Tomcat
Professional
- Messages
- 2,687
- Reaction score
- 1,036
- Points
- 113

Kaspersky Lab experts have prepared a report showing that detailed and well-implemented phishing attacks have become more frequent on Steam users since June this year.
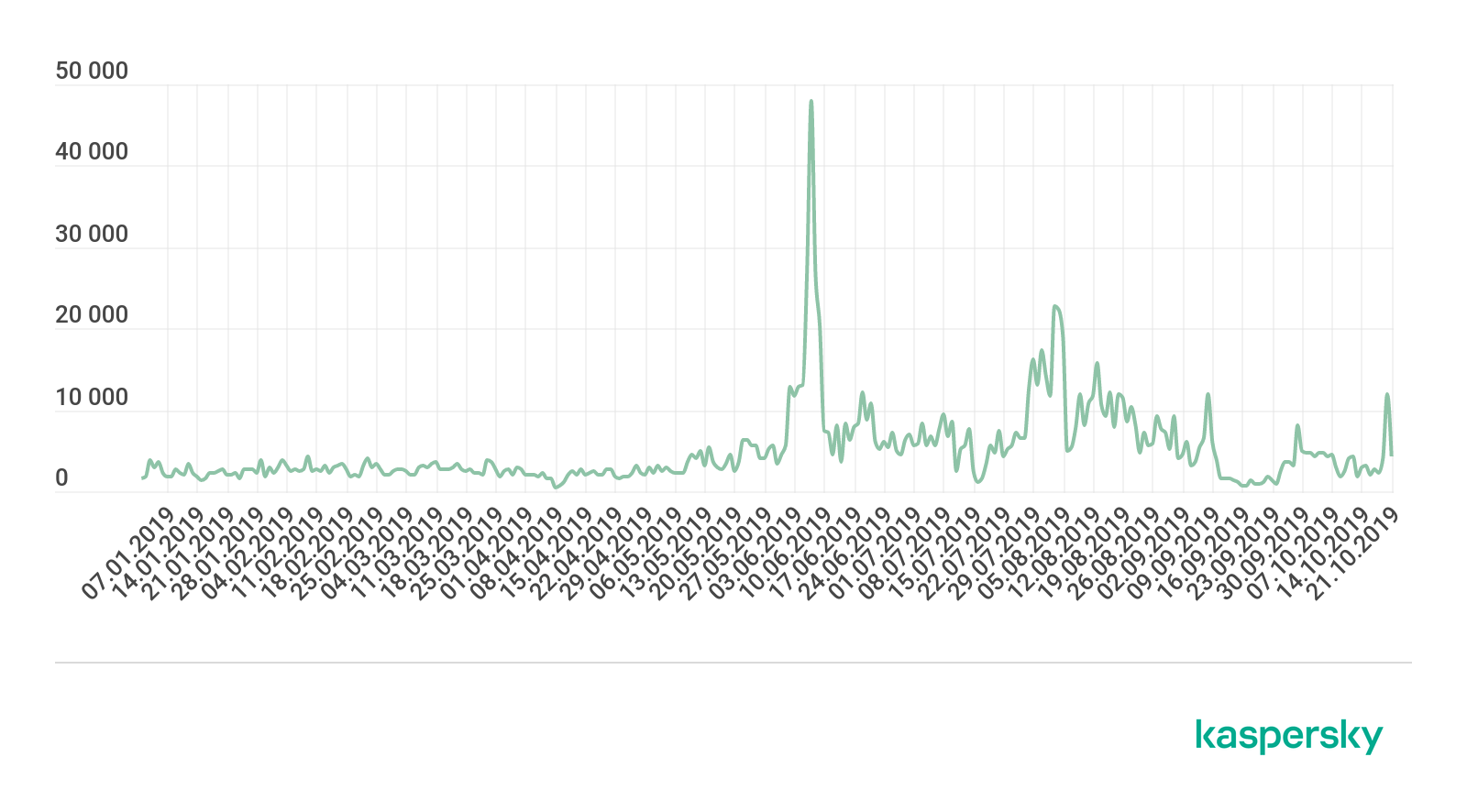
The researchers write that digital game distribution services have long been of interest to scammers. Typically, they try to obtain user credentials in order to strip the victim's characters and then sell the resulting items for real money. Steam is still one of the most popular services among users (and, accordingly, among cybercriminals).
