Tomcat
Professional
- Messages
- 2,687
- Reaction score
- 1,038
- Points
- 113
Details of the attack and methods of operation of the new banking Trojan.
Brazilian banking institutions have become the target of a new campaign to distribute a special version of the remote access Trojan AllaKore for Windows called AllaSenha. The RAT Trojan is designed to steal credentials needed to access bank accounts and uses the Azure cloud platform as its C2 infrastructure.
The information security company HarfangLab described the campaign in detail in its technical analysis. The attack covers banks such as Banco do Brasil, Bradesco, Banco Safra, Caixa Economica Federal, Itaú Unibanco, Sicoob and Sicredi. It is assumed that attackers use phishing messages with malicious links for initial access.
In general, the infection chain looks like this:
It is worth noting that the DLL library is extracted from one of the domain names created using the Domain generation algorithm (DGA). The generated hostnames correspond to those associated with the Microsoft Azure Functions service, a serverless infrastructure that in this case allows operators to easily deploy and manage intermediate infrastructure.
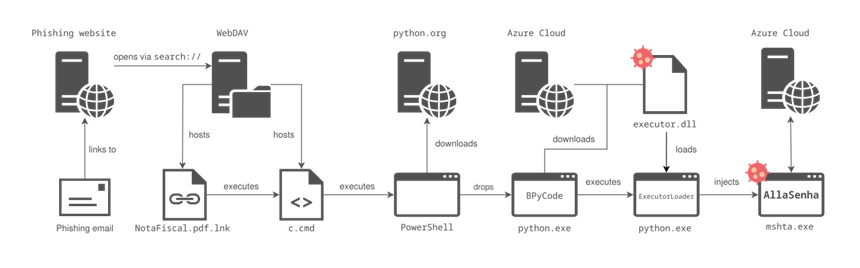
AllaSenha infection chain
In addition to stealing online banking credentials from web browsers, AllaSenha can display overlay windows to capture two-factor authentication (2FA) codes and even trick the victim into scanning a QR code to approve a fraudulent transaction initiated by the attackers.
HarfangLab also reported that all AllaSenha samples use Access_PC_Client_dll.dll as the original file name. Such a name can be found in the KL Gorki project, a banking malware that apparently combines AllaKore and ServerSocket components.
Additional analysis of the source code associated with the initial LNK file and AllaSenha samples revealed that a Portuguese-speaking user named bert1m may have been involved in the malware development. However, there is no evidence yet that it is he who controls the tools.
Cybercriminals operating in Latin America are often particularly productive in creating such threats. Although their targets are mostly Latin Americans, attackers often compromise computers owned by companies around the world, but managed by employees or subsidiaries in Brazil.
Brazilian banking institutions have become the target of a new campaign to distribute a special version of the remote access Trojan AllaKore for Windows called AllaSenha. The RAT Trojan is designed to steal credentials needed to access bank accounts and uses the Azure cloud platform as its C2 infrastructure.
The information security company HarfangLab described the campaign in detail in its technical analysis. The attack covers banks such as Banco do Brasil, Bradesco, Banco Safra, Caixa Economica Federal, Itaú Unibanco, Sicoob and Sicredi. It is assumed that attackers use phishing messages with malicious links for initial access.
In general, the infection chain looks like this:
- The attack begins by launching a Windows LNK shortcut disguised as a PDF document hosted on a WebDAV server;
- The shortcut opens the Windows command shell, displays the dummy PDF document, and loads the "c.cmd"BAT file;
- The BAT file runs a PowerShell command that downloads the Python binary from the official website (python.org) and executes the BPyCode script;
- The BPyCode script loads and runs the dynamic library (executor.dll);
- The library runs in memory and injects the AllaSenha Trojan into a legitimate process "mshta.exe".
It is worth noting that the DLL library is extracted from one of the domain names created using the Domain generation algorithm (DGA). The generated hostnames correspond to those associated with the Microsoft Azure Functions service, a serverless infrastructure that in this case allows operators to easily deploy and manage intermediate infrastructure.

AllaSenha infection chain
In addition to stealing online banking credentials from web browsers, AllaSenha can display overlay windows to capture two-factor authentication (2FA) codes and even trick the victim into scanning a QR code to approve a fraudulent transaction initiated by the attackers.
HarfangLab also reported that all AllaSenha samples use Access_PC_Client_dll.dll as the original file name. Such a name can be found in the KL Gorki project, a banking malware that apparently combines AllaKore and ServerSocket components.
Additional analysis of the source code associated with the initial LNK file and AllaSenha samples revealed that a Portuguese-speaking user named bert1m may have been involved in the malware development. However, there is no evidence yet that it is he who controls the tools.
Cybercriminals operating in Latin America are often particularly productive in creating such threats. Although their targets are mostly Latin Americans, attackers often compromise computers owned by companies around the world, but managed by employees or subsidiaries in Brazil.

