Carding 4 Carders
Professional
- Messages
- 2,728
- Reaction score
- 1,585
- Points
- 113
Learn about RowPress before it's too late.
In 2015, researchers discovered a security threat known as RowHammer that allowed sensitive data to be corrected , modified, or stolen by repeatedly accessing certain areas of DDR memory chips. Memory chip manufacturers have been actively working to develop protection against this attack.
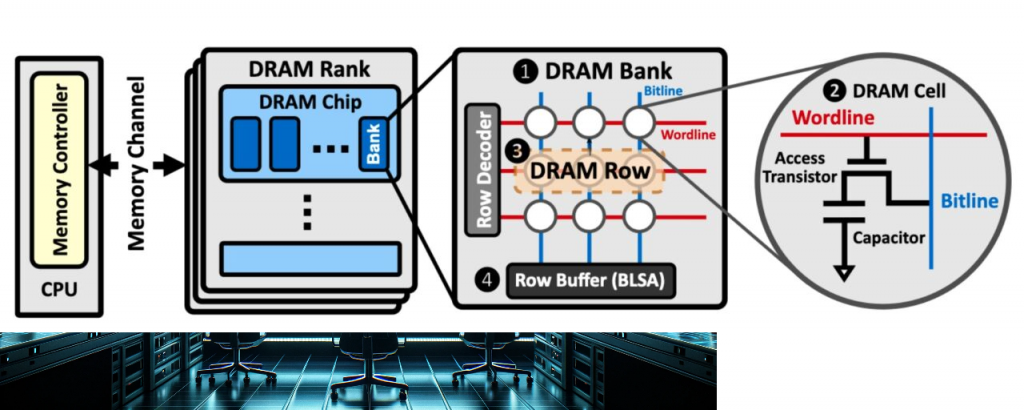
A diagram illustrating the hierarchical organization of a DRAM chip.
However, a new method has recently been developed to create the same RowHammer-induced "bitflips" even on a new generation of DDR4 chips that already had built-in RowHammer protection. This new method, called RowPress, works not by repeatedly "hitting" carefully selected areas, but by opening them for a long time.
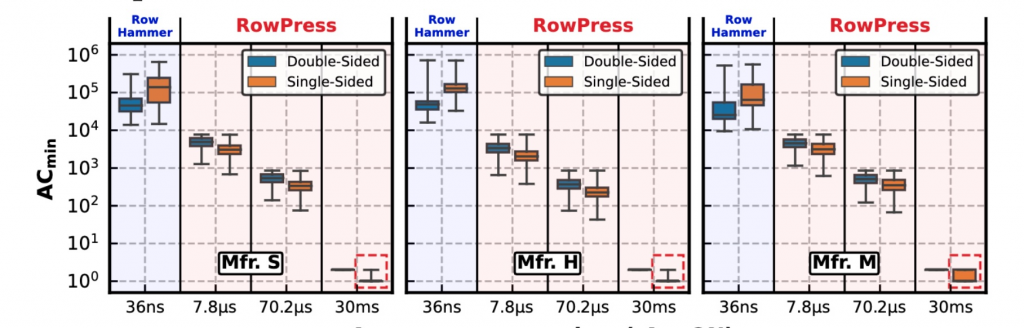
A diagram showing the standard of a regular RowHammer in three representative RowPress cases among 164 DDR4 chips from all three major manufacturers.
RowPress increases the vulnerability of DDR4 chips to read attacks, which is compounded when combined with RowHammer access. Interestingly, increasing the chip temperature also enhances this effect.
Onur Mutlu, a professor at ETH Zurich and co-author of a recently published paper, stated: "We demonstrate the concept of RowPress, which can trigger bitflips in a real system that is already protected from RowHammer. Note that this is not an attack in itself. It just shows that bitflips are possible, and there are many of them, which can easily become the basis for an attack."
The basis of DRAM (Dynamic Random Access Memory) is a storage cell. Each cell consists of a capacitor and a transistor and stores one bit of data. Bitflips have long been known as a rare phenomenon. They occur when an unexpected flow of electrons inside the gate of a transistor changes the voltage.
It is worth noting that research in the field of memory security continues, and new methods of attacks require the development of new methods of protection.
In 2015, researchers discovered a security threat known as RowHammer that allowed sensitive data to be corrected , modified, or stolen by repeatedly accessing certain areas of DDR memory chips. Memory chip manufacturers have been actively working to develop protection against this attack.

A diagram illustrating the hierarchical organization of a DRAM chip.
However, a new method has recently been developed to create the same RowHammer-induced "bitflips" even on a new generation of DDR4 chips that already had built-in RowHammer protection. This new method, called RowPress, works not by repeatedly "hitting" carefully selected areas, but by opening them for a long time.

A diagram showing the standard of a regular RowHammer in three representative RowPress cases among 164 DDR4 chips from all three major manufacturers.
RowPress increases the vulnerability of DDR4 chips to read attacks, which is compounded when combined with RowHammer access. Interestingly, increasing the chip temperature also enhances this effect.
Onur Mutlu, a professor at ETH Zurich and co-author of a recently published paper, stated: "We demonstrate the concept of RowPress, which can trigger bitflips in a real system that is already protected from RowHammer. Note that this is not an attack in itself. It just shows that bitflips are possible, and there are many of them, which can easily become the basis for an attack."
The basis of DRAM (Dynamic Random Access Memory) is a storage cell. Each cell consists of a capacitor and a transistor and stores one bit of data. Bitflips have long been known as a rare phenomenon. They occur when an unexpected flow of electrons inside the gate of a transistor changes the voltage.
It is worth noting that research in the field of memory security continues, and new methods of attacks require the development of new methods of protection.

