Carding Forum
Professional
- Messages
- 2,788
- Reaction score
- 1,323
- Points
- 113
Google Ads is used to run a sophisticated campaign.
In recent weeks, Threat Down experts have seen a surge in malicious ads on Google aimed at IT professionals. The campaign aims to gain access to victims systems and steal confidential data.
Research has shown the use of a single infrastructure to distribute two malicious programs: MadMxShell and WorkersDevBackdoor. The most interesting discovery was that the MadMxShell C2 server is directly connected to the WorkersDevBackdoor delivery infrastructure. Both malware programs are capable of collecting and stealing confidential data, as well as providing initial access for ransomware operators.
Most malicious ads are associated with IP scanners and redirect to the infrastructure, which the researchers called goodgoog1e. The name comes from the attacker's email address, which binds all domains together.
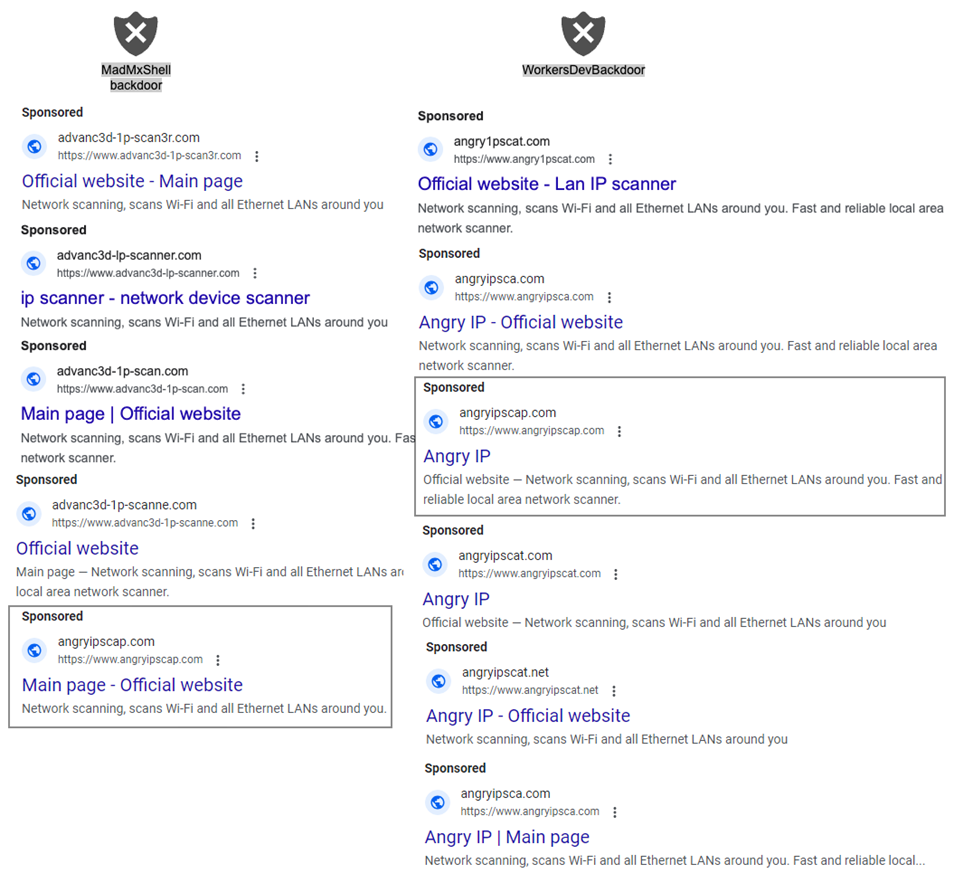
Malicious Google Ads
All infection chains come from the same source (goodgoog1e), but from different advertising accounts. One of the ads was used to deliver both malware via the "angryipo[.]org" domain.
MadMxShell uses several obfuscated scripts to load the payload, including a complex script that creates a one-liner for automatic loading. WorkersDevBackdoor is hosted on Dropbox with Rotating URLs dynamically uploaded via "azureedge [.] net".
In a recent campaign, the MadMxShell C2 server was changed from "litterbolo [.] com" to "getstorege [.] com". The domain "getstorege [.] com" was registered to the same email address used for both malware delivery infrastructure.
One of the WorkersDevBackdoor samples included a PowerShell script that checks for certain programs, such as RDP, TeamViewer, and others, to determine whether to finish installing malware.
PowerShell scripts that check whether a computer is connected to a domain allow attackers to avoid alarms in sandboxes or virtual machines. This is a good reminder that a file scanned statically or even running in a sandbox may be legitimate simply because the conditions for its proper execution were not met.
Source
In recent weeks, Threat Down experts have seen a surge in malicious ads on Google aimed at IT professionals. The campaign aims to gain access to victims systems and steal confidential data.
Research has shown the use of a single infrastructure to distribute two malicious programs: MadMxShell and WorkersDevBackdoor. The most interesting discovery was that the MadMxShell C2 server is directly connected to the WorkersDevBackdoor delivery infrastructure. Both malware programs are capable of collecting and stealing confidential data, as well as providing initial access for ransomware operators.
- MadMxShell, first described in April, is distributed through malicious ads for IP scanners. The program uses DLL hijacking and DNS to communicate with the C2 server via OneDrive.exe.
- WorkersDevBackdoor has a more complex history and was described by eSentire. The special feature is that the payload is packaged in a password-protected archive. The payload is linked to the ThunderShell RAT and Parcel RAT Trojans. WorkersDevBackdoor works through the NSIS installer with an encrypted 7z archive and places the payload on Dropbox.
Most malicious ads are associated with IP scanners and redirect to the infrastructure, which the researchers called goodgoog1e. The name comes from the attacker's email address, which binds all domains together.

Malicious Google Ads
All infection chains come from the same source (goodgoog1e), but from different advertising accounts. One of the ads was used to deliver both malware via the "angryipo[.]org" domain.
MadMxShell uses several obfuscated scripts to load the payload, including a complex script that creates a one-liner for automatic loading. WorkersDevBackdoor is hosted on Dropbox with Rotating URLs dynamically uploaded via "azureedge [.] net".
In a recent campaign, the MadMxShell C2 server was changed from "litterbolo [.] com" to "getstorege [.] com". The domain "getstorege [.] com" was registered to the same email address used for both malware delivery infrastructure.
One of the WorkersDevBackdoor samples included a PowerShell script that checks for certain programs, such as RDP, TeamViewer, and others, to determine whether to finish installing malware.
PowerShell scripts that check whether a computer is connected to a domain allow attackers to avoid alarms in sandboxes or virtual machines. This is a good reminder that a file scanned statically or even running in a sandbox may be legitimate simply because the conditions for its proper execution were not met.
Source