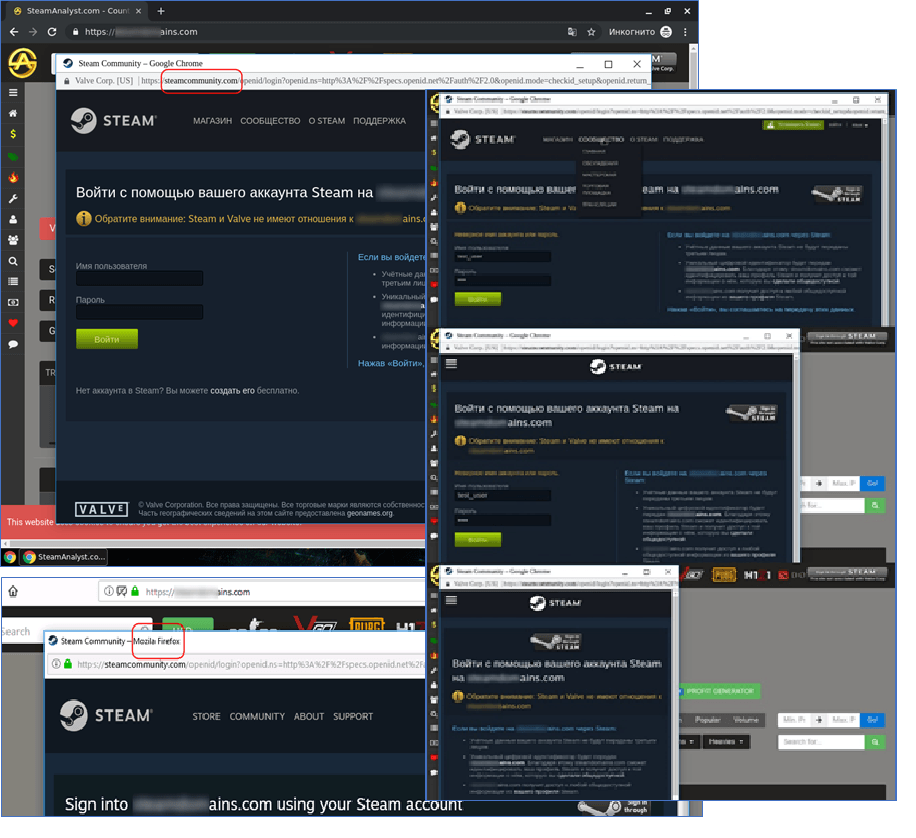
Attackers lure users to sites that mimic or copy real online stores - in this case, related to Steam - where they can purchase items for games. Such resources look very high quality, and it is quite difficult to suspect a fake, and in some cases it is almost impossible to distinguish a copy from the original.
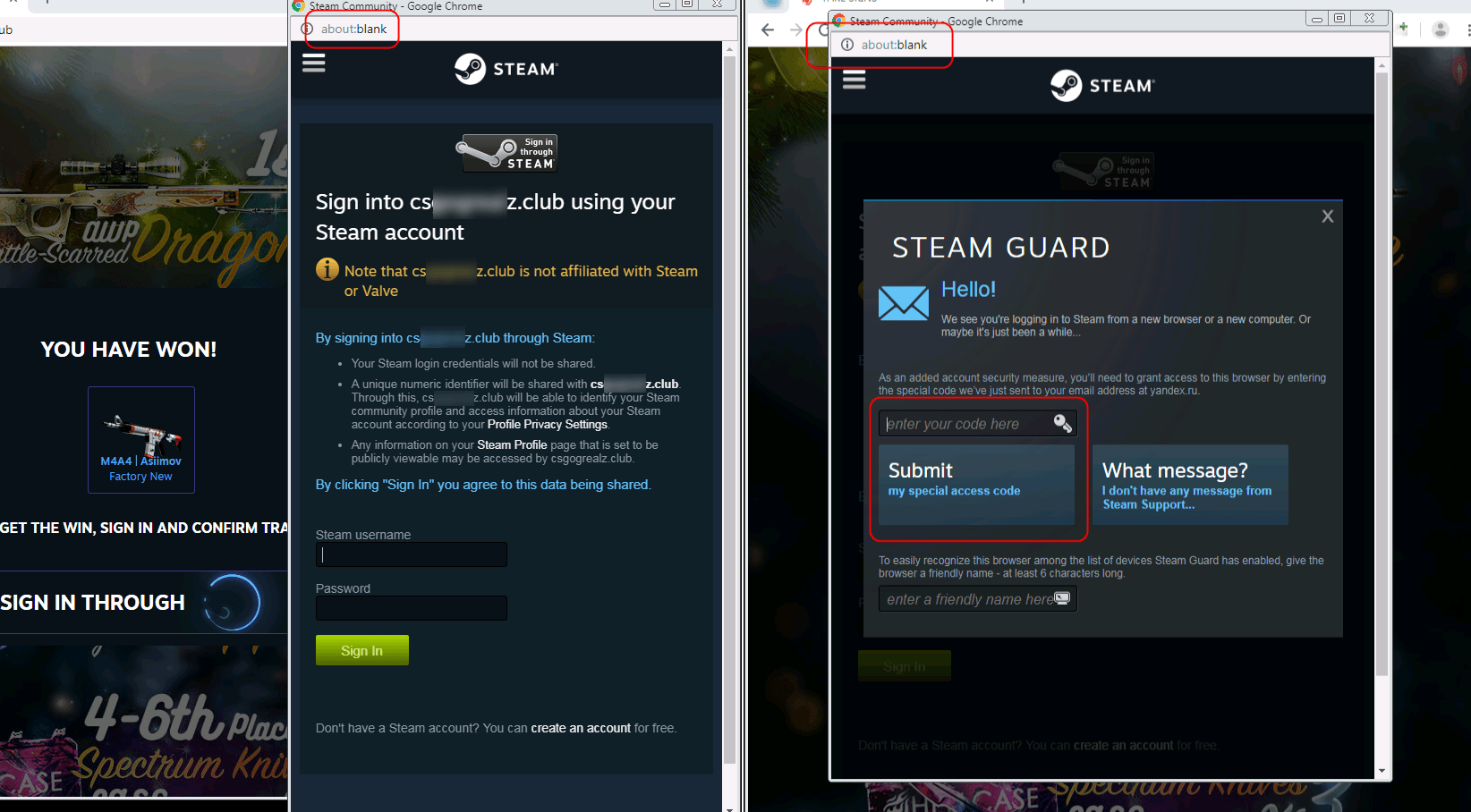
Scammers are not interested in the user spending a lot of time on such a site - sooner or later he may find that the site is fake. Therefore, phishing sites go "to the point" very quickly: as soon as the user clicks on any link, a window appears in front of him for entering the login and password from his account on Steam. By itself, this point of suspicion may not raise: the practice of using an account of one service to log in to another is quite common (registration in web services through social networks, Google authorization, and so on), and Steam also allows you to use an account to log in to third-party resources. Moreover, the trading platform needs access to the user's account to obtain data about the items that he has in stock.
A fake window for entering a login and password is very similar to the real one: the address bar contains the correct URL for the social portal of the Steam network, an adaptive layout is used, and if you open the link in another browser, with a different interface language, it will change in accordance with the new "locale" the content of the fake page, and its title.
