about:support)
Possible problems:
Default: resource://app/defaults/permissions
*/
user_pref("permissions.manager.defaultsUrl", "");
/*
HTML5. Disables sending ping when clicking on a link (HTML5 supports the ping attribute, like <a ping="http://ping.site" href="http://site.com")
This function sends data to the URI defined in the hyperlink when the user clicks on it.
Possible problems:
Default: false
*/
user_pref("browser.send_pings.require_same_host", false);
user_pref("browser.send_pings", false);
/*
Disable requesting IPv6 addresses from DNS.
Possible problems: if the DNS settings on the server are only IPv6
Default: true
*/
user_pref("network.dns.disableIPv6", true);
/*
Disable the use of disk cache if an SSL encrypted connection is used.
Possible problems: Reduced performance due to not caching
Default: true
*/
user_pref("browser.cache.disk_cache_ssl", false);
/*
Offline App Cache. Do not use without explicit permission from the user.
Example: (from the forum). People who have problems with sites like https://web.telegram.org/ - which save data for offline operation, copying their garbage to the auto storage?
Possible problems:
Default: true
*/
user_pref("browser.offline-apps.notify", true);
user_pref("offline-apps.allow_by_default", false);
/*
Adding a list of downloaded files to the "Recent Documents" list:
Possible problems: uploaded files will not be added to this list
Default: true
*/
user_pref("browser.download.manager.addToRecentDocs", false);
/*
Firefox Hello (Telefonica).
Video and calls in the browser. (Firefox connects without asking the user)
*/
user_pref("loop.enabled", false);
//------------------------------------------------ -------------------------------------------------- -----------------------
/* POTENTIAL LEAKS */
//------------------------------------------------ -------------------------------------------------- -----------------------
/*
WebRTC and peering (used for some chats, video calls, etc.).
IP address leak, incl. the one from the computer to the provider (when there is no VPN)
Possible problems: I think this can be sacrificed until the gap is patched
Default: true
*/
user_pref("media.peerconnection.enabled", false);
//If I understand correctly, there is some kind of peerconnection with the FireFox account, but this is not certain and is possible. the point above is already disabled
user_pref("media.peerconnection.identity.enabled", false);
/*
WebRTC WG. Additional functionality - capture and video broadcast of desktops and Media Capture Task Force
Possible problems:
*/
user_pref("media.getusermedia.browser.enabled", false); //Default: false
user_pref("media.getusermedia.screensharing.enabled", false); //Default: true
/*
Perform DNS queries through a SOCKS proxy rather than on the client (not bypassing proxy settings). DNS leaks
Attention: This setting is valid only(!) through a remote server; for example, when using onion routing
true - the browser performs a DNS lookup on the remote server;
false - a DNS search is performed on localhost (usually, direct DNS acquisition from the Internet provider).
If a remote server is not used, then the DNS server addresses specified in the properties of the current network connection are used
computer, i.e. the setting doesn't matter
Possible problems:
Default: false
*/
user_pref("network.proxy.socks_remote_dns", true);
/*
Pre-query DNS for every link on a page
DNS leak when accessing through a proxy or VPN
Possible problems: Loss of performance.
Default: false
*/
user_pref("network.dns.disablePrefetch", true);
/*
Disable browser measurements of the start and end times of page loading.
Analysis of this data by sites allows you to determine whether a proxy server is being used.
Possible problems: lack of information. about performance (including add-ons: Ghostery, app.telemetry Page Speed Monitor)
Default: true
*/
user_pref("dom.enable_performance", false); //Information about the start and end time of page loading
user_pref("dom.enable_performance_observer", false); //Interface for monitoring measurement events and new performance records
user_pref("dom.enable_performance_navigation_timing", false); //Resource Timing API (information about the speed of processing elements)
/*
Prohibits defining network connection parameters (in this case, the type of connection is transmitted: LAN, Wifi, 3G, and so on)
Possible problems:
Default: true
*/
user_pref("dom.netinfo.enabled", false);
/*
Optimizing prefetch (lookahead queries). There is a chance of grabbing excess + showing excessive activity
Possible problems: Loss of performance.
On the other hand, if out of 100500 pre-selected, 1-2 are required, it should increase.
