Teacher
Professional
- Messages
- 2,669
- Reaction score
- 819
- Points
- 113
Hello! Everyone knows what phishing is. He has been with us for over 20 years. But now, it seems that phishing has become more accessible than before. This article explains how scammers can benefit from increasing the popularity of phishing service sales in the form of a service.
In this article, you will learn:
Getting a phishing link
It all started when we received a text message from thePalestinian pigs "Isracard" (this is the name of an Israeli financial services company).
The text message contained the following link: https://ow[.]ly/tthX30SiE8w (Picture 1). This link is a short link leading to: https://3fed85ce0a9501496.temporary[.]link/2/ar22/aramex-infos.php
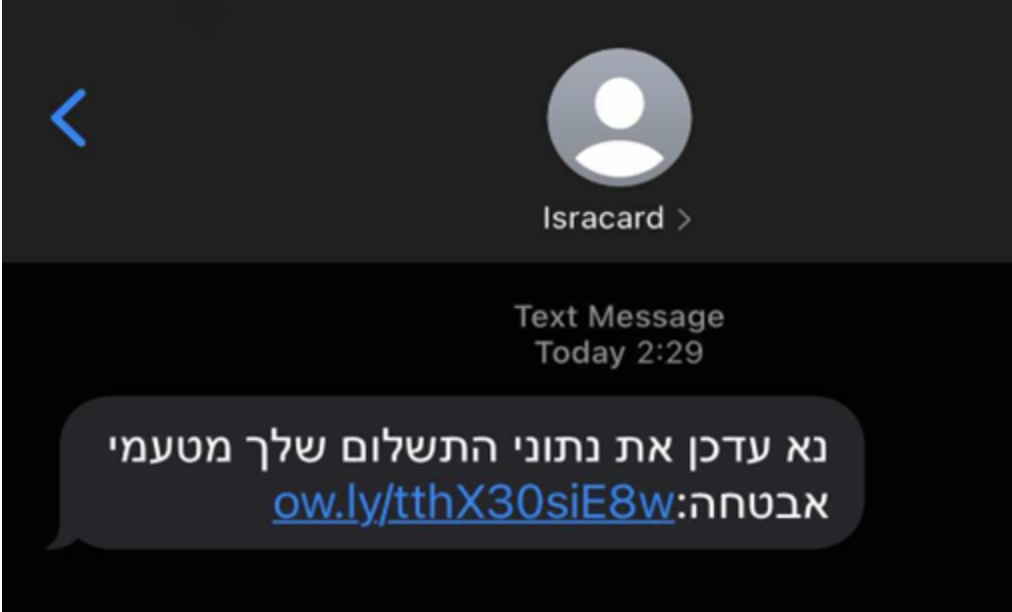

Picture 1. In the message: You need to update your payment information for security reasons.
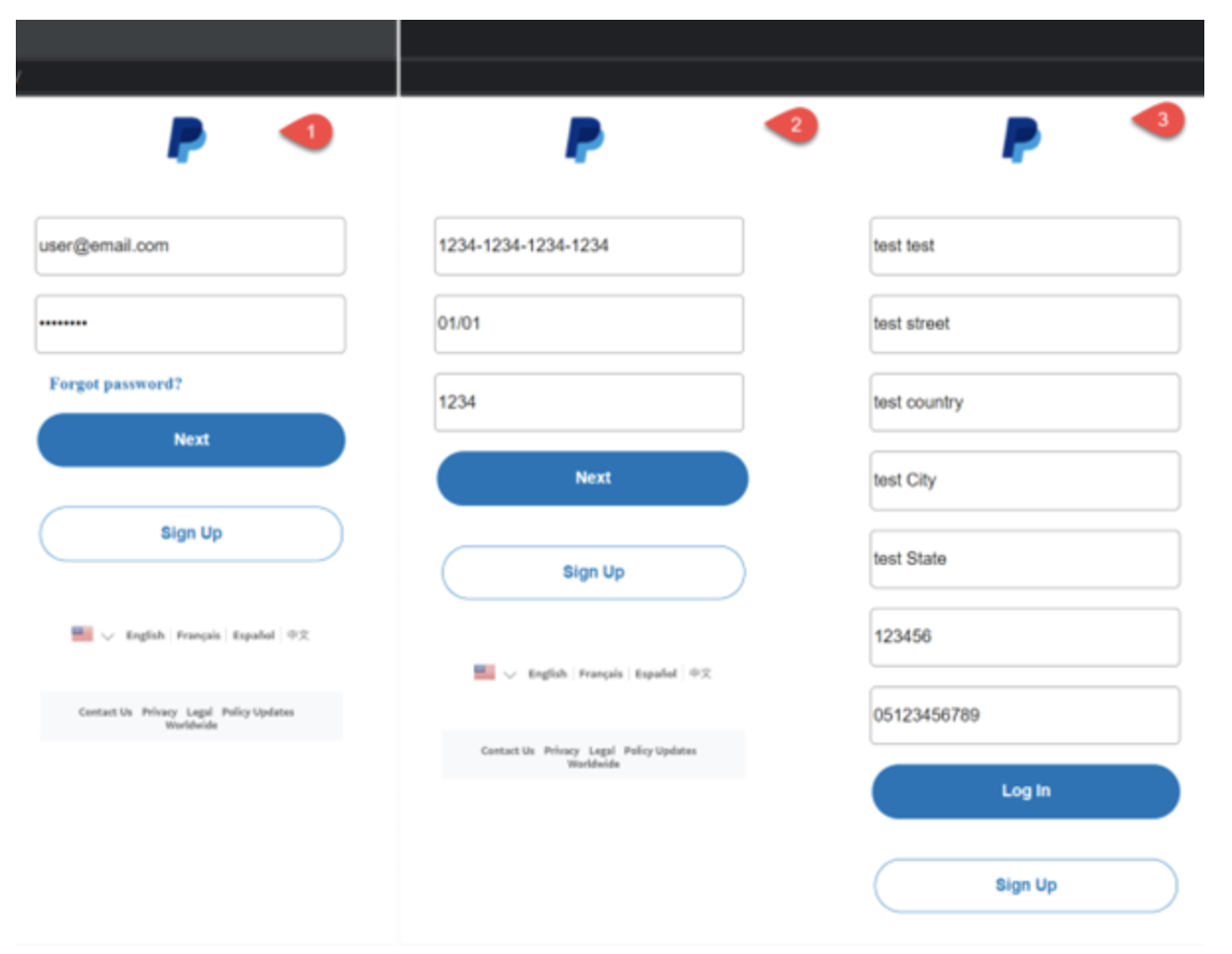
Clicking on the link takes you to the next page for filling out billing information (Picture 2), which at first glance looks strange. It looks like the attackers created a mirror image of a real company's page in order to trick victims into entering their personal information, such as CC data, CVV code, and card expiration date. When the confirmation button is clicked, the information is sent to the attackers ' server, after which the victim is redirected to the site www.aramex.com
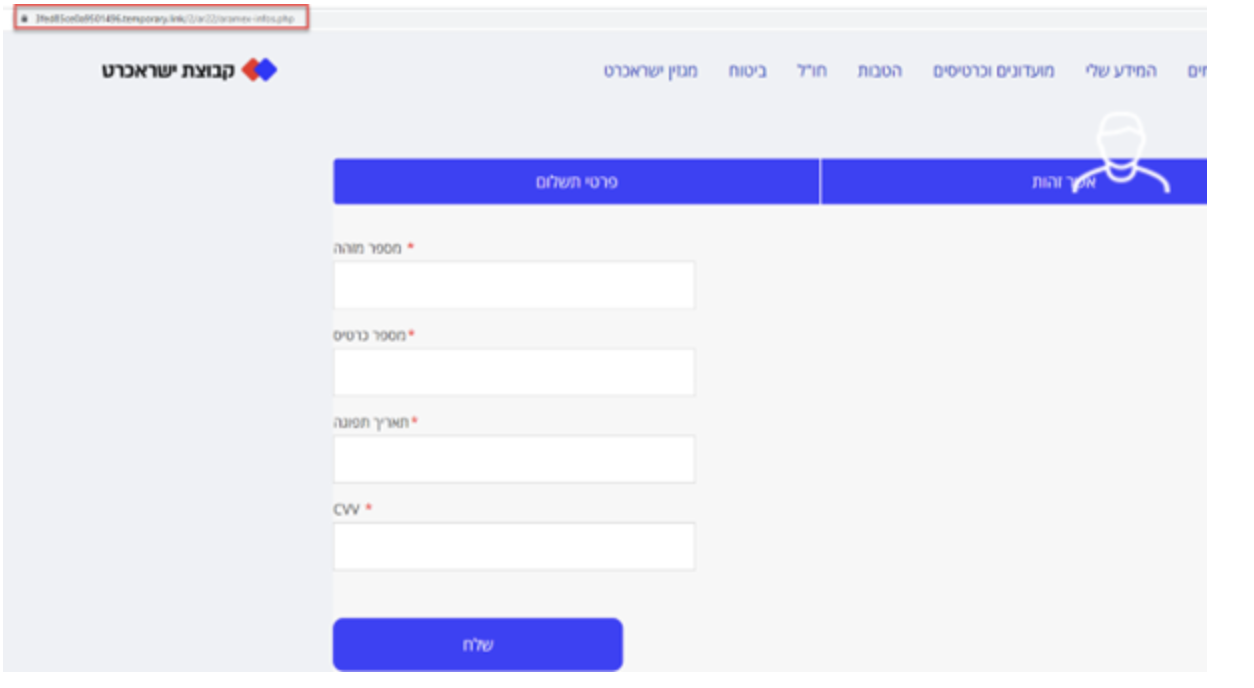

