Brother
Professional
- Messages
- 2,590
- Reaction score
- 526
- Points
- 113
How does one of the largest fraudulent associations in the CIS work and what can you do to protect yourself?
In their recently published report, ESET experts told about a group of scammers "Gipsy Team", who were dubbed"Neanderthals". The group is responsible for developing and maintaining a fraudulent Telegram bot called Telekopye, which helps cybercriminals deceive people on online platforms aimed at CIS countries. The bot is capable of creating phishing sites, emails, SMS messages, and much more.
In August, ESET already published a detailed report on Telekopye, which we also carefully reviewed and made a brief squeeze . However, scammers do not sit still and constantly evolve, and therefore the release of the second part of the investigation was not long in coming.
ESET researchers studied the methods of recruiting new members to the Neanderthal group, the training process, as well as the use of various deception schemes and other aspects of the activities of intruders, which we will discuss below, providing readers with useful information on how to recognize online fraud and not become one of the victims of scammers.
Neanderthals is gaining new members through advertising on various channels, including underground forums. There they promise honest 75% of the money earned, stable operation for three years and point out the high quality of phishing sites used, completely repeating the design of the original sites of Avito, Yula and SDEK.
After contacting a potential employer via a Telegram bot and then approving the application, newcomers get access to group chats and channels where rules and guidelines are stored.
In the work of Neanderthals, there are three main scenarios of fraud: "seller", "buyer" and "refund". Each scenario has its own characteristics. For example, in the case of the seller's scenario, scammers offer victims (the so-called "Mammoths") some interesting product at an attractive price and redirect them to a phishing site for payment.
"Unlike a legitimate web page, this page asks for an online banking login, credit card details, or other sensitive information. If the Mammoth enters this data, the phishing website automatically steals it," the ESET researchers explain.
It is interesting to note that data stolen from phishing sites is not made available to the specific Neanderthal responsible for mining them. They are placed in a separate database and processed by other members of the group. This is probably done to achieve maximum efficiency: each attacker is engaged exclusively in his own business, akin to a small cog in a giant mechanism.
In the scenario with a buyer, as you might guess, scammers show interest in a particular product that the Mammoth has put up for sale. The Neanderthal initiates a correspondence with the seller, in which he uses social engineering to gain the trust of the Mammoth, and then sends him a phishing link with the promise that after specifying his bank details, the money for the product will automatically be credited to the seller's account.
The refund scenario is particularly insidious, as scammers can double-cross the Mammoth. First, pretending to be a seller and receiving money with bank data from the victim, and then pretending to be the site's support service, which promises to return the money to the Mammoth in exchange for another click on a phishing link, where even more personal data is collected from the victim.
The Neanderthal documentation, which is used both for training beginners and as a cheat sheet for experienced scammers, includes various images with possible correspondence options, graphs, quick guides, and even very complex documents.
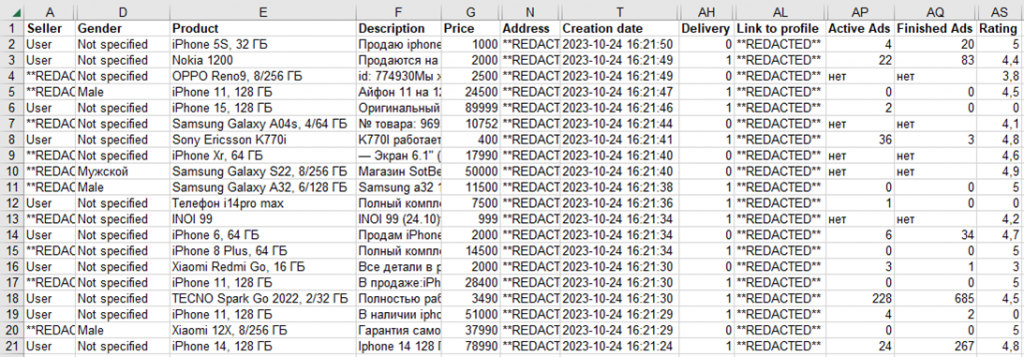
Fraudsters usually find potential victims through web scrappers, exporting data from the platform they are interested in to an Excel spreadsheet and then carefully selecting the Mammoth for a number of key parameters. So, a high user rating and extensive experience in interacting with the site may indicate that they are more likely to recognize fraud, which means that they should not spend time on it.
According to the working script, Neanderthals can only tolerate a certain level of resistance from Mammoths. If scammers believe that the scam is unlikely to succeed, they quickly find another target. However, if they feel that they have almost won, they always try to put the squeeze on the victim, giving it their full attention and convincingly dispelling any fears.
According to the information above, it may seem that Neanderthals only target CIS sites, although this is not entirely true. ESET specialists found prepared tables with the translation of various duty phrases from Russian into other popular languages, which means that scammers work all over the world.
It is worth noting that Neanderthals do not use the newfangled artificial intelligence in their operations, which can greatly simplify the generation of new fraud scenarios. The group prefers traditional methods of communication and, it should be said, comes out quite successfully.
"Neanderthals realize that their groups are full of 'rats' (such as law enforcement officers or researchers). Therefore, they strictly adhere to the rules prohibiting the search for information that could identify other members of the group. Violation of such rules may well lead to a ban," ESET researchers report.
In an interview with one of the administrators of Telekopye, conducted at the end of 2020 and discovered by ESET specialists, a high-ranking Neanderthal shares his vision of online fraud in the future and emphasizes that despite numerous restrictions on the part of platforms, it is impossible to completely eradicate this kind of fraud, and that it will always exist.
