Friend
Professional
- Messages
- 2,675
- Reaction score
- 987
- Points
- 113
Quantum resilience and lightning-fast proliferation are qualitatively changing the cyber threat landscape.
The Indian hacking group CyberVolk, originally known by the name GLORIAMIST India, began operations in March 2024 and has since become one of the notable cybercriminal organizations. The first public information about the group appeared only recently thanks to the ThreatMon analytics platform, which monitors the activity of various network threats.
Soon after its founding, the group began to attract attention due to its successful attacks and active presence both on the darknet and on the regular Internet through the maintenance of an official Telegram channel and an account on the X platform.
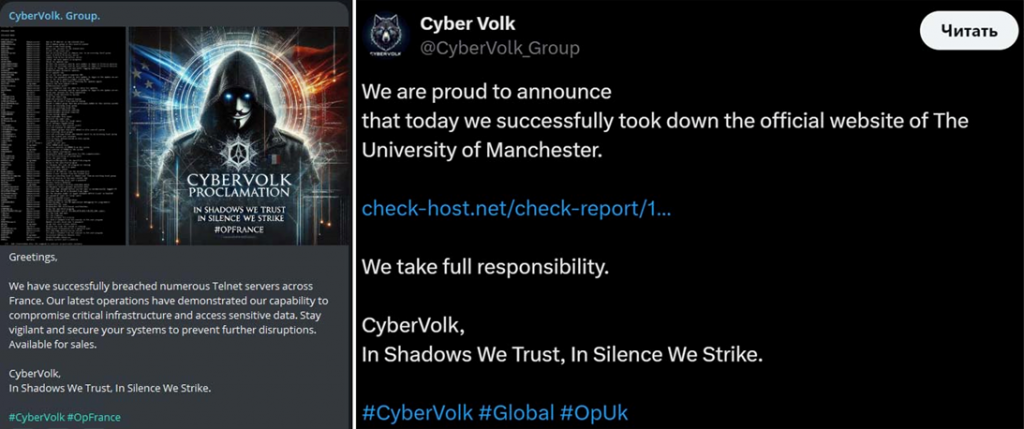
CyberVolk specializes in various types of cyberattacks, including DDoS attacks, website hacking (defaceting), data breaches, and network hacks. However, their ransomware known as the CyberVolk Ransomware is of particular concern. The software was first registered online on July 1, 2024, and just a few days later appeared on shady platforms in the form of a "Ransomware as a Service" (RaaS) service, which means that anyone can rent this tool for their own cyberattacks.
Initially, CyberVolk Ransomware used the common AES encryption algorithm, however, this version of the program was lost due to a data leak on the VirusTotal service, which made it inoperable. Hackers did not ignore this and released an updated version of the program with a number of serious changes.
The new malware variant involves the use of complex cryptographic algorithms such as ChaCha20-Poly1305, AES, and quantum-resistant encryption technologies. These algorithms make the program even more dangerous, as it can resist decryption attempts even with quantum computers.
The CyberVolk Ransomware is unique in that it can encrypt data without connecting to a C2 command and control server, making it difficult to detect and block. The program also contains a mechanism that automatically deletes data when an incorrect decryption key is entered, making data recovery almost impossible in the event of an error or missing backups.
The updated version of the program differs in that it no longer uses the ".cvenc" extension. The hackers have moved on to the new '. CyberVolk». This is another evidence that developers are actively developing their software, taking into account the vulnerabilities and gaps of previous versions. It is noteworthy that the new ransomware has become completely invisible to antivirus solutions (Fully Undetectable), which makes it even more dangerous for end users.
The first data on the profit received by hackers from the use of the CyberVolk program corresponded to the amount of $2632. However, in recent months, the revenue has grown significantly, already exceeding $20,000. This highlights the high level of threat posed by the use of this software, especially for companies that do not have a robust data protection system.
During their analysis, ThreatMon experts revealed that once executed on a device, the CyberVolk Ransomware would immediately block access to system tools such as Task Manager to prevent the encryption process from being interrupted. The program begins to encrypt all files on the computer, and this process takes place within just a few minutes.
Once encryption is complete, a $1000 ransom window appears on the device, as well as a text file «Readme.txt" with further instructions. If the request is not fulfilled within five hours, the data will be irretrievably destroyed.
