Carding
Professional
- Messages
- 2,870
- Reaction score
- 2,493
- Points
- 113
Software vulnerabilities are errors made by programmers during the software development phase. They allow attackers to gain illegal access to program functions or data stored in it. Flaws can appear at any stage of the life cycle, from design to release of the finished product.
In some cases, programmers deliberately leave loopholes for debugging and tuning, which can also be viewed as backdoors or undeclared features. In some cases, the emergence of vulnerabilities is due to the use of development tools of various origins, which increase the risk of sabotage defects in the program code.
Vulnerabilities appear due to the addition of third-party components or free code (open source) to the software. Foreign code is often used “as is” without careful analysis and security testing.
One should not exclude the presence of insider programmers in the team, who deliberately introduce additional undocumented functions or elements into the product being created.
Classification of software vulnerabilities
Vulnerabilities arise as a result of errors that have arisen during the design phase or when writing software code.
Depending on the stage of emergence, this type of threat is divided into design, implementation and configuration vulnerabilities.
1. Design mistakes are the hardest to spot and fix. These are inaccuracies of algorithms, bookmarks, inconsistencies in the interface between different modules or in protocols for interacting with the hardware, the introduction of suboptimal technologies. Their elimination is a very time-consuming process, including because they can appear in non-obvious cases - for example, when the specified volume of traffic is exceeded or when a large number of additional equipment is connected, which complicates the provision of the required level of security and leads to the emergence of ways to bypass the firewall.
2. Implementation vulnerabilities appear at the stage of writing a program or introducing security algorithms into it. This is an incorrect organization of the computational process, syntactic and logical defects. However, there is a risk that the flaw will lead to buffer overflows or other problems. Finding them takes a long time, and elimination means fixing certain parts of the machine code.
3. Hardware and software configuration errors are common. Their common reasons are insufficient quality development and lack of tests for the correct operation of additional functions. Passwords that are too simple and default accounts left unchanged can also fall into this category.
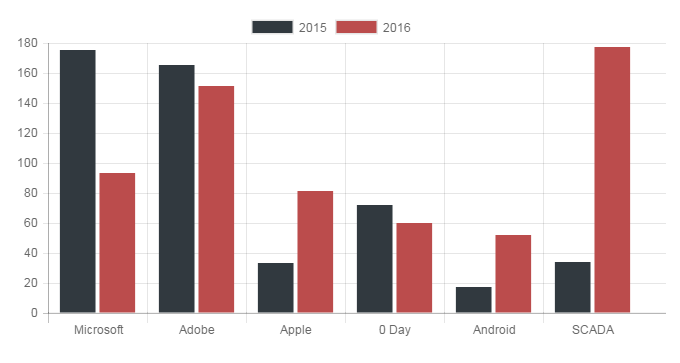
According to statistics, vulnerabilities are especially often found in popular and widespread products - desktop and mobile operating systems, browsers.
Risks of using vulnerable programs
The programs in which the largest number of vulnerabilities are found are installed on almost all computers. On the part of cybercriminals there is a direct interest in finding such flaws and writing exploits for them.
Since it takes a long time from the moment a vulnerability is discovered to the release of a patch (patch), there is a fair amount of opportunity to infect computer systems through code security holes.
In this case, the user only needs to open once, for example, a malicious PDF file with an exploit, after which the attackers will gain access to the data. In the latter case, infection occurs according to the following algorithm:
Research carried out by various companies (Kaspersky Lab, Positive Technologies) shows that there are vulnerabilities in almost any application, including antiviruses. Therefore, the probability of installing a software product containing flaws of varying degrees of criticality is very high.
To minimize the number of holes in the software, it is necessary to use the SDL (Security Development Lifecycle). SDL technology is used to reduce the number of bugs in applications at all stages of their creation and support. So, when designing software, information security specialists and programmers simulate cyber threats in order to find vulnerabilities. During programming, automatic tools are included in the process, immediately reporting potential flaws. The developers seek to significantly limit the functionality available to unverified users, which helps to reduce the attack surface.
To minimize the impact of vulnerabilities and damage from them, you must follow some rules:
In some cases, programmers deliberately leave loopholes for debugging and tuning, which can also be viewed as backdoors or undeclared features. In some cases, the emergence of vulnerabilities is due to the use of development tools of various origins, which increase the risk of sabotage defects in the program code.

Vulnerabilities appear due to the addition of third-party components or free code (open source) to the software. Foreign code is often used “as is” without careful analysis and security testing.
One should not exclude the presence of insider programmers in the team, who deliberately introduce additional undocumented functions or elements into the product being created.
Classification of software vulnerabilities
Vulnerabilities arise as a result of errors that have arisen during the design phase or when writing software code.
Depending on the stage of emergence, this type of threat is divided into design, implementation and configuration vulnerabilities.
1. Design mistakes are the hardest to spot and fix. These are inaccuracies of algorithms, bookmarks, inconsistencies in the interface between different modules or in protocols for interacting with the hardware, the introduction of suboptimal technologies. Their elimination is a very time-consuming process, including because they can appear in non-obvious cases - for example, when the specified volume of traffic is exceeded or when a large number of additional equipment is connected, which complicates the provision of the required level of security and leads to the emergence of ways to bypass the firewall.
2. Implementation vulnerabilities appear at the stage of writing a program or introducing security algorithms into it. This is an incorrect organization of the computational process, syntactic and logical defects. However, there is a risk that the flaw will lead to buffer overflows or other problems. Finding them takes a long time, and elimination means fixing certain parts of the machine code.
3. Hardware and software configuration errors are common. Their common reasons are insufficient quality development and lack of tests for the correct operation of additional functions. Passwords that are too simple and default accounts left unchanged can also fall into this category.
According to statistics, vulnerabilities are especially often found in popular and widespread products - desktop and mobile operating systems, browsers.
Risks of using vulnerable programs
The programs in which the largest number of vulnerabilities are found are installed on almost all computers. On the part of cybercriminals there is a direct interest in finding such flaws and writing exploits for them.
Since it takes a long time from the moment a vulnerability is discovered to the release of a patch (patch), there is a fair amount of opportunity to infect computer systems through code security holes.
In this case, the user only needs to open once, for example, a malicious PDF file with an exploit, after which the attackers will gain access to the data. In the latter case, infection occurs according to the following algorithm:
- The user receives a phishing email from a trusted sender.
- An exploit file is attached to the letter.
- If a user attempts to open a file, then there is an infection computer virus, trojan (cryptographer) or other malware.
- Cybercriminals gain unauthorized access to the system.
- It takes place stealing valuable data.
Research carried out by various companies (Kaspersky Lab, Positive Technologies) shows that there are vulnerabilities in almost any application, including antiviruses. Therefore, the probability of installing a software product containing flaws of varying degrees of criticality is very high.
To minimize the number of holes in the software, it is necessary to use the SDL (Security Development Lifecycle). SDL technology is used to reduce the number of bugs in applications at all stages of their creation and support. So, when designing software, information security specialists and programmers simulate cyber threats in order to find vulnerabilities. During programming, automatic tools are included in the process, immediately reporting potential flaws. The developers seek to significantly limit the functionality available to unverified users, which helps to reduce the attack surface.
To minimize the impact of vulnerabilities and damage from them, you must follow some rules:
- Promptly install developer-released patches (patches) for applications or (preferably) enable automatic update mode.
- If possible, do not install questionable programs whose quality and technical support raise questions.
- Use special vulnerability scanners or specialized functions of antivirus products to search for security errors and, if necessary, update the software.