Picture 2. What a phishing page looks like
We searched the site to see if we could find something interesting. And, fortunately, we got access to several directories, which you can see in Picture 3. One of the directories, called "2", allowed us to view the contents (a list of directories). After we dug around inside, we saw that there was a file archive called "ar22.zip", which contained the full package of phishing files.
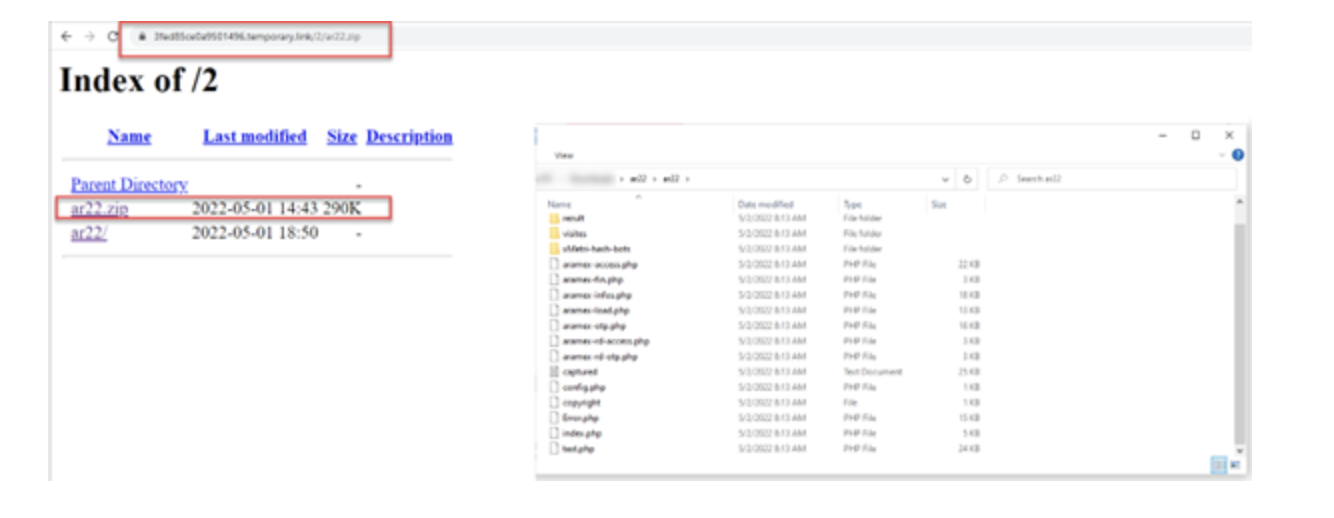

