Man
Professional
- Messages
- 3,222
- Reaction score
- 1,199
- Points
- 113
Have you heard of such types of information attacks as Baiting, Honey Trap, Scareware, Water Holing, Quid pro Quo? In this article, we will consider them and a number of others, including various types of phishing, and also give high-profile examples of attacks and tell you about effective ways to protect yourself from them. All these actions are taken by attackers with one goal - to seize users' personal data. And first, about what unites all these types of attacks. Understanding the mechanisms of social engineering will make you much less vulnerable to this type of manipulation.
Often, attacks using social engineering tools occur in two stages. First, the scammers research the intended victim to collect the necessary background information. It is at this stage that the attacker tries to gain the victim's trust. And after successful attempts to establish "good" relations, the criminal, using various tricks, extracts confidential information from the victim (for example, passwords and IP addresses). We will now talk about different types of such tricks.

A phishing attack can also be planned in such a way that after going to a fake site, the victim will have other problems: for example, malicious spyware will be installed on the computer or the system will freeze due to a ransomware attack (we wrote about them in the previous article). In some cases, fraudsters are satisfied with obtaining the victim's credit card information or other personal data for financial gain. But it happens that phishing emails are sent to obtain employee registration information or other data for further extended attack on a specific company.
There are several types of phishing cyber attacks. These include targeted, voice, SMS phishing, as well as "whaling" (the description will make it clear why it is called that) and clone phishing.
An example that is partly related to “whaling” phishing: in March 2019, the CEO of a British energy company received a call from a man who sounded exactly like his president. The caller was so convincing that the CEO transferred $243,000 to a “Hungarian supplier” in a bank account that actually belonged to the fraudster.
Some attackers focus on sick or elderly people. And in such attacks, they shamelessly exploit the unstable physical and/or mental state of the victim to convince the person that he must hand over his personal information in order to receive help. In such cases, the criminals use the promise of financial assistance as bait, but only after they are given personal information. Another common type of vishing attack: criminals report that something has allegedly happened to the victim's loved ones, and demand a quick transfer of money to solve the problem.
The largest attack of this type, not only phishing but also using social engineering in general, was carried out by Lithuanian citizen Evaldas Rimasauskas against two of the world's largest web corporations: Google and Facebook. Rimasauskas and his team created a fake company and posed as a computer manufacturer that worked with Google and Facebook. Rimasauskas also opened bank accounts in the company's name. As a result, the web giants suffered a total loss of more than $120 million.
In another high-profile case, Chinese aircraft parts maker FACC lost nearly $60 million in a scam in which scammers posed as high-ranking executives and tricked employees into transferring funds to them. After the incident, FACC spent millions more suing its CEO and CFO for damages. The company claimed that the executives had failed to implement proper internal security controls, but FACC's suit was dismissed.
In this way, scammers copy the corporate email format, creating an almost identical sample: only this email is sent not from the real one, but from a similar address. The body of the email looks the same as in the emails that the user has already received from this organization, but the links in the email are replaced with malicious ones. Inventive criminals can even explain to the victim why they are receiving the “same” message again.
In fact, these emails have only one goal: “social hackers” try to trick the recipient into revealing personal or financial information by clicking on a link in the email, which redirects the user to a seemingly similar but criminally controlled website designed to steal personal information.
A recent example of clone phishing: In January 2022, a large-scale attack was carried out to steal credentials from the Office 365 service. The attackers were able to successfully imitate messages from the US Department of Labor (DoL). This scam is a clear example of how effective phishing attempts can be. In this case, addresses with the real dol.gov domain were replaced with addresses from the dol-gov.com and dol-gov.us domains that the scammers had previously purchased. Moreover, the phishing emails successfully passed the security gateways of the target organizations. The emails used official DoL attributes and were professionally written, inviting recipients to bid on a government project. The bidding instructions were included in a three-page PDF file with an embedded “Bid” button. When victims clicked on the link, they were redirected to a phishing site that looked identical to the real DoL site. The fake auction site prompted users to enter their Office 365 credentials and even displayed an error message after the first entry. This ensured that the victim would enter their credentials twice, reducing the likelihood of an incorrect entry. This situation would not have occurred if the target organization had better email security measures in place.
