Tomcat
Professional
- Messages
- 2,687
- Reaction score
- 1,036
- Points
- 113
In February 2017, we published research on fileless attacks on corporate networks. Incident response teams from several financial institutions located in different countries collected data that showed how malware infected corporate networks without leaving any traces on hard drives. The attackers' goal was money, and the best way to make money without leaving any records of transactions is to use remote ATM administration.
This is the second publication about this threat. Here we will describe the methods and techniques that the attackers used in the second stage of attacks on financial organizations - in essence, we will tell how exactly the attackers performed remote administration of ATMs.
In June 2016, Kaspersky Lab received a report from a Russian bank that was the victim of a targeted attack. During the attack, the attackers were able to gain control of ATMs and download malware onto them. After receiving money from ATMs, the program was deleted. The bank's forensic experts were unable to recover the malicious executable files due to the fragmentation of the hard drive after the attack, but were able to obtain the malware logs and the names of some files.
After performing a thorough forensic analysis of the ATM hard drive, the bank's forensics team was able to recover the following log files:
[Date - Time]
[%d %m %Y - %H : %M : %S] > Entering process dispense.
[%d %m %Y - %H : %M : %S] > Items from parameters converted successfully. 4 40
[%d %m %Y - %H : %M : %S] > Unlocking dispenser, result is 0
[%d %m %Y - %H : %M : %S] > Catch some money, bitch! 4000000
[%d %m %Y - %H : %M : %S] > Dispense success, code is 0
As mentioned in the previous post, based on the log data, we created a YARA rule to find a malware sample; The search criterion in this case was the MD5 hash cef6c2aa78ff69d894903e41a3308452. And we found what we were looking for. The sample was downloaded under the name “tv.dll” twice – from Kazakhstan and from Russia.
The malware, which we have codenamed 'ATMitch', operates quite simply. The malware is installed remotely, and a remote connection is established with the ATM from inside the bank using the Remote Desktop Connection protocol. After this, the malware looks for the “command.txt” file, which must be created by the attacker and located in the same folder as the malware. If the file is found, the malware reads its contents, consisting of one character, and executes the corresponding command:
The "tv.dll" sample obtained successfully in this case does not attempt to hide its presence on the system.
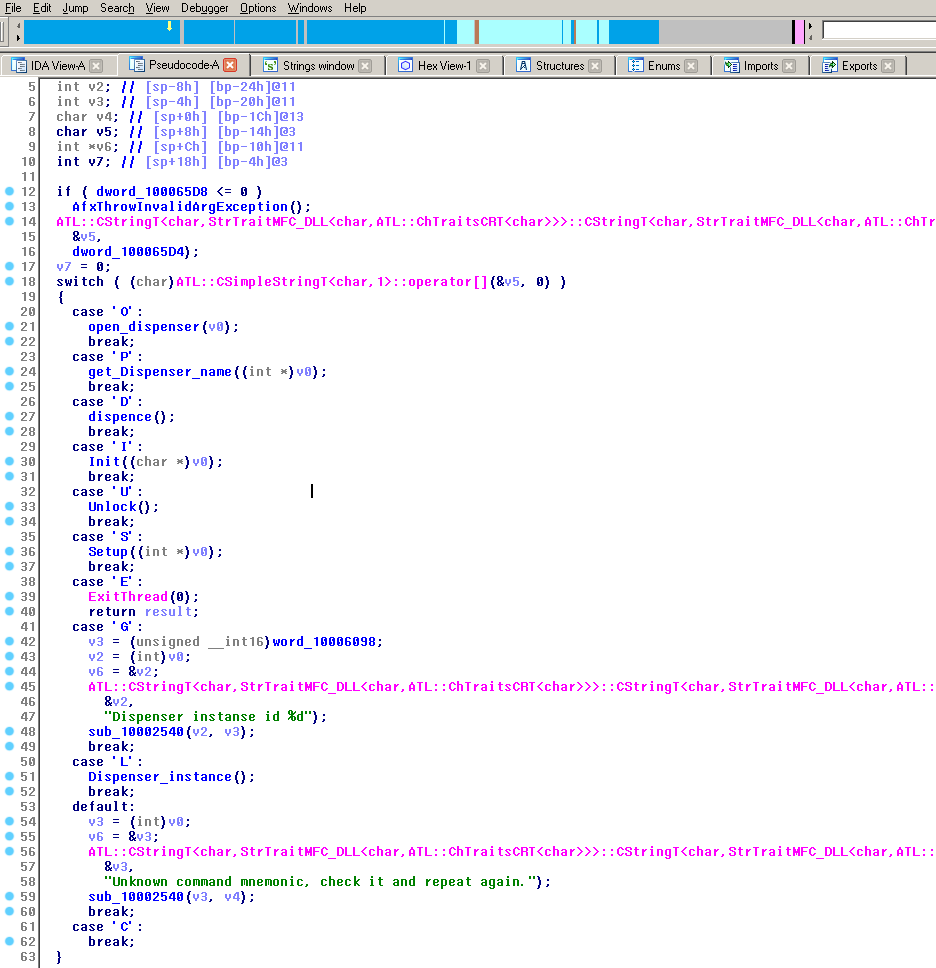
Malware command parser
To control the ATM, the malware uses the standard XFS library. It should be noted that the malware works on any ATM that supports the XFS library (and the vast majority of such ATMs).