The brakes will appear - you can turn them on. back
*/
//DNS lookups, TCP handshakes and TLS handshakes
user_pref("network.predictor.enabled", false); //Default: true
user_pref("network.predictor.enable-hover-on-ssl", false); //Default: false
//Preload links that the browser considers the user's most likely next choice
user_pref("network.prefetch-next", false); //Default: true
//Preload pages when hovering over a link
user_pref("network.http.speculative-parallel-limit", 0); //Default: 6
//------------------------------------------------ -------------------------------------------------- -----------------------
/* POTENTIAL FINGERPRINTS */
//------------------------------------------------ -------------------------------------------------- -----------------------
/*
HTML5. Transferring statistics to sites about the performance of decoding HTML5 videos, which are used to create a fingerprint
Possible problems:
Default: true
*/
user_pref("media.video_stats.enabled", false);
/*
WebGL. Interactive 3D graphics in JavaScript. Under detailed information. You can get an impression of the system's graphical capabilities
WebGL. Inertial 3D graphics in JavaScript
Possible problems:
*/
user_pref("webgl.disable-extensions", false); // Default: false
user_pref("webgl.min_capability_mode", true); // Default: false
user_pref("webgl.enable-debug-renderer-info", false); // Default: true
/*
WebGL OffscreenCanvas
The mechanism for performing rendering via WebGL in a separate thread, using the OffscreenCanvas API of the ServiceWorkers system (that is, even when the application is closed). You can simply disable ServiceWorkers (see below)
Possible problems:
Default: false
*/
user_pref("gfx.offscreencanvas.enabled", false);
/*
GamePad
Gamers write that using information about the controller and the codes of unusual keys, you can make a fingerprint. Sounds logical.
Possible problems: Will cut out the GamePad
Default: true
*/
user_pref("dom.gamepad.enabled", false);
//------------------------------------------------ -------------------------------------------------- -----------------------
/* POSSIBLY EXTRA LOAD */
//------------------------------------------------ -------------------------------------------------- -----------------------
/*
Browser startup time measurement. No warning will be displayed if it starts slowly
Possible problems:
Default: true
*/
user_pref("browser.slowStartup.notificationDisabled", false);
/*
Collecting browser usage statistics about page loading
Possible problems:
Default: true
*/
user_pref("beacon.enabled", false);
/*
Replacement of requested pages with Mozilla page
From the forum: Periodically, a line pops up at the top of the browser window with the inscription: “This network may require you to log in to gain access to the Internet” and is redirected to the site detectportal.firefox.com.
Possible problems:
*/
user_pref("network.captive-portal-service.enabled", false); //Default: true
user_pref("network.captive-portal-service.minInterval", 0); //Default: 60000
user_pref("captivedetect.maxRetryCount", 0); //Default: 5
/*
Submitting performance and error reports
Possible problems:
Default: true
*/
user_pref("datareporting.healthreport.service.enable", false);
user_pref("datareporting.healthreport.uploadEnabled", false);
user_pref("datareporting.policy.dataSubmissionEnabled", false);
user_pref("security.ssl.errorReporting.enabled", false);
user_pref("security.ssl.errorReporting.automatic", false);
user_pref("security.ssl.errorReporting.url", ""); //По умолчанию: https://incoming.telemetry.mozilla.org/submit/sslreports/
user_pref("datareporting.healthreport.infoURL", ""); //По умолчанию: https://www.mozilla.org/legal/privacy/firefox.html#health-report
user_pref("datareporting.policy.firstRunURL", ""); //По умолчанию: https://www.mozilla.org/privacy/firefox/
user_pref("breakpad.reportURL", ""); //По умолчанию: https://crash-stats.mozilla.com/report/index/
/*
Submitting plugin error reports
Possible problems:
Default: true
*/
user_pref("dom.ipc.plugins.flash.subprocess.crashreporter.enabled", false);
user_pref("dom.ipc.plugins.reportCrashURL", false);
/*
Collection and sending of statistics.
