Carding 4 Carders
Professional
- Messages
- 2,724
- Reaction score
- 1,586
- Points
- 113
What is a CDN?
A CDN is a geographically distributed network infrastructure that allows you to quickly transfer resources such as HTML, Javascript, CSS, images, and videos needed to download Internet content. Over time, the popularity of CDN providers continues to grow, and today most of the web traffic is served through their servers, including traffic from such large sites as Facebook, Netflix and Amazon.
Why do websites need a CDN?
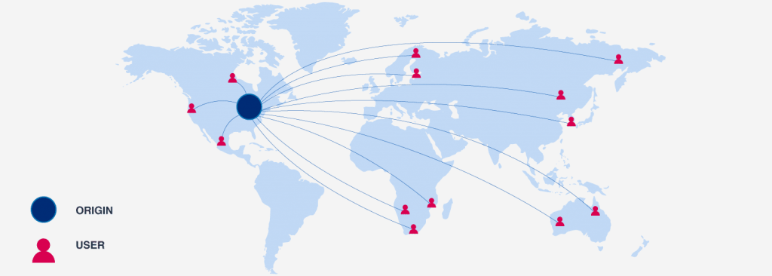
Performance is always a priority. If a website does not use a CDN to receive content, users ' computers are forced to send requests to a single server. This approach is not practical, as it can lead to a heavy load on the server, resulting in a decrease in site performance. Currently, most services use CDN because this technology helps them improve site loading speed, reduce bandwidth costs, improve security, and much more.
CDN networks offer many benefits for different types of businesses and organizations, such as:
What are the advantages of using a CDN?
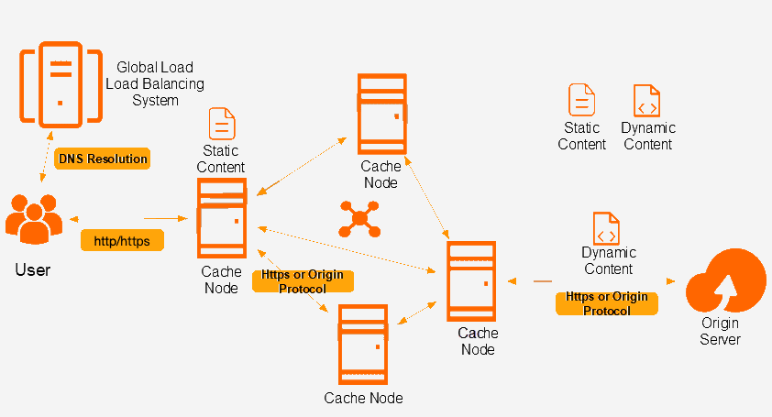
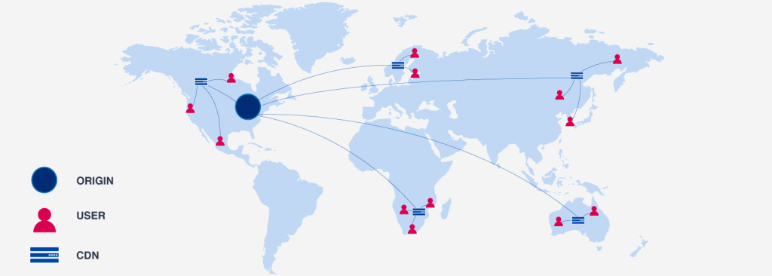
When using a CDN, all users requesting website content will receive a cached version of it from the nearest edge CDN server, so the content will load much faster and performance will improve.
Reverse CDN proxy
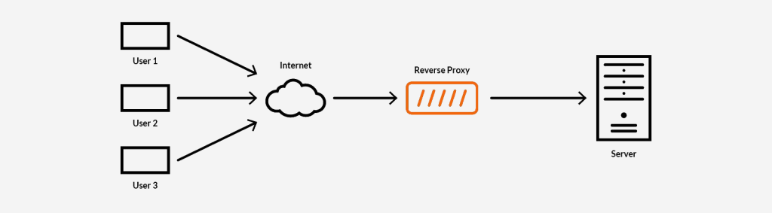
A reverse proxy server is a server that accepts a client's request and forwards it to an internal server. This is an intermediate server between the client and the source server. A reverse CDN proxy takes this concept forward by caching responses from the source server, which are then returned to the client. This way, CDN servers can deliver content to the nearest users faster. This method is also preferred for the following reasons:
CDN and WAF security
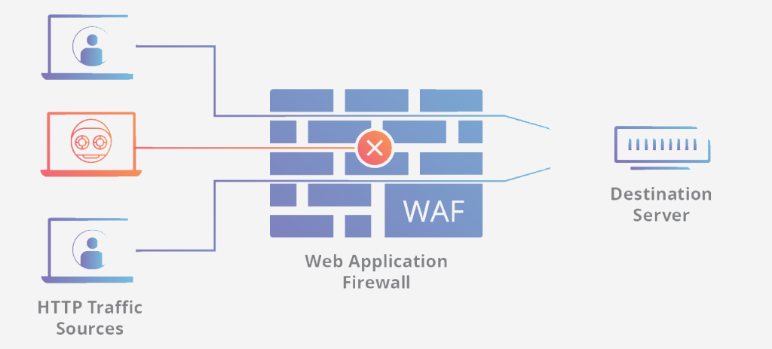
CDNs themselves cannot block bot attacks. they are vulnerable to such attacks, so site owners need to use WAF.
A WAF or web application firewall helps protect web applications by filtering and monitoring HTTP traffic between them and the Internet.
Generally, WAF protects web applications from attacks such as cross-site scripting (XSS), PHP injection, SQL injection, and others.
Source IP of websites
