Carding
Professional
- Messages
- 2,870
- Reaction score
- 2,494
- Points
- 113
Bank customers themselves provided hackers with their account details.
Attackers are attacking hundreds of banking customers in Latin America with a new version of an existing banking Trojan that mimics the interfaces of more than 40 Mexican and Brazilian banks. The campaign aims to trick victims into providing two-factor authentication (2FA) and payment card details, which will allow attackers to hijack their bank accounts.
Researchers from Check Point Software have revealed that the main method of spreading malware is phishing attacks. As part of the campaign, attackers are actively spreading a variant of the BBTok banking Trojan, aimed at users from Mexico and Brazil.
Attackers have developed sophisticated methods to infect different versions of Windows in order to expand the scale of attacks. Cybercriminals use unique techniques, which makes it difficult to detect malware. In particular, as stated by Check Point experts, hackers use "a unique combination of Living off the Land Binaries (LOLBins).
In addition, cybercriminals use advanced geofencing techniques to ensure that victims who receive phishing messages are located only in Brazil and Mexico.
One of the key features of the campaign is the use of fake interfaces for more than 40 banks in Mexico and Brazil. The interfaces are so plausible that many users, without suspecting fraud, provide their personal and financial data.
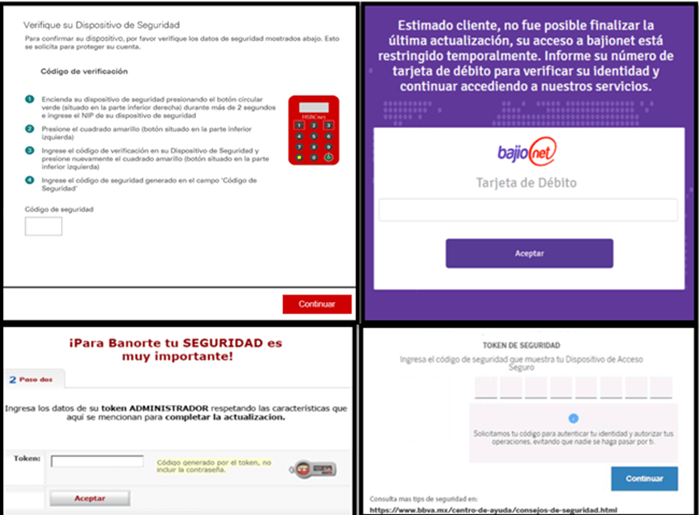
Examples of fake site interfaces
The BBTok trojan was first detected in Latin America in 2020. Its functionality includes control of processes, keyboard and mouse, as well as the ability to manipulate the contents of the clipboard. Check Point researchers discovered the latest version of the Trojan by analyzing the attackers server resources.
The study uncovered a database of victims of the BBTok Trojan in Mexico, containing more than 150 records with information about victims. This confirms the success of the malicious operation, which apparently continues.
Recall that in August, Trend Micro researchers discovered a new banking Trojan called MMRat, targeting Android users in Southeast Asia. MMRat is distributed through phishing sites disguised as official app stores. To improve performance when transmitting large amounts of data, the Trojan uses a specially developed C2 protocol based on Protobuf.
It was also noted that a new banking Trojan for Android called Hook is based on another once-famous ERMAC Trojan. Experts from the NCC Group claim that the ERMAC source code was used as the basis for the Hook.
Attackers are attacking hundreds of banking customers in Latin America with a new version of an existing banking Trojan that mimics the interfaces of more than 40 Mexican and Brazilian banks. The campaign aims to trick victims into providing two-factor authentication (2FA) and payment card details, which will allow attackers to hijack their bank accounts.
Researchers from Check Point Software have revealed that the main method of spreading malware is phishing attacks. As part of the campaign, attackers are actively spreading a variant of the BBTok banking Trojan, aimed at users from Mexico and Brazil.
Attackers have developed sophisticated methods to infect different versions of Windows in order to expand the scale of attacks. Cybercriminals use unique techniques, which makes it difficult to detect malware. In particular, as stated by Check Point experts, hackers use "a unique combination of Living off the Land Binaries (LOLBins).
In addition, cybercriminals use advanced geofencing techniques to ensure that victims who receive phishing messages are located only in Brazil and Mexico.
One of the key features of the campaign is the use of fake interfaces for more than 40 banks in Mexico and Brazil. The interfaces are so plausible that many users, without suspecting fraud, provide their personal and financial data.

Examples of fake site interfaces
The BBTok trojan was first detected in Latin America in 2020. Its functionality includes control of processes, keyboard and mouse, as well as the ability to manipulate the contents of the clipboard. Check Point researchers discovered the latest version of the Trojan by analyzing the attackers server resources.
The study uncovered a database of victims of the BBTok Trojan in Mexico, containing more than 150 records with information about victims. This confirms the success of the malicious operation, which apparently continues.
Recall that in August, Trend Micro researchers discovered a new banking Trojan called MMRat, targeting Android users in Southeast Asia. MMRat is distributed through phishing sites disguised as official app stores. To improve performance when transmitting large amounts of data, the Trojan uses a specially developed C2 protocol based on Protobuf.
It was also noted that a new banking Trojan for Android called Hook is based on another once-famous ERMAC Trojan. Experts from the NCC Group claim that the ERMAC source code was used as the basis for the Hook.

