Teacher
Professional
- Messages
- 2,669
- Reaction score
- 819
- Points
- 113
The vulnerability affects more than 1 million Tesla Model 3 vehicles worldwide"
Security researchers Talal Haj Bakri and Tommy Misk have demonstrated how they can conduct a phishing attack to compromise a Tesla owner's account, unlock the car, and start the engine. It is noted that the attack is relevant for the latest version of the Tesla app 4.30.6 and the car firmware version 11.1 2024.2.7.
The authors of the study informed Tesla about the vulnerability found, pointing out the insufficient security of the procedure for linking a car to a new phone. However, the manufacturer considered the error insignificant.
The Flipper Zero gadget was used to demonstrate the attack, but it can also be carried out using other devices – a computer, Raspberry Pi, or Android smartphone.
The attack begins with the deployment of a fake WiFi network named "Tesla Guest" at a Tesla charging station. This SSID is usually found in Tesla service centers and is well known to car owners. After connecting to the fake network, the victim sees a phishing login page for the Tesla account, where he enters his credentials, which instantly get to the attacker.
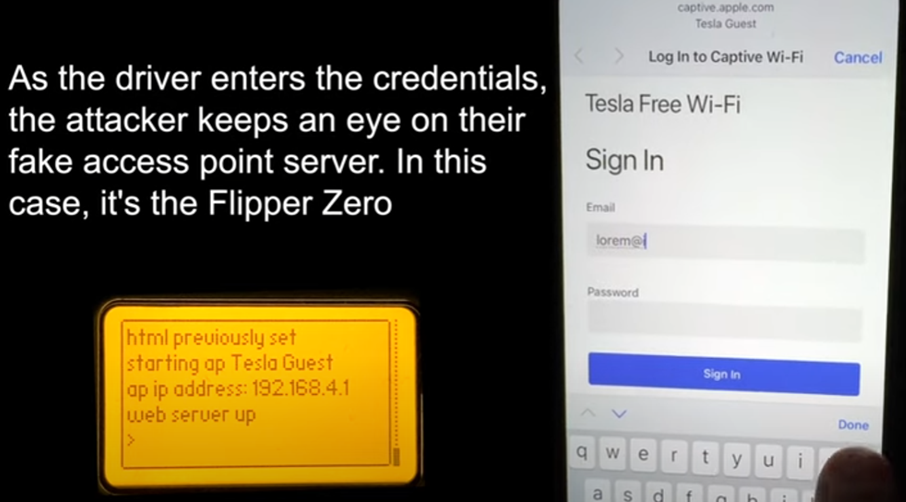
Phishing process
After receiving the credentials, the attacker requests a one-time password to bypass two-factor authentication (2FA) and gains access to the Tesla app, which allows you to track the car's location in real time.
After gaining access to the Tesla account, an attacker can add a new Phone Key. To do this, you need to be in close proximity to the car. The Phone Key works through the Tesla mobile app and the owner's smartphone, providing the ability to automatically close and open the car via a secure Bluetooth connection.
It is worth noting that after adding a new Phone Key, the owner of a Tesla does not receive notifications about this in the app, and no warnings are displayed on the car's touch screen. With the new Phone Key, an attacker can unlock the car and activate all its systems, allowing them to drive away as if they were the owner.
The attack was successfully carried out on the Tesla Model 3. The researchers proposed to improve security by requiring a physical key card (RFID card) of Tesla when adding a new Phone Key to add an additional layer of authentication.
Tesla cars also use key cards — thin RFID cards that need to be placed in an RFID reader on the center console to start the car. Although they are more secure, Tesla considers them as a backup option if the Phone Key is unavailable or the battery is low.
In response to the vulnerability report, Tesla said that the system behavior in question is intended, and the Tesla Model 3 user guide does not specify that an RFID card is required to add a Phone Key. Tesla did not respond to requests for comment or plans to release software updates to prevent such attacks.
Security researchers Talal Haj Bakri and Tommy Misk have demonstrated how they can conduct a phishing attack to compromise a Tesla owner's account, unlock the car, and start the engine. It is noted that the attack is relevant for the latest version of the Tesla app 4.30.6 and the car firmware version 11.1 2024.2.7.
The authors of the study informed Tesla about the vulnerability found, pointing out the insufficient security of the procedure for linking a car to a new phone. However, the manufacturer considered the error insignificant.
The Flipper Zero gadget was used to demonstrate the attack, but it can also be carried out using other devices – a computer, Raspberry Pi, or Android smartphone.
The attack begins with the deployment of a fake WiFi network named "Tesla Guest" at a Tesla charging station. This SSID is usually found in Tesla service centers and is well known to car owners. After connecting to the fake network, the victim sees a phishing login page for the Tesla account, where he enters his credentials, which instantly get to the attacker.

Phishing process
After receiving the credentials, the attacker requests a one-time password to bypass two-factor authentication (2FA) and gains access to the Tesla app, which allows you to track the car's location in real time.
After gaining access to the Tesla account, an attacker can add a new Phone Key. To do this, you need to be in close proximity to the car. The Phone Key works through the Tesla mobile app and the owner's smartphone, providing the ability to automatically close and open the car via a secure Bluetooth connection.
It is worth noting that after adding a new Phone Key, the owner of a Tesla does not receive notifications about this in the app, and no warnings are displayed on the car's touch screen. With the new Phone Key, an attacker can unlock the car and activate all its systems, allowing them to drive away as if they were the owner.
The attack was successfully carried out on the Tesla Model 3. The researchers proposed to improve security by requiring a physical key card (RFID card) of Tesla when adding a new Phone Key to add an additional layer of authentication.
Tesla cars also use key cards — thin RFID cards that need to be placed in an RFID reader on the center console to start the car. Although they are more secure, Tesla considers them as a backup option if the Phone Key is unavailable or the battery is low.
In response to the vulnerability report, Tesla said that the system behavior in question is intended, and the Tesla Model 3 user guide does not specify that an RFID card is required to add a Phone Key. Tesla did not respond to requests for comment or plans to release software updates to prevent such attacks.

