Father
Professional
- Messages
- 2,602
- Reaction score
- 837
- Points
- 113
The world of information security has enough references to the Wild West. For example, the same division of hackers into Black and White Hat, which came from westerns: villains always wear black hats, and good guys – white.
Continuing this analogy, we can say that DDoS is a revolver that hackers "grab" first of all, attacking the infrastructure of certain companies. The frequency of DDoS attacks is growing every year. The number of attacks of this type has increased several times over the past year alone.
In this article, we will analyze the "main caliber" of hacker attacks, consider its history and current application trends.
The first recorded DOS attack occurred almost half a century ago – in 1974. Its initiator was a schoolboy David Dennis. Using the terminal vulnerability he identified to the EXT command, he disabled 31 terminals of the University of Illinois Computer Computing Laboratory.
For almost half a century, DOS attacks have ceased to be a threat, due to weak characteristics:
For all these reasons, DOS attacks are almost nonexistent in the wild. They do not require much knowledge and technical resources to reflect them. However, they also "live" in the educational system, as an element of training in the basics of DDoS, and in general, the problem of denial of service.
DOS attacks have been replaced by DDoS attacks: they have the same advantages, but they are much more difficult to block. The main difference is the ability to involve more devices and users in the attack. Such a decentralized attack is more complex both in terms of detection and in terms of counteraction.
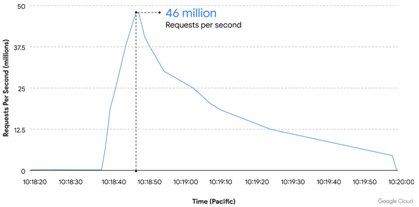
Another important trend is an increase in the "weight" of attacks, that is, their power. In mid-August, Google reported on repelling the most powerful attack in history. To understand its scale, just evaluate the graph of the number of incoming requests.
Attacks of this scale have become possible thanks to the development of botnets. A botnet is a network of infected devices that attackers use in a DDoS attack. At the same time, it is quite difficult to detect the fact of infection of the device: malware manifests itself only at the time of a cyber attack, and remains passive the rest of the time, practically without affecting the performance of the computer.
Hacker activism has also gained unprecedented momentum this year. For example, KillNet and NoName057(16) groups conducted a series of cyber attacks on Estonian companies and government agencies in response to calls from a number of local politicians to restrict the entry of Russians to EU countries.
At the same time, as modern practice has shown, hackers themselves can become a victim of DDoS. Hackers from the LockBit group began to blackmail Entrust after a successful attack. But instead of money, they received a powerful DDoS attack on their own resources.
Calls for hackers to delete data related to Entrust were found in the attack logs. The effectiveness of such countermeasures is still difficult to predict, because much will depend on the further development of events. But the very fact of using a DDoS attack to fight hackers is a precedent.
Tools to protect against such attacks have been around for a long time and are well established. There are both comprehensive solutions and specialized ones that specifically address the problem of frequent DDoS attacks.
At the same time, Russian businesses should quickly become familiar with this class of security solutions, since a significant decline in DDOS attacks is unlikely to be expected in the foreseeable future.
Continuing this analogy, we can say that DDoS is a revolver that hackers "grab" first of all, attacking the infrastructure of certain companies. The frequency of DDoS attacks is growing every year. The number of attacks of this type has increased several times over the past year alone.
In this article, we will analyze the "main caliber" of hacker attacks, consider its history and current application trends.
Differences between DOS and DDOS attacks
The development of DDoS attacks was preceded by DOS: a simplified version of the attack that blocks user access to a resource by creating an excessive number of requests.The first recorded DOS attack occurred almost half a century ago – in 1974. Its initiator was a schoolboy David Dennis. Using the terminal vulnerability he identified to the EXT command, he disabled 31 terminals of the University of Illinois Computer Computing Laboratory.
Alexander Gerasimov
CISO Awillix
DOS attacks occur as a result of errors when creating web resources. For example, a site sends a file of several Megabytes. Also, the possibility of implementing DOS attacks occurs when there are errors in the resource logic.
For almost half a century, DOS attacks have ceased to be a threat, due to weak characteristics:
- The attack is conducted from the same network, most often on behalf of a single host.
- A DOS attack is easily detected by the contents of log files.
