Which is better to choose: Wireguard or OpenVPN? Linus Torvalds' Favorite VPN
VPN technologies are rarely the subject of much scrutiny: there is and is. Wireguard creator Jason A. Donenfeld was lucky after Linus Torvalds' harshly laudatory assessment of the code quality.
Can I just once again state my love for it and hope it gets merged soon? Maybe the code isn’t perfect, but I’ve skimmed it, and compared to the horrors that are OpenVPN and IPSec, it’s a work of art.
Shortly thereafter, Wireguard ended up in the upstream of the stable Linux kernel. Why is Wireguard so great and different from other VPNs?
Encryption: Differences between Wireguard and OpenVPN
Wireguard takes a minimalist and no-nonsense approach to encryption, deliberately eliminating the flexibility and protocol choices that are too expensive. If there is no choice of protocols, there is no negotiation process in which security holes are traditionally found. In addition, SSL / TLS vulnerabilities, coming in an even stream, are also not in favor of a wealth of choice.
Wireguard encryption protocols
- Brevity is the sister of talent - 4000 lines of code has become almost a hallmark of Wireguard.
- A deterministic set of modern cryptographic algorithms:
- ChaCha20 for symmetric encryption is also used in the AEAD structure of RFC7539;
- Poly1305 for authentication, also used in the AEAD structure of RFC7539;
- Curve25519 - elliptic curve for the Diffie-Hellman secure key exchange protocol;
- Blake2 - in RFC7693 for the corresponding hash function;
- SipHash2-4 - a pseudo-random function for finding the decrypted public keys of the initiator of the communication session;
- HKDF - for key extraction;
- UDP - as a transport layer protocol;
- Perfect forward secrecy is the principle of preventing compromise of session keys.
Unlike OpenVPN, Wireguard does not use X.509 certificates and has no associated issues. Instead, Wireguard uses asymmetric public and private key encryption.
OpenVPN encryption protocols
OpenVPN supports many cryptographic algorithms using the
OpenSSL library. More specifically, the following algorithms are used for encryption and authentication. Such functions are available for hash sums. OpenVPN in conjunction with OpenSSL supports PKI standards RSA, DSA and ECDSA, but not all of them are suitable for all user scenarios. For example, ECDSA keys have not yet received widespread support from root CAs.
Code:
aes-128-cbc aes-128-ecb aes-192-cbc aes-192-ecb
aes-256-cbc aes-256-ecb aria-128-cbc aria-128-cfb
aria-128-cfb1 aria-128-cfb8 aria-128-ctr aria-128-ecb
aria-128-ofb aria-192-cbc aria-192-cfb aria-192-cfb1
aria-192-cfb8 aria-192-ctr aria-192-ecb aria-192-ofb
aria-256-cbc aria-256-cfb aria-256-cfb1 aria-256-cfb8
aria-256-ctr aria-256-ecb aria-256-ofb base64
bf bf-cbc bf-cfb bf-ecb
bf-ofb camellia-128-cbc camellia-128-ecb camellia-192-cbc
camellia-192-ecb camellia-256-cbc camellia-256-ecb cast
cast-cbc cast5-cbc cast5-cfb cast5-ecb
cast5-ofb des des-cbc des-cfb
des-ecb des-ede des-ede-cbc des-ede-cfb
des-ede-ofb des-ede3 des-ede3-cbc des-ede3-cfb
des-ede3-ofb des-ofb des3 desx
idea idea-cbc idea-cfb idea-ecb
idea-ofb rc2 rc2-40-cbc rc2-64-cbc
rc2-cbc rc2-cfb rc2-ecb rc2-ofb
rc4 rc4-40 rc5 rc5-cbc
rc5-cfb rc5-ecb rc5-ofb seed
seed-cbc seed-cfb seed-ecb seed-ofb
sm4-cbc sm4-cfb sm4-ctr sm4-ecb
(1:701)$ openssl dgst --list
Supported digests:
Code:
-blake2b512 -blake2s256 -md4
-md5 -md5-sha1 -mdc2
-ripemd -ripemd160 -rmd160
-sha1 -sha224 -sha256
-sha3-224 -sha3-256 -sha3-384
-sha3-512 -sha384 -sha512
-sha512-224 -sha512-256 -shake128
-shake256 -sm3 -ssl3-md5
-ssl3-sha1 -whirlpool
- UDP / TCP - as a transport layer protocol;
- Perfect forward secrecy is the principle of preventing compromise of session keys.