Possible problems:
Default: true
*/
user_pref("toolkit.telemetry.enabled", false);
user_pref("toolkit.telemetry.archive.enable", false);
user_pref("toolkit.telemetry.unified", false);
user_pref("toolkit.telemetry.bhrPing.enabled", false);
user_pref("toolkit.telemetry.bhrPing.enabled", false);
user_pref("toolkit.telemetry.firstShutdownPing.enabled", false);
user_pref("toolkit.telemetry.newProfilePing.enabled", false);
user_pref("toolkit.telemetry.reportingpolicy.firstRun", false);
user_pref("toolkit.telemetry.shutdownPingSender.enabled", false);
user_pref("toolkit.telemetry.shutdownPingSender.enabledFirstSession", false);
user_pref("toolkit.telemetry.updatePing.enabled", false);
user_pref("toolkit.telemetry.debugSlowSql", false);
user_pref("toolkit.telemetry.hybridContent.enabled", false);
user_pref("browser.newtabpage.activity-stream.telemetry", false);
user_pref("browser.newtabpage.activity-stream.telemetry.ut.events", false);
user_pref("browser.newtabpage.activity-stream.feeds.telemetry", false);
user_pref("security.ssl.errorReporting.enabled", false);
user_pref("browser.ping-centre.telemetry", false);
user_pref("devtools.onboarding.telemetry.logged", false);
user_pref("toolkit.telemetry.server", ""); //Default: https://incoming.telemetry.mozilla.org
user_pref("browser.newtabpage.activity-stream.telemetry.ping.endpoint", ""); ////Default: https://tiles.services.mozilla.com/v4/links/activity-stream
user_pref("toolkit.telemetry.cachedClientID", "");
/*
Experimental features
Possible problems:
Default: true
*/
user_pref("network.allow-experiments", false);
/*
Sending information about add-ons and metadata about add-on usage.
Possible problems: Firefox, based on the list of already installed add-ons, offers new ones on the "Get Add-ons" page in the add-ons manager
After switching off - it will not offer
Default: true
*/
user_pref("extensions.getAddons.cache.enabled", false);
/*
Prohibiting the creation of a cache for offline browsing
Possible problems:
Default: true
*/
user_pref("browser.cache.offline.enable", false);
//------------------------------------------------ -------------------------------------------------- -----------------------
/* POSSIBLY - EXTRA SERVICES */
//------------------------------------------------ -------------------------------------------------- -----------------------
/*
WebGL. Interactive 3D graphics in JavaScript. But it seems that this technology is not very widespread
Example: https://habr.com/post/190388/
*/
user_pref("webgl.disabled", true); //Default: false
/*
Snippets. Disable the sending of statistical information associated with Snippets technology ("snippet").
Firefox's default home page (about:home) has a built-in mechanism for displaying some information and tracking user preferences.
*/
user_pref("browser.aboutHomeSnippets.updateUrl", ""); //Default:https://snippets.cdn.mozilla.net/%STARTPAGE_VERSION%/%NAME%/%VERSION%/%APPBUILDID%/%BUILD_TARGET%/%LOCALE%/%CHANNEL%/%OS_VERSION%/%DISTRIBUTION%/%DISTRIBUTION_VERSION%/
user_pref("browser.newtabpage.activity-stream.disableSnippets", true); //По умолчанию: false
user_pref("browser.newtabpage.activity-stream.feeds.snippets", false); //По умолчанию: false
/*
WebRTC and peering (used for some chats, video calls, etc.).
