Brother
Professional
- Messages
- 2,590
- Reaction score
- 533
- Points
- 113
The critical CVE-2023-51467 has become the object of active attention to Apache systems.
VulnCheck specialists have developed a Proof-of-Concept (PoC) code that exploits a recently discovered critical vulnerability in the Enterprise Resource Planning (ERP) system Apache OFBiz to run malicious code in memory.
We are talking about the vulnerability CVE-2023-51467 (CVSS score: 9.8), which is an authentication bypass error that allows an attacker to execute arbitrary code on a remote device and gain access to confidential information. The bug allows you to bypass another critical flaw in the same software ( CVE-2023-49070 with CVSS rating: 9.8).
Although the vulnerability was fixed in Apache OFBiz version 18.12.11, released in December, attackers are trying to take advantage of it by attacking vulnerable software instances. According to VulnCheck, CVE-2023-51467 can be exploited to run malware directly from memory, leaving minimal traces of hacking.
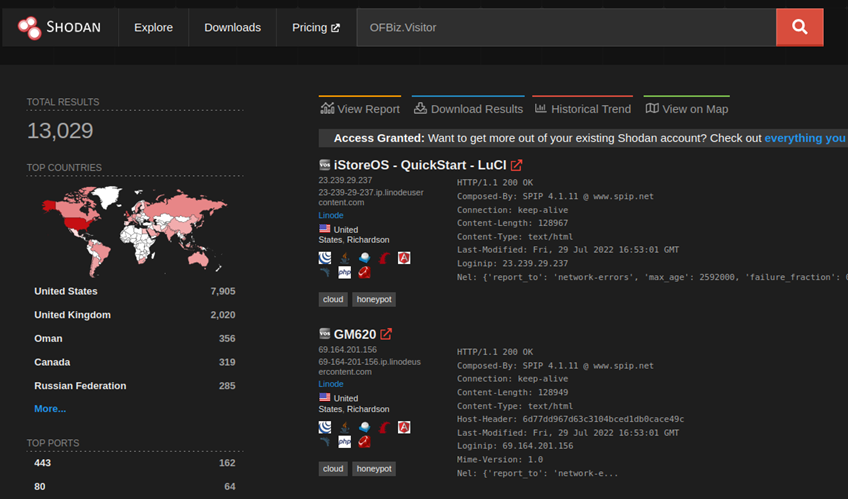
A search on Shodan shows more than 13,000 instances connected to the internet, but most of them are decoys. The number of real Apache OFBiz systems is about 1000, as the software is not popular with customers.
Although the implemented Apache security mechanisms (such as the Groovy sandbox ) block attempts to load web shells or run Java code through this endpoint, insufficient implementation of the sandbox means that an attacker can run curl commands and get a reverse bash shell on Linux systems. However, for an advanced attacker, such payloads are not ideal, since they affect the disk and depend on the specifics of Linux.
The Go-based PoC exploit developed by VulnCheck is a cross-platform solution that runs on both Windows and Linux. The PoC bypasses the blacklist by using the groovy.util functions.Eval to run the Reverse Nashorn Shell in memory as a payload.
There is a lot of noise around CVE-2023-51467, but there is no public malicious load, which casts doubt on the possibility of its use. VulnCheck experts came to the conclusion that exploitation is not only possible, but also allows you to execute arbitrary code in memory.
VulnCheck specialists have developed a Proof-of-Concept (PoC) code that exploits a recently discovered critical vulnerability in the Enterprise Resource Planning (ERP) system Apache OFBiz to run malicious code in memory.
We are talking about the vulnerability CVE-2023-51467 (CVSS score: 9.8), which is an authentication bypass error that allows an attacker to execute arbitrary code on a remote device and gain access to confidential information. The bug allows you to bypass another critical flaw in the same software ( CVE-2023-49070 with CVSS rating: 9.8).
Although the vulnerability was fixed in Apache OFBiz version 18.12.11, released in December, attackers are trying to take advantage of it by attacking vulnerable software instances. According to VulnCheck, CVE-2023-51467 can be exploited to run malware directly from memory, leaving minimal traces of hacking.

A search on Shodan shows more than 13,000 instances connected to the internet, but most of them are decoys. The number of real Apache OFBiz systems is about 1000, as the software is not popular with customers.
Although the implemented Apache security mechanisms (such as the Groovy sandbox ) block attempts to load web shells or run Java code through this endpoint, insufficient implementation of the sandbox means that an attacker can run curl commands and get a reverse bash shell on Linux systems. However, for an advanced attacker, such payloads are not ideal, since they affect the disk and depend on the specifics of Linux.
The Go-based PoC exploit developed by VulnCheck is a cross-platform solution that runs on both Windows and Linux. The PoC bypasses the blacklist by using the groovy.util functions.Eval to run the Reverse Nashorn Shell in memory as a payload.
There is a lot of noise around CVE-2023-51467, but there is no public malicious load, which casts doubt on the possibility of its use. VulnCheck experts came to the conclusion that exploitation is not only possible, but also allows you to execute arbitrary code in memory.

