Hacker
Professional
- Messages
- 1,041
- Reaction score
- 851
- Points
- 113
The content of the article
A bit of theory
It is a well-known fact: all applications in iOS run in the so-called sandbox - an isolated environment from which they cannot directly access the components of the operating system and other programs. This ensures high security of the OS: when working in a sandbox, the application interacts only with its own data and resources, so the malicious program will simply have nowhere to roam.
In addition, Apple only allows apps to be installed on iOS devices from their own App Store directory, where they come after thorough review. “Unhappy” owners of iPhones are deprived even of the function “Allow the installation of applications from unknown sources”, which is familiar to Android users - if the necessary program is not in the App Store, it will most likely not be on your smartphone either.
On the other hand, such strict restrictions deprive the owners of Apple devices of a number of useful features. If your iPhone belongs to an outdated model range and its operating system has already retired, sooner or later you will face a complete impossibility to install or update the program you need through the App Store.
One day your favorite application will refuse to launch, saying that the developers have released a new version for it a long time ago, which is time to replace the current one. By clicking on the "Update" button, the App Store program will start and happily inform you that a fresher operating system is required to install a new version of the software you are interested in. Finally, going to the "Settings" section, you will be surprised to find that your device already has the most current version of iOS, and to use a more modern version, you will have to run to a nearby store for a new iPhone. The circle is complete, as one former Jedi used to say.
There are exactly two ways out of this impasse. The first is to sell a kidney on the black market and buy yourself a new phone with a bitten apple on the case, holding the hope that it will not lose its relevance over the next few years. The second way is jailbreak. This incomprehensible word means a banal operating system hack that allows you to get access to the file system not authorized by the phone manufacturer, and in addition, install applications from third-party repositories or, in some cases, directly from your computer.
Jailbreak, of course, will not turn your fourth iPhone into the tenth and will not give you the opportunity to use the latest version of iOS on ancient hardware. But on the other hand, it will allow you to find and install an old version of the program you need on your smartphone, which may not be able to boast of a modern set of functions, but it will at least work stably.
There is another loophole that allows you to almost officially install various software on iPhones and iPads, bypassing the App Store. It is called Mobile Device Management (MDM). It is a set of tools that allows you to manage iOS devices in a corporate environment. It is used, in particular, to install various "internal" applications on the "apple" devices of employees of firms, which are not intended for wide distribution outside the company.
Such programs can be delivered to iOS devices without having to download them to the App Store and go through painful testing. It is also obvious that it will not be possible to install any application on an iPhone using this method: the method has a number of natural limitations designed to exclude its possible use by malefactors.
Does all this mean that the existence of malware for iOS is impossible in principle and that users of Apple devices can feel completely safe? No. Dangerous programs for iOS like that legendary gopher: not visible, but still there. I will tell you about the most famous technologies for distributing such software.
Spy games
By 2013, when Apple mobile phones had already firmly occupied their niche in the global market, and the iPhone 5s appeared in retail, information security specialists knew about 50 spyware for iOS. Almost all of them were intended for devices with jailbreak, and almost all of them were distributed through the "pirate" repository of Cydia - an alternative directory of applications for jailbroken "apple" devices.
The user could find a spy on his phone either unknowingly (some were presented in the catalog under completely neutral names), or as a result of a purposeful installation, if some well-wisher decided, for example, to help the neophyte with setting up the device.
These programs had a set of functions quite traditional for spyware: theft of SMS and call history, contacts and photos, browser history, transmission of GPS coordinates. More advanced spies recorded information about the calls made, could record audio using the built-in microphone, take photos on command from the server, copy e-mail messages and social media correspondence that the user conducted using client applications. All information was sent to the control server, where it could be obtained in a convenient and accessible form.