Hackers study the vulnerabilities of the "target group" sites and inject malware, usually hidden in JavaScript or directly in the HTML code. This malicious code redirects the "loot" from the target group sites to another site that has malware or advertising installed. The viruses are now ready to infect computers as soon as victims visit the compromised sites.

But these tips are intended primarily for company management and IT specialists, but what should users do, including those with high access levels, who also often lose their vigilance? We will also give them some tips that will, with some probability, help prevent the creation of vulnerabilities.
And finally, a telling statistic: the US Cybercrime Report for 2019 states that phishing attacks caused damage to individuals and businesses in the amount of about $58 million. In addition, about 115 thousand people or organizations fell victim to these attacks. And to adequately assess these numbers and the scale of the threat, it should be borne in mind that this report concerns only the USA.
What is social engineering and how does it work
Social engineering is a method of manipulating people in order to obtain confidential information from them. The information that criminals are looking for can be different, but most often it is bank details, as well as passwords for accounts. In addition, criminals can try to gain access to the victim's computer in order to install malicious software there, which helps to extract any information. And here, attackers use a diverse arsenal of social engineering, because it is much easier to get what you want from a person (personal data) by winning their trust. This is a much more convenient way than directly hacking someone's account: it is much easier to exploit user weaknesses than to try to find a vulnerability in a service or software.Often, attacks using social engineering tools occur in two stages. First, the scammers research the intended victim to collect the necessary background information. It is at this stage that the attacker tries to gain the victim's trust. And after successful attempts to establish "good" relations, the criminal, using various tricks, extracts confidential information from the victim (for example, passwords and IP addresses). We will now talk about different types of such tricks.
Types of Social Engineering Attacks
There are more than ten known types of such attacks, and if we take into account combined methods, some of which we will also consider, then their number already amounts to several dozen.
Phishing
These attacks actively exploit the human factor to collect credentials or to distribute malware. Phishing can be said to be the fraudulent use of electronic communications to deceive and benefit users. Most often, with the help of phishing attacks, attackers try to obtain such confidential information as logins and passwords, credit card data, network credentials.A phishing attack can also be planned in such a way that after going to a fake site, the victim will have other problems: for example, malicious spyware will be installed on the computer or the system will freeze due to a ransomware attack (we wrote about them in the previous article). In some cases, fraudsters are satisfied with obtaining the victim's credit card information or other personal data for financial gain. But it happens that phishing emails are sent to obtain employee registration information or other data for further extended attack on a specific company.
There are several types of phishing cyber attacks. These include targeted, voice, SMS phishing, as well as "whaling" (the description will make it clear why it is called that) and clone phishing.
Spear Phishing
These attacks are similar to regular phishing, but they are aimed at a specific person or organization. Therefore, the attackers first collect detailed information about their targets in order to then send emails that look as credible as possible. People often have no idea that a phishing email has come from an unreliable source. Spear phishing can be called a more advanced version of regular phishing, since it requires much more solid preparation. For this reason, it is extremely difficult to protect against such an attack using regular technical means. In addition, the person being targeted by spear phishing is in most cases not the real target of the criminals - their ultimate goal is usually the corporate network infrastructure, having gained control over which the fraudsters will derive financial benefit from this.Voice Phishing
In this case, criminals use the phone to collect personal and financial information from the victim. For example, the attacker may introduce himself as an employee of a bank or insurance company and, under the pretext of advertising new services, gradually find out the personal data of the interlocutor. Thus, "vishers" can take their victims by surprise, offering them a loan on extremely favorable terms. And since such services are often associated with the disclosure of personal financial information, then if the fraudster can convince the victim of the legitimacy of his offer, the person may not even suspect a trick and pass on confidential information to the criminal.An example that is partly related to “whaling” phishing: in March 2019, the CEO of a British energy company received a call from a man who sounded exactly like his president. The caller was so convincing that the CEO transferred $243,000 to a “Hungarian supplier” in a bank account that actually belonged to the fraudster.