Unfortunately, we were unable to extract the malicious executable files ('!A.exe' and 'IJ.exe' located in C:ATM) from the ATM, so we only had file names obtained from forensic analysis. We believe that these are the names of the installer and uninstaller of the malware, respectively. It is also worth noting that the “tv.dll” file contained one Russian-language resource.
Kaspersky Lab continues to monitor and monitor this type of threat. We remind you that ATMs must use approved lists, and banking networks must use solutions to protect against APT attacks.
This is the second publication about this threat. Here we will describe the methods and techniques that the attackers used in the second stage of attacks on financial organizations - in essence, we will tell how exactly the attackers performed remote administration of ATMs.
In June 2016, Kaspersky Lab received a report from a Russian bank that was the victim of a targeted attack. During the attack, the attackers were able to gain control of ATMs and download malware onto them. After receiving money from ATMs, the program was deleted. The bank's forensic experts were unable to recover the malicious executable files due to the fragmentation of the hard drive after the attack, but were able to obtain the malware logs and the names of some files.
After performing a thorough forensic analysis of the ATM hard drive, the bank's forensics team was able to recover the following log files:
- C:WindowsTempkl.txt
- C:logfile.txt
- C:ATM!A.EXE
- C:ATMIJ.EXE
[Date - Time]
[%d %m %Y - %H : %M : %S] > Entering process dispense.
[%d %m %Y - %H : %M : %S] > Items from parameters converted successfully. 4 40
[%d %m %Y - %H : %M : %S] > Unlocking dispenser, result is 0
[%d %m %Y - %H : %M : %S] > Catch some money, bitch! 4000000
[%d %m %Y - %H : %M : %S] > Dispense success, code is 0
As mentioned in the previous post, based on the log data, we created a YARA rule to find a malware sample; The search criterion in this case was the MD5 hash cef6c2aa78ff69d894903e41a3308452. And we found what we were looking for. The sample was downloaded under the name “tv.dll” twice – from Kazakhstan and from Russia.
The malware, which we have codenamed 'ATMitch', operates quite simply. The malware is installed remotely, and a remote connection is established with the ATM from inside the bank using the Remote Desktop Connection protocol. After this, the malware looks for the “command.txt” file, which must be created by the attacker and located in the same folder as the malware. If the file is found, the malware reads its contents, consisting of one character, and executes the corresponding command:
- 'O' – open the dispenser (money dispenser)
- 'D' – give out money
- 'I' – Initialize XFS library
- 'U' – Unlock XFS
- 'S' –Set
- 'E' — Exit
- 'G' – Get dispenser ID
- 'L' – Set dispenser ID
- 'C' — Cancel
The "tv.dll" sample obtained successfully in this case does not attempt to hide its presence on the system.

Malware command parser
To control the ATM, the malware uses the standard XFS library. It should be noted that the malware works on any ATM that supports the XFS library (and the vast majority of such ATMs).
Unfortunately, we were unable to extract the malicious executable files ('!A.exe' and 'IJ.exe' located in C:ATM) from the ATM, so we only had file names obtained from forensic analysis. We believe that these are the names of the installer and uninstaller of the malware, respectively. It is also worth noting that the “tv.dll” file contained one Russian-language resource.
Kaspersky Lab continues to monitor and monitor this type of threat. We remind you that ATMs must use approved lists, and banking networks must use solutions to protect against APT attacks.