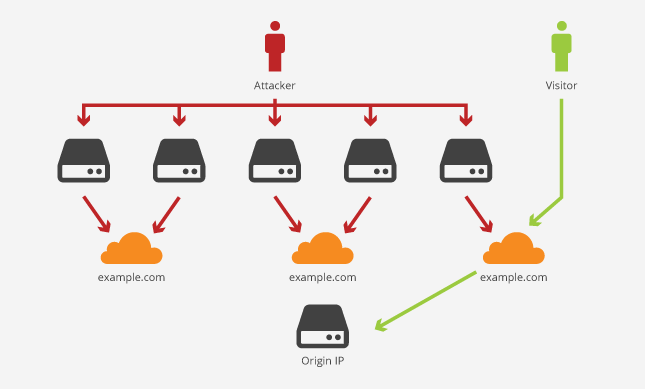
Many sites use the security features mentioned above to hide their original IP address and prevent DDOS attacks (and other malicious activities).) from intruders.
Using cloud technologies, proxies, or DNS-based services makes it difficult to find the source IP.
Why do we need the source IP?
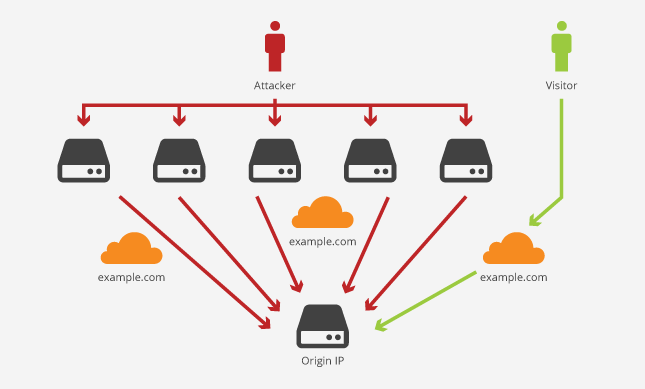
The answer is quite simple and concise; if you have the source IP address of the website, you can bypass all the security measures provided by the CDN.
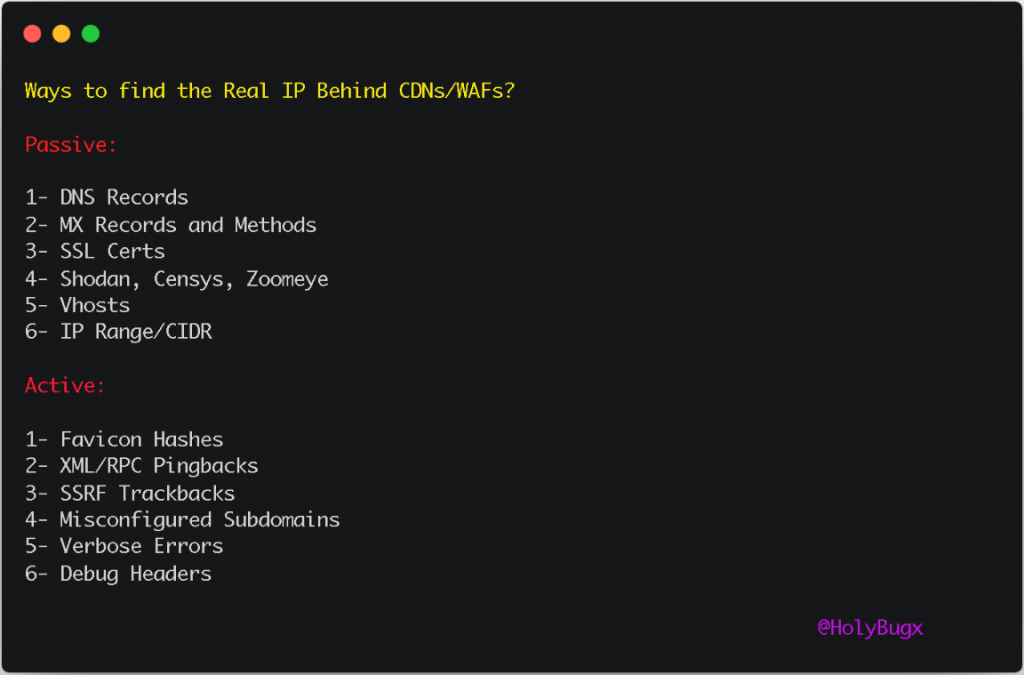
As I mentioned in my tweet, there are several ways to find the source IP address hidden behind a CDN or WAF. We will discuss most of the current methods that can be used by an attacker.
Reverse engineering
Whenever you want to get around something, put yourself in the opponent's shoes and reframe your thought process. Think like the Blue Team to try to figure out how they can be protected!
Blue Team Protection
Here is a General list of what CDN providers and Blue Team do to hide the source IP address of websites.
To disable / block direct IP access for port 80, we create a server configuration as follows:
To disable / block direct IP access for port 443, we use the following snippet in one of the server configuration blocks:
This will block all traffic to https://YOUR_IP_ADDRESS
We can circumvent this restriction with one interesting method.
This is problematic. Many CDN networks do not give out a list of their IP addresses, and even if they do, when upgrading, they may receive new IP addresses, change them, and forget to notify you about it. These whitelists must be updated regularly to avoid disrupting the site.
This name will only be known to them and their CDN provider, and they will be able to whitelist requests with this hostname.
Conclusion
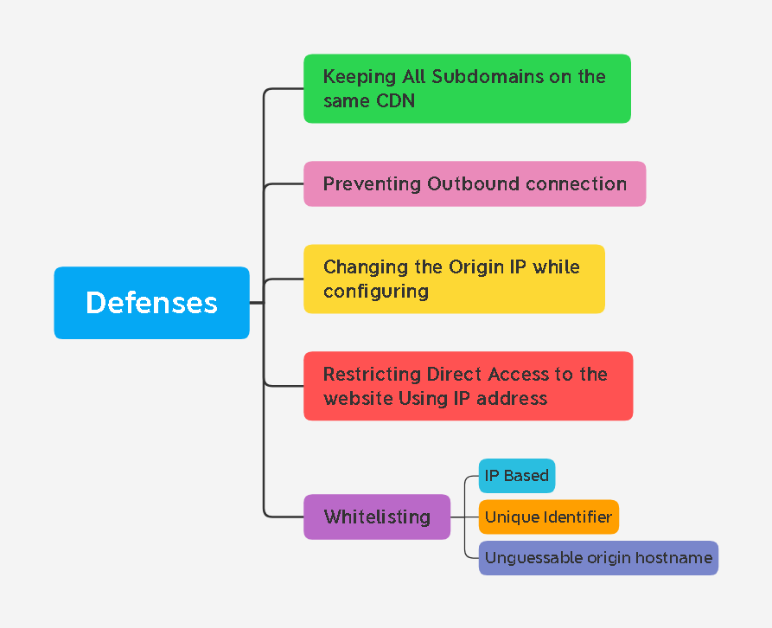
Back to the attacker's side
I described a few basic ways that Blue Team uses to protect its own web services from potential attacks. Based on their security concept, I have prepared a Mindmap of what we will do as attackers, trying to bypass their defenses and find the source IP of the Web server.
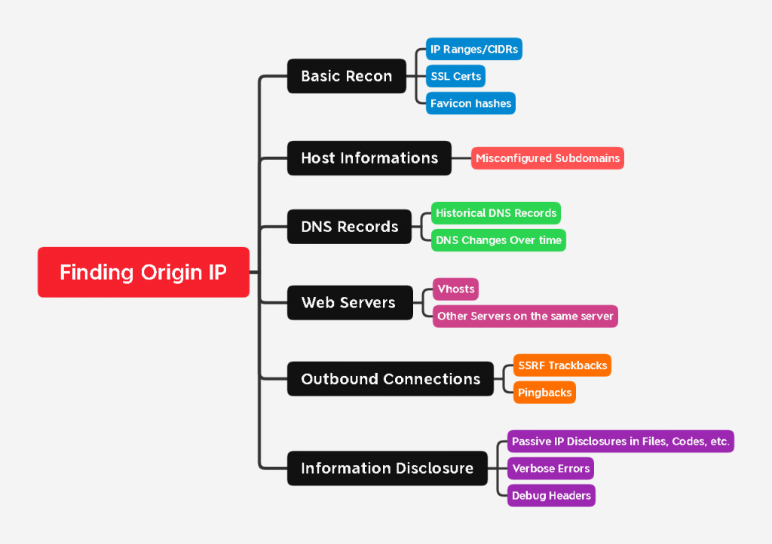
Above is a diagram with the methods that we should try when testing a site for IP address leaks. Let's go deeper into this.
Recon

