Look for events like Scan failed, Malware detected, and Failed to update signatures.
Hackers try to hide their presence. Event ID 104 Event Log was Cleared and event ID 1102 Audit Log was Cleared could indicate such activity. Event ID 4719 System audit policy was changed could also show malicious behavior. If an application crashes, it could be that a hacker has tried to force a process to end to hide their actions.
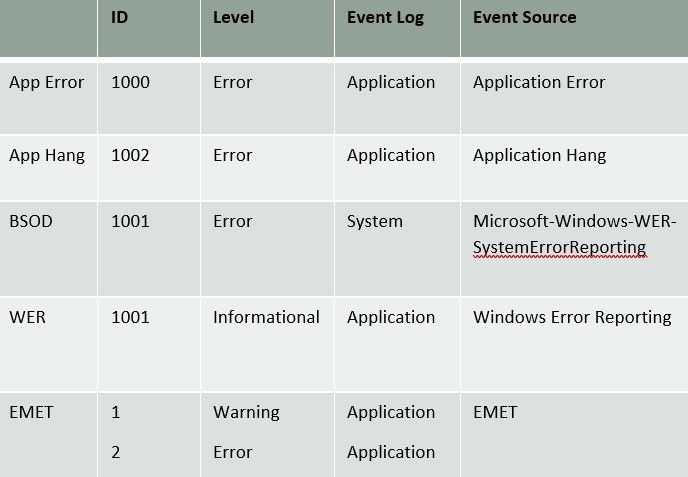
Table 2 shows events that might indicate suspicious logon activity. Pass-the-Hash (PtH) is a popular form of attack that allows hackers to gain access to an account without needing to know the password. Look out for NTLM Logon Type 3 event IDs 4624 (failure) and 4625 (success).

- Application Allow listing
- Application Crashes
- System or Service Failures
- Windows Update Errors
- Windows Firewall
- Clearing Event Logs
- Software and Service Installation
- Account Usage Kernel Driver Signing
- Group Policy Errors
- Windows Defender Activities
- Mobile Device Activities
- External Media Detection
- Printing Services
- Pass the Hash Detection Remote Desktop Logon Detection
Hackers try to hide their presence. Event ID 104 Event Log was Cleared and event ID 1102 Audit Log was Cleared could indicate such activity. Event ID 4719 System audit policy was changed could also show malicious behavior. If an application crashes, it could be that a hacker has tried to force a process to end to hide their actions.

Table 2 shows events that might indicate suspicious logon activity. Pass-the-Hash (PtH) is a popular form of attack that allows hackers to gain access to an account without needing to know the password. Look out for NTLM Logon Type 3 event IDs 4624 (failure) and 4625 (success).