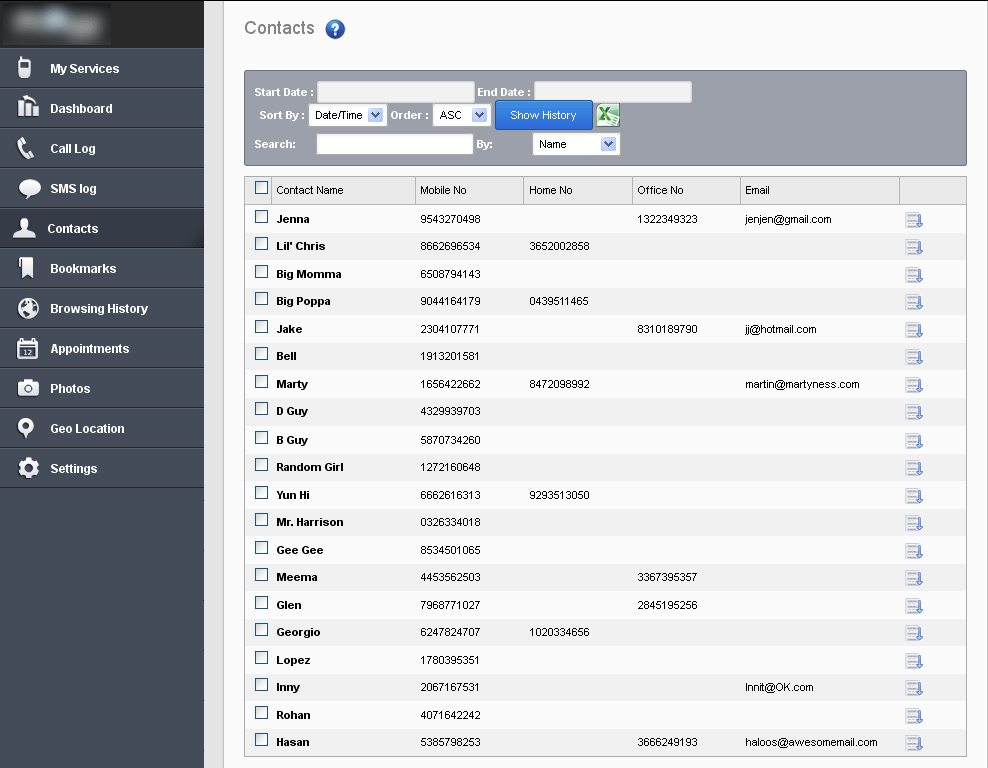
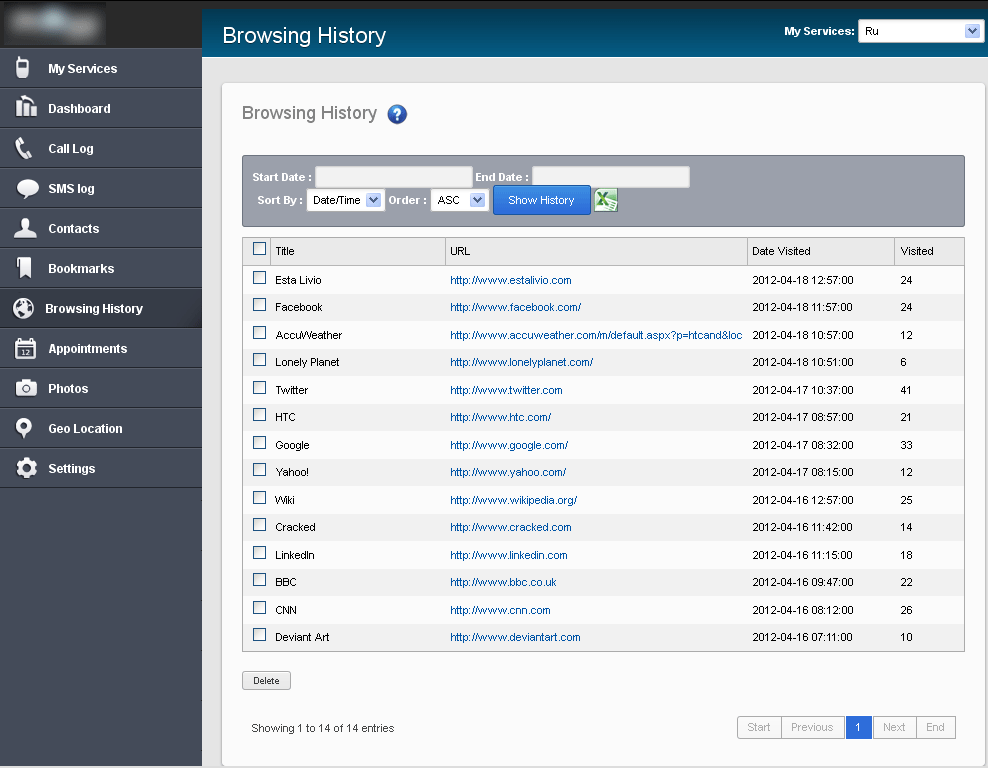
Spy admin interface for iOS
Such spies did not create an application icon on the system. If desired, only a part of the functions could be activated in them in order to reduce the likelihood of the program being detected by the user. The most popular spyware for iOS in those days were SpyBubble, TopSpy, Tracker, OwnSpy, TruSpy, and FlexiSpy.