Conclusions on encryption and security standards
Wireguard is
architecturally more secure due to the fact that the attack surface is significantly smaller compared to OpenVPN. Nevertheless, OpenVPN is considered very secure and reliable, having undergone independent code audits many times. As a result, OpenVPN
benefits from a conservative VPN solution.
At the same time, the lack of flexibility and choice of encryption method creates significant obstacles for the use of Wireguard in the corporate segment of VPN users. Imagine a typical situation for our employees in which employees connect to a work network via VPN from various devices. In such a situation, the lack of flexibility and choice will create many more problems than it can eliminate them.
Performance comparison
Since Wireguard is implemented in kernel space and OpenVPN is in user space, the former should have a speed advantage. This is due to the fact that packages are constantly copied from one space to another, and in addition, a constant background OpenVPN service is required.
All this needs to be checked in practice, fortunately there are many speed measurements for VPN tunnels. For starters, you can take a look at the VPN derby results from the author of Wireguard himself. Here are some details and measurement results.
- Technologies - IPSEC, OpenVPN and Wireguard;
- Processors IntelCore i7-3820QM and Intel Core i7-5200U;
- Network cards - Intel 82579LM and Intel I218LM gigabit Ethernet;
Comparison of VPN performance by Jason A. Donenfeld
In both throughput and ping response tests, Wireguard significantly outperformed OpenVPN, as well as two IPSec variations. In addition, during the throughput test using OpenVPN and IPSec, CPU utilization
reached 100%. At the same time, the use of Wireguard did not load the central processor so much, thereby making it possible to completely utilize the resources of the Gigabit Ethernet network card.
It is natural to assume that the author of Wireguard may be biased in scripting and interpreting the results of measuring the performance of VPN technologies. Therefore, it makes sense to look at other speed tests of different VPNs. Fortunately, all that is needed for this is a VPS server, VPN and iperf3 package.
But other similar tests show the superiority of Wireguard in performance tests.
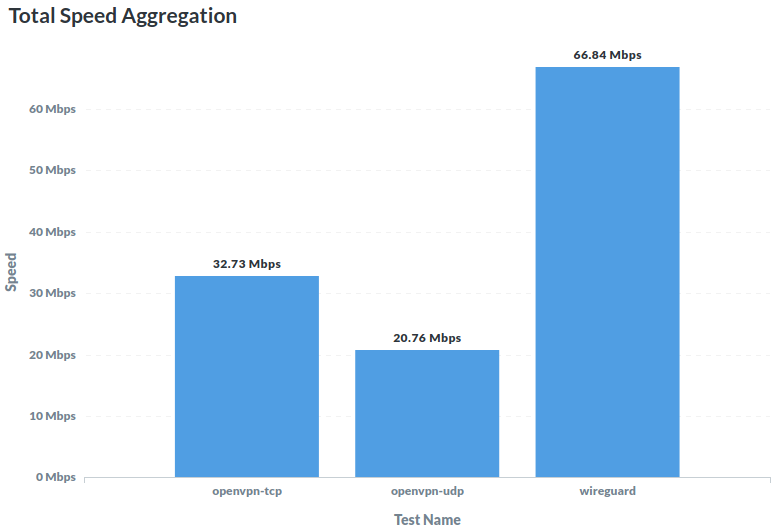
Wireguard vs. OpenVPN Performance Comparison
An unexpected fact is that openvpn-tcp is faster than openvpn-udp, but upon closer inspection, everything falls into place. TCP stream has fewer completed tests than UDP. Anyway, here Wireguard shows the best performance results.