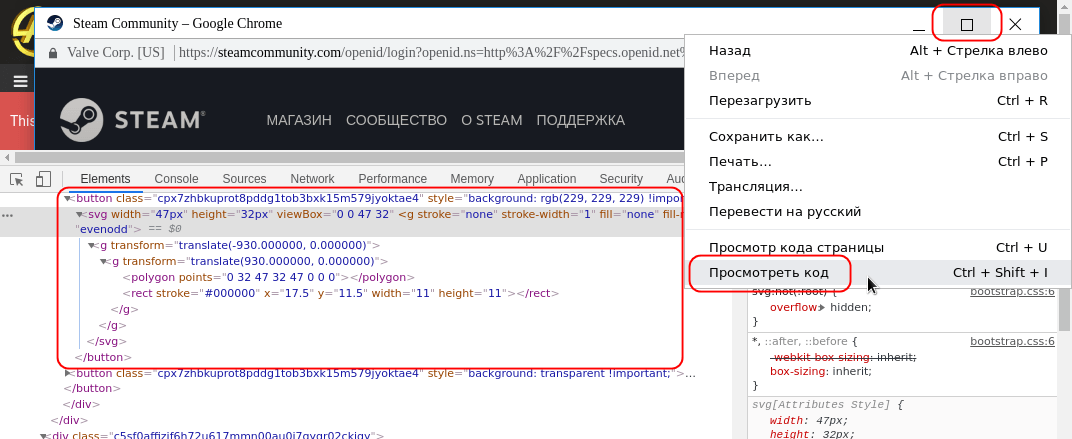
But as soon as we right-click on the title of this window (or on the controls), we will see the standard context menu for web pages. If you select the "view code" item in it, it becomes clear that the window is a fake, implemented by means of HTML and CSS:
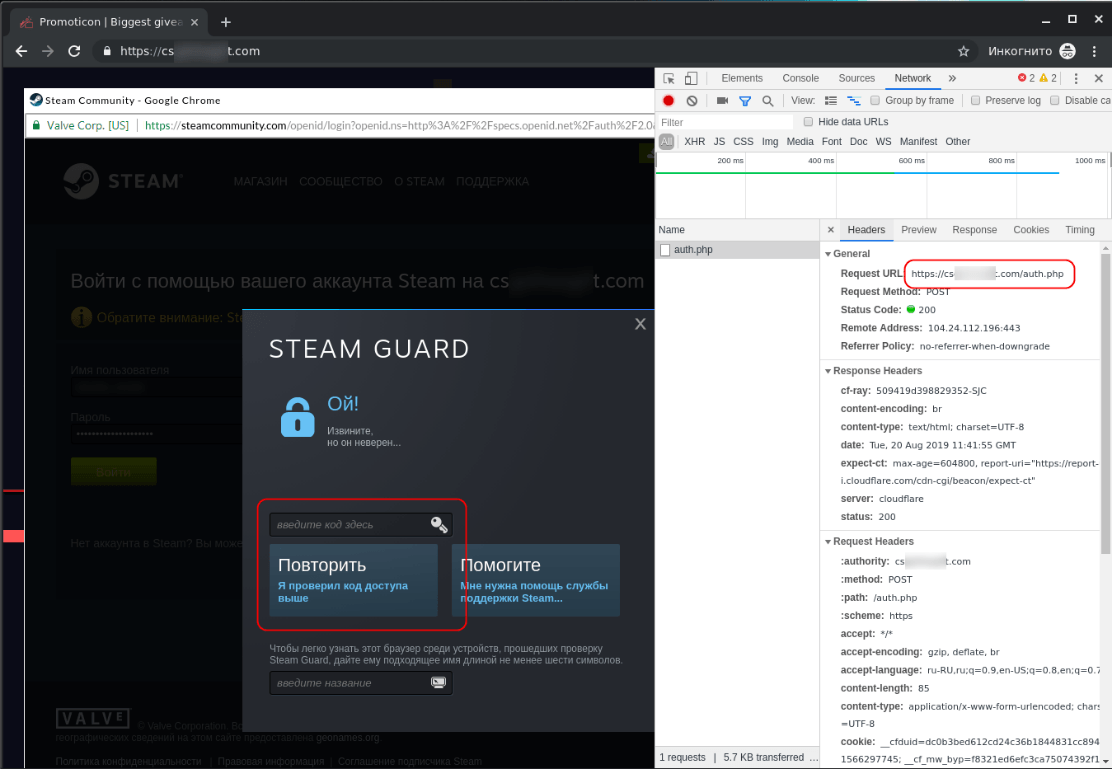
The plausibility of the fake authorization form is also added by the fact that the entered data is checked using original services: when entering an incorrect login and password, the user will be notified of an error.
After entering a valid username and password, you will be prompted for a two-factor authorization code, either sent by email or generated in the Steam Guard app. Obviously, the entered code will also be sent to the scammers, who, as a result, will gain full control over the account.
In addition to the "complex" approach of creating an authorization window using HTML and CSS, attackers do not forget about the good old tricks, when a fake form opens in a separate window, but with an empty address value. Despite the different method of displaying the window, the principle of its operation is similar to the examples described above: the form checks the correctness of the data entered, and if the password and login are suitable, it asks for a two-factor authorization code ...
(c) xakep.ru