However, all these applications could not be called full-fledged Trojans, because, firstly, they had to be installed on the device manually, secondly, this required a jailbreak and, thirdly, many of them were sold on the Internet practically legally as means parental control or control over employees of the enterprise.
MDM technology
Because of the paranoid security mechanisms that Apple uses in the architecture of its mobile OS, creating full-fledged malware for this platform turned out to be laborious, but it did not come as a surprise to specialists. If you can't enter iOS through the door, you can break in through a window - that's what the attackers thought, and to distribute Trojans, they began to use the same mechanism for distributing MDM applications using corporate certificates.
In short, it works like this. First, you need to deploy a special MDM server, obtain an Apple Push Notification Service (APNs certificate) certificate for it and install it on this server. Next, you need to create a custom configuration profile, which is actually a modified .plist file that needs to be delivered to the iOS device. The device receives a push notification from the server, establishes a TLS connection with the server and, after checking the certificate, is authorized on it.
Next, the server can send the device a set of settings (MDM Payload) associated with its configuration profile. In this case, the MDM server does not have to be in the same network as the mobile device; it is sufficient that it is accessible from the outside via the HTTPS protocol. As a result, using an MDM server, it becomes possible to manage an iOS device and install applications on it, bypassing the App Store.
All this implies serious dancing with a tambourine, but theoretically opens a loophole for MITM attacks. Using this technology, it is quite possible to implement targeted "point" attacks, which was proven in practice in the summer of 2020. Among other things, an attacker can be, for example, an offended employee of a company using MDM, if he has access to the server.
They say that it was in this way that a client base and correspondence with counterparties were stolen from a well-known American company, which subsequently leaked to competitors along with one of the former employees. It seems that it is impossible to organize mass distribution of malware using MDM technology. However, it is not.
In 2015, using MDM, a large-caliber distribution of the YiSpecter Trojan was arranged, hidden in a client application - a video player for watching porn. It was distributed mainly in China under the guise of a fork of the popular QVOD porn player in this country, the developers of which were covered by the Chinese police in 2014. Following the instructions found on the Internet, users themselves copied the necessary profiles and certificates to their device in order to be able to download commercial or “prohibited” applications to their phone for free, for which they paid.
In addition, the Trojan's developers organized a whole partnership program, within the framework of which they paid 2.5 yuan for each installation of the software they ran. The offer was immediately taken advantage of by numerous "basement" service centers for the repair of iPhones and firms specializing in the sale of refurbished "Apple" devices, and began to quietly add the necessary components to the system to grateful customers. From a black sheep, as they say, at least a tuft of wool.
As a result, thousands of unsuspecting Chinese became the owners of the "surprise" iPhones.
