Carding
Professional
- Messages
- 2,870
- Reaction score
- 2,493
- Points
- 113
This guide will help you to find the best Bitcoin wallet or cryptocurrency wallet for YOU!
Hint:
There's no "one size fits all" wallet. Wallets come on different platforms with different features.
If you want the best possible wallet, keep reading...
Chapters
CHAPTER 1 What is a Wallet?
CHAPTER 2 Wallet Types
CHAPTER 3 Hardware Wallets
CHAPTER 4 Hot Wallets
CHAPTER 5 Banks vs. Wallets
CHAPTER 6 Theft and Scams
Our Top Picks
Best Wallet For
Best for Security Ledger Nano X
Secure storage for any cryptocurrency
The Ledger Nano X is the newest crypto hardware wallet, and is very easy to use. It connects to iOS, Android & desktop computers.
Best for Mobile ZenGo
Easy to use iOS & Android wallet
ZenGo is an easy-to-use iOS and Android Bitcoin & crypto wallet. Start within 20 seconds.
Best for Desktop Electrum
Simple yet powerful desktop wallet
Electrum is a Bitcoin-only wallet that has been around since 2011. It's easy to use, but has advanced features.
Chapter 1
What is a Bitcoin & Cryptocurrency Wallet?
A Bitcoin/cryptocurrency wallet is the first step to using Bitcoin or crypto.
Why?
A “wallet” is basically the equivalent of a bank account. It allows you to receive bitcoins and other coins, store them, and then send them to others.
You can think of a wallet as your personal interface to the Bitcoin network, similar to how your online bank account is an interface to the regular monetary system.
Wallets contain private keys; secret codes that allow you to spend your coins.
In reality, it’s not coins that need to be stored and secured, but the private keys that give you access to them.
In short:
A crypto or Bitcoin wallet is simply an app, website, or device that manages private keys for you.

Ledger Live makes it easy to send and receive Bitcoins to your Ledger Nano X
This guide will show you how to create a wallet and pick the best one.
Types of Bitcoin Wallets
There are a few different types of Bitcoin wallets used today, and each of them come with their own tradeoffs between security and convenience:
We'll cover this in full detail in chapter two (up next), but put simply there are wallets for holding your everyday spending money (hot wallets) and there are wallets for your long term savings (cold wallets). There are even several types of both hot and cold wallets.
An Exchange is Not a Wallet
Again, we will cover this is more detail in Chapter five below, but its worth stating here as well that your Bitcoin "bank" or exchange accounts that do hold Bitcoin are NOT wallets.
Coinbase app does not let you hold you own keys, therefore it is not a wallet.
If that is confusing, don't worry - it will all make sense by the time we are done here.
This is not to say that bitcoin banks are inherently bad.
It is simply important to remember that whoever controls the private keys controls the bitcoin attached to those keys. A misunderstanding of this point has led to hundreds of millions of US dollars being lost in the past, so it’s important to understand this key difference in how Bitcoin private keys can be stored.
For now, just know that private keys are what you need to protect if you want to keep your bitcoin safe from hackers, user error, and other possible issues.
Chapter 2
Types of Bitcoin & Crypto Wallets
Now let's discuss the types of wallets and why you might want to use one kind over another.
By the end of this chapter, you should have a good idea of which wallet is right for you.
Hardware Wallets
The Ledger Nano S is one example of a hardware wallet.
A hardware wallet is a physical electronic device, built for the sole purpose of securing crypto coins.
The core innovation is that the hardware wallet must be connected to your computer, phone, or tablet before coins may be spent.
The two most popular and best Bitcoin and cryptocurrency hardware wallets are:
- Ledger Nano X
- TREZOR T
Hardware wallets are a good choice if you’re serious about security and convenient, reliable Bitcoin & crypto storage.
Hardware wallets keep private keys separate from vulnerable, internet-connected devices.
Your all-important private keys are maintained in a secure offline environment on the hardware wallet, fully protected even should the device be plugged into a malware-infected computer.