Picture 3. Contents of the phish archive (after downloading and extracting the zip file)
Hunting for intruders
Almost immediately, we noticed a file called "config.php". This file contained a token for the Telegram bot (Picture 4). Using this token for Telegram, we were able to get information about people who subscribed to the bot in TG (Picture 5).
In other words, we had details for each phishing campaign group and user.
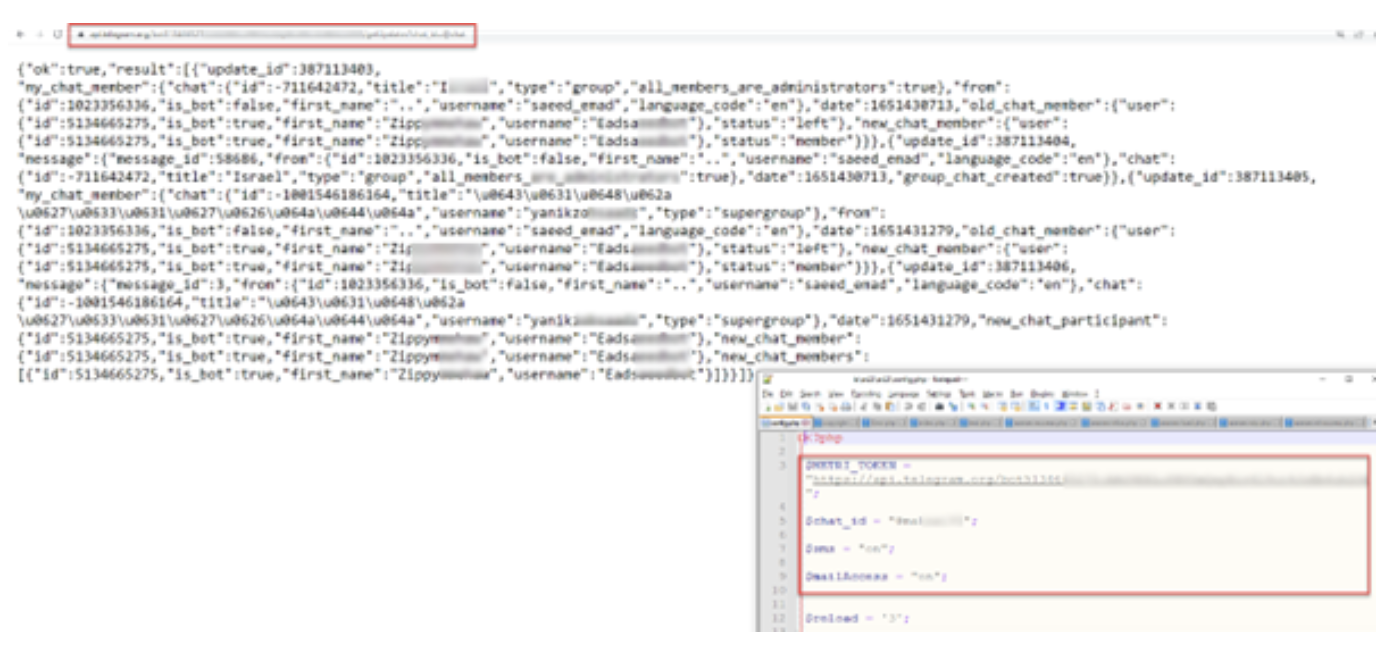

Picture 4. You can see the users and groups that use this bot
We found 2 channels that were either fully open or had no access restrictions. This allowed us to easily review the content without being a member of the group or receiving an invitation.
Here's what information was available:
* Chats between group members
* How and where to buy phishing kits
* Information for accessing the VPS server (where the phishing kits were stored)
* Discussions about future phishing campaigns
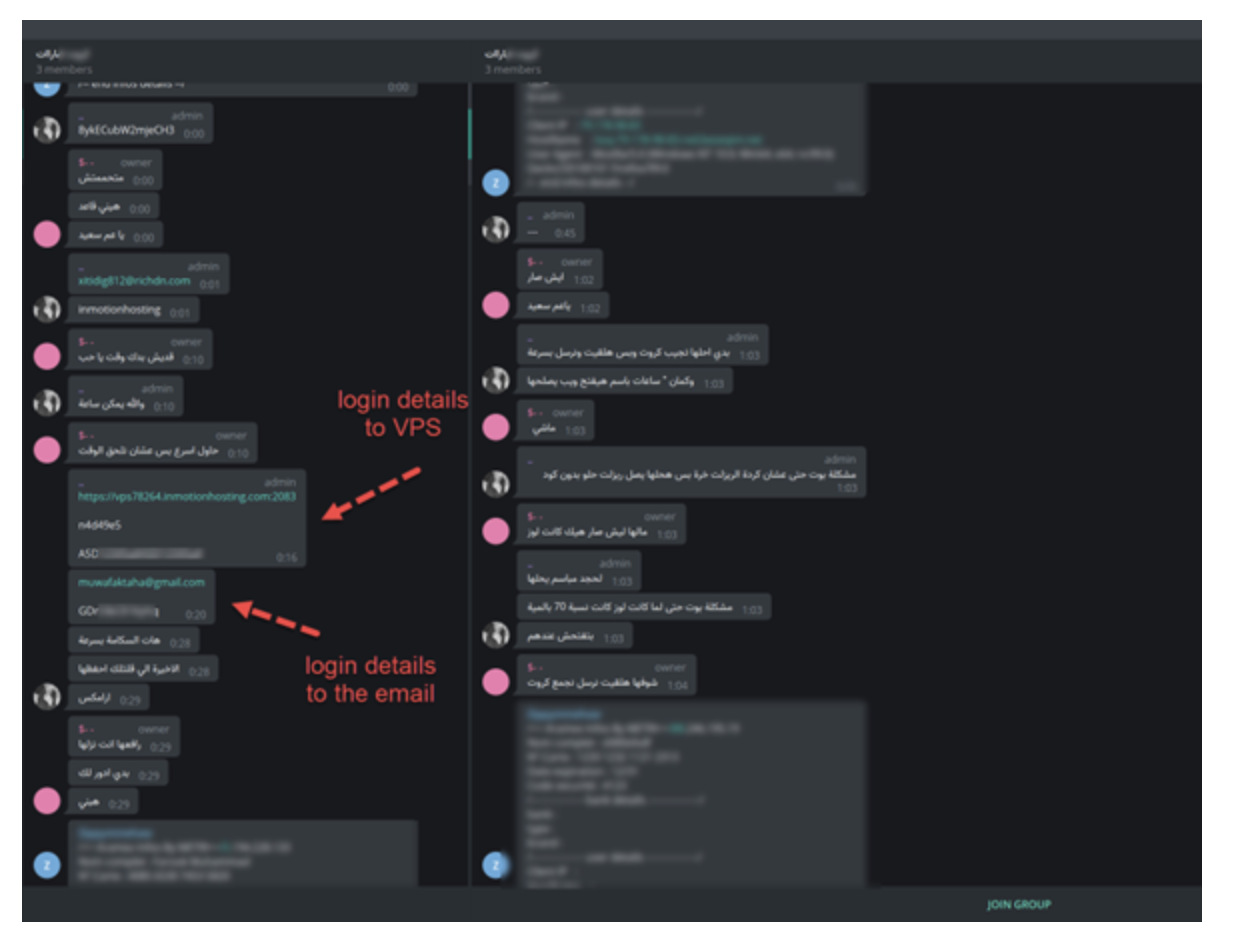

