Brother
Professional
- Messages
- 2,590
- Reaction score
- 537
- Points
- 113
The source of the risk was a built-in but long-forgotten browser feature.
Security researchers from Guardio Labs discovered a serious flaw in the Opera web browser for Windows and macOS operating systems. With its help, attackers can run absolutely any files, including malicious ones, in the basic operating system of the computer.
Experts assigned the vulnerability the code name " MyFlaw "(a play on words, literally translated" my vulnerability"), as it is associated with the" My Flow"function, which allows you to synchronize messages and files between mobile and desktop devices.
To implement the vulnerability, a browser extension controlled by an attacker is used, which actually bypasses its sandbox and the entire operation process. The issue affects both the regular version of Opera and Opera GX.
My Flow has a chat-like interface and is used to share notes and files between your smartphone and desktop computer. As it turned out, files from this chat can be launched directly through the browser's web interface, outside the browser's security limits.
The work of My Flow is provided by a built-in extension called "Opera Touch Background", which is responsible for communicating with the mobile counterpart. The extension contains its own manifest file, which specifies its behavior, as well as all the necessary permissions, including the "externally_connectable" property, which declares which other web pages and extensions can connect to it.
Domains that can communicate with the extension must match the "* "pattern.flow.opera.com" and". flow.op-test.net", controlled by the browser developer itself. However, researchers at Guardio Labs found a "forgotten" version of the My Flow start page on the domain "web.flow.opera.com".
The page found is visually similar to the current version, but differs in the absence of a content security policy tag and the presence of a script tag that calls a JavaScript file without checking its integrity.
"This is exactly what an attacker needs — an insecure, forgotten and vulnerable resource for code injection that has access to the browser API with very high permissions," the report from Guardio Labs says.
The final chain of attack consists in creating a special extension that disguises itself as a mobile device to communicate with the victim's computer, and transmitting encrypted malicious code through a modified JavaScript file for subsequent execution, by simply clicking the user on the screen.
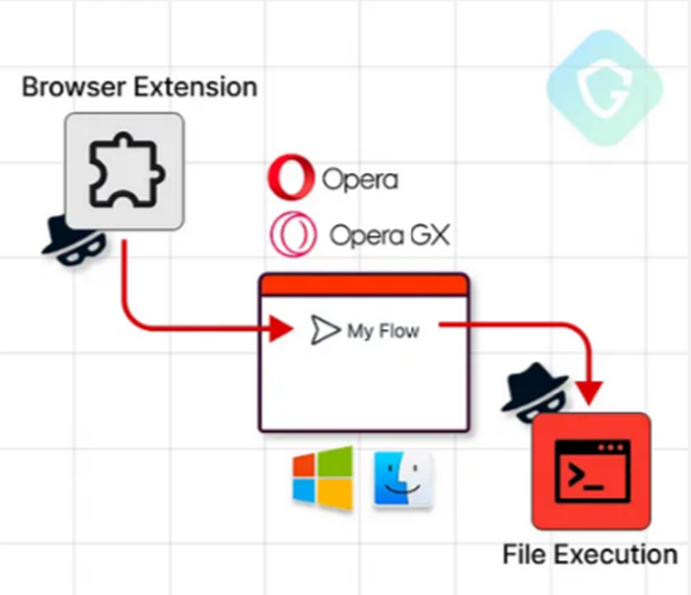
MyFlaw attack scheme
"Despite working in isolated environments, extensions can be powerful tools for hackers, allowing them to steal information and break the security boundaries of the browser," the researchers said.
Opera representatives fixed the vulnerability on November 22, 2023, just 5 days after the disclosure. The developers have also implemented server-side fixes and taken a number of steps to prevent similar issues in the future. For security reasons, it was decided to publicly disclose the vulnerability only now, so that as many users as possible could get the necessary update in auto mode.
Security researchers from Guardio Labs discovered a serious flaw in the Opera web browser for Windows and macOS operating systems. With its help, attackers can run absolutely any files, including malicious ones, in the basic operating system of the computer.
Experts assigned the vulnerability the code name " MyFlaw "(a play on words, literally translated" my vulnerability"), as it is associated with the" My Flow"function, which allows you to synchronize messages and files between mobile and desktop devices.
To implement the vulnerability, a browser extension controlled by an attacker is used, which actually bypasses its sandbox and the entire operation process. The issue affects both the regular version of Opera and Opera GX.
My Flow has a chat-like interface and is used to share notes and files between your smartphone and desktop computer. As it turned out, files from this chat can be launched directly through the browser's web interface, outside the browser's security limits.
The work of My Flow is provided by a built-in extension called "Opera Touch Background", which is responsible for communicating with the mobile counterpart. The extension contains its own manifest file, which specifies its behavior, as well as all the necessary permissions, including the "externally_connectable" property, which declares which other web pages and extensions can connect to it.
Domains that can communicate with the extension must match the "* "pattern.flow.opera.com" and". flow.op-test.net", controlled by the browser developer itself. However, researchers at Guardio Labs found a "forgotten" version of the My Flow start page on the domain "web.flow.opera.com".
The page found is visually similar to the current version, but differs in the absence of a content security policy tag and the presence of a script tag that calls a JavaScript file without checking its integrity.
"This is exactly what an attacker needs — an insecure, forgotten and vulnerable resource for code injection that has access to the browser API with very high permissions," the report from Guardio Labs says.
The final chain of attack consists in creating a special extension that disguises itself as a mobile device to communicate with the victim's computer, and transmitting encrypted malicious code through a modified JavaScript file for subsequent execution, by simply clicking the user on the screen.

MyFlaw attack scheme
"Despite working in isolated environments, extensions can be powerful tools for hackers, allowing them to steal information and break the security boundaries of the browser," the researchers said.
Opera representatives fixed the vulnerability on November 22, 2023, just 5 days after the disclosure. The developers have also implemented server-side fixes and taken a number of steps to prevent similar issues in the future. For security reasons, it was decided to publicly disclose the vulnerability only now, so that as many users as possible could get the necessary update in auto mode.