Malware should be no match for your hardware wallet.
As bitcoins and cryptocurrencies are digital, cyber-criminals could, potentially, target your computer’s “software wallet” and steal them by accessing your private key.
Generating and storing private keys offline using a hardware wallet ensures that hackers have no way to reach your coins.
Hackers would have to steal the hardware wallet itself, but even then, it can be protected with a PIN code.
Don’t worry about your hardware wallet getting stolen, lost or damaged either; so long as you create a secret backup code, you can always retrieve your coins.
Think of a hardware wallet like your own underground steel vault. If you own a significant amount of bitcoin or crypto, you should strongly consider getting one!
Why are hardware wallets good?
Easiest way to securely store bitcoins and other coins
Easy to backup and secure
Less margin for error; setup is easy even for less technical users
Multiple hardware wallets can be used together for extra security
Why are hardware wallets bad?
They're not free!
They can be challenging for new users to understand
Hot Wallets
Hot wallets are wallets that run on internet connected devices like a computer, mobile phone, or tablet.
Private keys are secret codes. Because hot wallets generate your private keys on an internet connected device, these private keys can’t be considered 100% secure.
Think of a hot wallet like your wallet today: you use it to store some cash, but not your life savings. Hot wallets are great if you make frequent payments, but not a good choice for the secure storage of bitcoins.
Why are hot wallets good?
Easiest way to store small amounts of bitcoin and crypto
Convenient; spending and receiving payments is easy and fast
Some hot wallets allow access to funds across multiple devices
Why are hot wallets bad?
Not safe for the secure storage of large amounts of bitcoins and crypto
You might forget about the application being installed on your phone
Which Wallet is Best for You?
Why are you using Bitcoin & Crypto?
Investing or saving? Then a hardware wallet will keep your coins safe.
Otherwise, a software wallet will send and receive bitcoins & crypto just fine. Best of all, software wallets are free.
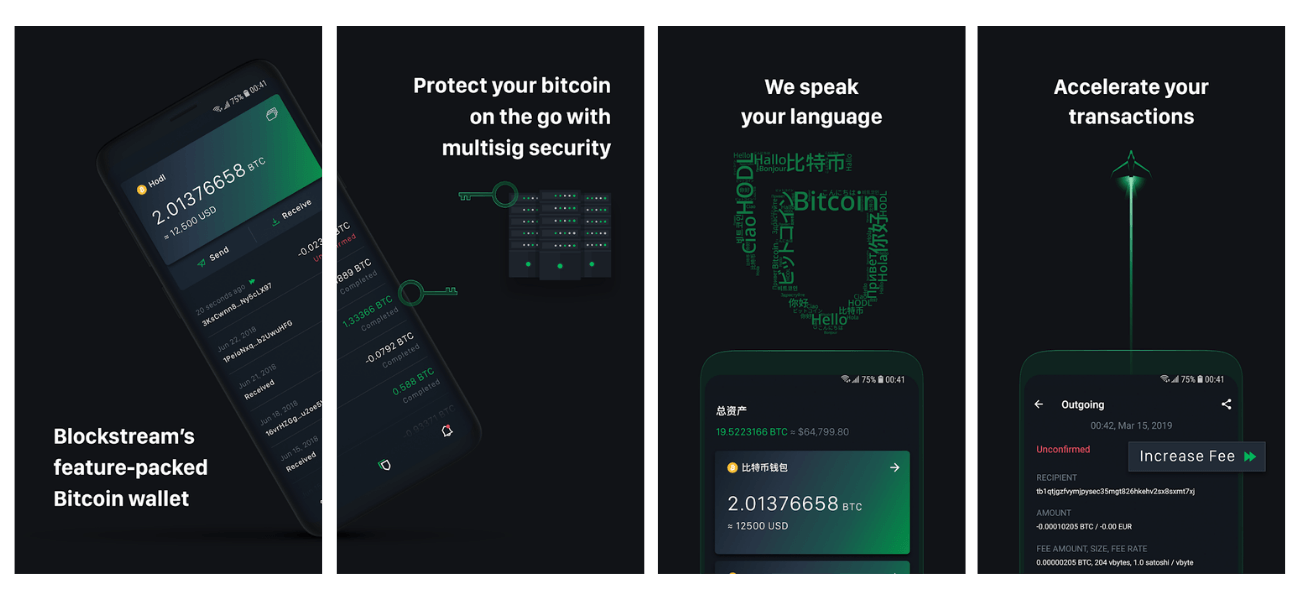
Blockstream Green is one of the most secure mobile wallets out there.