Based on this bold position, we will allow ourselves to give a number of specific recommendations that can protect both you and your loved ones from fraud:
We hope that thanks to the information provided about the methods of fraudsters work and the above-mentioned protection tips, you will feel safer and more confident on the Internet. Caution and awareness in the online space are key factors in preventing such threats. Remember that knowledge is your best defense in the fight against cybercrime.
In their recently published report, ESET experts told about a group of scammers "Gipsy Team", who were dubbed"Neanderthals". The group is responsible for developing and maintaining a fraudulent Telegram bot called Telekopye, which helps cybercriminals deceive people on online platforms aimed at CIS countries. The bot is capable of creating phishing sites, emails, SMS messages, and much more.
In August, ESET already published a detailed report on Telekopye, which we also carefully reviewed and made a brief squeeze . However, scammers do not sit still and constantly evolve, and therefore the release of the second part of the investigation was not long in coming.
ESET researchers studied the methods of recruiting new members to the Neanderthal group, the training process, as well as the use of various deception schemes and other aspects of the activities of intruders, which we will discuss below, providing readers with useful information on how to recognize online fraud and not become one of the victims of scammers.
Neanderthals is gaining new members through advertising on various channels, including underground forums. There they promise honest 75% of the money earned, stable operation for three years and point out the high quality of phishing sites used, completely repeating the design of the original sites of Avito, Yula and SDEK.
After contacting a potential employer via a Telegram bot and then approving the application, newcomers get access to group chats and channels where rules and guidelines are stored.
In the work of Neanderthals, there are three main scenarios of fraud: "seller", "buyer" and "refund". Each scenario has its own characteristics. For example, in the case of the seller's scenario, scammers offer victims (the so-called "Mammoths") some interesting product at an attractive price and redirect them to a phishing site for payment.
"Unlike a legitimate web page, this page asks for an online banking login, credit card details, or other sensitive information. If the Mammoth enters this data, the phishing website automatically steals it," the ESET researchers explain.
It is interesting to note that data stolen from phishing sites is not made available to the specific Neanderthal responsible for mining them. They are placed in a separate database and processed by other members of the group. This is probably done to achieve maximum efficiency: each attacker is engaged exclusively in his own business, akin to a small cog in a giant mechanism.
In the scenario with a buyer, as you might guess, scammers show interest in a particular product that the Mammoth has put up for sale. The Neanderthal initiates a correspondence with the seller, in which he uses social engineering to gain the trust of the Mammoth, and then sends him a phishing link with the promise that after specifying his bank details, the money for the product will automatically be credited to the seller's account.
The refund scenario is particularly insidious, as scammers can double-cross the Mammoth. First, pretending to be a seller and receiving money with bank data from the victim, and then pretending to be the site's support service, which promises to return the money to the Mammoth in exchange for another click on a phishing link, where even more personal data is collected from the victim.
The Neanderthal documentation, which is used both for training beginners and as a cheat sheet for experienced scammers, includes various images with possible correspondence options, graphs, quick guides, and even very complex documents.
Fraudsters usually find potential victims through web scrappers, exporting data from the platform they are interested in to an Excel spreadsheet and then carefully selecting the Mammoth for a number of key parameters. So, a high user rating and extensive experience in interacting with the site may indicate that they are more likely to recognize fraud, which means that they should not spend time on it.

According to the working script, Neanderthals can only tolerate a certain level of resistance from Mammoths. If scammers believe that the scam is unlikely to succeed, they quickly find another target. However, if they feel that they have almost won, they always try to put the squeeze on the victim, giving it their full attention and convincingly dispelling any fears.
According to the information above, it may seem that Neanderthals only target CIS sites, although this is not entirely true. ESET specialists found prepared tables with the translation of various duty phrases from Russian into other popular languages, which means that scammers work all over the world.
It is worth noting that Neanderthals do not use the newfangled artificial intelligence in their operations, which can greatly simplify the generation of new fraud scenarios. The group prefers traditional methods of communication and, it should be said, comes out quite successfully.
"Neanderthals realize that their groups are full of 'rats' (such as law enforcement officers or researchers). Therefore, they strictly adhere to the rules prohibiting the search for information that could identify other members of the group. Violation of such rules may well lead to a ban," ESET researchers report.
In an interview with one of the administrators of Telekopye, conducted at the end of 2020 and discovered by ESET specialists, a high-ranking Neanderthal shares his vision of online fraud in the future and emphasizes that despite numerous restrictions on the part of platforms, it is impossible to completely eradicate this kind of fraud, and that it will always exist.
Based on this bold position, we will allow ourselves to give a number of specific recommendations that can protect both you and your loved ones from fraud:
- Be careful with payment links. Never click on suspicious links, especially those that come from strangers on the Internet. Legitimate payment systems and online platforms do not require entering bank account details, CVV codes, or other information via third-party links.
- Check the authenticity of websites. Before entering personal or financial data, make sure that the site is authentic. Check its URL, use of the HTTPS protocol, and whether it has a security certificate. by mistake or grammatical errors.
- Avoid correspondence outside of official platforms. If a seller or buyer insists on communicating outside of the official platform, this may be a red flag. It is best to continue communication and transactions through trusted and secure platforms, otherwise just block such a suspicious contact.
- Don't trust suggestions that seem too good to be true. If the price of an item is significantly lower than the market price or the offer seems unrealistically profitable, this may be a sign of fraud. Always conduct a thorough review before making transactions.
- Be careful with non-standard payment methods. Fraudsters often offer payment through non-standard channels or require prepayment for goods and services. Avoid such transactions and stick to the usual payment methods through trusted services.
We hope that thanks to the information provided about the methods of fraudsters work and the above-mentioned protection tips, you will feel safer and more confident on the Internet. Caution and awareness in the online space are key factors in preventing such threats. Remember that knowledge is your best defense in the fight against cybercrime.
