decodex10o0
Member
- Messages
- 1
- Reaction score
- 1
- Points
- 3
Hi, I am interested in learning how to write my own tracks or dumps to clone cards, because I don't want to be scammed by people who supposedly sell this. Also if it is not possible as such to write them, I would be interested to know how I can get them in a safe way and not scammed.
I would also like to know the name of the program in the picture I am attaching, which is supposed to be used to get the information from ccs and know the balance they have, and I would like to understand a little more how this program works.
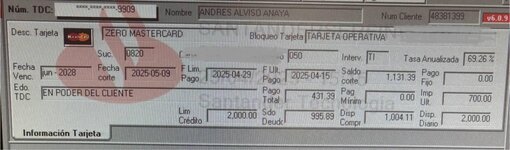
I would also like to know the name of the program in the picture I am attaching, which is supposed to be used to get the information from ccs and know the balance they have, and I would like to understand a little more how this program works.


