Teacher
Professional
- Messages
- 2,669
- Reaction score
- 819
- Points
- 113
Who is behind the hidden backdoor that Cloudflare is helping with malicious purposes?
The Cisco Talos discovered a large-scale espionage campaign targeting a nonprofit charity in Saudi Arabia. The campaign, which began in March 2021, used a previously unknown custom backdoor called Zardoor. The malware downloaded data twice a month from the systems of a compromised organization, which Cisco chose not to name.
A special feature of the attack is the use of modified reverse proxy tools and the ability to remain undetected for almost three years, which indicates a high level of training for attackers.
Cisco Talos specialists noted that the use of a reverse proxy server is typical for some hacker groups from China. This raises questions about Beijing's involvement in the operation, although the target of the attack does not correspond to the interests of Chinese cyber espionage groups. However, the use of reverse proxies is also a common practice for groups from other countries, which makes the technology a popular tool for providing hidden access to secure networks (RDP, domain controllers, database servers, etc.) and data transmission through encrypted channels.
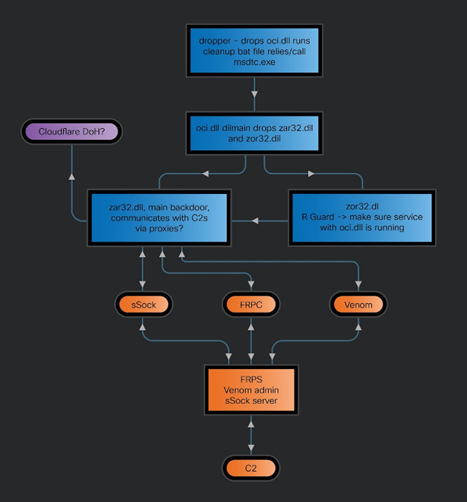
Zardoor Modules
At the moment, the Zardoor attack vector is unknown. Experts found out that the attackers created a command and control mechanism for the attack, using the open-source Fast Reverse Proxy (FRP) reverse proxy server tool, a customized version of the Socks Linux and Venom server, as well as a penetration testing tool for conducting security audits.
After establishing a foothold in the victim's network, cybercriminals used Windows Management Instrumentation (WMI) for Lateral Movement and Zardoor implementation.
The Zardoor malware installs a permanent backdoor, allowing attackers to execute commands such as updating malicious code or exfiltrating data through a specially designed module. Zar32.dll. The component that works through the Socks or HTTPS proxy is disguised as legitimate network applications and uses IP addresses used by CloudFlare DNS services.
Cisco has added Zardoor malware detection to its enterprise security tools and published signs of compromise, which is likely to prompt the rest of the vendor community to add similar detection and response capabilities.
To increase security, even when using security products from other manufacturers, experts recommend following standard procedures for responding to new threats, checking systems and network activity logs for signs of infection, and ensuring that antivirus and intrusion detection systems are updated with the latest malware signatures.
The Cisco Talos discovered a large-scale espionage campaign targeting a nonprofit charity in Saudi Arabia. The campaign, which began in March 2021, used a previously unknown custom backdoor called Zardoor. The malware downloaded data twice a month from the systems of a compromised organization, which Cisco chose not to name.
A special feature of the attack is the use of modified reverse proxy tools and the ability to remain undetected for almost three years, which indicates a high level of training for attackers.
Cisco Talos specialists noted that the use of a reverse proxy server is typical for some hacker groups from China. This raises questions about Beijing's involvement in the operation, although the target of the attack does not correspond to the interests of Chinese cyber espionage groups. However, the use of reverse proxies is also a common practice for groups from other countries, which makes the technology a popular tool for providing hidden access to secure networks (RDP, domain controllers, database servers, etc.) and data transmission through encrypted channels.

Zardoor Modules
At the moment, the Zardoor attack vector is unknown. Experts found out that the attackers created a command and control mechanism for the attack, using the open-source Fast Reverse Proxy (FRP) reverse proxy server tool, a customized version of the Socks Linux and Venom server, as well as a penetration testing tool for conducting security audits.
After establishing a foothold in the victim's network, cybercriminals used Windows Management Instrumentation (WMI) for Lateral Movement and Zardoor implementation.
The Zardoor malware installs a permanent backdoor, allowing attackers to execute commands such as updating malicious code or exfiltrating data through a specially designed module. Zar32.dll. The component that works through the Socks or HTTPS proxy is disguised as legitimate network applications and uses IP addresses used by CloudFlare DNS services.
Cisco has added Zardoor malware detection to its enterprise security tools and published signs of compromise, which is likely to prompt the rest of the vendor community to add similar detection and response capabilities.
To increase security, even when using security products from other manufacturers, experts recommend following standard procedures for responding to new threats, checking systems and network activity logs for signs of infection, and ensuring that antivirus and intrusion detection systems are updated with the latest malware signatures.