Some attackers focus on sick or elderly people. And in such attacks, they shamelessly exploit the unstable physical and/or mental state of the victim to convince the person that he must hand over his personal information in order to receive help. In such cases, the criminals use the promise of financial assistance as bait, but only after they are given personal information. Another common type of vishing attack: criminals report that something has allegedly happened to the victim's loved ones, and demand a quick transfer of money to solve the problem.
Smishing (SMS-phishing)
This type of phishing attack uses mobile devices. The victim receives a message supposedly from a bank number. The message usually contains some scary information (see Scareware below), and then offers a solution to the problem. A classic example: the victim's personal account allegedly has been debited for an unauthorized purpose, so the person is asked to follow a link to the bank's page (of course, a fake one) or call the phone number provided (also controlled by the scammers). People also receive messages asking to help victims of a natural disaster, but to help, they must leave their personal information. Particularly cunning hackers can "milk" their victims for months in this way, regularly withdrawing small amounts so as not to alert people.Whale Phishing
This is a phishing attack aimed specifically at a top manager of a large company. That is why it is called "whaling", because the victim is highly valued, and the stolen information will be much more valuable than what ordinary company employees can offer to the scammers. And since the victims in this case are high-ranking people, the criminals act accordingly: for example, they send legal messages or offer to discuss serious financial issues.The largest attack of this type, not only phishing but also using social engineering in general, was carried out by Lithuanian citizen Evaldas Rimasauskas against two of the world's largest web corporations: Google and Facebook. Rimasauskas and his team created a fake company and posed as a computer manufacturer that worked with Google and Facebook. Rimasauskas also opened bank accounts in the company's name. As a result, the web giants suffered a total loss of more than $120 million.
In another high-profile case, Chinese aircraft parts maker FACC lost nearly $60 million in a scam in which scammers posed as high-ranking executives and tricked employees into transferring funds to them. After the incident, FACC spent millions more suing its CEO and CFO for damages. The company claimed that the executives had failed to implement proper internal security controls, but FACC's suit was dismissed.
Clone Phishing
The principle of this phishing attack is that the hacker sends a fake email disguised as a regular email, with the address from which the email was sent being very similar to one used by known and trusted sources (e.g. Mail.crop instead of Mail.corp ). That is, the phishing emails look like they are from your bank or service provider, asking for your personal information.In this way, scammers copy the corporate email format, creating an almost identical sample: only this email is sent not from the real one, but from a similar address. The body of the email looks the same as in the emails that the user has already received from this organization, but the links in the email are replaced with malicious ones. Inventive criminals can even explain to the victim why they are receiving the “same” message again.
In fact, these emails have only one goal: “social hackers” try to trick the recipient into revealing personal or financial information by clicking on a link in the email, which redirects the user to a seemingly similar but criminally controlled website designed to steal personal information.
A recent example of clone phishing: In January 2022, a large-scale attack was carried out to steal credentials from the Office 365 service. The attackers were able to successfully imitate messages from the US Department of Labor (DoL). This scam is a clear example of how effective phishing attempts can be. In this case, addresses with the real dol.gov domain were replaced with addresses from the dol-gov.com and dol-gov.us domains that the scammers had previously purchased. Moreover, the phishing emails successfully passed the security gateways of the target organizations. The emails used official DoL attributes and were professionally written, inviting recipients to bid on a government project. The bidding instructions were included in a three-page PDF file with an embedded “Bid” button. When victims clicked on the link, they were redirected to a phishing site that looked identical to the real DoL site. The fake auction site prompted users to enter their Office 365 credentials and even displayed an error message after the first entry. This ensured that the victim would enter their credentials twice, reducing the likelihood of an incorrect entry. This situation would not have occurred if the target organization had better email security measures in place.

