Father
Professional
- Messages
- 2,602
- Reaction score
- 837
- Points
- 113
Even experienced specialists do not see the catch and voluntarily let hackers into corporate networks.
Recently, cybersecurity researchers at Malwarebytes observed an ongoing wave of cyberattacks targeting system administrators through fraudulent advertising of PuTTY and FileZilla utilities. The ad is served as sponsored results in the Google search engine and is aimed at users from North America, serving as a clever trap for downloading the Nitrogen malware.
Nitro is used by attackers for initial access to private networks, subsequent data theft, and distribution of ransomware, including ALPHV/BlackCat cryptographic programs.
At the moment, despite numerous requests from specialists, Google has not yet taken any active actions to block this malicious operation.
The attack consists of several stages, each of which will be discussed later.
The first stage. Attract victims through fraudulent ads in Google search results that lead to fake sites.
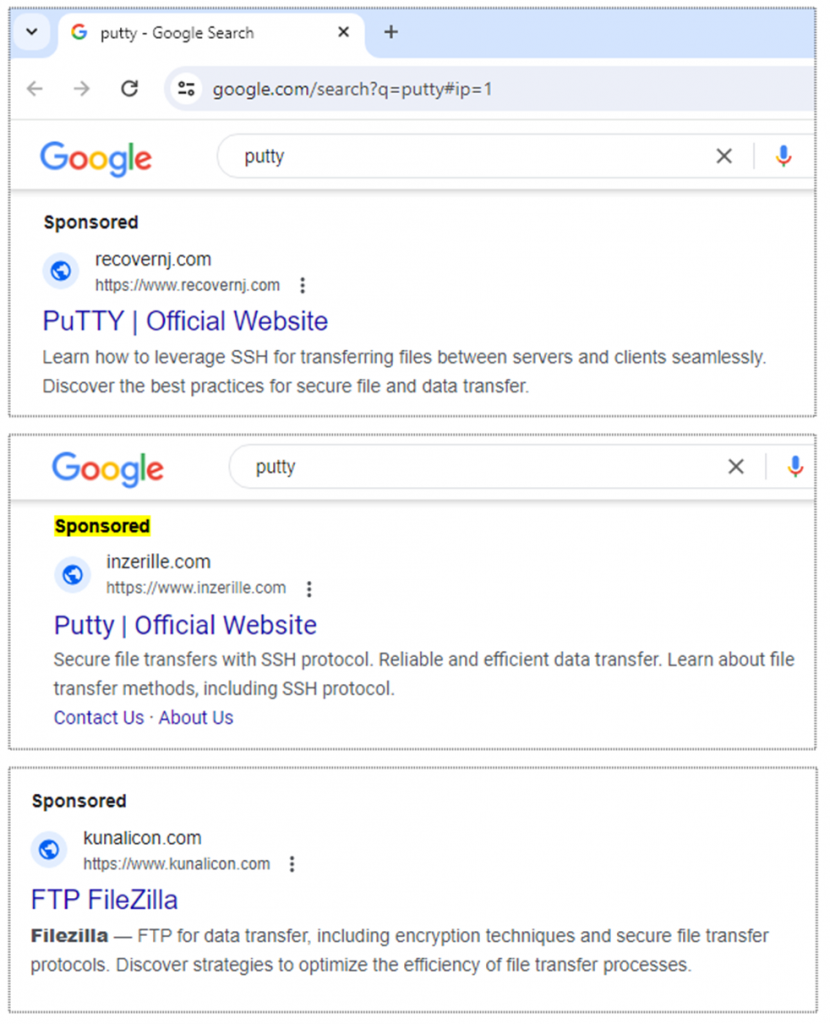
Sponsored malicious sites in the top of Google search results
It's funny that the attackers set up a mock redirect to the so — called Rick Roll-the cult music video of Rick Astley, if the system detects invalid traffic. Thus, it is quite possible that hackers wanted to mock the security researchers who will investigate this malicious campaign.
The second stage. Redirection to duplicate sites that are so well copied that they can mislead any user, even experienced system administrators.