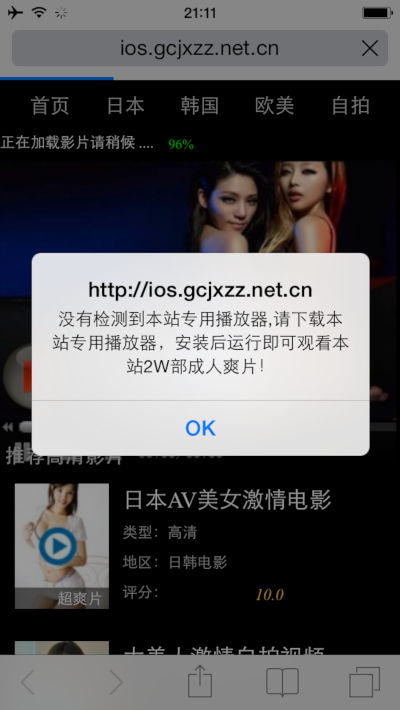
This is how the YiSpecter iOS Trojan was spread
YiSpecter installed a special module on the device that downloaded the malware components if they were removed, and at the command of the bot bots could quietly remove any programs from the phone, replacing them with trojanized copies. He received the necessary software from his own MDM server.
The user did not notice the trick, since the clients of social networks and instant messengers, substituted by the Trojan, worked as usual, from time to time tapping on the control server and dropping confidential information there, including correspondence and the victim's credentials. Among other things, the trooper could display full-screen advertisements on the screen of the infected device, due to which, in fact, it was detected.
In general, it is clear that in this way it is difficult to organize a mass infection of "apple" devices, although the Chinese almost succeeded. Another thing is important: YiSpecter was one of the first real malware capable of infecting an iPhone without jailbreak.
DRM technology
Trojans that did not use MDM to spread originated from the same place as most of the original IT developments - from China. This brings together Apple's greedy desire to earn as much as possible from distributing iOS apps and some users' irresistible passion for freebies.
As you know, applications for the iPhone must be purchased from the official App Store - at least that's what Apple thinks. If the program is honestly bought on this resource and is listed on the user's account, he can install it on the phone later by connecting the latter to the computer using a USB-Lighting cable and using iTunes.
When launched, the program will check the user's Apple ID and ask for an authorization code to make sure that the application installed on the mobile device was actually purchased by this user in a lawful manner. It uses Apple's Digital Rights Management (DRM) technology.
To bypass this check, the cunning Chinese have come up with a special software that emulates the actions of iTunes. By purchasing an application from the App Store, the creators of this program intercept and save the authorization code using a vulnerability in the DRM implementation, and then transfer it to all other users of their application.
As a result, they get the opportunity to install on their iPhone or iPad a program for which they did not pay. One of these applications is called Aisi.
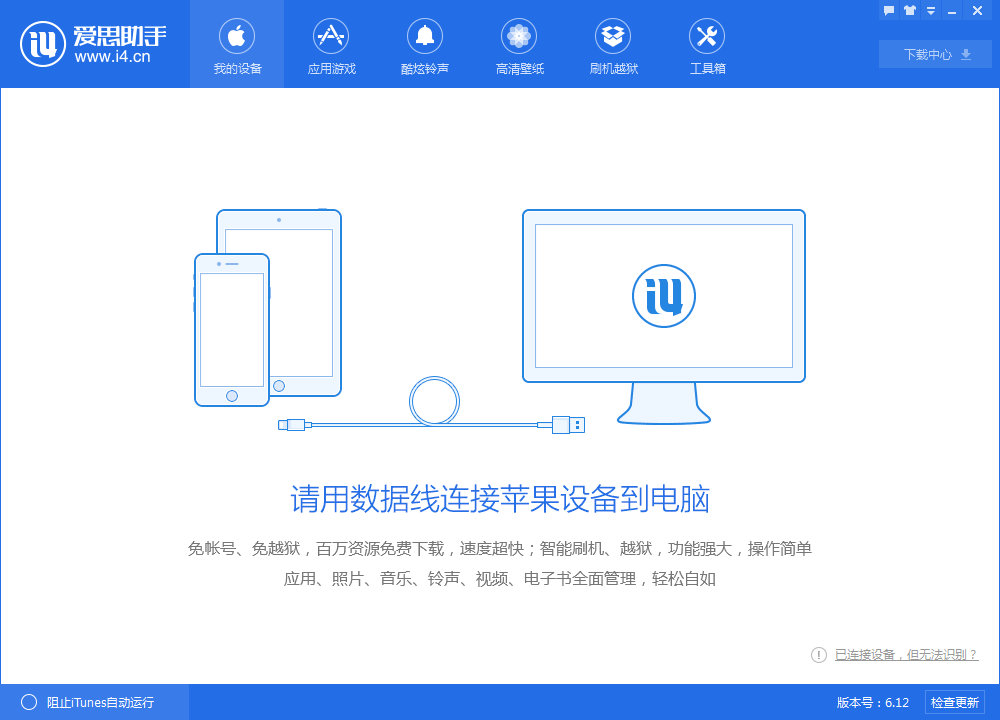
Aisi program
Aisi allows users of Apple devices not only to install illegal software, but also to update and create backup copies of the firmware, jailbreak, download ringtones and various multimedia content to the phone.