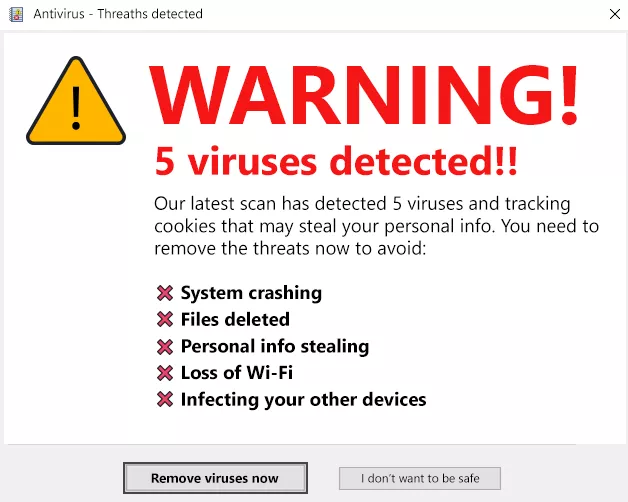
Scareware
The essence of this type of attack is that the victim is scared (usually by pop-ups when visiting websites hacked by scammers), making them think that their computer is infected with malware or has accidentally downloaded illegal content. After some time, when the scammer understands that the victim is ready, he offers a solution to this fictitious problem. However, in fact, the program that is offered to the victim under the guise of an antivirus is malware, the purpose of which is to steal the user's personal information. Thus, the creators of "scarecrows" use suggestion technology, causing fear in the user and pushing him to install fake antivirus software.Baiting
A very original method of social engineering, when the calculation is made on one of the most common human vices - curiosity. The essence of the bait is that the attacker intentionally leaves devices infected with malware (for example, USB drives) in places where they are sure to be found (for example, in the smoking room of an office building). The victim swallows this simple bait and inserts the flash drive into the computer, as a result of which malware is automatically installed in the system. Another type of bait is distributed via the Internet. Potential victims are offered tempting advertising, which in fact leads to malicious sites or encourages users to download an application infected with malware - most often, of course, "free". In addition, attackers often combine bait with Scareware attacks, only this time the "scares" are real, because the computer is already infected.Water-Holing ("watering hole")
The name fully reflects the essence of the attack, only the "water" here is poisoned. Using network vulnerabilities, the attacker tries to compromise a specific group of people by infecting the sites they visit and trust. The objects of "watering hole" attacks are often popular sites, which are called the "target group". Cybercriminals practicing Water holing (another name: Watering hole) call their victims "target prey", and most often this prey is employees of government agencies or large organizations.Hackers study the vulnerabilities of the "target group" sites and inject malware, usually hidden in JavaScript or directly in the HTML code. This malicious code redirects the "loot" from the target group sites to another site that has malware or advertising installed. The viruses are now ready to infect computers as soon as victims visit the compromised sites.
Pretexting attack
The essence of the attack is that one party simply lies to the other to gain access to privileged data. The scam is often initiated by a dishonest employee who pretends to need confidential information from the victim to perform an important task. There is no hacking involved - pure psychological influence that looks very natural.Quid pro quo (Latin for "service for a service")
This type of attack is usually carried out by scammers who do not have advanced hacking tools in their arsenal, but conduct preliminary research of the targets. Using this type of attack, the attacker pretends to provide the victim with an important service. For example, the hacker finds someone with high access privileges to the network and calls them on the phone, introducing themselves as an employee of the company's technical support service. If negotiations are successful and the victim agrees to "help" in solving the allegedly discovered problems, the cybercriminal begins to control the victim, forcing them to perform certain actions. These actions eventually lead to the launch of malware in the system or the theft of registration data.Honey Trap, Honey Pot
Remember the fable about the crow and the fox? The principle of attacks like Honey Pot is exactly the same. The fraudster gets acquainted with the victim and pretends to have a certain interest in them (for example, romantic or sexual attraction). Gradually, a virtual "relationship" is established, which the victim begins to take seriously. And the charming criminal, wasting no time, gradually collects confidential information, which can then be used, for example, to hack social media accounts or an email box. The fraudster can also get remote access to the gullible victim's computer.