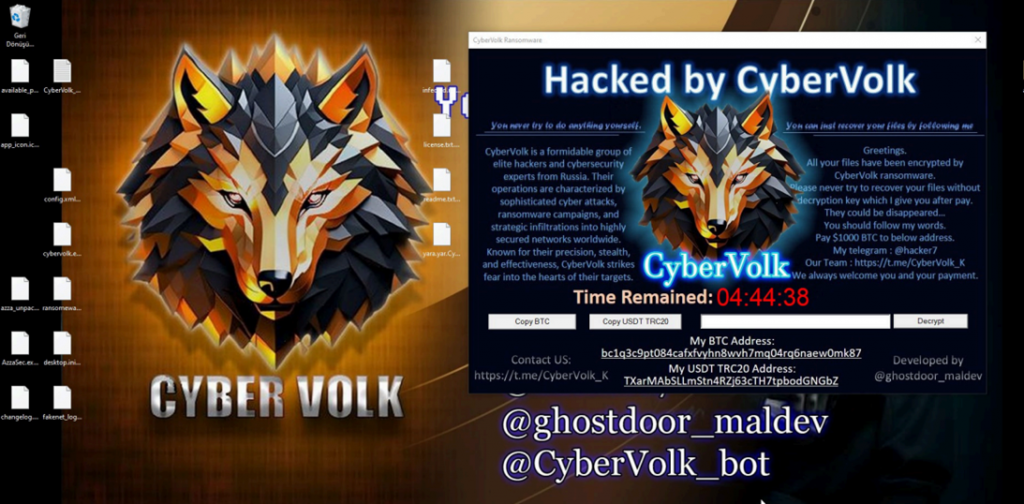
The technical features of CyberVolk Ransomware make the program unique from other ransomware software. It is developed in C++ and does not use any packers to hide its code, which allowed us to conduct a detailed analysis of it. The program runs with the saving of a temporary file "time.dat", which counts down exactly 18,000 seconds (five hours), giving the user extremely limited time to make a decision to pay the ransom.
In addition, the program has debugger detection and runtime inspection, which allows it to hide in virtual machines and avoid analysis. The CyberVolk Ransomware checks for the presence of SafeBoot keys in the Windows registry to determine if it is running in Safe Mode. If the program detects that the device is in safe mode, it suspends some of its functions, which complicates its analysis by cybersecurity specialists.
One of the key features of the CyberVolk Ransomware is that the program is capable of spreading like computer worms. It scans all connected disks and devices, including removable media and network storage, and tries to copy itself to these devices for further distribution. This makes it dangerous not only for one infected device, but also for the entire network to which it is connected.
Despite the high threat level, ThreatMon specialists have discovered several critical vulnerabilities in the program. For example, although the program blocks Task Manager, it does not block PowerShell, which allows advanced users to stop the encryption process by typing the appropriate commands.
It also turned out that the timer that counts down to data destruction can be easily changed by modifying the "time.dat" file located in the /User/AppData/Roaming path, which allows you to extend the time for analyzing the program and restoring data indefinitely.
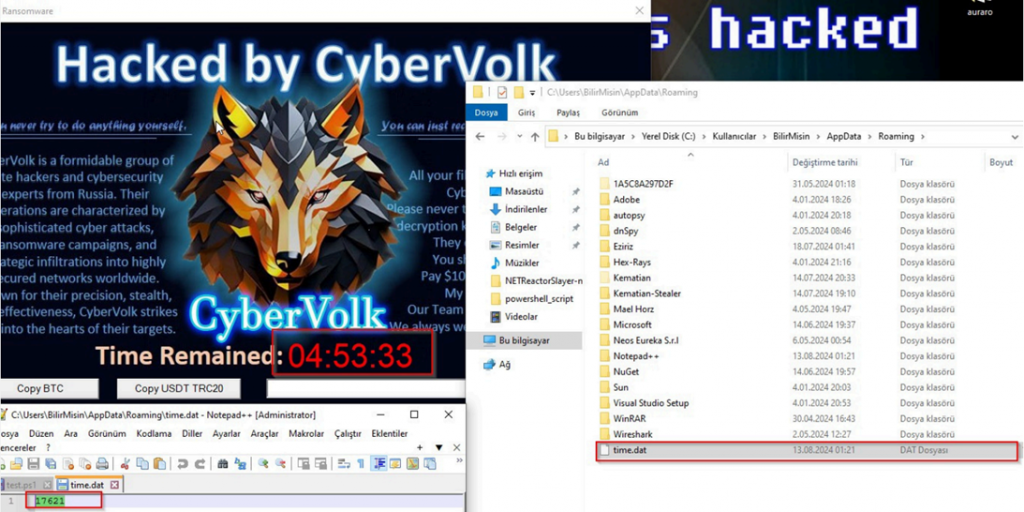
Thus, the CyberVolk Ransomware poses a serious threat to companies and individuals, but the presence of several vulnerabilities in its structure gives hope for effective counteraction. Cybersecurity experts recommend regularly updating security software, backing up data, and educating employees on the basics of cyber hygiene to minimize the risks of ransomware attacks.