https://medium.com/bugbountywriteup/guide-to-basic-recon-bug-bounties-recon-728c5242a115
The most important part is basic intelligence. It is necessary to get as much primary information about the goal as possible. Our goal is to find useful information, such as:
All about DNS records
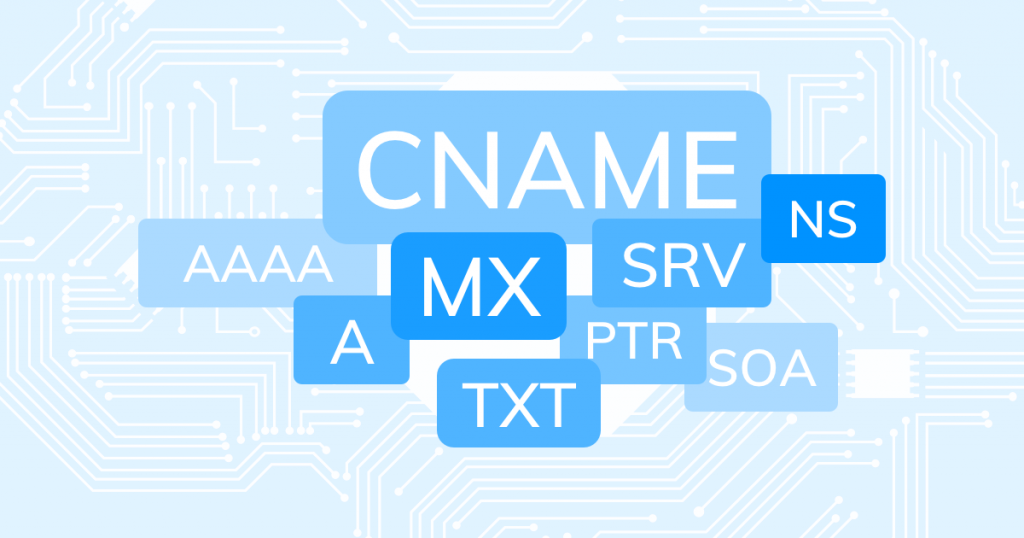
DNS records are a set of places that store information about matching the name and service information of the server. An archive of such records will most likely contain the source IP address of the website using the CDN.
As I mentioned earlier, there is a possibility that some websites have incorrectly configured DNS records, from which we can get useful information.
1 - SecurityTrails

