Tomcat
Professional
- Messages
- 2,687
- Reaction score
- 1,036
- Points
- 113
How old vulnerabilities are used to install a new web shell.
Akamai report an increase in cyber attacks on vulnerable instances of the Chinese PHP framework ThinkPHP in order to install the Dama web shell.
Dama allows hackers to continue exploiting compromised systems, turning them into part of the infrastructure to avoid detection. The first signs of activity were recorded in October 2023. According to Akamai, the scale of attacks has increased significantly recently.
Attackers exploit two old vulnerabilities in ThinkPHP:
Attackers use vulnerabilities to execute remote code, affecting CMS systems. Hackers upload the file "public.txt", disguised as a Dama web wrapper and saved as "roeter.php". The file is downloaded from hacked servers in Hong Kong, giving cybercriminals remote control after authenticating with the password "admin". Akamai reports that the servers distributing this file are also infected with Dama, turning them into nodes of the attackers infrastructure.
Dama has extensive features that allow you to:
Despite all its abilities, Dama lacks a command-line interface, which limits the "practicality" of the web shell.
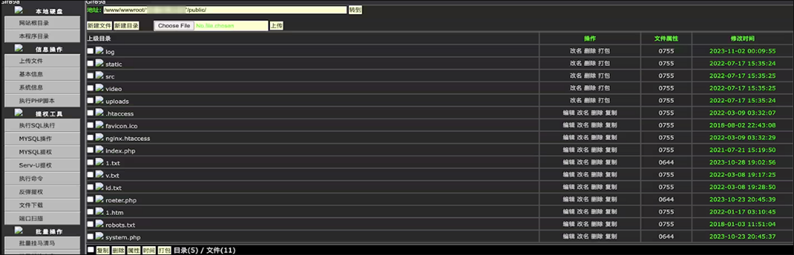
Dama Interface
Exploiting old vulnerabilities highlights the need for effective vulnerability management. Attackers exploit long-patched vulnerabilities, so timely software updates are critical. Organizations are advised to upgrade to the latest version of ThinkPHP-8.0, which is protected from known vulnerabilities. Akamai notes that the scope of the campaign is wide and affects systems that do not use ThinkPHP, which indicates opportunistic motives of attackers.
Note that CVE-2018-20062 was already used in attacks on ThinkPHP in 2019, when exploits were discovered that allowed the introduction of various malware-from Trojans for Windows-based PCs and IoT devices to cryptominers.
Akamai report an increase in cyber attacks on vulnerable instances of the Chinese PHP framework ThinkPHP in order to install the Dama web shell.
Dama allows hackers to continue exploiting compromised systems, turning them into part of the infrastructure to avoid detection. The first signs of activity were recorded in October 2023. According to Akamai, the scale of attacks has increased significantly recently.
Attackers exploit two old vulnerabilities in ThinkPHP:
- CVE-2018-20062 (CVSS score: 9.8) is related to NoneCMS 1.3 and allows a remote attacker to execute arbitrary PHP code. Fixed in December 2018.
- CVE-2019-9082 (CVSS score: 8.8) affects ThinkPHP versions 3.2.4 and older used in Open Source BMS 1.1.1 and allows remote code execution (RCE). Fixed in February 2019.
Attackers use vulnerabilities to execute remote code, affecting CMS systems. Hackers upload the file "public.txt", disguised as a Dama web wrapper and saved as "roeter.php". The file is downloaded from hacked servers in Hong Kong, giving cybercriminals remote control after authenticating with the password "admin". Akamai reports that the servers distributing this file are also infected with Dama, turning them into nodes of the attackers infrastructure.
Dama has extensive features that allow you to:
- manage the file system on a compromised server;
- upload files;
- collect system data.
- scan network ports;
- access databases;
- bypass disabled PHP functions to execute shell commands.
Despite all its abilities, Dama lacks a command-line interface, which limits the "practicality" of the web shell.

Dama Interface
Exploiting old vulnerabilities highlights the need for effective vulnerability management. Attackers exploit long-patched vulnerabilities, so timely software updates are critical. Organizations are advised to upgrade to the latest version of ThinkPHP-8.0, which is protected from known vulnerabilities. Akamai notes that the scope of the campaign is wide and affects systems that do not use ThinkPHP, which indicates opportunistic motives of attackers.
Note that CVE-2018-20062 was already used in attacks on ThinkPHP in 2019, when exploits were discovered that allowed the introduction of various malware-from Trojans for Windows-based PCs and IoT devices to cryptominers.

