Father
Professional
- Messages
- 2,602
- Reaction score
- 837
- Points
- 113
Iranian hackers have found new ways of covert espionage attacks.
The APT42 cyber espionage group uses social engineering to infiltrate corporate networks and cloud environments in the West and Middle East.
The new campaign is reported by Mandiant (Google), which first documented the group's activities in September 2022. According to experts, APT42 has been active since 2015 and has conducted at least 30 operations in 14 countries.
APT42's main targets are non-governmental organizations, media, educational institutions, activists, and legal services. Google analysts who track the group's operations indicate that malicious emails with two configurable backdoors — Nicecurl and Tamecat-are used to infect targets. Tools allow you to execute commands and steal data.
APT42 impersonates various media outlets, including The Washington Post (USA), The Economist (UK), The Jerusalem Post (IL), Khaleej Times (UAE), Azadliq (Azerbaijan), while attacks often use domains with Typosquatting, for example, " washin q tonpost[.]press"
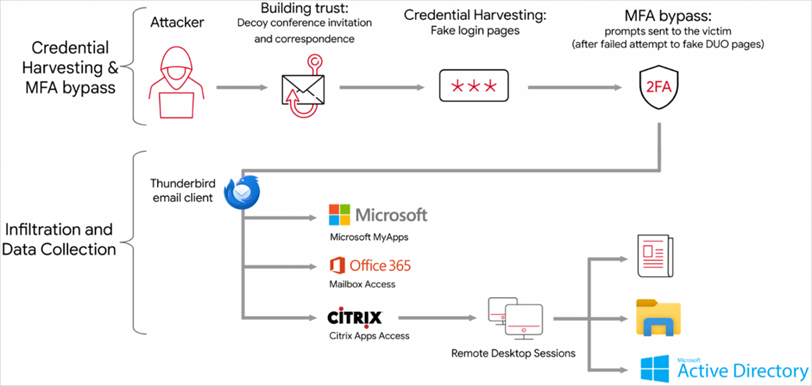
APT42 Attack
APT42 disguises itself as journalists, NGO representatives, or event organizers by sending messages from domains similar to legitimate ones. In the course of communication, attackers seek to gain the victim's trust, and then send a link to a document that redirects to fake login pages that mimic well-known services such as Google and Microsoft. Phishing sites not only steal the victim's credentials, but also multi-factor authentication tokens.
To strengthen its position in infected networks and bypass detection, APT42 uses cloud-based tools, clears Google Chrome history, and uses email addresses that appear to belong to victims organizations to exfiltrate files to OneDrive accounts.
In addition, APT42 uses ExpressVPN nodes, Cloudflare-hosted domains, and temporary VPS servers to ensure the anonymity of its operations. The group also uses Nicecurl and Tamecat backdoors:
Earlier, researchers from Mandiant noted that the APT42 group acts on behalf of the Islamic Revolutionary Guard Corps (IRGC) , and its tactics, techniques and procedures (TTPs) are very similar to APT35 – another Iranian group known as Charming Kitten and Phosphorus.
APT42 gives preference to targeted phishing against corporate and personal email accounts . The victims of APT42 are from at least 14 countries, including the United States, Australia, Europe and the Middle East, including government officials, former Iranian politicians, members of the Iranian diaspora and opposition groups, journalists and academics.
The APT42 cyber espionage group uses social engineering to infiltrate corporate networks and cloud environments in the West and Middle East.
The new campaign is reported by Mandiant (Google), which first documented the group's activities in September 2022. According to experts, APT42 has been active since 2015 and has conducted at least 30 operations in 14 countries.
APT42's main targets are non-governmental organizations, media, educational institutions, activists, and legal services. Google analysts who track the group's operations indicate that malicious emails with two configurable backdoors — Nicecurl and Tamecat-are used to infect targets. Tools allow you to execute commands and steal data.
APT42 impersonates various media outlets, including The Washington Post (USA), The Economist (UK), The Jerusalem Post (IL), Khaleej Times (UAE), Azadliq (Azerbaijan), while attacks often use domains with Typosquatting, for example, " washin q tonpost[.]press"

APT42 Attack
APT42 disguises itself as journalists, NGO representatives, or event organizers by sending messages from domains similar to legitimate ones. In the course of communication, attackers seek to gain the victim's trust, and then send a link to a document that redirects to fake login pages that mimic well-known services such as Google and Microsoft. Phishing sites not only steal the victim's credentials, but also multi-factor authentication tokens.
To strengthen its position in infected networks and bypass detection, APT42 uses cloud-based tools, clears Google Chrome history, and uses email addresses that appear to belong to victims organizations to exfiltrate files to OneDrive accounts.
In addition, APT42 uses ExpressVPN nodes, Cloudflare-hosted domains, and temporary VPS servers to ensure the anonymity of its operations. The group also uses Nicecurl and Tamecat backdoors:
- Nicecurl is a VBScript-based backdoor that can execute commands, upload and execute additional useful data, or perform data mining on an infected host.
- Tamecat is a more sophisticated PowerShell backdoor that can execute arbitrary PowerShell code or C# scripts, giving APT42 greater operational flexibility for data theft and extensive system manipulation. Tamecat can also dynamically update its configuration to avoid detection
Earlier, researchers from Mandiant noted that the APT42 group acts on behalf of the Islamic Revolutionary Guard Corps (IRGC) , and its tactics, techniques and procedures (TTPs) are very similar to APT35 – another Iranian group known as Charming Kitten and Phosphorus.
APT42 gives preference to targeted phishing against corporate and personal email accounts . The victims of APT42 are from at least 14 countries, including the United States, Australia, Europe and the Middle East, including government officials, former Iranian politicians, members of the Iranian diaspora and opposition groups, journalists and academics.