Picture 5. Communication between group members
Once we had a username / password, we were able to access the VPS server (Picture 6). On the server, we saw several active phishing campaigns, where each set related to a different country.
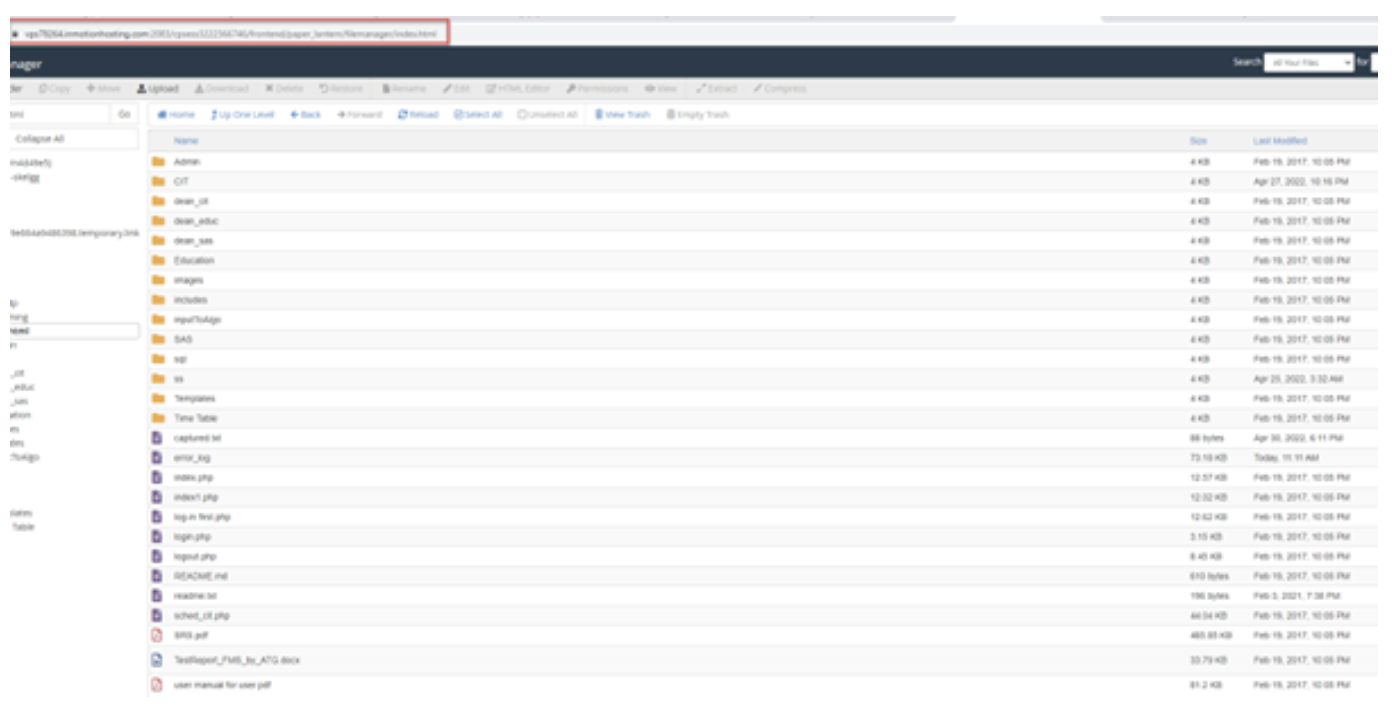