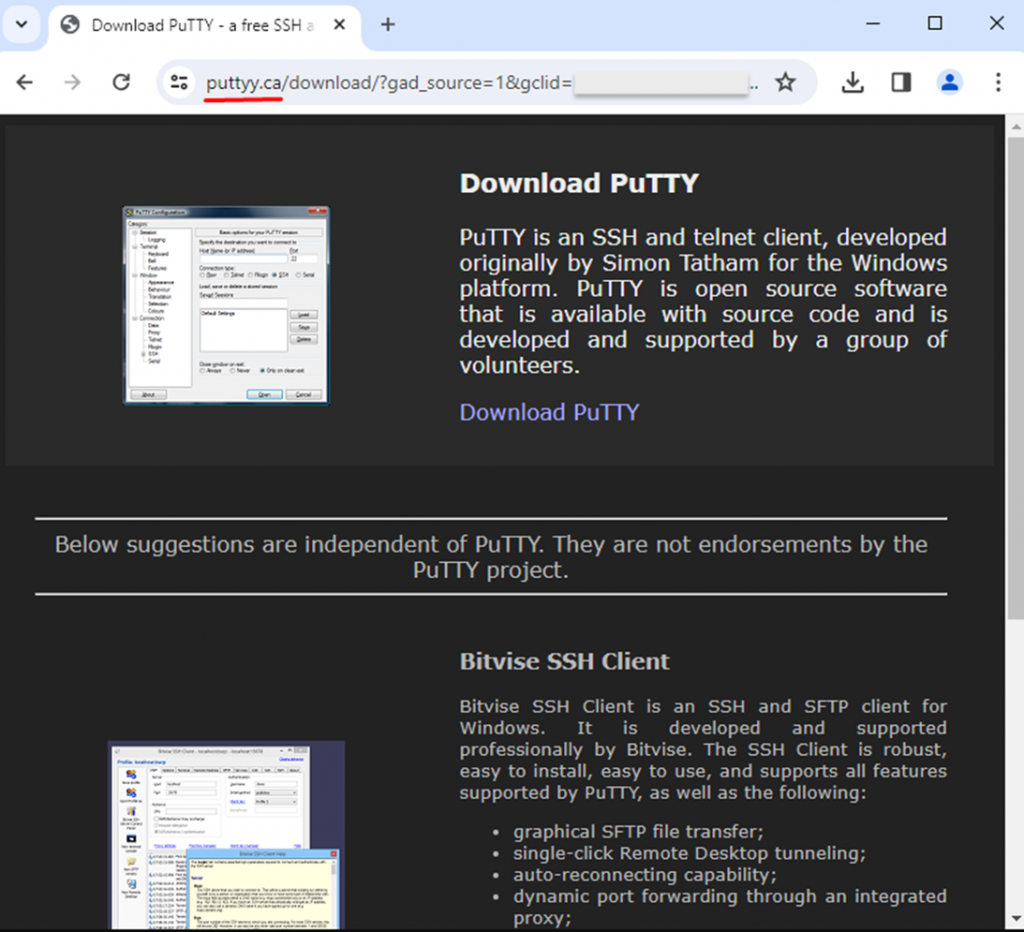
Fake PuTTY website that looks indistinguishable from the original one
The third stage. Download and run malicious software through a fake installer. It uses a technique known as DLL Sideloading, in which a legitimate and signed executable runs a malicious DLL library. In the case considered by the researchers, when launching a legitimate setup.exe (from the Python Software Foundation) side-loading occurs python311.dll (Nitrogen).