In the same series of tests, it is interesting to compare the speed of a VPN connection depending on the number of open sockets. With an increase in their number, Wireguard's performance drops abruptly, although it continues to be higher than openvpn-tcp and openvpn-udp.
Comparison of Wireguard and OpenVPN performance depending on the number of open sockets. TestID 0-600 corresponds to openvpn-udp, 700-1200 to openvpn-tcp and 1300-1800 to Wireguard
Conclusions on VPN connection speed
Synthetic speed tests from various authors using the iperf3 package suggest
Wireguard is faster than OpenVPN.
Data confidentiality
VPN protocols place much more emphasis on connection security than confidentiality. However, the ability to preserve anonymity also matters - who wants to write explanatory notes on the fact of downloading an Oracle textbook, or a Cisco topology emulator? Nothing betrays the fact of an offense as well as the user's IP address.
Wireguard's settings explicitly contain the IP addresses of users and this circumstance will not allow them to go unnoticed after the server is interested in law enforcement agencies. Of course, you will not be able to read the network traffic, but you can identify the participants in the secure connection.
Setting up a Wireguard secure connection itself is pretty straightforward. Installation first.
Code:
(1:530)$ sudo emerge -av wireguard-modules wireguard-tools
These are the packages that would be merged, in order:
Calculating dependencies... done!
Code:
[binary N ] net-dns/openresolv-3.11.0 USE="(-selinux)"
[binary N ] virtual/resolvconf-1
[ebuild N ] net-vpn/wireguard-modules-1.0.20201221 USE="module -debug -module-src"
[binary N ] net-vpn/wireguard-tools-1.0.20200827 USE="wg-quick"
Would you like to merge these packages? [Yes/No]
We create public and private keys.
Code:
(1:531)$ wg genkey | tee privatekey | wg pubkey > publickey
Next, you need to configure the /etc/wireguard/wg0.conf file.
Code:
/etc/wireguard/wg0.conf
[Interface]
Address = 10.0.0.1/24, fdc9:1f28:04d7:9ee9::1/64
SaveConfig = true
ListenPort = 51820
PrivateKey = 2JtKAUFzecmgIVzbscQh3iUZrZanxIzvbejcIkvC5Hk= #PEER_A_PRIVATE_KEY
[Peer]
PublicKey = rgqd1cHKgRWX3IkYYSlrKA/SW3qZUhSJMqwTq4+3eFs= #PEER_B_PUBLIC_KEY
PresharedKey = PEER_A-PEER_B-PRESHARED_KEY
AllowedIPs = 10.0.0.2/32, fdc9:1f28:04d7:9ee9::2/128
Endpoint = pb.example.com:51280
The second participant connection must be set up at the same file by specifying it in your private key and public key participant A. To connect each party fulfills wg-quick up interface_name.
This shows that when setting the IP address Wireguard or host name specified in an explicit form and are visible in system log files and SNMP tables until the server is rebooted.
OpenVPN better protects the confidentiality of client connections, since it does not require setting the IP addresses or the network name of client computers before establishing a secure connection.
Conclusions on data privacy
In this nomination, OpenVPN has a definite advantage due to the fact that only Wireguard assumes storing users' IP addresses on a VPN server for a long time.
Bottom Line: Which VPN to Choose?
There are a myriad of custom VPN use cases out there, and the same recommendation is unlikely to be good for everyone. Accordingly, for different scenarios, two groups can be distinguished with the most suitable VPN solution.
- If you are a regular user;
- You need a VPN to bypass any ridiculous RKN restrictions;
- speed matters to you, for example, for file sharing, or the operation of your application;
Use Wireguard.
- Business users of medium and large companies using VPN for remote access to the internal network;
- business users who provide remote access via VPN to IT resources containing confidential data or trade secrets;
- anyone who needs a reliable and time-tested VPN solution;
It's better to use OpenVPN.
Well, you already know which VPS to take for VPN.
More info:
This guide compares WireGuard vs OpenVPN in the areas of speed, security, privacy, encryption, audits, OS support, and more.

restoreprivacy.com