Picture 6. All phishing kits that this group sent to victims. Each folder contains a separate phishing kit.
Among other things, there were phishing campaigns that mimic the pages of large well-known organizations (Picture 7)
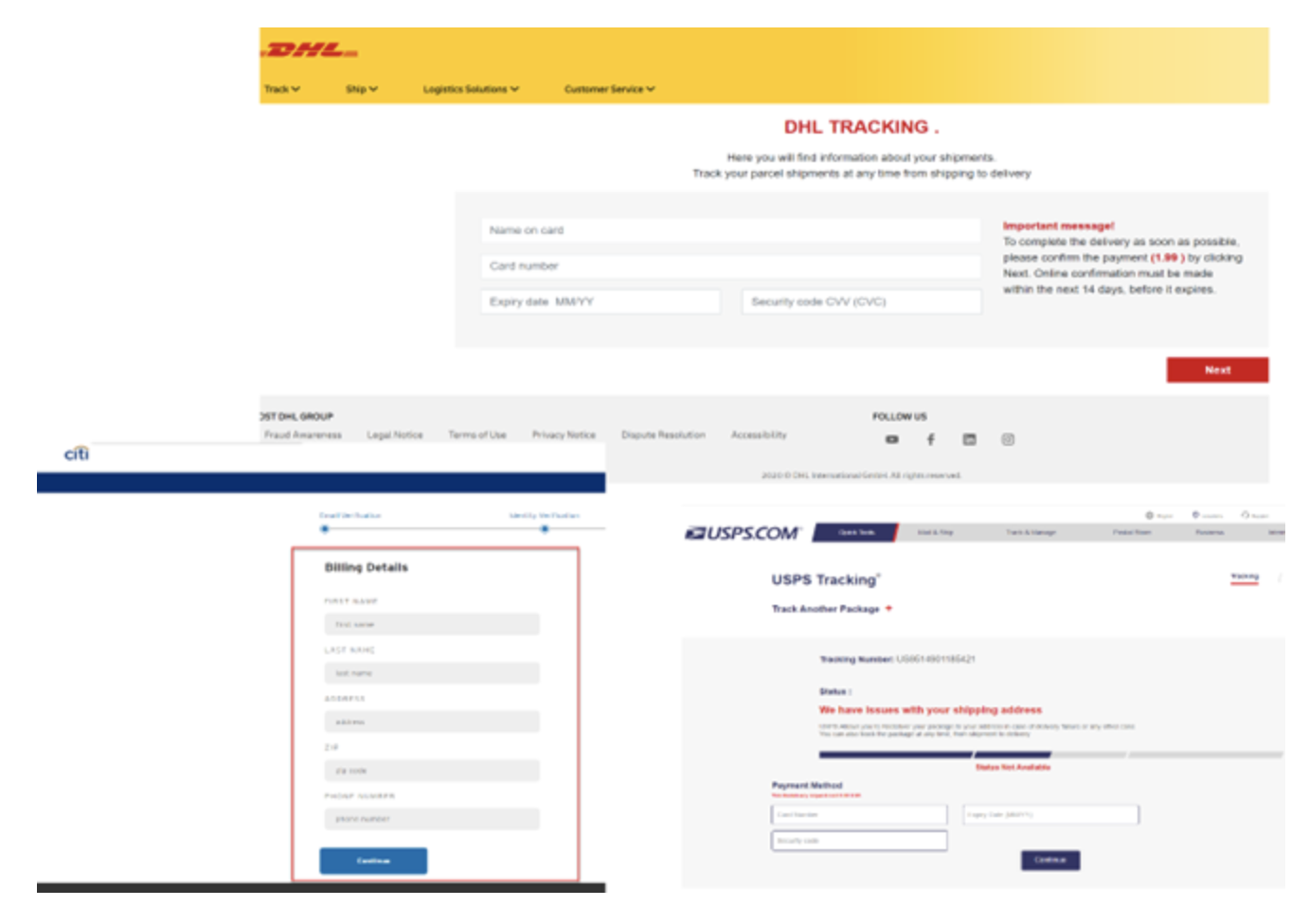

Picture 7. Several mirror sites that we found there
Search for phishing kits for sale
After searching through these groups, we found additional information about the creators of these phishing packages. (Pictures 8, 9)
Some nicknames:
After we searched for these nicknames on the cart, darknet, and Google, we tracked down the groups of these creators. These groups had tools and information that led to phishing attacks. Here's what they contained:
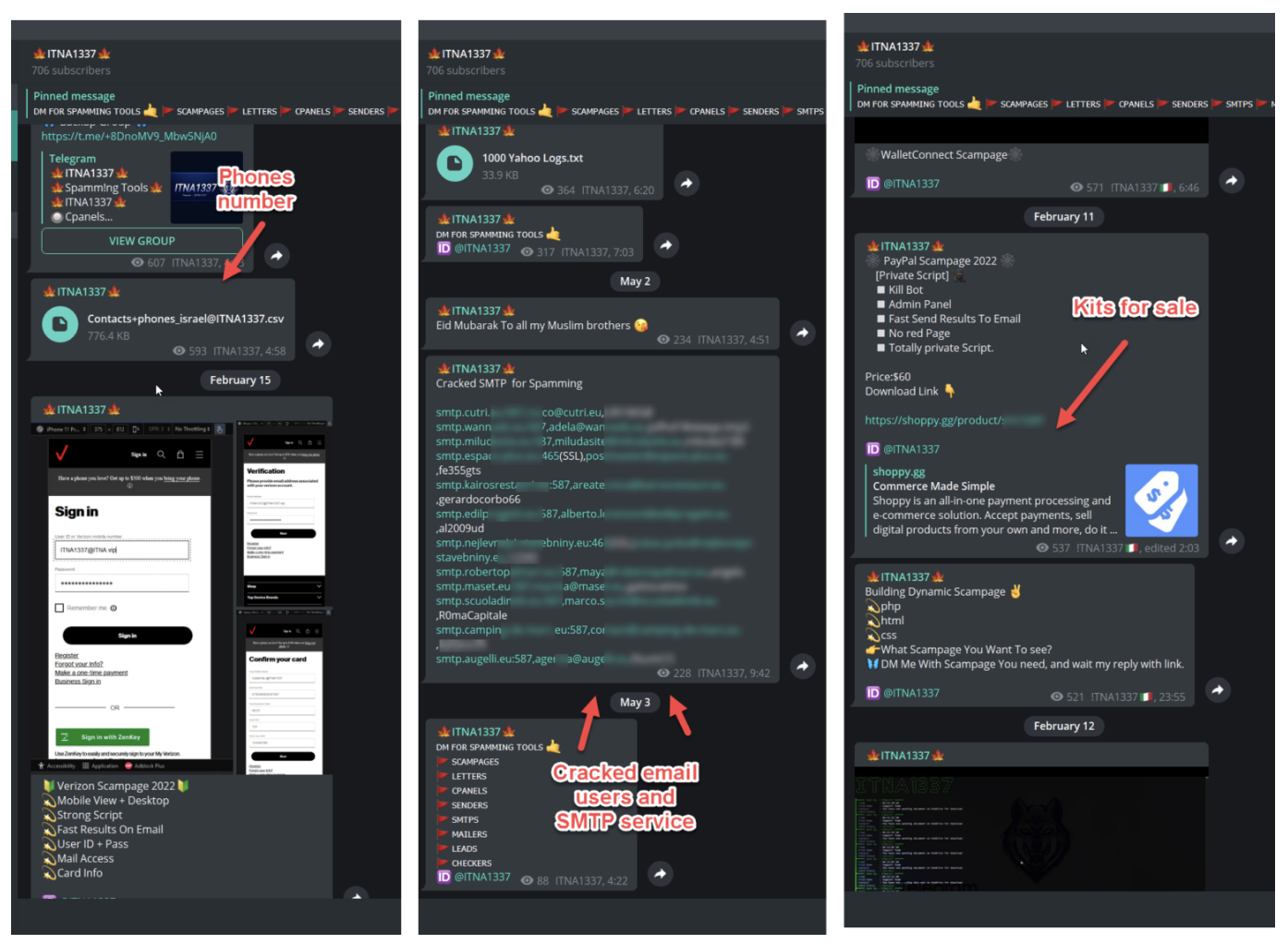