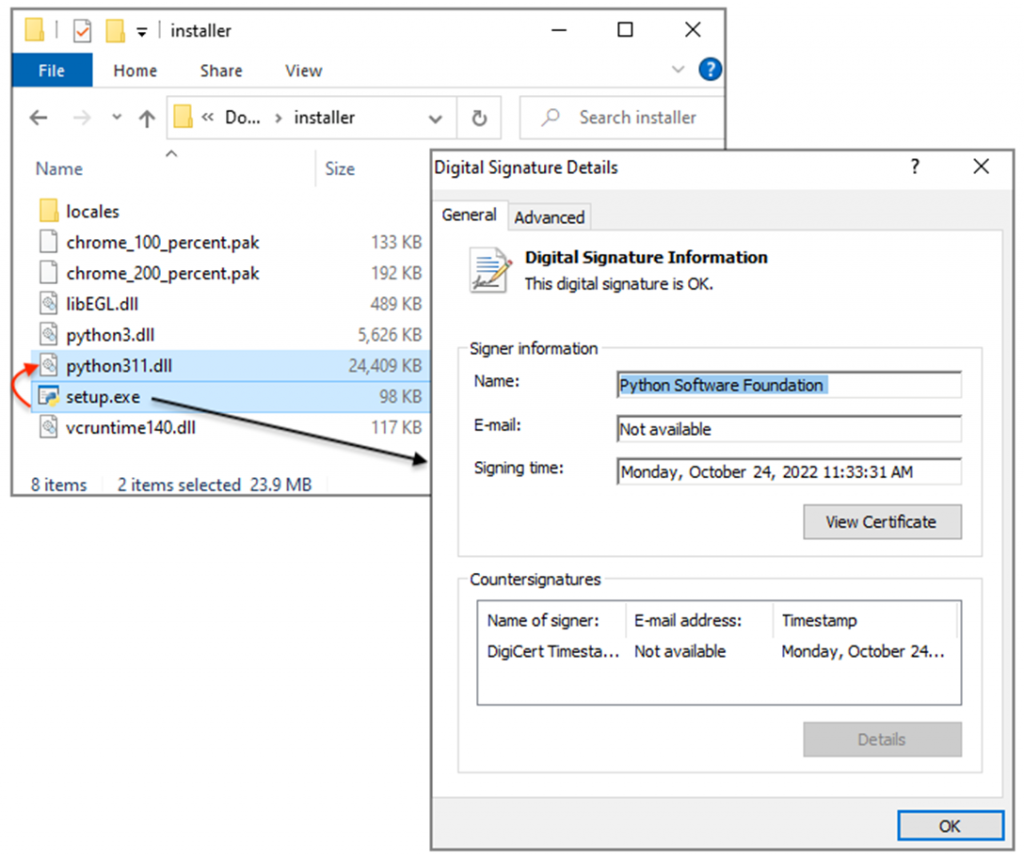
DLL Sideloading using a legitimate installer
Malwarebytes experts recommend taking the following protective measures to avoid becoming a victim of scammers:
Thus, even experienced system administrators who consider themselves experts in the computer industry can become victims of sophisticated cyber attacks. This story demonstrates that malicious actors are constantly improving their methods to deceive even the most trained specialists.
Recently, cybersecurity researchers at Malwarebytes observed an ongoing wave of cyberattacks targeting system administrators through fraudulent advertising of PuTTY and FileZilla utilities. The ad is served as sponsored results in the Google search engine and is aimed at users from North America, serving as a clever trap for downloading the Nitrogen malware.
Nitro is used by attackers for initial access to private networks, subsequent data theft, and distribution of ransomware, including ALPHV/BlackCat cryptographic programs.
At the moment, despite numerous requests from specialists, Google has not yet taken any active actions to block this malicious operation.
The attack consists of several stages, each of which will be discussed later.
The first stage. Attract victims through fraudulent ads in Google search results that lead to fake sites.

Sponsored malicious sites in the top of Google search results
It's funny that the attackers set up a mock redirect to the so — called Rick Roll-the cult music video of Rick Astley, if the system detects invalid traffic. Thus, it is quite possible that hackers wanted to mock the security researchers who will investigate this malicious campaign.
The second stage. Redirection to duplicate sites that are so well copied that they can mislead any user, even experienced system administrators.

Fake PuTTY website that looks indistinguishable from the original one
The third stage. Download and run malicious software through a fake installer. It uses a technique known as DLL Sideloading, in which a legitimate and signed executable runs a malicious DLL library. In the case considered by the researchers, when launching a legitimate setup.exe (from the Python Software Foundation) side-loading occurs python311.dll (Nitrogen).

DLL Sideloading using a legitimate installer
Malwarebytes experts recommend taking the following protective measures to avoid becoming a victim of scammers:
- conduct user training to raise awareness of threats spread through malicious advertising;
- apply group policies to restrict ad network traffic;
- configure EDR and MDR solutions to quickly inform the security team about a potential attack.
Thus, even experienced system administrators who consider themselves experts in the computer industry can become victims of sophisticated cyber attacks. This story demonstrates that malicious actors are constantly improving their methods to deceive even the most trained specialists.