SecurityTrails allows you to view complete current and archived data for any Internet resources. History of IP and DNS, domain, SSL, and open ports.
We are going to perform a simple query for our target to see its DNS records, as they will let us know A, AAAA, MX, NS, SOA, and TXT.
It can be convenient to find out the real IP address of the server when the website was running directly on the server's IP address and then was moved to the CDN.
Then we click on "Historical Data" to view useful information about our goal.
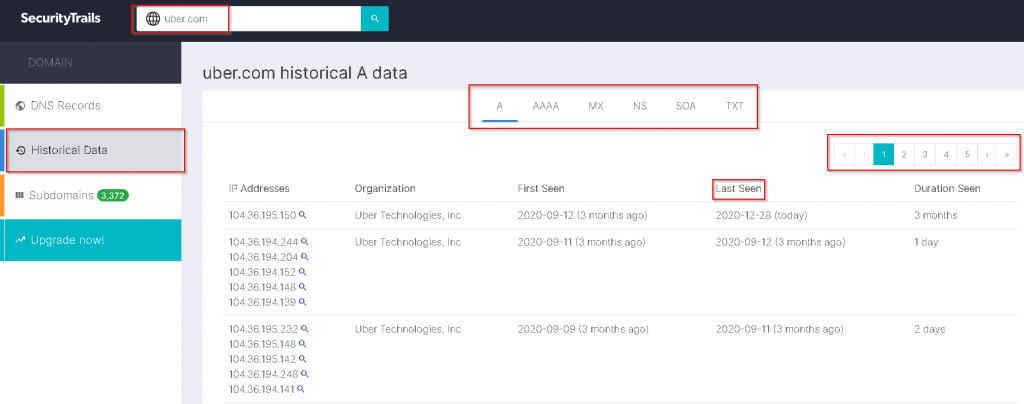
None of the DNS records should contain any mention of the source IP address. Carefully review all SPF and TXT records.
Simple A, AAA, CNAME, or MX records can serve as the source IP.
2 - Dig
You can use the dig utility to make a few simple queries and find out if our target uses the services of CDN providers such as Cloudflare.
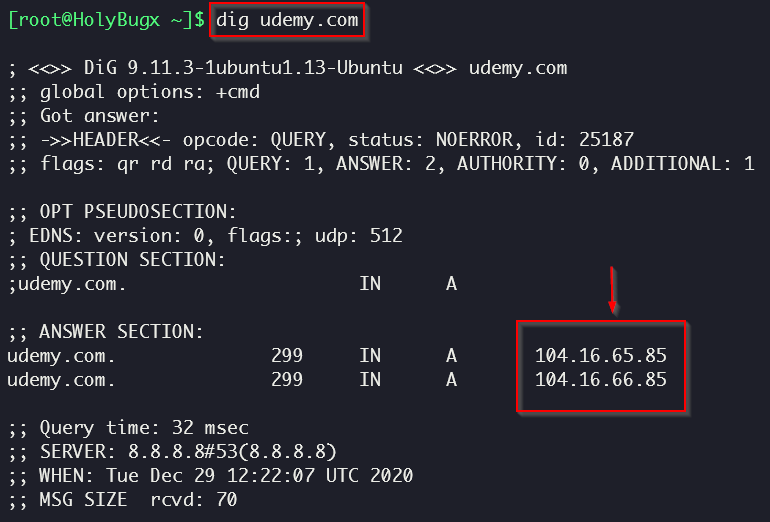
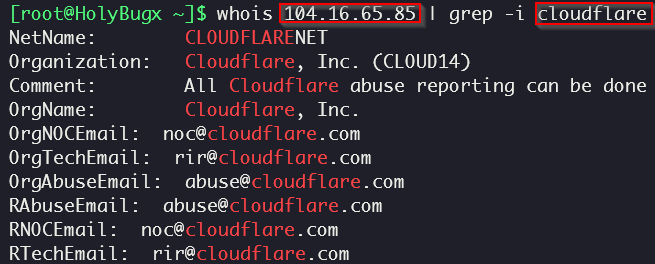
This IP address range belongs to Cloudflare. To verify this, we can use whois for the a-record IP address that we found:
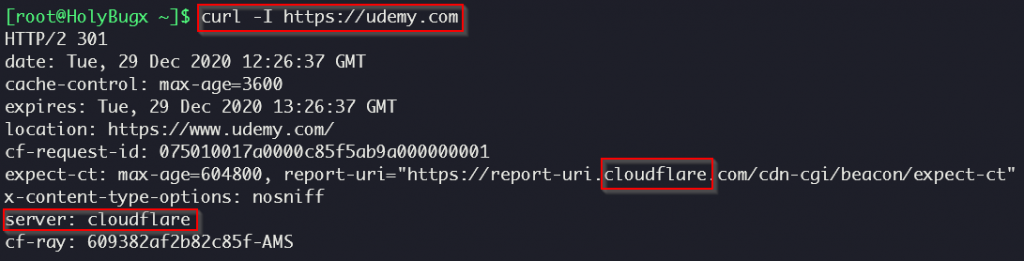
In addition, there is another way to find out whether a goal is hidden behind Cloudflare or not, using curl:
All about MX records
MX records are one of the most popular methods, as they often give the source address. If the mail server is hosted on the same IP address as the web server, an attacker may try to find it in the incoming mail message.
1 - Email Headers and password reset
If the mail server is hosted on the same IP address as the web server, another interesting option we have is to use the "Reset password" function to get an email, possibly containing the IP address of the source server.
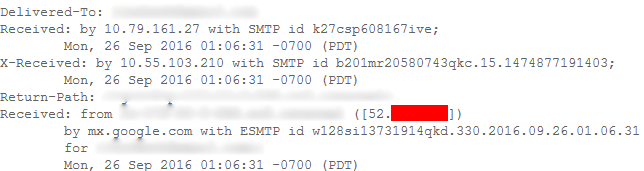
Please note that you should investigate all the IP addresses that you see in the received email and try accessing them manually to find out if they are the source IP addresses of the server. Sometimes the value of the "Return-Path" Directive can be useful.
2 - Outgoing email
There is another interesting method that you can use: sending an email to a non-existent email address "non-existent@target.com" will result in a failure; since such a user will not exist, delivery will fail, and we will be able to get back a notification about this, containing the original IP address of the server.
Detecting virtual hosts
Once you have the IP addresses of the web servers in your hands, you should find out if the target domain on these servers is configured as a virtual host.
To detect virtual hosts, I suggest several specially designed utilities for this purpose:
Invalid security configuration