Each wallet has pros and cons, and different wallets are built to solve different problems.
Some wallets may be geared towards security, while some wallets may be more focused on ease-of-use.
Your specific needs should determine the wallet you use, as there is no “best bitcoin wallet”.
How to Add Funds to a Bitcoin Wallet
Most wallets don't give you the ability to buy and sell bitcoin. So, if you want funds in your wallet you'll need to purchase on an exchange and send the coins to your wallet.
We've listed some popular exchanges below:
Popular Exchanges
Coinmama
Works in almost all countries
Highest limits for buying bitcoins with a credit card
Reliable and trusted broker
eToro
Supports Bitcoin, Ethereum & 15 other coins
Start trading fast; high limits
Your capital is at risk.
This ad promotes virtual cryptocurrency investing within the EU (by eToro Europe Ltd. and eToro UK Ltd.) & USA (by eToro USA LLC); which is highly volatile, unregulated in most EU countries, no EU protections & not supervised by the EU regulatory framework. Investments are subject to market risk, including the loss of principal.
Below, we've listed wallets you can buy or download. We suggest using the wallets listed or doing research before buying or downloading any wallet.
Each day, new Bitcoin scam wallets are added to the Google Play Store and Apple app store that are designed to steal peoples' bitcoins.
We only list wallets that have published and open-sourced their code.
Chapter 3
Hardware Wallets: Keep Your Coins Safe
Hardware wallets aren't free.
But the price can be worth it if you own a significant amount of coins.
A hardware wallet will protect a few hundred in bitcoin/crypto just as effectively as a few million.
The three most popular hardware wallets: KeepKey, Ledger Nano S, and Trezor.
How Hardware Wallets Work
Hardware wallets are secure, offline devices. They store your private keys offline so they can't be hacked.
This means you can even use one on a malware infected computer.
Why A Hardware Wallet with a Screen is Important
In the table below, you'll notice we show which hardware wallets have screens.
Screens provide extra security by verifying and displaying important wallet details. Since the hardware wallet is nearly impossible to hack, its screen is more trustworthy than data displayed on your computer.
Bitcoin & Crypto Hardware Wallet Comparison
Check the table below for a quick comparison. Note:
We also did a detailed comparison of the three main ones: Ledger Nano S, Trezor, and KeepKey.
COMPARISON
Ledger Nano X
RELEASED: 2019
PRICE: $119
Ledger Nano S
RELEASED: 2016
PRICE: $59
TREZOR T
RELEASED: 2018
PRICE: $159
TREZOR One
RELEASED: 2013
PRICE: $59
Best Bitcoin Hardware Wallet Overviews
Ledger Nano X
The Ledger Nano X is Ledger's newest hardware wallet. The main benefit is that it has bluetooth, making it the first hardware wallet that connects with iOS devices. It's more secure than using just an app on your phone, because all transactions are signed with the Nano X.
Ledger Nano S
The Ledger Nano S is the cheapest of the three hardware wallets with a screen; it costs about $59. Ledger, one of the most well-known Bitcoin security companies, released the device in August 2016.
TREZOR T
The TREZOR Model-T is a second generation Bitcoin/crypto hardware wallet manufactured by SatoshiLabs. The TREZOR line debuted in 2014 with the TREZOR One and has remained one of the most popular cryptocurrency cold storage solutions to date.