Picture 8. Part of what we found on the ITNA1337 channel
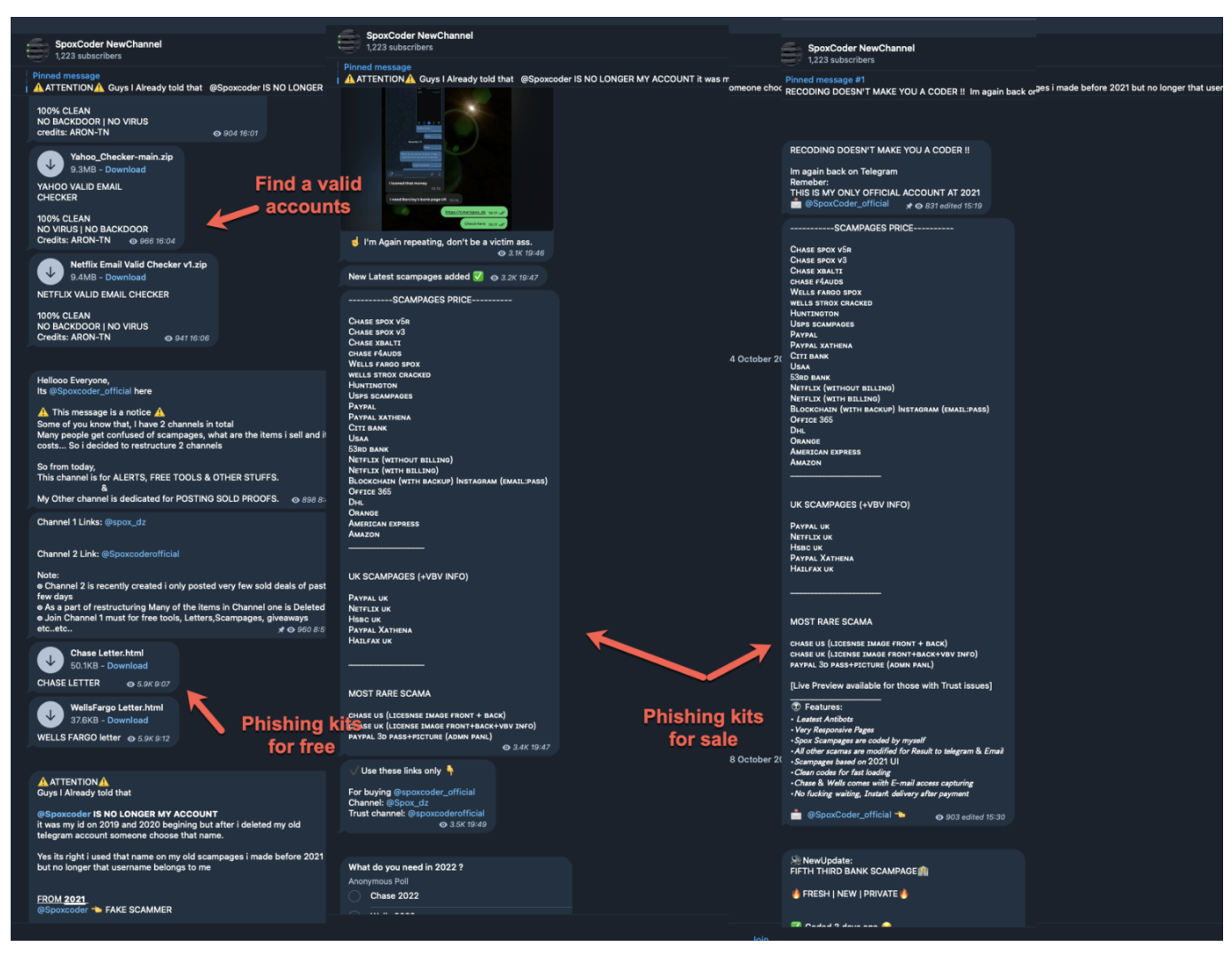

Picture 9. Part of what we found on the “SpoxCoder NewChannel”channel
Creating our Own Phishing Attack
During our research, we came to the conclusion that creating a phishing attack is quite simple. You don't have to be tech-savvy to do this. We decided to create a phishing campaign to demonstrate this (Picture 12).
Here's what you need before launching your campaign::
On the server, we used Apache to install a web server. After that, we uploaded the phishing kit from the cart group to our server.
To hide the actual link and shorten it, we used bit.ly (Picture 10)
After we shortened the link to the server where the phishing kit was stored, the campaign was ready (Picture 11)
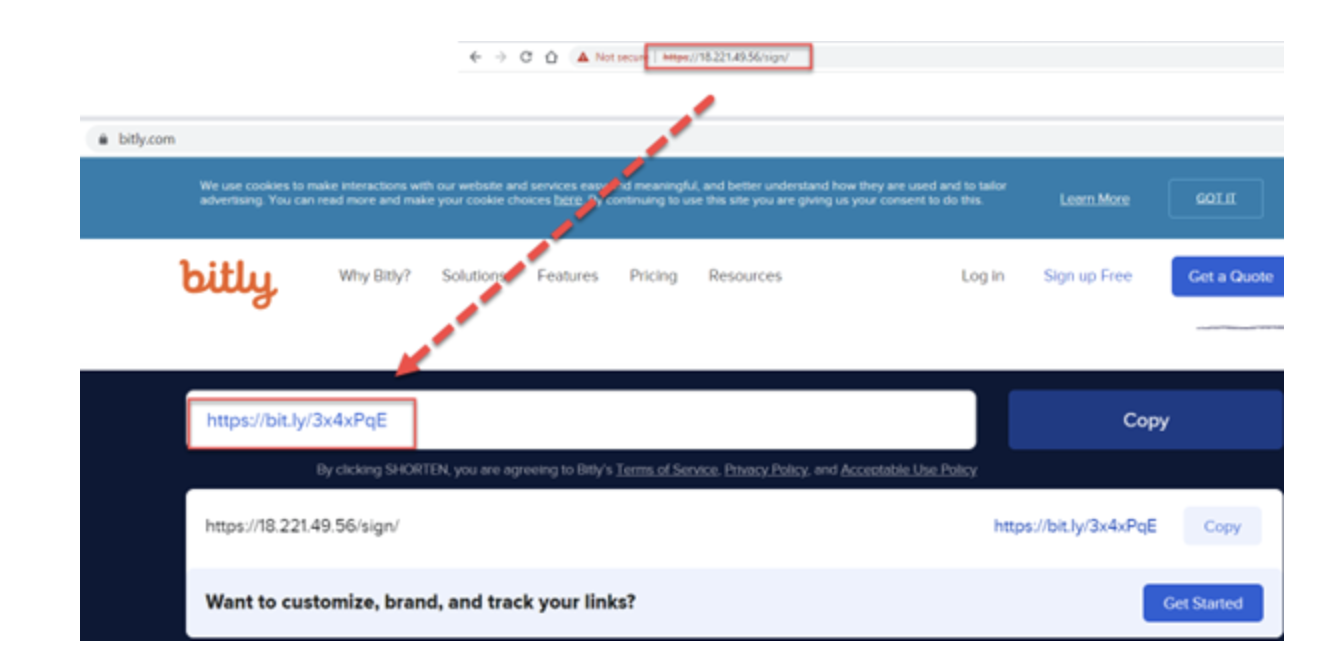