Incorrect configuration can be easily exploited. For example, if the url of the uploaded content points to an IP address that is not part of the CDN, it is likely to be the real IP address of the server.
IoT search engines

Internet of things search engines are our best friends when it comes to basic goal intelligence. There are several Internet of things search engines that we can ask for useful information about our goal.
1 - Censys

Censys is a platform that helps information security professionals discover devices that are accessible from the Internet. With Censys, you can find valuable information such as:
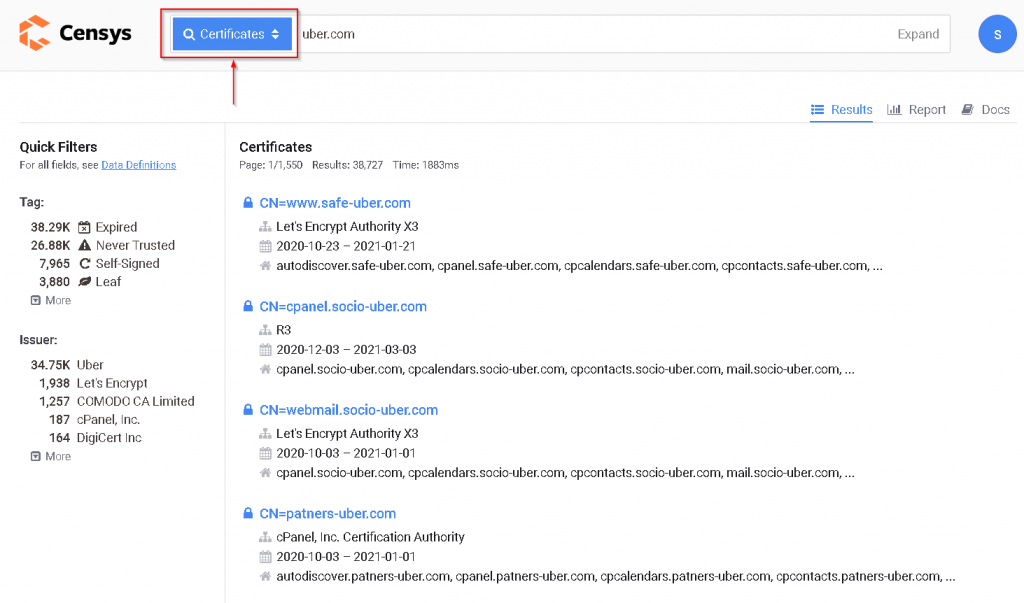
Another method that can be used is certificate - based search. Just select "Certificates" in the blue panel and find your target.
Now open each result to display detailed information, and in the "Overview" menu on the right, select " IPv4 Hosts»:
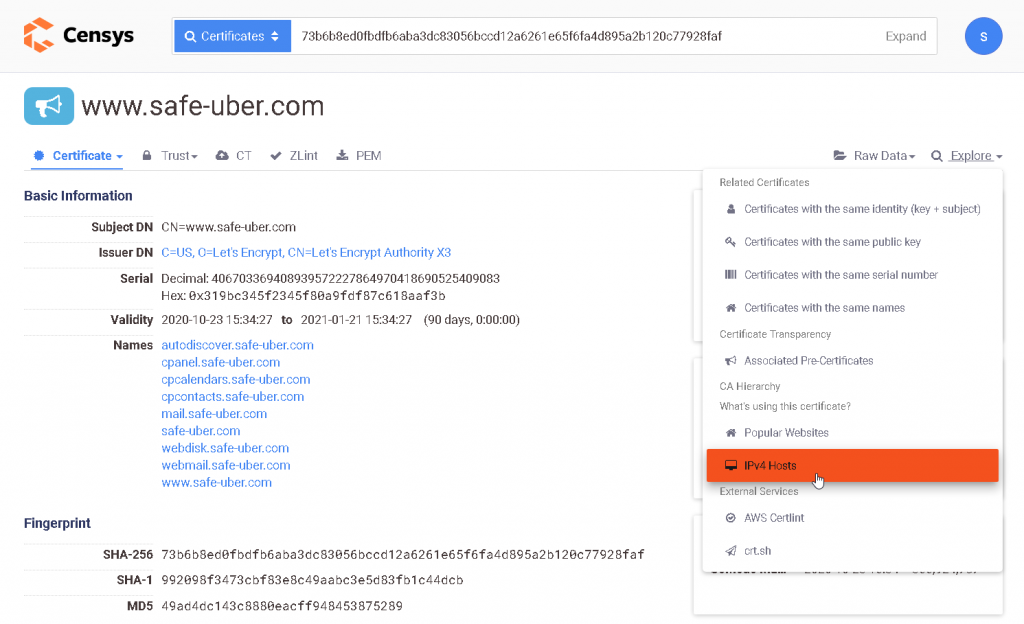
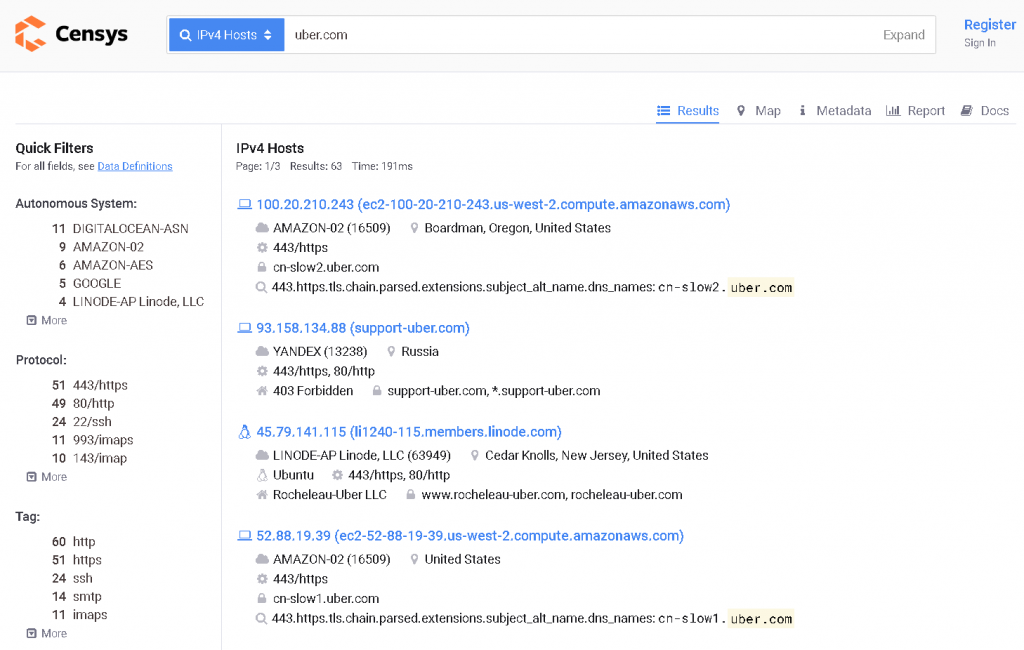
To clearly show you how Censys can help you find the source IP, I'll leave a screenshot from a site search I've been working on recently, and with a simple IPv4 query, I found the IP address behind the CDN:
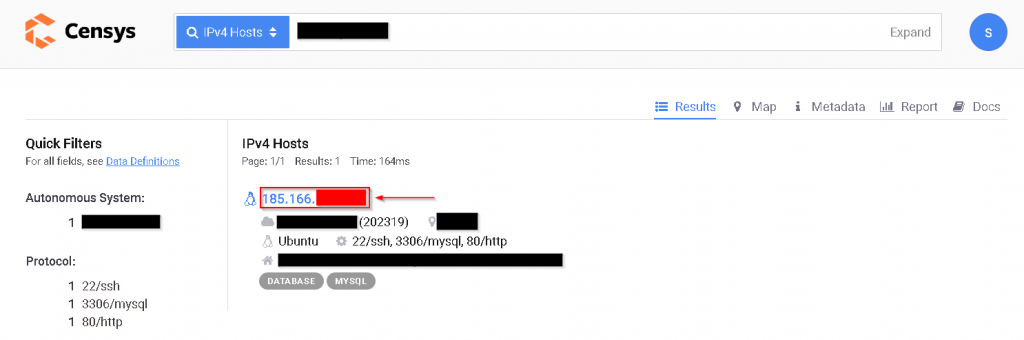
2 - Shodan

