Carding 4 Carders
Professional
- Messages
- 2,724
- Reaction score
- 1,586
- Points
- 113
While the administrators are inactive, hackers are going to make some good money.
Vulnerable WS_FTP servers that are open to access from the Internet have become the target of massive ransomware attacks.
As experts from Sophos recently noted, the Reichsadler group of cybercriminals is mass deploying malicious ransomware programs using the LockBit 3.0 constructor, which was merged into the network in September 2022.
Sophos X-Ops reported: "Ransomware didn't wait long and started exploiting a recently discovered vulnerability in the WS_FTP Server software."
Despite the fact that Progress Software released a patch for this vulnerability last month, not all servers have been updated yet. Sophos X-Ops recorded some unsuccessful attempts to deploy ransomware through uncorrected services.
The attackers tried to perform an attack using the open GodPotato tool, which allows you to increase privileges to "NT AUTHORITY\SYSTEM" on Windows client platforms (from Windows 8 to Windows 11) and server platforms (from Windows Server 2012 to Windows Server 2022). An attempt to deploy malware on the victim's systems was prevented by Sophos security software.
It's funny that despite the unsuccessful attempt to encrypt the files, a note still appeared on the victim's device with demands to pay a ransom for decryption in the amount of $ 500.
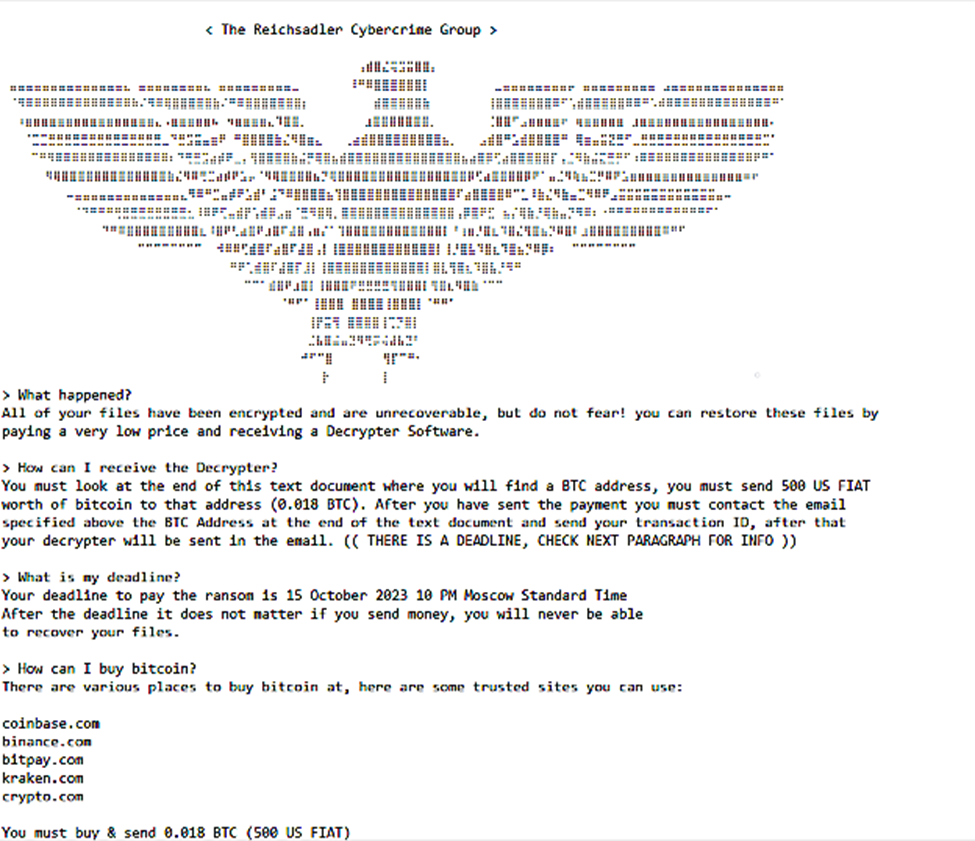
A ransom note worth 0.018 bitcoins
The low ransom amount indicates that vulnerable WS_FTP servers accessible from the Internet are likely targets for mass automated attacks. Thus, attackers hope to get rich by taking vulnerable systems with the amount, rather than the amount of a cash ransom.
A critical WS_FTP vulnerability known as CVE-2023-40044, which we reported earlier, has been caused .NET deserialization in the Ad Hoc Transfer Module, which allows attackers to execute commands on the underlying OS via remote HTTP requests.
Progress Software released security updates on September 27, strongly recommending that all administrators update vulnerable installations. Organizations that cannot immediately update their servers can block incoming attacks by disabling the vulnerable WS_FTP Server Ad Hoc Transfer module.
Progress Software is still dealing with the consequences of large-scale data attacks caused by the exploitation of a zero-day vulnerability in their MOVEit Transfer platform in May this year . It is reported that these attacks affected more than 2.5 thousand organizations and over 64 million people.
Vulnerable WS_FTP servers that are open to access from the Internet have become the target of massive ransomware attacks.
As experts from Sophos recently noted, the Reichsadler group of cybercriminals is mass deploying malicious ransomware programs using the LockBit 3.0 constructor, which was merged into the network in September 2022.
Sophos X-Ops reported: "Ransomware didn't wait long and started exploiting a recently discovered vulnerability in the WS_FTP Server software."
Despite the fact that Progress Software released a patch for this vulnerability last month, not all servers have been updated yet. Sophos X-Ops recorded some unsuccessful attempts to deploy ransomware through uncorrected services.
The attackers tried to perform an attack using the open GodPotato tool, which allows you to increase privileges to "NT AUTHORITY\SYSTEM" on Windows client platforms (from Windows 8 to Windows 11) and server platforms (from Windows Server 2012 to Windows Server 2022). An attempt to deploy malware on the victim's systems was prevented by Sophos security software.
It's funny that despite the unsuccessful attempt to encrypt the files, a note still appeared on the victim's device with demands to pay a ransom for decryption in the amount of $ 500.

A ransom note worth 0.018 bitcoins
The low ransom amount indicates that vulnerable WS_FTP servers accessible from the Internet are likely targets for mass automated attacks. Thus, attackers hope to get rich by taking vulnerable systems with the amount, rather than the amount of a cash ransom.
A critical WS_FTP vulnerability known as CVE-2023-40044, which we reported earlier, has been caused .NET deserialization in the Ad Hoc Transfer Module, which allows attackers to execute commands on the underlying OS via remote HTTP requests.
Progress Software released security updates on September 27, strongly recommending that all administrators update vulnerable installations. Organizations that cannot immediately update their servers can block incoming attacks by disabling the vulnerable WS_FTP Server Ad Hoc Transfer module.
Progress Software is still dealing with the consequences of large-scale data attacks caused by the exploitation of a zero-day vulnerability in their MOVEit Transfer platform in May this year . It is reported that these attacks affected more than 2.5 thousand organizations and over 64 million people.