Previously, Chinese virus makers created and placed in the App Store a small utility that allows you to change the wallpaper on an iOS device. The utility successfully passed all Apple checks, even though it hid in itself one potentially dangerous function, which was activated, however, when a number of external conditions coincided - this is probably why it was not noticed.
After connecting the device to the computer and enabling the "trust" mode between devices, Aisi secretly installed the same utility in iOS using the technology described above, informing the device that it had allegedly been previously purchased by the user in the App Store. When launched, the application asked for your Apple ID account credentials. This information was immediately transmitted to the control server.
Further, in general, you can create a lot of interesting things with the device: the leak of Apple ID opens up a lot of opportunities for potential attackers. For example, you can change the password, lock the device, and demand a ransom from the owner to unlock it. Or you can access iCloud storage and admire other people's vacation photos. This is at its best.
Conclusions
Despite the fact that iOS is indeed a very secure and secure operating system, we can see that virus writers were able to find loopholes in it too. True, all of them, without exception, represent a close symbiosis of techniques and social engineering. Developers of malware for iPhones and iPads are working in this direction - playing on the naivete or greed of the owners of Apple phones.
However, the interest in them is not surprising: it is believed that buyers of expensive phones made by Apple Corporation are wealthy enough to have something to profit from. Therefore, users of such devices need to be especially vigilant and cautious: at any time they may be targeted by attackers, because technology does not stand still.
- A bit of theory
- Spy games
- MDM technology
- DRM technology
- Conclusions
A bit of theory
It is a well-known fact: all applications in iOS run in the so-called sandbox - an isolated environment from which they cannot directly access the components of the operating system and other programs. This ensures high security of the OS: when working in a sandbox, the application interacts only with its own data and resources, so the malicious program will simply have nowhere to roam.
In addition, Apple only allows apps to be installed on iOS devices from their own App Store directory, where they come after thorough review. “Unhappy” owners of iPhones are deprived even of the function “Allow the installation of applications from unknown sources”, which is familiar to Android users - if the necessary program is not in the App Store, it will most likely not be on your smartphone either.
On the other hand, such strict restrictions deprive the owners of Apple devices of a number of useful features. If your iPhone belongs to an outdated model range and its operating system has already retired, sooner or later you will face a complete impossibility to install or update the program you need through the App Store.
One day your favorite application will refuse to launch, saying that the developers have released a new version for it a long time ago, which is time to replace the current one. By clicking on the "Update" button, the App Store program will start and happily inform you that a fresher operating system is required to install a new version of the software you are interested in. Finally, going to the "Settings" section, you will be surprised to find that your device already has the most current version of iOS, and to use a more modern version, you will have to run to a nearby store for a new iPhone. The circle is complete, as one former Jedi used to say.
There are exactly two ways out of this impasse. The first is to sell a kidney on the black market and buy yourself a new phone with a bitten apple on the case, holding the hope that it will not lose its relevance over the next few years. The second way is jailbreak. This incomprehensible word means a banal operating system hack that allows you to get access to the file system not authorized by the phone manufacturer, and in addition, install applications from third-party repositories or, in some cases, directly from your computer.
Jailbreak, of course, will not turn your fourth iPhone into the tenth and will not give you the opportunity to use the latest version of iOS on ancient hardware. But on the other hand, it will allow you to find and install an old version of the program you need on your smartphone, which may not be able to boast of a modern set of functions, but it will at least work stably.