Shodan is another Internet of things search engine. It may be useful for security researchers to find information about the target being attacked.
There's a lot to look for in Shodan, so I strongly recommend that you check out the filters guide. For this article, we can simply search the domain and find the IP addresses.
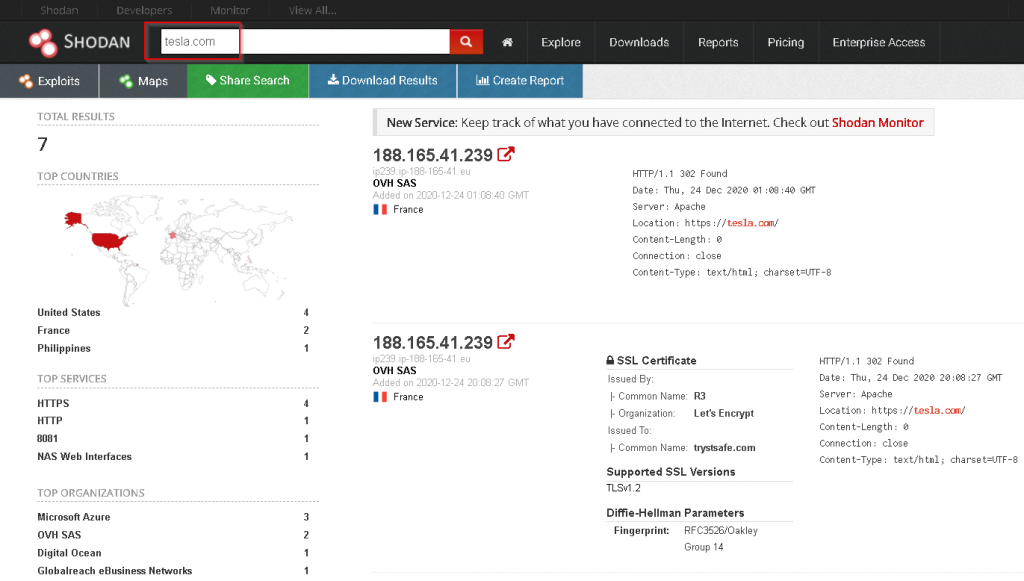
Using Shodan, you can use various filters:
3 - Zoomeye

ZoomEye is another IoT search engine that you can use to discover the most popular IoT applications:
Direct access to the website using an IP address

I mentioned this earlier
Another interesting option that Blue Team has in its Arsenal is to restrict access to users who are trying to access the website by IP. This means that the website is loaded only when the domain name is specified.
We can circumvent this restriction with one interesting method.
Let's think outside the box. What if we scan the IP address range of our target CDN provider, and then do something magical with Curl?
To find a range of IP addresses, we can perform DNS Bruteforcing, so find a range of IP addresses, and then use the following command:
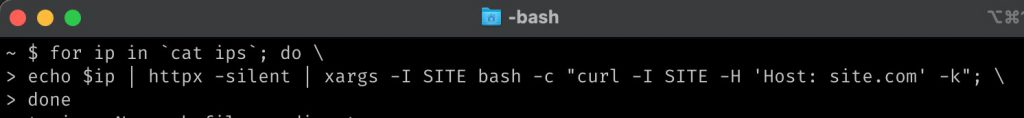
In this way, we scan the target's IP address range. Then we find the "live" addresses using Httpx. Then we use curl to provide the Host header containing the target domain, thus bypassing all restrictions.
Time to get creative: Favicon hashes

Favicons are sometimes very useful to find interesting information about the technologies that the site uses.
Shodan allows you to search for the favicon hash over http.favicon.hash. The hash is MurmurHash3 of the Favicon content in base64.
A Python3 script for generating a hash:
Check out the following blog post for a deeper dive: Asm0d3us - Favicon hashes
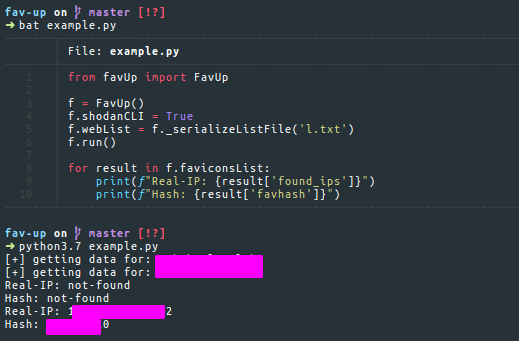
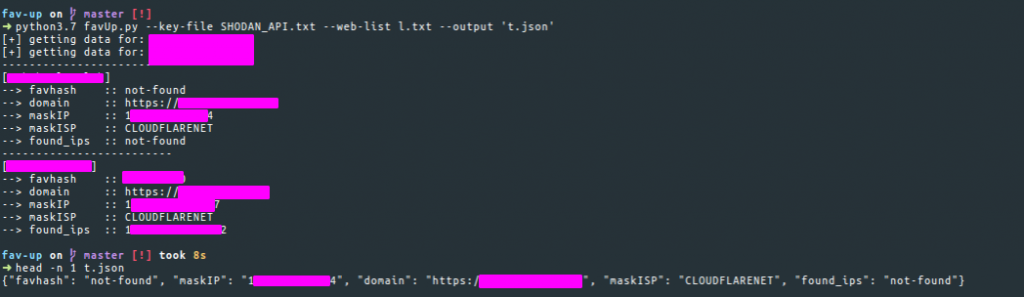
Another useful tool that you can use is Fav-Up from pielco11. Using this utility, you can find the real IP address with a Favicon and using Shodan.
XML-RPC Pingback
XML-RPC allows site administrators to remotely manage content using XML queries.
Pingback is a method of notifying intellectual property authors when someone links to their content. When site A takes content from site B and mentions it as a source, a link check is performed, after which site B notifies site A that it is aware of the mention. This is a Pingback.
You can easily check its functionality by contacting <url> https://www.target.com/xmlrpc.php. You should get the following:
The XML-RPC server accepts only POST requests.
You can also use XML-RPC Validator.
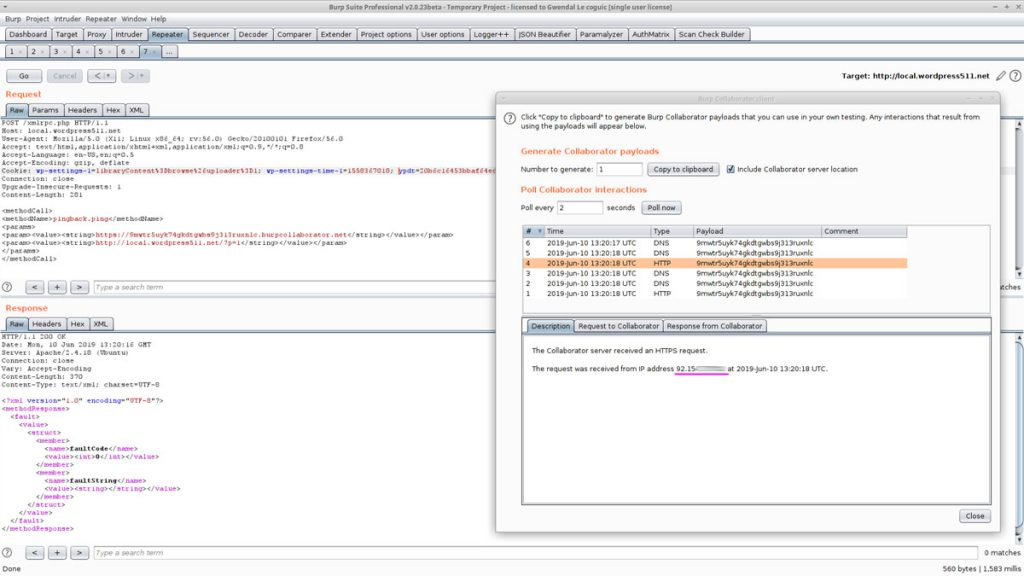
According to The WordPress XML-RPC Pingback API, functions accept 2 parameters sourceUri and targetUri. Here's what it looks like in Burp Suite:
Closing remarks
Many thanks to all readers for such support! I tried my best to write an article that could help all of you understand the CDN process, the Blue Team and Red Team approaches. So that you, knowing how they work, can both protect and test servers for leaks of source IP addresses.
A CDN is a geographically distributed network infrastructure that allows you to quickly transfer resources such as HTML, Javascript, CSS, images, and videos needed to download Internet content. Over time, the popularity of CDN providers continues to grow, and today most of the web traffic is served through their servers, including traffic from such large sites as Facebook, Netflix and Amazon.
Why do websites need a CDN?