*/
user_pref("media.peerconnection.enabled", false); //Default: false
user_pref("media.peerconnection.ice.default_address_only", false); //Default: false
user_pref("media.peerconnection.ice.tcp", false); //Default: false
user_pref("media.peerconnection.identity.enabled", false); //Default: false
user_pref("media.peerconnection.rtpsourcesapi.enabled", false); //Default: false
user_pref("media.peerconnection.simulcast", false); //Default: false
user_pref("media.peerconnection.video.enabled", false); //Default: false
user_pref("media.peerconnection.video.vp9_enabled", false); //Default: false
user_pref("media.peerconnection.use_document_iceservers", false); //Default: false
/*
SSDP. Streaming. Do not send requests to the network to detect the TV and broadcast video to it
*/
user_pref("browser.casting.enabled", false);
/*
WebSpeech. Speech recognition and synthesis
*/
user_pref("media.webspeech.synth.enabled", false);
user_pref("media.webspeech.test.fake_recognition_service", false);
user_pref("media.webspeech.test.fake_fsm_events", false);
user_pref("media.webspeech.test.enable", false);
user_pref("media.webspeech.synth.force_global_queue", false);
user_pref("media.webspeech.recognition.force_enable", false);
user_pref("media.webspeech.recognition.enable", false);
/*
GCLI. Automatic publication of screenshots on Imgur.com
*/
user_pref("devtools.gcli.underscoreSrc", "");
user_pref("devtools.gcli.lodashSrc", "");
user_pref("devtools.gcli.jquerySrc", "");
user_pref("devtools.gcli.imgurUploadURL", "");
user_pref("devtools.gcli.imgurClientID", "");
/*
WebVR. Support for virtual reality devices
*/
user_pref("dom.vr.require-gesture", false);
user_pref("dom.vr.poseprediction.enabled", false);
user_pref("dom.vr.openvr.enabled", false);
user_pref("dom.vr.oculus.invisible.enabled", false);
user_pref("dom.vr.oculus.enabled", false);
user_pref("dom.vr.enabled", false);
user_pref("dom.vr.test.enabled", false);
user_pref("dom.vr.puppet.enabled", false);
user_pref("dom.vr.osvr.enabled", false);
user_pref("dom.vr.external.enabled", false);
user_pref("dom.vr.autoactivate.enabled", false);
user_pref("dom.vr.autoactivate.enabled", false);
/*
WebCompat
Ability to send reports to https://webcompat.com about browser compatibility issues with websites
For those interested, there is an addon for quickly sending reports:
https://addons.mozilla.org/ru/firefox/addon/webcompatcom-reporter/
*/
user_pref("media.decoder-doctor.new-issue-endpoint", ""); //Default: https://webcompat.com/issues/new
user_pref("extensions.webcompat-reporter.newIssueEndpoint", ""); //Default: https://webcompat.com/issues/new
user_pref("media.decoder-doctor.wmf-disabled-is-failure", true); //Default: false
user_pref("media.decoder-doctor.verbose", false); //Default: false
//------------------------------------------------ -------------------------------------------------- -----------------------
/* POSSIBLY - UNNECESSARY SERVICES */
//------------------------------------------------ -------------------------------------------------- -----------------------
/*
Geolocation and Google geopositioning (GeoIP when working with search servers)
Possible problems: Will cut out geolocation. Sites request location access to better respond to search queries
and provide relevant information based on the user's location.
Content may unexpectedly appear in US instead of EN
*/
user_pref("geo.enabled", false); //Default: true
user_pref("geo.wifi.uri", ""); //Default: https://www.googleapis.com/geolocation/v1/geolocate?key=%GOOGLE_API_KEY%
user_pref("browser.geolocation.warning.infoUR", ""); //Default: https://www.mozilla.org/%LOCALE%/firefox/geolocation/
//GeoIP
user_pref("browser.search.geoSpecificDefaults", false); //Default: true
user_pref("browser.search.geoip.url", ""); //Default: https://location.services.mozilla.com/v1/country?key=%MOZILLA_API_KEY%
user_pref("browser.search.countryCode", "US"); //Default: EN
user_pref("browser.search.region", "US"); //Default: EN
/*
Everything related to searching for add-ons and themes in the “Get add-ons” settings window
Possible problems: "Get add-ons" will not work
*/
user_pref("extensions.getAddons.compatOverides.url", ""); //Default: https://services.addons.mozilla.org/api/v3/addons/compat-override/?guid=%IDS%&lang=%LOCALE%
user_pref("extensions.getAddons.compatOverides.url", ""); //Default: https://services.addons.mozilla.org/api/v3/addons/search/?guid=%IDS%&lang=%LOCALE%
user_pref("extensions.getAddons.compatOverides.url", ""); //Default: https://addons.mozilla.org/%LOCALE%/firefox/
user_pref("extensions.getAddons.compatOverides.url", ""); //Default: https://addons.mozilla.org/%LOCALE%/firefox/search?q=%TERMS%&platform=%OS%&appver=%VERSION%
user_pref("extensions.getAddons.compatOverides.url", ""); //Default: https://addons.mozilla.org/%LOCALE%/firefox/themes/?src=firefox
user_pref("extensions.webservice.discoverURL", ""); //Default: https://discovery.addons.mozilla.org/%LOCALE%/firefox/discovery/pane/%VERSION%/%OS%/%COMPATIBILITY_MODE%
/*
Pocket. Allows you to save links to texts in cloud storage for later reading
Possible problems:
*/
user_pref("extensions.pocket.enabled", false);
user_pref("extensions.pocket.site", ""); //Default: getpocket.com
user_pref("extensions.pocket.api", ""); //Default: api.getpocket.com
user_pref("extensions.pocket.oAuthConsumerKey", "");
/*
Playback of DRM ("Protected (paid) media content", EME).