There is another loophole that allows you to almost officially install various software on iPhones and iPads, bypassing the App Store. It is called Mobile Device Management (MDM). It is a set of tools that allows you to manage iOS devices in a corporate environment. It is used, in particular, to install various "internal" applications on the "apple" devices of employees of firms, which are not intended for wide distribution outside the company.
Such programs can be delivered to iOS devices without having to download them to the App Store and go through painful testing. It is also obvious that it will not be possible to install any application on an iPhone using this method: the method has a number of natural limitations designed to exclude its possible use by malefactors.
Does all this mean that the existence of malware for iOS is impossible in principle and that users of Apple devices can feel completely safe? No. Dangerous programs for iOS like that legendary gopher: not visible, but still there. I will tell you about the most famous technologies for distributing such software.
Spy games
By 2013, when Apple mobile phones had already firmly occupied their niche in the global market, and the iPhone 5s appeared in retail, information security specialists knew about 50 spyware for iOS. Almost all of them were intended for devices with jailbreak, and almost all of them were distributed through the "pirate" repository of Cydia - an alternative directory of applications for jailbroken "apple" devices.
The user could find a spy on his phone either unknowingly (some were presented in the catalog under completely neutral names), or as a result of a purposeful installation, if some well-wisher decided, for example, to help the neophyte with setting up the device.
These programs had a set of functions quite traditional for spyware: theft of SMS and call history, contacts and photos, browser history, transmission of GPS coordinates. More advanced spies recorded information about the calls made, could record audio using the built-in microphone, take photos on command from the server, copy e-mail messages and social media correspondence that the user conducted using client applications. All information was sent to the control server, where it could be obtained in a convenient and accessible form.


Spy admin interface for iOS
Such spies did not create an application icon on the system. If desired, only a part of the functions could be activated in them in order to reduce the likelihood of the program being detected by the user. The most popular spyware for iOS in those days were SpyBubble, TopSpy, Tracker, OwnSpy, TruSpy, and FlexiSpy.
However, all these applications could not be called full-fledged Trojans, because, firstly, they had to be installed on the device manually, secondly, this required a jailbreak and, thirdly, many of them were sold on the Internet practically legally as means parental control or control over employees of the enterprise.
MDM technology
Because of the paranoid security mechanisms that Apple uses in the architecture of its mobile OS, creating full-fledged malware for this platform turned out to be laborious, but it did not come as a surprise to specialists. If you can't enter iOS through the door, you can break in through a window - that's what the attackers thought, and to distribute Trojans, they began to use the same mechanism for distributing MDM applications using corporate certificates.
In short, it works like this. First, you need to deploy a special MDM server, obtain an Apple Push Notification Service (APNs certificate) certificate for it and install it on this server. Next, you need to create a custom configuration profile, which is actually a modified .plist file that needs to be delivered to the iOS device. The device receives a push notification from the server, establishes a TLS connection with the server and, after checking the certificate, is authorized on it.
Next, the server can send the device a set of settings (MDM Payload) associated with its configuration profile. In this case, the MDM server does not have to be in the same network as the mobile device; it is sufficient that it is accessible from the outside via the HTTPS protocol. As a result, using an MDM server, it becomes possible to manage an iOS device and install applications on it, bypassing the App Store.
All this implies serious dancing with a tambourine, but theoretically opens a loophole for MITM attacks. Using this technology, it is quite possible to implement targeted "point" attacks, which was proven in practice in the summer of 2020. Among other things, an attacker can be, for example, an offended employee of a company using MDM, if he has access to the server.
They say that it was in this way that a client base and correspondence with counterparties were stolen from a well-known American company, which subsequently leaked to competitors along with one of the former employees. It seems that it is impossible to organize mass distribution of malware using MDM technology. However, it is not.