Performance is always a priority. If a website does not use a CDN to receive content, users ' computers are forced to send requests to a single server. This approach is not practical, as it can lead to a heavy load on the server, resulting in a decrease in site performance. Currently, most services use CDN because this technology helps them improve site loading speed, reduce bandwidth costs, improve security, and much more.
CDN networks offer many benefits for different types of businesses and organizations, such as:
- E-Commerce
- Government
- Finance
- Mass media / Publishers
- Mobile apps
- Technologies and SaaS
What are the advantages of using a CDN?

- Faster operation and shorter response time.
- Reduce bandwidth costs.
- Increased security.
- SEO benefits
- Scalability
- Best conversion rate
- Reliability
- Etc.

When using a CDN, all users requesting website content will receive a cached version of it from the nearest edge CDN server, so the content will load much faster and performance will improve.
Reverse CDN proxy

A reverse proxy server is a server that accepts a client's request and forwards it to an internal server. This is an intermediate server between the client and the source server. A reverse CDN proxy takes this concept forward by caching responses from the source server, which are then returned to the client. This way, CDN servers can deliver content to the nearest users faster. This method is also preferred for the following reasons:
- Load balancing and scalability
- Increased security and reliability
CDN and WAF security

CDNs themselves cannot block bot attacks. they are vulnerable to such attacks, so site owners need to use WAF.
A WAF or web application firewall helps protect web applications by filtering and monitoring HTTP traffic between them and the Internet.
Generally, WAF protects web applications from attacks such as cross-site scripting (XSS), PHP injection, SQL injection, and others.
Source IP of websites

Many sites use the security features mentioned above to hide their original IP address and prevent DDOS attacks (and other malicious activities).) from intruders.
Using cloud technologies, proxies, or DNS-based services makes it difficult to find the source IP.
Why do we need the source IP?

The answer is quite simple and concise; if you have the source IP address of the website, you can bypass all the security measures provided by the CDN.
How to find out the source IP address of the site

As I mentioned in my tweet, there are several ways to find the source IP address hidden behind a CDN or WAF. We will discuss most of the current methods that can be used by an attacker.
Reverse engineering
Whenever you want to get around something, put yourself in the opponent's shoes and reframe your thought process. Think like the Blue Team to try to figure out how they can be protected!
Blue Team Protection
Here is a General list of what CDN providers and Blue Team do to hide the source IP address of websites.
- Hiding all subdomains under a single CDN
- Banning connections based on user actions
- Hiding the source IP address when configuring a CDN
- Prohibition of direct access to the site by IP address
To disable / block direct IP access for port 80, we create a server configuration as follows:
Code:
server {
listen 80 default_server;
server_name _;
return 404;
}To disable / block direct IP access for port 443, we use the following snippet in one of the server configuration blocks:
Code:
if ($host != "example.com") {
return 404;
}
Example:
server {
listen 443 ssl;
server_name example.com
ssl_certificate /etc/nginx/ssl/example.com.crt;
ssl_certificate_key /etc/nginx/ssl/example.com.key;
if ($host != "example.com") {
return 404;
}
}This will block all traffic to https://YOUR_IP_ADDRESS
We can circumvent this restriction with one interesting method.
- Whitelists
- Option A. Whitelisting IP addresses
This is problematic. Many CDN networks do not give out a list of their IP addresses, and even if they do, when upgrading, they may receive new IP addresses, change them, and forget to notify you about it. These whitelists must be updated regularly to avoid disrupting the site.
- Option B. Adding a unique identifier from the request to the whitelist
- Option C: unknown source host name
This name will only be known to them and their CDN provider, and they will be able to whitelist requests with this hostname.
Conclusion

Back to the attacker's side
I described a few basic ways that Blue Team uses to protect its own web services from potential attacks. Based on their security concept, I have prepared a Mindmap of what we will do as attackers, trying to bypass their defenses and find the source IP of the Web server.

