Man
Professional
- Messages
- 3,222
- Reaction score
- 1,201
- Points
- 113
In the digital space, an invisible battle for control of technology is taking place around the world.
Shadowserver The Foundation has discovered a botnet that exploits a zero-day vulnerability in outdated GeoVision devices to compromise them and use them in DDoS attacks or cryptocurrency mining.
The vulnerability CVE-2024-11120 (CVSS score: 9.8) is related to OS command injection and allows an unauthorized attacker to execute arbitrary commands on the system. The operation of this Zero-Day has already begun, as reported by the Taiwan CERT. Experts note that the problem affects several models of devices:
All of the listed models are out of service and no longer supported by the manufacturer, so no security updates are expected. This makes them particularly vulnerable to attacks.
According to The Shadowserver Foundation, there are about 17,000 GeoVision devices on the Internet that are in the public domain and vulnerable to CVE-2024-11120. The largest number was recorded in the United States (9100), followed by Germany (1600), Canada (800), Taiwan (800), Japan (350), Spain (300) and France (250).
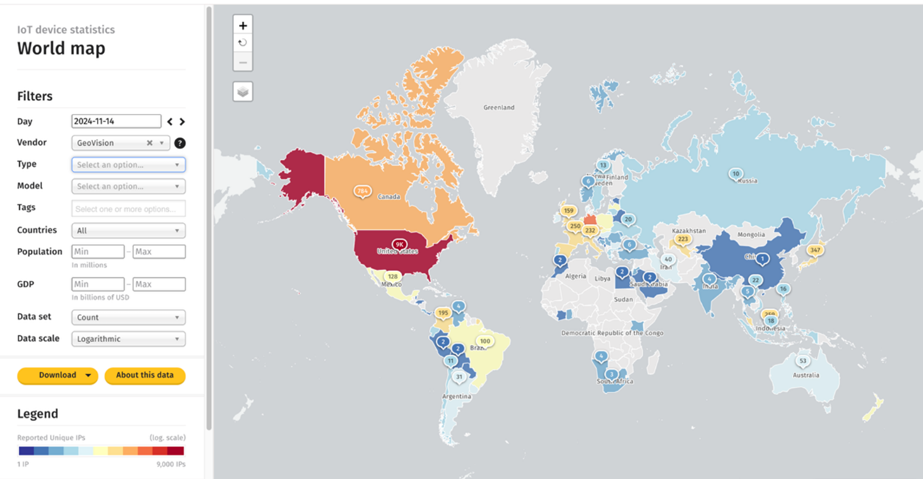
Geography of infected devices (The Shadowserver Foundation)
Experts from The Shadowserver Foundation have suggested that a variant of the Mirai botnet, usually used for DDoS attacks or hidden cryptocurrency mining, is behind the attacks.
Signs of compromise
Among the symptoms of botnet infection of devices are:
Recommendations for protection
To minimize risks, it is recommended:
If replacing devices with supported models is not possible, experts advise isolating them in a separate network and regularly monitoring activity. Replacing outdated devices with up-to-date analogues remains the most reliable solution to prevent attacks.
Source
Shadowserver The Foundation has discovered a botnet that exploits a zero-day vulnerability in outdated GeoVision devices to compromise them and use them in DDoS attacks or cryptocurrency mining.
The vulnerability CVE-2024-11120 (CVSS score: 9.8) is related to OS command injection and allows an unauthorized attacker to execute arbitrary commands on the system. The operation of this Zero-Day has already begun, as reported by the Taiwan CERT. Experts note that the problem affects several models of devices:
- The GV-VS12 is a 2-channel H.264 video server that converts analog video signals into digital streams for transmission over the network.
- The GV-VS11 is a single-channel video server designed to digitize analog video for network streaming.
- The GV-DSP LPR V3 is a Linux-based license-plate recognition (LPR) system.
- The GV-LX4C V2 and GV-LX4C V3 are compact DVRs for mobile surveillance.
All of the listed models are out of service and no longer supported by the manufacturer, so no security updates are expected. This makes them particularly vulnerable to attacks.
According to The Shadowserver Foundation, there are about 17,000 GeoVision devices on the Internet that are in the public domain and vulnerable to CVE-2024-11120. The largest number was recorded in the United States (9100), followed by Germany (1600), Canada (800), Taiwan (800), Japan (350), Spain (300) and France (250).

Geography of infected devices (The Shadowserver Foundation)
Experts from The Shadowserver Foundation have suggested that a variant of the Mirai botnet, usually used for DDoS attacks or hidden cryptocurrency mining, is behind the attacks.
Signs of compromise
Among the symptoms of botnet infection of devices are:
- Overheating;
- Slow performance or freezes
- Configuration changes without the user's knowledge.
Recommendations for protection
To minimize risks, it is recommended:
- Reset the device.
- Set a complex password instead of a standard one.
- Disable remote access.
- Place the device behind a firewall.
If replacing devices with supported models is not possible, experts advise isolating them in a separate network and regularly monitoring activity. Replacing outdated devices with up-to-date analogues remains the most reliable solution to prevent attacks.
Source