Source
The Indian hacking group CyberVolk, originally known by the name GLORIAMIST India, began operations in March 2024 and has since become one of the notable cybercriminal organizations. The first public information about the group appeared only recently thanks to the ThreatMon analytics platform, which monitors the activity of various network threats.
Soon after its founding, the group began to attract attention due to its successful attacks and active presence both on the darknet and on the regular Internet through the maintenance of an official Telegram channel and an account on the X platform.

CyberVolk specializes in various types of cyberattacks, including DDoS attacks, website hacking (defaceting), data breaches, and network hacks. However, their ransomware known as the CyberVolk Ransomware is of particular concern. The software was first registered online on July 1, 2024, and just a few days later appeared on shady platforms in the form of a "Ransomware as a Service" (RaaS) service, which means that anyone can rent this tool for their own cyberattacks.
Initially, CyberVolk Ransomware used the common AES encryption algorithm, however, this version of the program was lost due to a data leak on the VirusTotal service, which made it inoperable. Hackers did not ignore this and released an updated version of the program with a number of serious changes.
The new malware variant involves the use of complex cryptographic algorithms such as ChaCha20-Poly1305, AES, and quantum-resistant encryption technologies. These algorithms make the program even more dangerous, as it can resist decryption attempts even with quantum computers.
The CyberVolk Ransomware is unique in that it can encrypt data without connecting to a C2 command and control server, making it difficult to detect and block. The program also contains a mechanism that automatically deletes data when an incorrect decryption key is entered, making data recovery almost impossible in the event of an error or missing backups.
The updated version of the program differs in that it no longer uses the ".cvenc" extension. The hackers have moved on to the new '. CyberVolk». This is another evidence that developers are actively developing their software, taking into account the vulnerabilities and gaps of previous versions. It is noteworthy that the new ransomware has become completely invisible to antivirus solutions (Fully Undetectable), which makes it even more dangerous for end users.
The first data on the profit received by hackers from the use of the CyberVolk program corresponded to the amount of $2632. However, in recent months, the revenue has grown significantly, already exceeding $20,000. This highlights the high level of threat posed by the use of this software, especially for companies that do not have a robust data protection system.
During their analysis, ThreatMon experts revealed that once executed on a device, the CyberVolk Ransomware would immediately block access to system tools such as Task Manager to prevent the encryption process from being interrupted. The program begins to encrypt all files on the computer, and this process takes place within just a few minutes.
Once encryption is complete, a $1000 ransom window appears on the device, as well as a text file «Readme.txt" with further instructions. If the request is not fulfilled within five hours, the data will be irretrievably destroyed.

The technical features of CyberVolk Ransomware make the program unique from other ransomware software. It is developed in C++ and does not use any packers to hide its code, which allowed us to conduct a detailed analysis of it. The program runs with the saving of a temporary file "time.dat", which counts down exactly 18,000 seconds (five hours), giving the user extremely limited time to make a decision to pay the ransom.
In addition, the program has debugger detection and runtime inspection, which allows it to hide in virtual machines and avoid analysis. The CyberVolk Ransomware checks for the presence of SafeBoot keys in the Windows registry to determine if it is running in Safe Mode. If the program detects that the device is in safe mode, it suspends some of its functions, which complicates its analysis by cybersecurity specialists.
One of the key features of the CyberVolk Ransomware is that the program is capable of spreading like computer worms. It scans all connected disks and devices, including removable media and network storage, and tries to copy itself to these devices for further distribution. This makes it dangerous not only for one infected device, but also for the entire network to which it is connected.
Despite the high threat level, ThreatMon specialists have discovered several critical vulnerabilities in the program. For example, although the program blocks Task Manager, it does not block PowerShell, which allows advanced users to stop the encryption process by typing the appropriate commands.
It also turned out that the timer that counts down to data destruction can be easily changed by modifying the "time.dat" file located in the /User/AppData/Roaming path, which allows you to extend the time for analyzing the program and restoring data indefinitely.

Thus, the CyberVolk Ransomware poses a serious threat to companies and individuals, but the presence of several vulnerabilities in its structure gives hope for effective counteraction. Cybersecurity experts recommend regularly updating security software, backing up data, and educating employees on the basics of cyber hygiene to minimize the risks of ransomware attacks.
Source