TREZOR One
TREZOR launched in August 2014 as the first Bitcoin hardware wallet, offering secure bitcoin storage plus the ability to spend with the convenience of a hot wallet. TREZOR is a small, thumb-sized device.
Chapter 4
Hot Wallets
Best hot wallet
Just a quick refresher:
Hot wallets are Bitcoin wallets that run on internet connected devices like a computer, mobile phone, or tablet.
As hot wallets generate private keys on an internet connected device, these private keys can’t be considered 100% secure.
Think of a hot wallet like your wallet today: you use it to store some cash, but not your life savings. Hot wallets are great if you make frequent payments, but not a good choice for the secure storage of bitcoins.
Desktop wallets are downloaded and installed on your computer. If privacy is your main concern, the Bitcoin core wallet is a good option since it does not rely on third parties for data.
Electrum
Electrum is a light weight Bitcoin wallet for Mac, Linux, and Windows. Electrum was created in November 2011. The main features of Electrum are: support for hardware wallets (such as TREZOR, Ledger Nano and KeepKey), and secure Bitcoin storage using an offline computer. Electrum is a good option for both beginners and advanced users.
Blockstream Green
Blockstream Green is a powerful Bitcoin wallet for iOS, Android, and Desktop. It's very easy to use and can be setup in a few minutes.
iOS and iPhone Bitcoin Wallets
Apple banned Bitcoin wallets from the App Store in February 2014, but reversed its decision a few months later. Luckily, there are now plenty of options for iOS users.
BRD
We consider BRD, along with Copay (below), as the best bitcoin wallet for iPhone. It’s open source and gives the user full control over their private keys. It also has a clean interface which makes the sending and receiving of bitcoins a pleasurable and super-simple process.
Edge
Edge is an easy to use Bitcoin wallet for iPhone and Android. Its familiar login feature makes using the app a breeze for people new to bitcoin. The wallet also creates automatic backups, so you don't have to worry about the technicalities of performing manual wallet backups.
Blockstream Green
Blockstream Green is a powerful Bitcoin wallet for iOS, Android, and Desktop. It's very easy to use and can be setup in a few minutes.
Aqua
Aqua is a new non-custodial, singlesig wallet made by Blockstream as a way to offer a more newb friendly wallet than Blockstream Green. It's incredibly simple to use and supports liquid assets as well.
Android Bitcoin Wallets
There is a large selection of Android wallets. Since Bitcoin wallets were originally banned by Apple, developers spent much of their time developing for Android.
BRD
BRD, the great iPhone Bitcoin wallet, recently released an Android wallet. It offers the user control of private keys, an easy to use interface, and passcode support.
Edge
Edge is an easy to use Bitcoin wallet for iPhone and Android. Its familiar login feature makes using the app a breeze for people new to bitcoin. The wallet also creates automatic backups, so you don't have to worry about the technicalities of performing manual wallet backups.
Blockstream Green
Blockstream Green is a powerful Bitcoin wallet for iOS, Android, and Desktop. It's very easy to use and can be setup in a few minutes.
Bitcoin Wallet
Bitcoin Wallet, or “Schildbach Wallet”, was the first mobile Bitcoin wallet. Bitcoin Wallet is more secure than most mobile Bitcoin wallets, because it connects directly to the Bitcoin network. Bitcoin Wallet has a simple interface and just the right amount of features, making it a great wallet and a great educational tool for Bitcoin beginners.
Chapter 5
Bitcoin Banks: $10 Billion Lost in Hacks
Bitcoin Banks
One last thing to keep in mind when it comes to bitcoin wallets is that there is a difference between a wallet and a bank.
Some Bitcoin users view Coinbase as a Bitcoin wallet, but companies like this operate much more like banks.
Remember:
The private keys are what users need to protect to safely use the Bitcoin network without getting robbed. When you hand someone else control over your private keys, you are essentially making a deposit at that financial institution – much like a deposit at any bank.