In 2015, using MDM, a large-caliber distribution of the YiSpecter Trojan was arranged, hidden in a client application - a video player for watching porn. It was distributed mainly in China under the guise of a fork of the popular QVOD porn player in this country, the developers of which were covered by the Chinese police in 2014. Following the instructions found on the Internet, users themselves copied the necessary profiles and certificates to their device in order to be able to download commercial or “prohibited” applications to their phone for free, for which they paid.
In addition, the Trojan's developers organized a whole partnership program, within the framework of which they paid 2.5 yuan for each installation of the software they ran. The offer was immediately taken advantage of by numerous "basement" service centers for the repair of iPhones and firms specializing in the sale of refurbished "Apple" devices, and began to quietly add the necessary components to the system to grateful customers. From a black sheep, as they say, at least a tuft of wool.
As a result, thousands of unsuspecting Chinese became the owners of the "surprise" iPhones.

This is how the YiSpecter iOS Trojan was spread
YiSpecter installed a special module on the device that downloaded the malware components if they were removed, and at the command of the bot bots could quietly remove any programs from the phone, replacing them with trojanized copies. He received the necessary software from his own MDM server.
The user did not notice the trick, since the clients of social networks and instant messengers, substituted by the Trojan, worked as usual, from time to time tapping on the control server and dropping confidential information there, including correspondence and the victim's credentials. Among other things, the trooper could display full-screen advertisements on the screen of the infected device, due to which, in fact, it was detected.
In general, it is clear that in this way it is difficult to organize a mass infection of "apple" devices, although the Chinese almost succeeded. Another thing is important: YiSpecter was one of the first real malware capable of infecting an iPhone without jailbreak.
DRM technology
Trojans that did not use MDM to spread originated from the same place as most of the original IT developments - from China. This brings together Apple's greedy desire to earn as much as possible from distributing iOS apps and some users' irresistible passion for freebies.
As you know, applications for the iPhone must be purchased from the official App Store - at least that's what Apple thinks. If the program is honestly bought on this resource and is listed on the user's account, he can install it on the phone later by connecting the latter to the computer using a USB-Lighting cable and using iTunes.
When launched, the program will check the user's Apple ID and ask for an authorization code to make sure that the application installed on the mobile device was actually purchased by this user in a lawful manner. It uses Apple's Digital Rights Management (DRM) technology.
To bypass this check, the cunning Chinese have come up with a special software that emulates the actions of iTunes. By purchasing an application from the App Store, the creators of this program intercept and save the authorization code using a vulnerability in the DRM implementation, and then transfer it to all other users of their application.
As a result, they get the opportunity to install on their iPhone or iPad a program for which they did not pay. One of these applications is called Aisi.

Aisi program
Aisi allows users of Apple devices not only to install illegal software, but also to update and create backup copies of the firmware, jailbreak, download ringtones and various multimedia content to the phone.
Previously, Chinese virus makers created and placed in the App Store a small utility that allows you to change the wallpaper on an iOS device. The utility successfully passed all Apple checks, even though it hid in itself one potentially dangerous function, which was activated, however, when a number of external conditions coincided - this is probably why it was not noticed.
After connecting the device to the computer and enabling the "trust" mode between devices, Aisi secretly installed the same utility in iOS using the technology described above, informing the device that it had allegedly been previously purchased by the user in the App Store. When launched, the application asked for your Apple ID account credentials. This information was immediately transmitted to the control server.
Further, in general, you can create a lot of interesting things with the device: the leak of Apple ID opens up a lot of opportunities for potential attackers. For example, you can change the password, lock the device, and demand a ransom from the owner to unlock it. Or you can access iCloud storage and admire other people's vacation photos. This is at its best.
Conclusions
Despite the fact that iOS is indeed a very secure and secure operating system, we can see that virus writers were able to find loopholes in it too. True, all of them, without exception, represent a close symbiosis of techniques and social engineering. Developers of malware for iPhones and iPads are working in this direction - playing on the naivete or greed of the owners of Apple phones.
However, the interest in them is not surprising: it is believed that buyers of expensive phones made by Apple Corporation are wealthy enough to have something to profit from. Therefore, users of such devices need to be especially vigilant and cautious: at any time they may be targeted by attackers, because technology does not stand still.

