Man
Professional
- Messages
- 3,222
- Reaction score
- 881
- Points
- 113
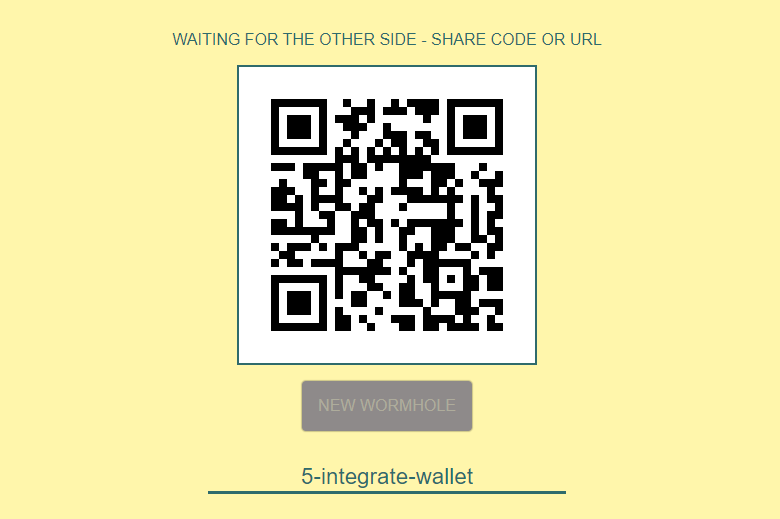
The new WebWormHole service works as a portal through which files are transferred from one computer to another. You click the New Wormhole button and get a code to enter. The person on the other side enters the same code or URL - and an ephemeral tunnel is established between you, through which files are transferred directly. Very simple and effective. Source code on Github.
You don't need to open a browser to install a portal between devices. The Go client runs from the command line and generates a one-time code in the console.
Installation:
Code:
$ go get -u webwormhole.io/cmd/wwTransfer:
Code:
$ cat hello.txt
hello, world
$ ww send hello.txt
8-enlist-decadenceThe recipient on the other side of the ephemeral tunnel enters a one-time code into the console and receives the file.
Code:
$ ww receive 8-enlist-decadence
$ cat hello.txt
hello, worldThe author of the program, Salmān Aljammāz, warns that the client is in early development, uses experimental cryptographic libraries, so it may glitch and not work in all browsers. The program has also not passed a security audit, so it may work incorrectly and unsafely.
The author borrowed the idea and name from the Magic Wormhole program, which also establishes a peer-to-peer connection and transfers files between computers.

Magic Wormhole
The difference is that WebWormHole uses WebRTC, which allows you to break through firewalls and NAT, as well as start the transfer from the browser.
Each tunnel is protected by a one-time password and PAKE - this is a specific way of exchanging keys with password authentication to establish an encrypted connection. The password itself is not transmitted over the network in any form.
The verification is carried out in a manner similar to a zero-knowledge proof, in which the recipient can verify the veracity of a statement without having any other information from the sender.

SPAKE2
In WebWormHole, session descriptions with DTLS certificate fingerprints, which WebRTC uses to encrypt connections, are exchanged to generate a common encryption key.
Transferring files via a peer-to-peer tunnel is faster and safer than via email, FTP, or other methods. These methods are compared in terms of convenience and security in the table from the Magic Wormhole presentation:
| Input by sender | Recipient input | Physical intimacy | Wiretapping | |
|---|---|---|---|---|
| ~30 simv. | providers, certification centers, internet | |||
| Upload to FTP/HTTP | ~60 simv. | server, providers, certification centers, internet | ||
| Dropbox | ~60 simv. | Dropbox, Certification Authorities | ||
| +link shortening service | ~20 simv. | URL Shortening Service, Random Enumeration, Dropbox, Certificate Authorities | ||
| USB drive | X | |||
| SSH/scp | ~740 chars public key | nobody | ||
| magic wormhole | ~20 simv. | nobody |
In addition to Python's Magic Wormhole, there are other clients for establishing direct connections via WebRTC between computers:
- pion WebRTC: Go's WebRTC API implementation
- aiortc: WebRTC library for Python's asyncio framework
- webrtcbin
- rawrtc
- node-webrtc
As a bonus:
- rtc-ssh: WebRTC wrapper for SSH-connected
The WebRTC channel can be used to establish video communication between devices, transmit voice, files, etc.
As for the PAKE key exchange mechanism, it is useful in various areas. For example, it allows you to implement authentication on a website without transmitting a password to the server.
Source