Don't store coins on exchanges! Bitcoin users have lost over $10 billion worth of bitcoins in exchange hacks and scams. Control your own private keys.
This is not to say that bitcoin banks are inherently bad. Companies like Coinbase have done wonders for bringing more users into the ecosystem. It is simply important to remember that whoever controls the private keys controls the bitcoin attached to those keys.

The Mt. Gox exchange was subject to the largest exchange hack in history, losing 850,000 Bitcoins.
A misunderstanding of this point has led to billions of US dollars being lost in the past, so it’s important to understand this critical difference in how Bitcoin private keys can be stored.
Understanding how bitcoin wallets work is an important aspect of safely using this new technology. Bitcoin is still in its early years of development and wallets will become much more user-friendly in time.
In the near future, certain devices may eventually come with pre-installed wallets that interact with the blockchain without the user’s knowledge.
For now, it’s vital to keep in mind that the private keys are what you need to protect if you want to keep your bitcoin safe from hackers, user error, and other possible issues.
Chapter 6
Theft and Scams
Bitcoin theft
No matter which wallet you choose, remember:
Our bitcoins are only safe if the private key was generated securely, remains a secret, and--most importantly--is controlled only by YOU!
Let's learn about what happens when this isn't the case.
Here are two examples where users got ripped off by leaving bitcoins in the care of a third party:
The Bitfinex hack, in which users lost $70 million
The failure of Mt Gox, in which users lost $450 million or more
To avoid theft, scams, and any other loss of funds, follow these three basic principles:
Generate your private keys in a secure, offline environment. (Except if using trivial amounts, in which cases keys may be created in a hot wallet).
Create backups of your private keys. This helps to protect against the loss of your bitcoins due to hard drive failure or some other problem or accident. Ideally you should have a duplicate set of backups kept off-site to protect against the possibility of fire, robbery, etc.
Encrypt wallets to provide additional security. This helps prevent the physical theft of your funds in the event that your device or hardware wallet is stolen.
Securing your bitcoins properly is the most important step for any Bitcoin user.
With Bitcoin you have the privilege - but also the responsibility - to safeguard your own money. There have been countless scams related to Bitcoin that could have been prevented had people not entrusted others with their bitcoins.
It’s a good rule of thumb to never trust anyone else with your money.
Ledger Nano X
Ledger Nano S
TREZOR T
TREZOR One
Bonus Chapter 1
Cryptocurrency Security Advice
Whether your on an exchange or using a wallet, this section will give you some tips on how to secure your cryptocurrency in ways you may not have seen before.
From changing your mobile network to encrypting your internet connection - these tips are actionable and easy to implement quickly.
The migration of value into the digital realm brings with it new challenges in terms of best security practices. As with any unit of value, there is always someone, somewhere that seeks to extract this value for their own ends, whether it be through coercion, social manipulation or brute force.
This guide is intended to provide a broad overview of the best practices for securing your crypto assets. While most of these steps are not mandatory, following them will greatly increase your financial security and peace of mind in the crypto world.
Passwords — Complexity & Re-Use
Starting from the ground up, password complexity and re-use are two major pain points that many average users do not consider adequately. As you can see by this list, average password complexity still leaves a lot to be desired. The less complex your password is, the more susceptible to hack your account is. If you use the same passwords, or even slight variations of the same passwords across multiple accounts, your chances of compromise are greatly increased.
So what can you do? Fortunately the fix for this is relatively easy. Use randomly generated 14 character+ passwords and never re-use the same password. If this seems daunting to you, consider leveraging a password manager such as LastPass or Dashlane that will assist in password generation and storage.
