Tens of thousands of organizations are not at all prepared for the new Internet threat.
A new wave of attacks using a modified variant of Mirai called GorillaBot caused more than 300,000 DDoS attacks, which affected about 20,000 organizations around the world in September this year.
In about 41% of cases, attackers used UDP Flood, directing packet arrays to overload victims' networks. Also, about a quarter of the attacks used ACK Bypass Flood, when attackers flooded one port with fake TCP ACK packets, creating congestion at the network protocol level.
Researchers from NSFOCUS noted that GorillaBot uses recycled code from the Mirai family and supports architectures such as ARM, MIPS, x86_64, and x86. A feature of GorillaBot is a message on infected devices with the text "gorilla botnet is on the device ur not a cat go away", which was the reason for the botnet's name.
To control the botnet, five C2 servers were used at once, which at the peak of the attacks generated up to 20 thousand commands per day. In total, 113 countries were affected by the attacks, with China being the hardest hit, followed by the United States, Canada and Germany.
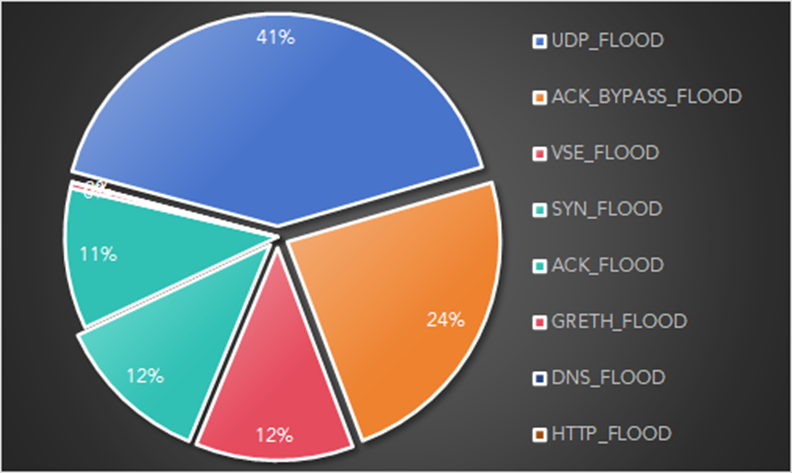
The most popular DDoS attack methods used by the GorillaBot botnet
GorillaBot uses 19 different DDoS attack methods, including UDP floods and TCP Syn/ACK floods, which complicates the protection process for organizations. Countering such multi-layered attacks requires the use of various security techniques, such as limiting the bit rate of UDP packets and using TCP snooping systems to filter only valid ACK packets.
Traffic from so-called "bad bots" like GorillaBot continues to grow. In 2023, Imperva researchers blocked about 6 trillion requests from such bots, which is 32% of all Internet traffic, which is 2% more than in the previous year. Imperva notes that the share of DDoS-related bot attacks reaches 12.4%, especially in industries such as the gaming industry, telecommunications, and healthcare.
The evolution of cyber threats requires constant vigilance and adaptation of protective measures. The emergence of new malware variants, such as GorillaBot, demonstrates that threat actors are constantly improving their tools, using multi-layered attacks and covering a wide range of targets around the world.
Organizations need to invest in comprehensive security systems and regularly update their defense strategies to counter the increasing sophistication and scale of cyberattacks in today's digital landscape.
Source
A new wave of attacks using a modified variant of Mirai called GorillaBot caused more than 300,000 DDoS attacks, which affected about 20,000 organizations around the world in September this year.
In about 41% of cases, attackers used UDP Flood, directing packet arrays to overload victims' networks. Also, about a quarter of the attacks used ACK Bypass Flood, when attackers flooded one port with fake TCP ACK packets, creating congestion at the network protocol level.
Researchers from NSFOCUS noted that GorillaBot uses recycled code from the Mirai family and supports architectures such as ARM, MIPS, x86_64, and x86. A feature of GorillaBot is a message on infected devices with the text "gorilla botnet is on the device ur not a cat go away", which was the reason for the botnet's name.
To control the botnet, five C2 servers were used at once, which at the peak of the attacks generated up to 20 thousand commands per day. In total, 113 countries were affected by the attacks, with China being the hardest hit, followed by the United States, Canada and Germany.

The most popular DDoS attack methods used by the GorillaBot botnet
GorillaBot uses 19 different DDoS attack methods, including UDP floods and TCP Syn/ACK floods, which complicates the protection process for organizations. Countering such multi-layered attacks requires the use of various security techniques, such as limiting the bit rate of UDP packets and using TCP snooping systems to filter only valid ACK packets.
Traffic from so-called "bad bots" like GorillaBot continues to grow. In 2023, Imperva researchers blocked about 6 trillion requests from such bots, which is 32% of all Internet traffic, which is 2% more than in the previous year. Imperva notes that the share of DDoS-related bot attacks reaches 12.4%, especially in industries such as the gaming industry, telecommunications, and healthcare.
The evolution of cyber threats requires constant vigilance and adaptation of protective measures. The emergence of new malware variants, such as GorillaBot, demonstrates that threat actors are constantly improving their tools, using multi-layered attacks and covering a wide range of targets around the world.
Organizations need to invest in comprehensive security systems and regularly update their defense strategies to counter the increasing sophistication and scale of cyberattacks in today's digital landscape.
Source