Possible problems: YouTube and Netflix will be cut out
*/
user_pref("media.eme.enabled", false);
user_pref("media.gmp-eme-adobe.enabled", false);
/*
FireFox Accounts
*/
user_pref("identity.fxaccounts.enabled", false); //Default: true
user_pref("identity.fxaccounts.remote.profile.uri", ""); //Default: https://profile.accounts.firefox.com/v1
user_pref("identity.fxaccounts.remote.oauth.uri", ""); //Default: https://oauth.accounts.firefox.com/v1
user_pref("identity.fxaccounts.auth.uri", ""); //Default: https://api.accounts.firefox.com/v1
user_pref("identity.fxaccounts.remote.root", ""); //Default: https://accounts.firefox.com/
user_pref("browser.newtabpage.activity-stream.fxaccounts.endpoint", ""); //Default: https://accounts.firefox.com/
user_pref("identity.sync.tokenserver.uri", ""); //Default: https://token.services.mozilla.com/1.0/sync/1.5
/*
Synchronization
*/
user_pref("services.sync.engine.addons", false); //Default: true
user_pref("services.sync.engine.bookmarks", false); //Default: true
user_pref("services.sync.engine.history", false);
user_pref("services.sync.engine.passwords", false);
user_pref("services.sync.engine.prefs", false);
user_pref("services.sync.engine.tabs", false);
user_pref("services.sync.engine.bookmarks.buffer", false); //Default: false
user_pref("services.sync.engine.creditcards", false); //Default: false
user_pref("services.sync.engine.creditcards.available", false); //Default: false
user_pref("services.sync.engine.addresses", false); //Default: false
user_pref("services.sync.engine.addresses.available", false); //Default: false
user_pref("services.sync.fxa.privacyURL", ""); //Default: services.sync.fxa.privacyURL
user_pref("services.sync.fxa.termsURL", ""); //Default: https://accounts.firefox.com/legal/terms
user_pref("services.sync.declinedEngines", ""); //Default: ""
/*
Web Push Notifications.
Even if the site is not loaded and there is a subscription from it, it can notify about something (the release of a new article, the arrival of goods)
*/
user_pref("dom.push.userAgentID" , "");
user_pref("dom.push.serverURL", ""); //Default: wss://push.services.mozilla.com/
user_pref("dom.push.alwaysConnect", false);
user_pref("dom.push.enabled", false);
user_pref("dom.push.connection.enabled", false);
user_pref("dom.push.alwaysConnect", false);
user_pref("dom.push.maxQuotaPerSubscription", 0);
user_pref("dom.webnotifications.enabled", false);
user_pref("dom.webnotifications.requireinteraction.enabled", false);
user_pref("dom.webnotifications.serviceworker.enabled", false);
/*
ServiceWorkers
It makes sense to disable it along with synchronization and push notifications
The script that the browser runs in the background does not require web pages or user interaction.
