CarderPlanet
Professional
- Messages
- 2,549
- Reaction score
- 724
- Points
- 113
The management of the aerospace company hardly praised the man for the mistake made.
North Korean hacker group Lazarus used fake jobs to break into the corporate network of an unnamed aerospace company in Spain, using a previously undocumented backdoor called LightlessCan in the attack.
As part of their long-running "Operation Dreamjob" campaign, which we have already described many times before, hackers present themselves as recruiters from large firms, allegedly offering high-paying jobs.
The victims of the attack are not chosen at all by chance. Fake recruiters look for active employees of a particular organization and apply with a fake job offer to them.
When a potential victim is interested in the offer, hackers send her a disguised malicious file. In order not to wait until the evening and not lose precious time, the victim runs this file directly from their work device, thereby inadvertently infecting the entire corporate network of the company with malware.
ESET specialists investigated one of these incidents and were able to recreate the initial stage of the attack, as well as extract components of the Lazarus toolkit.
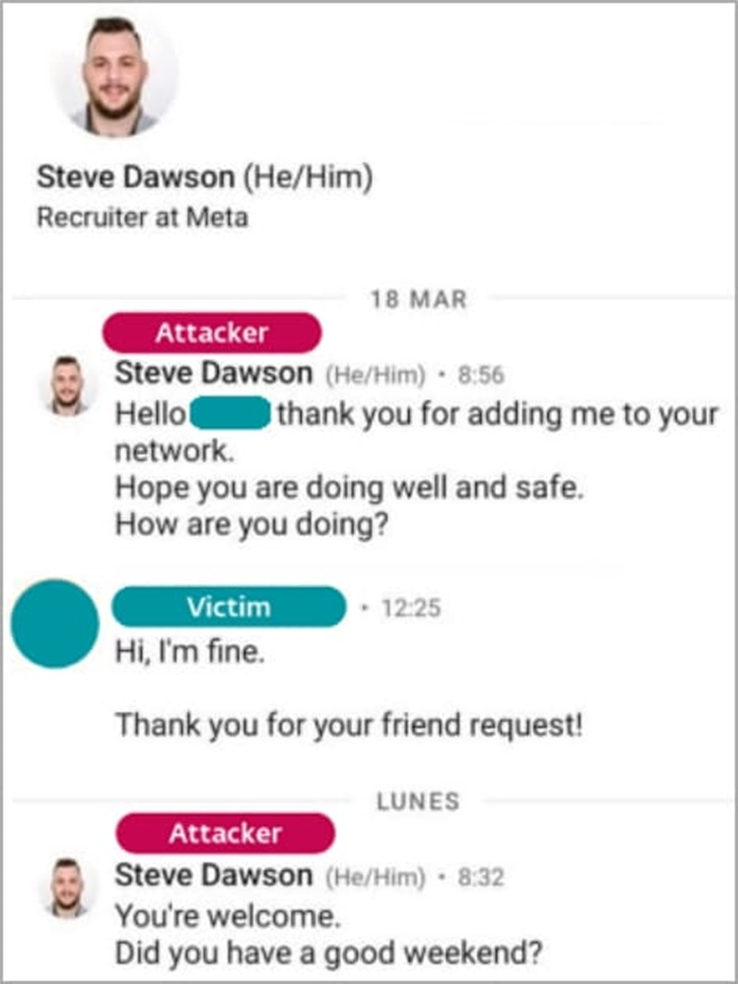
The attack began with a LinkedIn message * allegedly from a Meta recruiter * * named Steve Dawson. During the conversation, the victim was asked to download C++ programming tests provided as executable files packed in ISO containers.
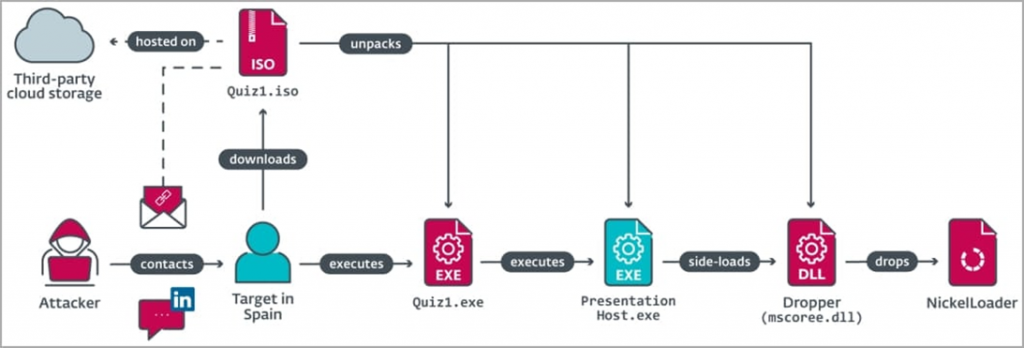
After launching a series of executable files accompanied by a chain of background operations, the NickelLoader malware loader is installed on the victim's computer, which installs two backdoors into the system at once: BlindingCan and LightlessCan.
LightlessCan is a kind of continuation of the already known BlindingCan, differing from it in a more complex code structure and advanced functionality. The version obtained from the attack on the Spanish organization supports 43 commands, although the code contains another 25 commands, the functionality of which is not yet fully implemented.
ESET also reports that one of the LightlessCan samples was encrypted and could only be decrypted using a key that depends on the target environment used. Such a security measure is necessary to prevent external access to the victim's computer, for example, by researchers or security analysts.
This data highlights that "Operation Dreamjob" is not only motivated by financial goals, such as cryptocurrency theft, but also includes cyber espionage goals.
The introduction of the new sophisticated LightlessCan malware is a worrying sign for foreign organizations that may be at risk of attacks by the North Korean Lazarus group.
North Korean hacker group Lazarus used fake jobs to break into the corporate network of an unnamed aerospace company in Spain, using a previously undocumented backdoor called LightlessCan in the attack.
As part of their long-running "Operation Dreamjob" campaign, which we have already described many times before, hackers present themselves as recruiters from large firms, allegedly offering high-paying jobs.
The victims of the attack are not chosen at all by chance. Fake recruiters look for active employees of a particular organization and apply with a fake job offer to them.
When a potential victim is interested in the offer, hackers send her a disguised malicious file. In order not to wait until the evening and not lose precious time, the victim runs this file directly from their work device, thereby inadvertently infecting the entire corporate network of the company with malware.
ESET specialists investigated one of these incidents and were able to recreate the initial stage of the attack, as well as extract components of the Lazarus toolkit.

The attack began with a LinkedIn message * allegedly from a Meta recruiter * * named Steve Dawson. During the conversation, the victim was asked to download C++ programming tests provided as executable files packed in ISO containers.
After launching a series of executable files accompanied by a chain of background operations, the NickelLoader malware loader is installed on the victim's computer, which installs two backdoors into the system at once: BlindingCan and LightlessCan.

LightlessCan is a kind of continuation of the already known BlindingCan, differing from it in a more complex code structure and advanced functionality. The version obtained from the attack on the Spanish organization supports 43 commands, although the code contains another 25 commands, the functionality of which is not yet fully implemented.
ESET also reports that one of the LightlessCan samples was encrypted and could only be decrypted using a key that depends on the target environment used. Such a security measure is necessary to prevent external access to the victim's computer, for example, by researchers or security analysts.
This data highlights that "Operation Dreamjob" is not only motivated by financial goals, such as cryptocurrency theft, but also includes cyber espionage goals.
The introduction of the new sophisticated LightlessCan malware is a worrying sign for foreign organizations that may be at risk of attacks by the North Korean Lazarus group.