Picture 10. Short link to the site
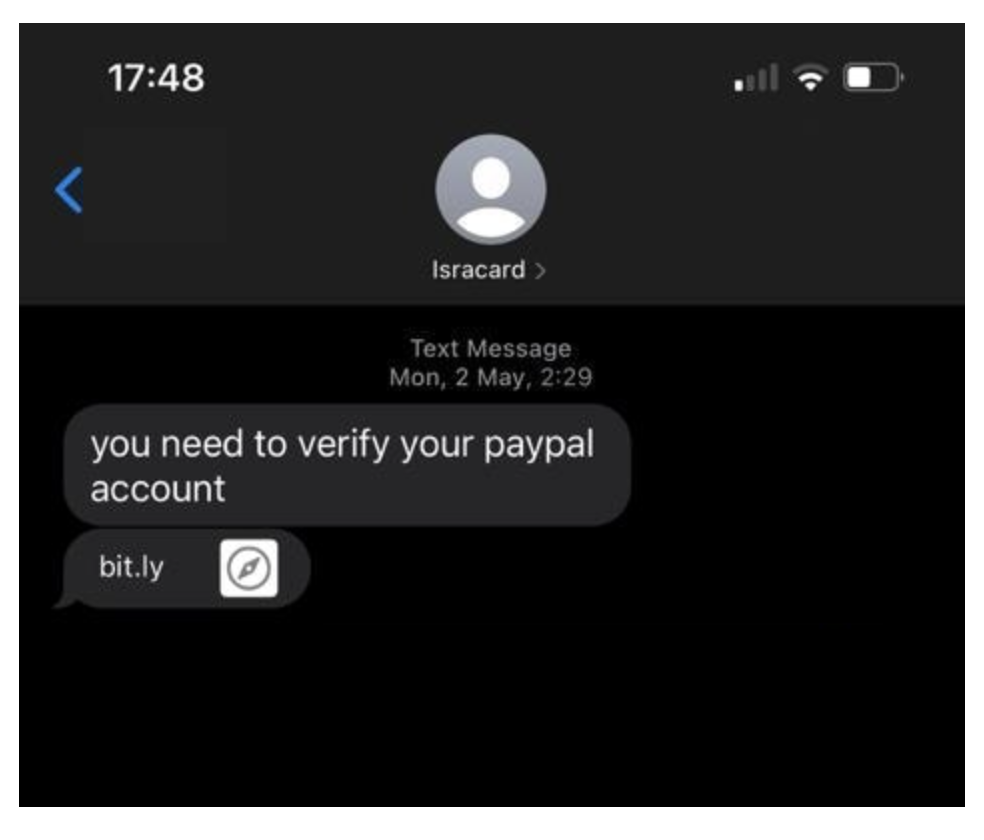

Image 11. Short link used in the campaign

Picture 12. Phishing Campaign steps
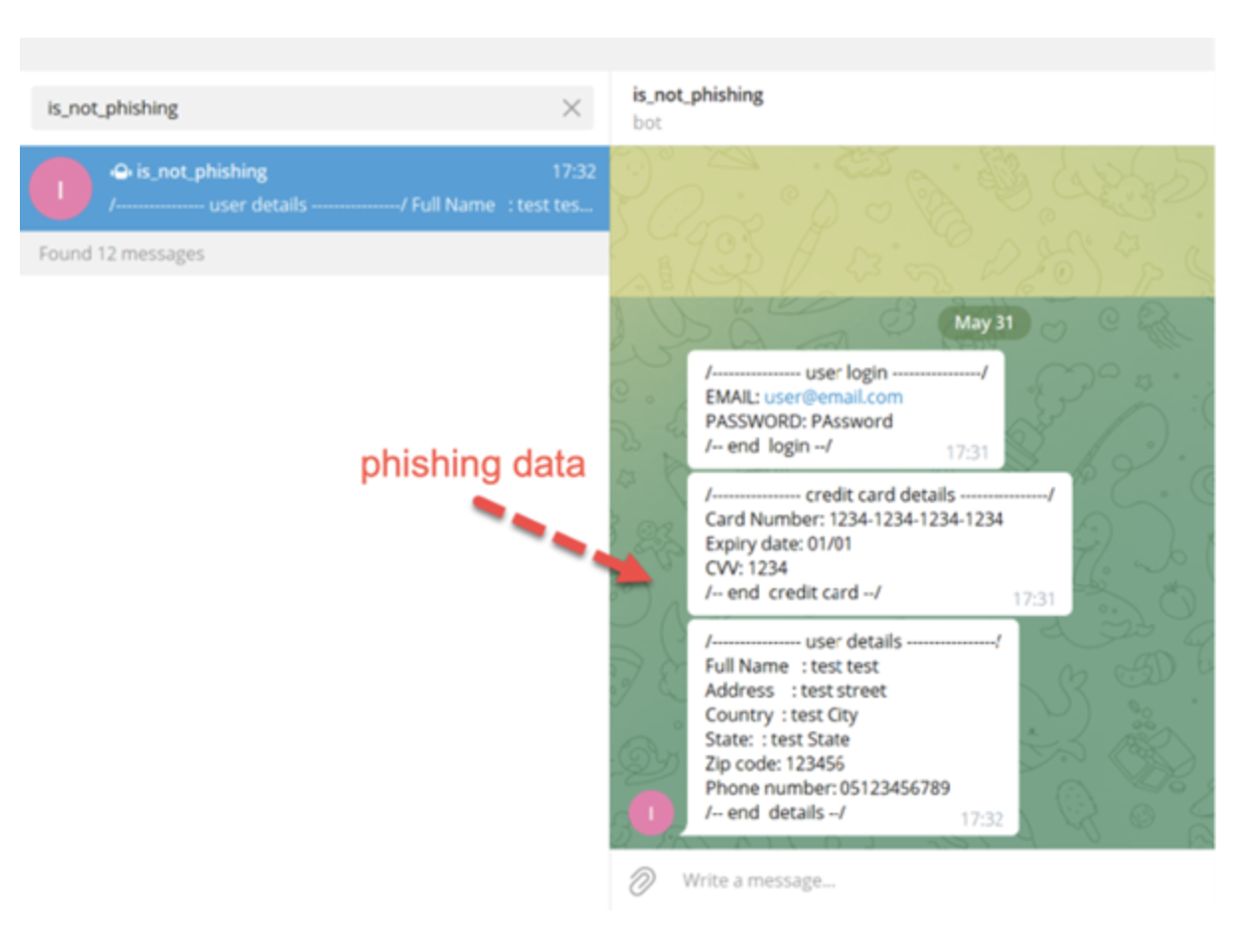

Picture 13. Shows us all the information that is sent to the group in the cart that was created for this purpose.
Conclusion
Let's talk about numbers. The information below is based on cart groups and logs from the VPS server:
In this article, you will learn:
- In this article, you will learn:
- Getting a phishing link
- Hunting for intruders
- Search for phishing kits for sale
- Creating our Own Phishing Attack
- Conclusion
Getting a phishing link
It all started when we received a text message from the
The text message contained the following link: https://ow[.]ly/tthX30SiE8w (Picture 1). This link is a short link leading to: https://3fed85ce0a9501496.temporary[.]link/2/ar22/aramex-infos.php


Picture 1. In the message: You need to update your payment information for security reasons.
Clicking on the link takes you to the next page for filling out billing information (Picture 2), which at first glance looks strange. It looks like the attackers created a mirror image of a real company's page in order to trick victims into entering their personal information, such as CC data, CVV code, and card expiration date. When the confirmation button is clicked, the information is sent to the attackers ' server, after which the victim is redirected to the site www.aramex.com


Picture 2. What a phishing page looks like
We searched the site to see if we could find something interesting. And, fortunately, we got access to several directories, which you can see in Picture 3. One of the directories, called "2", allowed us to view the contents (a list of directories). After we dug around inside, we saw that there was a file archive called "ar22.zip", which contained the full package of phishing files.


Picture 3. Contents of the phish archive (after downloading and extracting the zip file)
Hunting for intruders
Almost immediately, we noticed a file called "config.php". This file contained a token for the Telegram bot (Picture 4). Using this token for Telegram, we were able to get information about people who subscribed to the bot in TG (Picture 5).
In other words, we had details for each phishing campaign group and user.


Picture 4. You can see the users and groups that use this bot
We found 2 channels that were either fully open or had no access restrictions. This allowed us to easily review the content without being a member of the group or receiving an invitation.
Here's what information was available:
* Chats between group members
* How and where to buy phishing kits
* Information for accessing the VPS server (where the phishing kits were stored)
* Discussions about future phishing campaigns


Picture 5. Communication between group members
Once we had a username / password, we were able to access the VPS server (Picture 6). On the server, we saw several active phishing campaigns, where each set related to a different country.