Currently - such functions as push notifications and background synchronization. https://habr.com/company/2gis/blog/345552/
But there is a high probability that if some site uses this, the site’s functionality will be unavailable
*/
user_pref("dom.serviceWorkers.enabled", false);
user_pref("dom.serviceWorkers.testUpdateOverOneDay", false);
user_pref("dom.serviceWorkers.parent_intercept", false);
user_pref("devtools.serviceWorkers.testing.enabled", false);
/*
Disabling the SPDY protocol
In theory - non-private Google, in practice - it is to increase productivity and suddenly something can start to slow down a lot
*/
user_pref("network.http.spdy.enabled", false);
user_pref("network.http.spdy.enabled.deps", false);
user_pref("network.http.spdy.enabled.http2", false);
//------------------------------------------------ -------------------------------------------------- -----------------------
/* IRON */
//------------------------------------------------ -------------------------------------------------- -----------------------
/*
Collection of information from sensors (not necessary for a desktop PC)
*/
user_pref("device.sensors.enabled", false);
/*
Battery monitoring (not needed for desktop PC)
*/
user_pref("dom.battery.enabled", false);
/*
Disabling interaction with a mobile device vibrator (not necessary for a desktop PC)
*/
user_pref("dom.vibrator.enabled", false);
/*
Disabling interaction with the microphone and webcam:
*/
user_pref("media.navigator.enabled", false);
//------------------------------------------------ -------------------------------------------------- -----------------------
/* POTENTIAL OPTIMIZATION */
//------------------------------------------------ -------------------------------------------------- -----------------------
//Number of simultaneous connections to one server. Simply increasing values beyond these is not recommended
user_pref("network.http.max-persistent-connections-per-server", 8); // 6
user_pref("network.http.max-connections", 1500); //900
//------------------------------------------------ -------------------------------------------------- -----------------------
/* TUNING */
//------------------------------------------------ -------------------------------------------------- -----------------------
//Instant spell checking in text fields
user_pref("layout.spellcheckDefault", 2); //Default: 1
//Enables auto-completion of the address in the address bar
user_pref("browser.urlbar.autoFill", true); //false
//Do not capture a space when selecting a word on a page with a double click
user_pref("layout.word_select.eat_space_to_next_word", false);
//Disable the site's warning about closing a tab with important information.
//Message "Are you sure you want to leave this site?"
user_pref("dom.disable_beforeunload", true); //Default: false
//Remove the frame that surrounds the link when clicked
user_pref("browser.display.focus_ring_on_anything", true); //Default: false
user_pref("browser.display.focus_ring_width", 0); //Default: 1
//Prohibit autoplay of multimedia content
user_pref("media.autoplay.enabled", false);Go to the fox profile folder, something like this: \User\AppData\Roaming\Mozilla\Firefox\Profiles\xxxxx.defalut. Clear the SiteSecurityServiceState (supercookie) file, set it to read-only and reset the user's rights for it.
Configure DNS over HTTP.
Test everything properly on IpLeak .
And go out hunting for hunters. To do this:
1. Download Lightbeam
2. The profile must be clean (no banner cutters!). Lay out the route Yandex-Google-OK-Vk-YouTube
3. Look at the result. Something like that.

Here you just need to take into account that Lightbeam brings everything together, even if it has nothing to do with surveillance. All APIs, access to shared resources, etc. And unites sites that share them. And most importantly, do not try to add anything to the rules based on this picture. The second question on Google for the query “yastatic” is “how to remove it.” This is static, not statistics. And now Lightbeam is wondering why their rating has dropped, and users are wondering why their “pictures are not loading.”
4. Install uBlock Origin, cover it with Nano Defender, otherwise when you go to qaru the content suddenly turns around and thus reverses the image, install HTTPS Everywhere (which is also true for Zombie cookies), Decentraleyes, Privacy Badger, add, IMHO, Malwarebytes, of all the free add-ons, it seems to be the best at blocking phishing sites on the list.
Configure Malwarebytes
1. In the “Enable protection” settings, disable “Enable advertising/tracker protection”. It may cut out something that is not at all what is needed, and this is clearly superfluous for an “antivirus”.
2. Add to the exceptions the sites that will be needed for testing in the next chapter (they are not dangerous, but, of course, they take fingerprints, etc.): browserprint.info, ipcheck.info, iphones.ru, ip-check.info lolzteam.net
Set up uBlock Origin
A separate article is expected
After running between Yandex and Google, I got the result:

I was glad that I had broken the system, but I suspected Badger of treason; in Google, he became suspiciously quiet. I re-read the article, it seems like everything was cut out. But at the end of writing the article, I ended up here, and realized that it’s all vanity of vanities and vexation of spirit, we’re unlikely to become much more private, unless in a village, in the wilderness, in Saratov, but maybe at least it will be safer with all this. uBlock can handle advertising, and even if I’m suddenly offered my favorite type of coffee in a dark gateway, oh well.
But if the passport data falls into the wrong hands, and even with the help of a bigdata, it will be compared with what gateways we go through at what time. In general, I see that one patch has been released against abuse. Now let's wait for the service pack.

