Tomcat
Professional
- Messages
- 2,687
- Reaction score
- 1,038
- Points
- 113
How an international proxy network was used to steal social security payments.
The US Treasury Department has imposed sanctions on a network of cybercriminals that includes three Chinese citizens and three companies from Thailand. The subjects are linked to a large botnet that controlled a resident proxy service called "911 S5".
Detection and operation of the 911 S5
In June 2022, researchers from the Canadian University of Sherbrooke revealed that the 911 S5 lured victims by offering a free VPN. The VPN was used to install malware that added victims IP addresses to the 911 S5 botnet. At that time, the botnet controlled about 120,000 resident proxy nodes around the world, each of which interacted with several C2 servers located abroad or hosted on a cloud server.
Stopping and reviving the botnet
A month later, investigative journalist Brian Krebs reported that the 911 S5 stopped working after destroying key components of its business operations due to a security breach. However, the botnet was revived a few months later under the name CloudRouter, according to a report by Spur Intelligence in February.
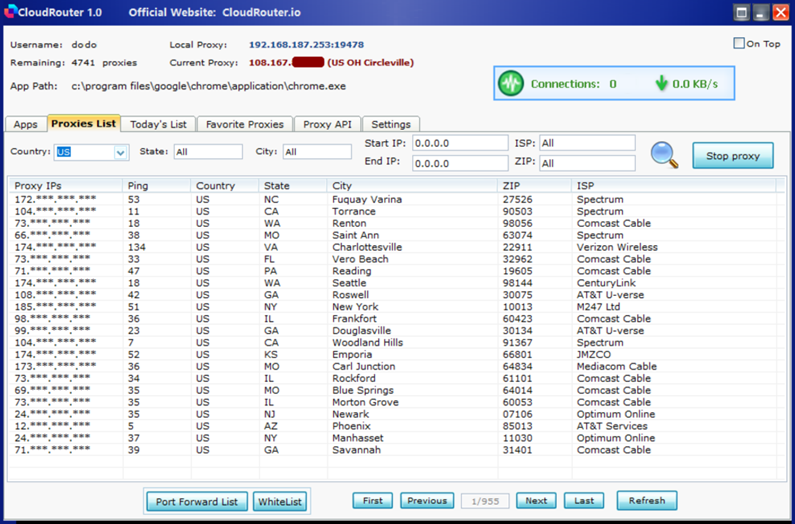
CloudRouter Interface
OFAC measures and damages
The U.S. Treasury Department's Office of Foreign Assets Control (OFAC) said the 911 S5 botnet was a malicious service that compromised victims ' computers and allowed cybercriminals to proxy their Internet connections through infected computers.
Infected devices allowed criminals to disguise their actions, shifting responsibility to the victims ' computers. The botnet compromised about 19 million IP addresses, allowing cybercriminals to file tens of thousands of fraudulent applications for programs related to the CARES Act, resulting in losses of billions of dollars.
Fares for 911 S5
Sanctions against participants
OFAC has imposed sanctions against the following individuals and companies:
According to OFAC documents, "the listed individuals and legal entities used the botnet to compromise personal devices, which allowed cybercriminals to fraudulently receive economic assistance intended for those in need."
As a result of the sanctions, all operations that affect the interests of the United States and the property of listed individuals and legal entities are prohibited. Any transactions with these individuals and companies are also subject to sanctions or enforcement actions.
The US Treasury Department has imposed sanctions on a network of cybercriminals that includes three Chinese citizens and three companies from Thailand. The subjects are linked to a large botnet that controlled a resident proxy service called "911 S5".
Detection and operation of the 911 S5
In June 2022, researchers from the Canadian University of Sherbrooke revealed that the 911 S5 lured victims by offering a free VPN. The VPN was used to install malware that added victims IP addresses to the 911 S5 botnet. At that time, the botnet controlled about 120,000 resident proxy nodes around the world, each of which interacted with several C2 servers located abroad or hosted on a cloud server.
Stopping and reviving the botnet
A month later, investigative journalist Brian Krebs reported that the 911 S5 stopped working after destroying key components of its business operations due to a security breach. However, the botnet was revived a few months later under the name CloudRouter, according to a report by Spur Intelligence in February.

CloudRouter Interface
OFAC measures and damages
The U.S. Treasury Department's Office of Foreign Assets Control (OFAC) said the 911 S5 botnet was a malicious service that compromised victims ' computers and allowed cybercriminals to proxy their Internet connections through infected computers.
Infected devices allowed criminals to disguise their actions, shifting responsibility to the victims ' computers. The botnet compromised about 19 million IP addresses, allowing cybercriminals to file tens of thousands of fraudulent applications for programs related to the CARES Act, resulting in losses of billions of dollars.

Fares for 911 S5
Sanctions against participants
OFAC has imposed sanctions against the following individuals and companies:
- Yunhe Wang (911 S5 administrator);
- Jingping Liu (money launderer);
- Yanni Zheng (Eunhae Wang's confidant);
- Spicy Code Company Limited;
- Tulip Biz Pattaya Group Company Limited;
- Lily Suites Company Limited.
According to OFAC documents, "the listed individuals and legal entities used the botnet to compromise personal devices, which allowed cybercriminals to fraudulently receive economic assistance intended for those in need."
As a result of the sanctions, all operations that affect the interests of the United States and the property of listed individuals and legal entities are prohibited. Any transactions with these individuals and companies are also subject to sanctions or enforcement actions.