Tailgating or Piggyback
Another original trick from the arsenal of social engineering specialists, which is somewhat similar to the previous one. In this case, the criminal enters a secure room, following someone with an access card. Of course, the hacker is already a "friend" of the employee with privileged access and follows him into the restricted area.Rogue Attack
This method is a type of Scareware attack. Malware is installed on the victim's computer under the pretext of security, and the attacker convinces the victim that this software is completely legal and safe. The installed program then creates pop-up windows and alerts that advise the user to download new "safe software". Pop-up windows often show the user several options for consent (with different scenarios). However, there is no difference: by clicking "yes" to any of these options, the user downloads a dangerous program to his computer. The computer is now at the attacker's disposal.Diversion Theft
Here, “social engineers” trick delivery services or couriers into delivering counterfeits to unsuspecting buyers. And the expensive items, of course, end up in the hands of the scammers. It works like this: the criminals plant their accomplices in the delivery company, and the latter get easy access to the list of goods to be delivered, which can then be quickly replaced. This method of theft arose even before the advent of the Internet (its birthplace is London’s East End), but with the development of network technologies, it has become easier for criminals to manipulate information.How to Protect Yourself from Social Engineering Attacks
The most important step in protecting individuals and the entire organization from social engineering attacks is to systematically and continuously inform all users (at all levels and in all departments) about the types of these attacks and what psychological techniques the attackers use to obtain the desired data. In addition, we must not forget about other preventive measures:- Penetration testing. Cybersecurity experts recommend that IT departments regularly test for possible attacks using social engineering techniques. This will help administrators learn which users pose the greatest risk to certain types of attacks. A penetration test is a simulated cyberattack on a computer system or specific users to test for vulnerabilities. Such periodic tests are useful because they allow you to determine the readiness of users and assess the possible scale of a data leak. Simulated phishing tests can be carried out using special programs. During the tests, employees are sent phishing emails and it is found out who falls for social engineering tactics. These employees can then be retrained.
- Two-factor authentication (2FA). 2FA involves two methods of identity verification: for example, a password and a code on a phone. It is one of the most effective methods of countering attacks using social engineering technologies.
- Using anti-malware protection. This protection should be comprehensive and include anti-virus software for web surfing, mail anti-virus and anti-spyware. Some companies provide package protection, but you can also use several good applications from different developers. One of the most important tasks of such protection is to prevent dangers when the user clicks on links in letters and messengers. Thus, if the user clicks on a link (in a browser, email or messenger) and if the web page is suspicious in terms of network threats, the protection should prevent the page with malicious content from loading and block it.
- Regular operating system updates. Operating systems on all computers in an organization should be updated promptly, as developers frequently release patches to eliminate vulnerabilities that have been detected.
- Proper selection and periodic password change. As an effective preventive measure, organizations should implement strict password management policies. Employees should be required to change their passwords periodically and, equally important, to create them correctly. The best option here is randomly generated complex passwords that are almost impossible to guess. Of course, employees should also be trained in the proper storage of such passwords.
- Using a firewall. A good network firewall (WAF) blocks malicious requests, which can also include social engineering attacks. So before visitors reach your site, they are filtered by the WAF, which determines whether the connection is safe and blocks the connection if it looks like a fraudulent attack.
- Create a positive environment. Your employees should feel comfortable reporting their suspicions if they believe they have been the victim of a social engineering attack, but they will not do so if they feel threatened with punishment or social stigma. This is important because if such attacks are reported as soon as they occur, the threat can be quickly addressed before too much damage is done to the company.
But these tips are intended primarily for company management and IT specialists, but what should users do, including those with high access levels, who also often lose their vigilance? We will also give them some tips that will, with some probability, help prevent the creation of vulnerabilities.
- To determine if an email has been spoofed, carefully check the sender's name and email address for errors.
- Be suspicious of any unexpected messages, especially from people you don't know.
- Avoid downloading suspicious email attachments.
- Don't click on links from suspicious emails. Better yet, get into the habit of not clicking on such links at all unless you're 100% sure they lead to a reliable site.
And finally, a telling statistic: the US Cybercrime Report for 2019 states that phishing attacks caused damage to individuals and businesses in the amount of about $58 million. In addition, about 115 thousand people or organizations fell victim to these attacks. And to adequately assess these numbers and the scale of the threat, it should be borne in mind that this report concerns only the USA.