- DOS is not only easy to detect, but also to suppress. To protect yourself from DOS attacks, just block one source.
For all these reasons, DOS attacks are almost nonexistent in the wild. They do not require much knowledge and technical resources to reflect them. However, they also "live" in the educational system, as an element of training in the basics of DDoS, and in general, the problem of denial of service.
Valentin Sokolov
IT Director of the RCloud by 3data cloud platform
When providing cloud services for our RCloud by 3data platform, we often receive questions from customers about information security. Users also face DOS attacks on servers, but DDoS attacks are much more common. The key difference between them is that in the second case, several resources are used at once to clog the channel. Now you can see huge bursts of malicious traffic, so it is important to deal with information security issues in a timely manner and not put them on hold.
DOS attacks have been replaced by DDoS attacks: they have the same advantages, but they are much more difficult to block. The main difference is the ability to involve more devices and users in the attack. Such a decentralized attack is more complex both in terms of detection and in terms of counteraction.
DDoS: the general trend of 2022
This year, the geopolitical crisis has greatly affected hacker activity. First of all, it is worth mentioning the increase in the number of cyber attacks. For example, according to Kaspersky Lab, the number of attacks in March was eight times higher than the number of attacks in the same period last year.Vitaly Arbuzov
founder of INPRO. digital
The growth of cyber attacks is not only a threat to business and the Russian economy as a whole, but also a good opportunity to improve domestic technologies and make them competitive on the international market. The Russian IT industry will need about 30 thousand specialists in the field of information security and cybersecurity to fulfill this goal.
DDoS attacks, malware, social engineering, and customer data leaks are not new phenomena. Many experts called 2021 a record year for the number of data leaks. At that time, Russia's share in the global distribution of data leaks was almost 17 %.
However, 2022 may well take a leading position in terms of the number of cybercrimes committed. In March 2022, the number of DDoS attacks on Russian organizations increased eight-fold compared to the same month in 2021. The duration of digital attacks has also increased. If in February-March of last year it was 12 minutes, now this value reaches 29.5 hours.
Another important trend is an increase in the "weight" of attacks, that is, their power. In mid-August, Google reported on repelling the most powerful attack in history. To understand its scale, just evaluate the graph of the number of incoming requests.

Attacks of this scale have become possible thanks to the development of botnets. A botnet is a network of infected devices that attackers use in a DDoS attack. At the same time, it is quite difficult to detect the fact of infection of the device: malware manifests itself only at the time of a cyber attack, and remains passive the rest of the time, practically without affecting the performance of the computer.
Igor Grachev
Head of Information Security Department at BBR Bank
A set of infected devices of users who do not know that their computer is involved in a DDOS attack is now called a "botnet". The botnet is controlled by a so-called "botmaster", which can be performed by either a single attacker or a group of hackers. The number of botnets ranges from several tens to hundreds of thousands of devices. In addition, it should be noted that recently such activity as support for "hacktivism" has been gaining popularity, i.e. users voluntarily join botnets, supporting the ideas and values promoted by botmaster.
Hacker activism has also gained unprecedented momentum this year. For example, KillNet and NoName057(16) groups conducted a series of cyber attacks on Estonian companies and government agencies in response to calls from a number of local politicians to restrict the entry of Russians to EU countries.
At the same time, as modern practice has shown, hackers themselves can become a victim of DDoS. Hackers from the LockBit group began to blackmail Entrust after a successful attack. But instead of money, they received a powerful DDoS attack on their own resources.
Calls for hackers to delete data related to Entrust were found in the attack logs. The effectiveness of such countermeasures is still difficult to predict, because much will depend on the further development of events. But the very fact of using a DDoS attack to fight hackers is a precedent.
Conclusion
Denial-of-service attacks remain a widespread phenomenon due to their versatility. They can act as a full-fledged attack aimed at disrupting access to services or sites, or they can be part of a deeper attack aimed, for example, at data theft.Tools to protect against such attacks have been around for a long time and are well established. There are both comprehensive solutions and specialized ones that specifically address the problem of frequent DDoS attacks.
At the same time, Russian businesses should quickly become familiar with this class of security solutions, since a significant decline in DDOS attacks is unlikely to be expected in the foreseeable future.

