What would such a clear link between groups mean?
Threat researchers at Check Point Research have found tactical similarities between the Rhysida and Vice Society ransomware groups, and their targets in the education and health sectors. Experts have noticed that with an average degree of reliability, Vice Society operators are currently using the Rhysida ransomware program in their campaigns.
The Vice Society group (Storm-0832), which has been active since May 2021, uses ready-made binary files of ransomware programs that are sold on hacker forums in its ransomware attacks. Initial access to the network is through compromised credentials or exploiting privilege escalation vulnerabilities.
In turn, the Rhysida ransomware group, first discovered in May 2023, uses phishing and Cobalt Strike to break into target networks and deploy payloads. Most of the group's victims are based in the US, UK, Italy, Spain and Austria.
Rhysida hackers perform lateral Movement using the Remote Desktop Protocol (RDP) and remote PowerShell sessions, and the ransomware payload is deployed using the Windows PsExec tool. Command and Control of operations (C2) is achieved using the Sysembc backdoor and remote management tools such as AnyDesk.
Notably, the group's attack chains constantly purge logs and forensic artifacts to hide traces of hacking, and change the password for the entire domain to thwart remediation efforts.
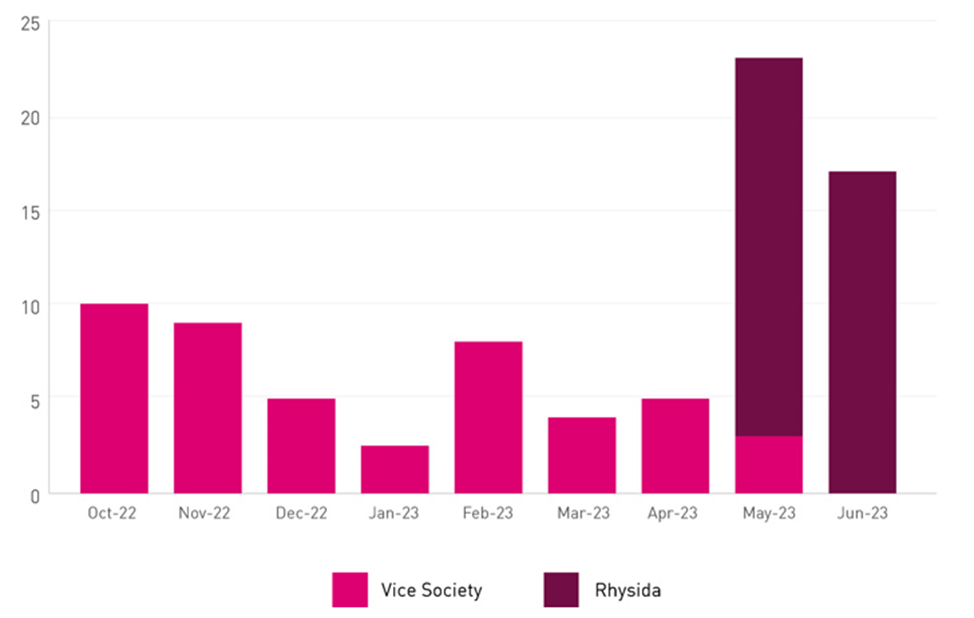
Activity of the Vice Society and Rhysida groups
According to Check Point, there is a clear link between the appearance of Rhysida and the disappearance of the Vice Society. Experts highlighted the use of the legitimate NTDSUTil command-line tool, the creation of local firewall rules to ensure communication with the C2 server via SystemBC, and the use of the PortStarter tool, which was used exclusively by the Vice Society.
Since Rhysida first appeared in May 2023, Vice Society has only posted 2 victims on its leak site. It is likely that the victims were known earlier, but were published only in June. Hackers of Vice Society stopped publishing messages on the site of leaks from June 21, 2023.
Another important indicator is compliance in cybercriminal victimology. Both Rhysida and Vice Society target the education industry, accounting for 32% and 35% of all attacks, respectively.
The researchers noted that the TTPs of group members remain virtually unchanged-from using remote management tools such as AnyDesk to deploying ransomware through PsExec.
Earlier, we wrote that, according to a report by Palo Alto Networks Unit 42, the Vice Society group attacked 33 educational institutions in 2022 , which is more than other ransomware programs. Palo Alto Networks named Vice Society "one of the most influential ransomware groups of 2022." In total, the group targeted companies from the healthcare, government, manufacturing, retail, and legal services sectors.
Threat researchers at Check Point Research have found tactical similarities between the Rhysida and Vice Society ransomware groups, and their targets in the education and health sectors. Experts have noticed that with an average degree of reliability, Vice Society operators are currently using the Rhysida ransomware program in their campaigns.
The Vice Society group (Storm-0832), which has been active since May 2021, uses ready-made binary files of ransomware programs that are sold on hacker forums in its ransomware attacks. Initial access to the network is through compromised credentials or exploiting privilege escalation vulnerabilities.
In turn, the Rhysida ransomware group, first discovered in May 2023, uses phishing and Cobalt Strike to break into target networks and deploy payloads. Most of the group's victims are based in the US, UK, Italy, Spain and Austria.
Rhysida hackers perform lateral Movement using the Remote Desktop Protocol (RDP) and remote PowerShell sessions, and the ransomware payload is deployed using the Windows PsExec tool. Command and Control of operations (C2) is achieved using the Sysembc backdoor and remote management tools such as AnyDesk.
Notably, the group's attack chains constantly purge logs and forensic artifacts to hide traces of hacking, and change the password for the entire domain to thwart remediation efforts.

Activity of the Vice Society and Rhysida groups
According to Check Point, there is a clear link between the appearance of Rhysida and the disappearance of the Vice Society. Experts highlighted the use of the legitimate NTDSUTil command-line tool, the creation of local firewall rules to ensure communication with the C2 server via SystemBC, and the use of the PortStarter tool, which was used exclusively by the Vice Society.
Since Rhysida first appeared in May 2023, Vice Society has only posted 2 victims on its leak site. It is likely that the victims were known earlier, but were published only in June. Hackers of Vice Society stopped publishing messages on the site of leaks from June 21, 2023.
Another important indicator is compliance in cybercriminal victimology. Both Rhysida and Vice Society target the education industry, accounting for 32% and 35% of all attacks, respectively.
The researchers noted that the TTPs of group members remain virtually unchanged-from using remote management tools such as AnyDesk to deploying ransomware through PsExec.
Earlier, we wrote that, according to a report by Palo Alto Networks Unit 42, the Vice Society group attacked 33 educational institutions in 2022 , which is more than other ransomware programs. Palo Alto Networks named Vice Society "one of the most influential ransomware groups of 2022." In total, the group targeted companies from the healthcare, government, manufacturing, retail, and legal services sectors.