Above is a diagram with the methods that we should try when testing a site for IP address leaks. Let's go deeper into this.
Recon

https://medium.com/bugbountywriteup/guide-to-basic-recon-bug-bounties-recon-728c5242a115
The most important part is basic intelligence. It is necessary to get as much primary information about the goal as possible. Our goal is to find useful information, such as:
- IP/CIDRs ranges
- Host-related information
- DNS records
- Web servers
- Vhosts
- Services running on the server (for example, mail clients)
- Vulnerabilities
All about DNS records

DNS records are a set of places that store information about matching the name and service information of the server. An archive of such records will most likely contain the source IP address of the website using the CDN.
As I mentioned earlier, there is a possibility that some websites have incorrectly configured DNS records, from which we can get useful information.
1 - SecurityTrails

SecurityTrails allows you to view complete current and archived data for any Internet resources. History of IP and DNS, domain, SSL, and open ports.
We are going to perform a simple query for our target to see its DNS records, as they will let us know A, AAAA, MX, NS, SOA, and TXT.
It can be convenient to find out the real IP address of the server when the website was running directly on the server's IP address and then was moved to the CDN.

Then we click on "Historical Data" to view useful information about our goal.

None of the DNS records should contain any mention of the source IP address. Carefully review all SPF and TXT records.
Simple A, AAA, CNAME, or MX records can serve as the source IP.
2 - Dig
You can use the dig utility to make a few simple queries and find out if our target uses the services of CDN providers such as Cloudflare.

This IP address range belongs to Cloudflare. To verify this, we can use whois for the a-record IP address that we found:

In addition, there is another way to find out whether a goal is hidden behind Cloudflare or not, using curl:

All about MX records
MX records are one of the most popular methods, as they often give the source address. If the mail server is hosted on the same IP address as the web server, an attacker may try to find it in the incoming mail message.
1 - Email Headers and password reset
If the mail server is hosted on the same IP address as the web server, another interesting option we have is to use the "Reset password" function to get an email, possibly containing the IP address of the source server.

Please note that you should investigate all the IP addresses that you see in the received email and try accessing them manually to find out if they are the source IP addresses of the server. Sometimes the value of the "Return-Path" Directive can be useful.
2 - Outgoing email
There is another interesting method that you can use: sending an email to a non-existent email address "non-existent@target.com" will result in a failure; since such a user will not exist, delivery will fail, and we will be able to get back a notification about this, containing the original IP address of the server.
Detecting virtual hosts

Once you have the IP addresses of the web servers in your hands, you should find out if the target domain on these servers is configured as a virtual host.
To detect virtual hosts, I suggest several specially designed utilities for this purpose:
- Vhostscan by Codingo
- Virtual-host-discovery by Jobertabma
- Gobuster by OJ
Invalid security configuration

Incorrect configuration can be easily exploited. For example, if the url of the uploaded content points to an IP address that is not part of the CDN, it is likely to be the real IP address of the server.
IoT search engines

Internet of things search engines are our best friends when it comes to basic goal intelligence. There are several Internet of things search engines that we can ask for useful information about our goal.
1 - Censys

Censys is a platform that helps information security professionals discover devices that are accessible from the Internet. With Censys, you can find valuable information such as:
- IP address
- Open ports
- SSL certificates
- Hosting providers
- etc.

Another method that can be used is certificate - based search. Just select "Certificates" in the blue panel and find your target.

Now open each result to display detailed information, and in the "Overview" menu on the right, select " IPv4 Hosts»:

To clearly show you how Censys can help you find the source IP, I'll leave a screenshot from a site search I've been working on recently, and with a simple IPv4 query, I found the IP address behind the CDN:

2 - Shodan

Shodan is another Internet of things search engine. It may be useful for security researchers to find information about the target being attacked.
There's a lot to look for in Shodan, so I strongly recommend that you check out the filters guide. For this article, we can simply search the domain and find the IP addresses.

Using Shodan, you can use various filters:
- Organizations
- ASN
- Favicon Hashes
- SSL certificates
- etc.
3 - Zoomeye

ZoomEye is another IoT search engine that you can use to discover the most popular IoT applications:
- Web server
- IP and ports
- Headers and status codes
- Vulnerabilities
- etc.
Direct access to the website using an IP address

I mentioned this earlier
Another interesting option that Blue Team has in its Arsenal is to restrict access to users who are trying to access the website by IP. This means that the website is loaded only when the domain name is specified.
We can circumvent this restriction with one interesting method.
Let's think outside the box. What if we scan the IP address range of our target CDN provider, and then do something magical with Curl?
To find a range of IP addresses, we can perform DNS Bruteforcing, so find a range of IP addresses, and then use the following command:

In this way, we scan the target's IP address range. Then we find the "live" addresses using Httpx. Then we use curl to provide the Host header containing the target domain, thus bypassing all restrictions.
Time to get creative: Favicon hashes

Favicons are sometimes very useful to find interesting information about the technologies that the site uses.
Shodan allows you to search for the favicon hash over http.favicon.hash. The hash is MurmurHash3 of the Favicon content in base64.
A Python3 script for generating a hash:
Code:
import mmh3
import requests
import codecs
response = requests.get('https://<website>/<favicon path>')
favicon = codecs.encode(response.content, 'base64')
hash = mmh3.hash(favicon)
print(hash)Check out the following blog post for a deeper dive: Asm0d3us - Favicon hashes
Another useful tool that you can use is Fav-Up from pielco11. Using this utility, you can find the real IP address with a Favicon and using Shodan.


XML-RPC Pingback

XML-RPC allows site administrators to remotely manage content using XML queries.
Pingback is a method of notifying intellectual property authors when someone links to their content. When site A takes content from site B and mentions it as a source, a link check is performed, after which site B notifies site A that it is aware of the mention. This is a Pingback.
You can easily check its functionality by contacting <url> https://www.target.com/xmlrpc.php. You should get the following:
The XML-RPC server accepts only POST requests.
You can also use XML-RPC Validator.
According to The WordPress XML-RPC Pingback API, functions accept 2 parameters sourceUri and targetUri. Here's what it looks like in Burp Suite:

Closing remarks
Many thanks to all readers for such support! I tried my best to write an article that could help all of you understand the CDN process, the Blue Team and Red Team approaches. So that you, knowing how they work, can both protect and test servers for leaks of source IP addresses.