Picture 6. All phishing kits that this group sent to victims. Each folder contains a separate phishing kit.
Among other things, there were phishing campaigns that mimic the pages of large well-known organizations (Picture 7)


Picture 7. Several mirror sites that we found there
Search for phishing kits for sale
After searching through these groups, we found additional information about the creators of these phishing packages. (Pictures 8, 9)
Some nicknames:
- spoxcoder
- Officiel[.]UGEYO
- Spox DZ
- ARON- []TN
- ITNA1337 (previous nickname Cyb3r_3rr0r)
- Shadow
- Greedy Coder
- Marshal STRIMER
After we searched for these nicknames on the cart, darknet, and Google, we tracked down the groups of these creators. These groups had tools and information that led to phishing attacks. Here's what they contained:
- Emails used for sending malicious links
- Phone numbers of potential victims
- Manuals
- Phishing kits for sale


Picture 8. Part of what we found on the ITNA1337 channel


Picture 9. Part of what we found on the “SpoxCoder NewChannel”channel
Creating our Own Phishing Attack
During our research, we came to the conclusion that creating a phishing attack is quite simple. You don't have to be tech-savvy to do this. We decided to create a phishing campaign to demonstrate this (Picture 12).
Here's what you need before launching your campaign::
- Server/VPS: used to store a phishing kit
- Short link: used to hide the real link from victims
- Phone numbers: we found a list of potential numbers in one of the cart groups
On the server, we used Apache to install a web server. After that, we uploaded the phishing kit from the cart group to our server.
To hide the actual link and shorten it, we used bit.ly (Picture 10)
After we shortened the link to the server where the phishing kit was stored, the campaign was ready (Picture 11)
The whole process takes about 10 minutes.


Picture 10. Short link to the site


Image 11. Short link used in the campaign


Picture 12. Phishing Campaign steps


Picture 13. Shows us all the information that is sent to the group in the cart that was created for this purpose.
Conclusion
Let's talk about numbers. The information below is based on cart groups and logs from the VPS server:
- Israel Credit Company: Attackers collected credit cards from almost 1,200 victims.
- Global Bank: personal information of 450 people, including credit cards, site logins/passwords, and SSNs.
- A major streaming service: information about 60 people, including credit cards, usernames/passwords, and cookies.
Most attacks used kits purchased on various platforms, such as Telegram, Shopify, and the darknet. No deep technical knowledge is required to create / manage them.
Due to a problem with the SMS protocol, an attacker can substitute the sender's name. This leads victims to believe that the SMS is from a real company, and not from scammers.
We showed that the attackers were not techies, and as a result: the server was exposed to several security vulnerabilities, which allowed us to detect phishing campaigns.