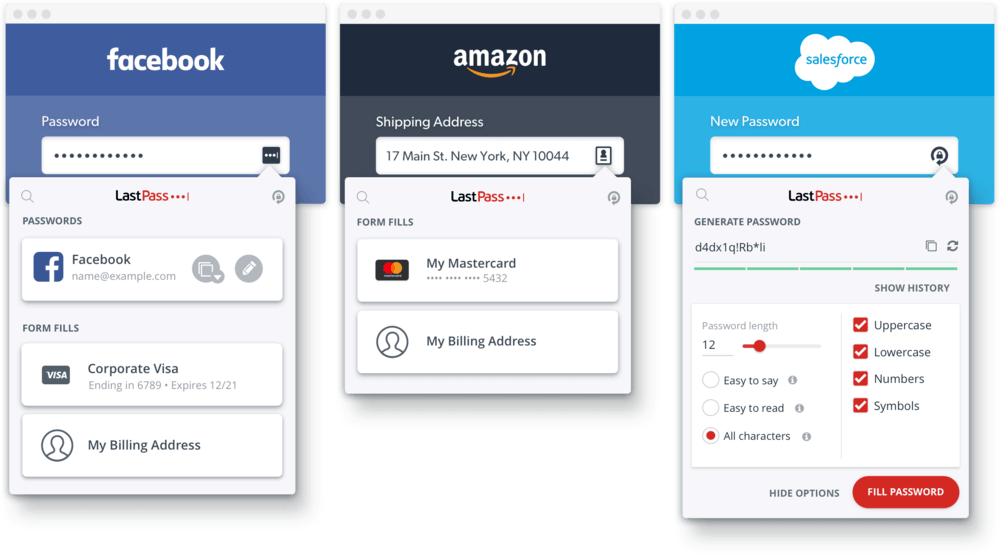
Lastpass is a our favorite password generator and manager.
You can find out if any accounts associated with you have ever been compromised here as well as using this tool https://howsecureismypassword.net to test just how strong variations of your passwords may be (*do not use your real password on here, only similarly structured variations).
Dedicated Email Accounts
Almost every online service/exchange requires some type of email account association during the activation process. If you are like most people, you will probably use your default email that you’ve had for years, and perhaps add a bit more complex password for the account itself for good measure.
In most cases however, all a hacker needs is access to your emails in order to reset account passwords that may be tied to it. It’s as simple as navigating to the website/exchange and clicking the ‘forgot password’ link to begin the process. So, if you are like most people and have an email address that has been active for years, with a weak login password, your chances of being hacked are much higher.
For the above reasons, do yourself a favor and create a new/dedicated email address for use with your crypto accounts. Services like ProtonMail and Tutanota are free and offer end to end encryption without sacrificing usability (mobile app availability etc.). If you decide to PayPal with Gmail, consider activating the Advanced Protection Program that Google offers.
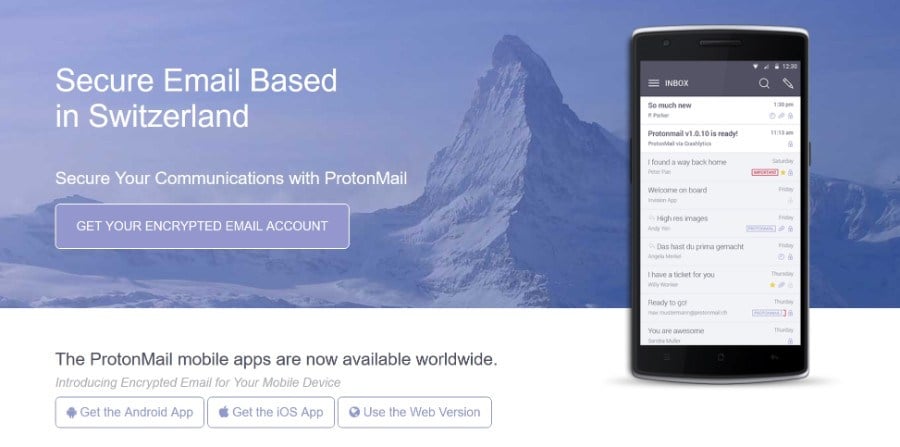
Proton Mail offers email with end-to-end encryption.
Usa a VPN
A virtual private network (or VPN) is simply a must for everyone today, but especially cryptocurrency users.
Why?
As we surf the internet, there are unfrotuantely a lot of eyes on us at all times. One very big set of eyes watching us is our internet service provider (or 'ISP'). They see and hear everything we do on the internet. And they often share that information with third parties. But our ISP and its friends are not the only people watching. Anyone using the same wifi network that we are using can also see what we are up to online.
A VPN solves this problem. When we use a VPN, our computer's IP address is not connecting to any website directly. Instead we are communicating to another IP address over an encrypted connection. Then that IP address makes website requests on our behalf and send us back that data. This helps keep onlookers onto our connection locked out so that only one party knows what we are doing (the VPN).

It's therefore important that you choose a vpn service with a great track record.
The reason VPNs are important for cryptocurrency users especially is that we use Bitcoin to keep as much data hidden as possible. However, when we expose our IP address, we might give away that our IP address is connected to someone who owns and uses cryptocurrency, merely because of the websites we visit.
Long story short: everyone should be using a VPN regardless of whethor or not they use Bitcoin. It's for your own safety.
VPN
NordVPN
Special support for Malaysia, Nigeria, Singapore, South Africa
SEPA & credit card supported
Trusted exchange
Surfshark
Users claim fast speed from wide range of servers all around the world
Compatible with nearly any OS
ExpressVPN
Allows for Netflix
Users claim fast speed
Has apps for nearly any platform
Two-Factor Authentication
We typically recommend setting up two-factor authentication (2FA) for any and every account that offers it, even if the service is not crypto related. All 2FA does is require a second means of confirmation that you are who you say you are when logging into accounts. Most typically this is in the form of something you know (password) and something you own (SMS code sent to phone).
While SMS is still the most common form of 2FA offered by online services, it is unfortunately the least secure. The following general use 2FA methods are ranked from most secure to least:
FIDO U2F — This is a physical device that plugs into a USB port and requires a physical button touch to generate a unique 2FA access code. It is preferable because a hacker would need to have the device in their physical possession in order to access your account. Most hacks occur remotely which makes this our top 2FA choice (albeit not a panacea).

Yubikey is the most popular hardware second factor
Google Authenticator — An app that resides on your mobile device and cycles through one-time use access tokens. If you go this route, be sure to save your backup code that is provided at initial setup. If you don’t have this and your phone is lost or broken then you have no way to get these code settings back. While not as good as a yubikey, it's still better than SMS two factor.
Authy — Similar to Google Authenticator but potentially less secure as you can re-access the codes from an alternate mobile device if your main one is lost or broken (this feature can be disabled but is active by default). While this may seem more ideal, what is more convenient for you is also more convenient for those who may be trying to hack you.
SMS — Codes send to your cell phone through text message. Better than no 2FA at all, but susceptible to social engineering SIM attacks. Interestingly, SMS 2FA security holes did not come to light until the popularity of Bitcoin began to grow.
Google Fi
Speaking of SIM attacks, there is one way to avoid them.
Services like Google Fi offer an alternative to traditional mobile phone contracts that are not only more flexible but also more secure.
With Google Fi, you can prevent any changes from occuring on your account without providing a second authentication factor. And because there are no SIM cards in a Google Fi plan, there are also no SIM attacks. This makes it impossible for attackers to hijack your text-messages and take over your accounts.
Currently, Google Fi is the only mobile phone service in the US that offers 2FA. So if you intend on taking your security serously in this area, Google Fi is the only way to do it if you live in the United States.

Google Fi features
Another nice perk of Google Fi is that its easy to change your phone number whenever you want. This feature alone also increases your security since many of our phone numbers have been leaked before and can be used to access other accounts online. If your leaked phone number is no longer active, you are a little more protected.
Mobile Crypto Wallets
Mobile app wallets such as Mycelium, BRD, Samourai, Cryptonator, etc. should be treated similarly to how you may treat your physical wallet/purse.
Samourai's homepage
You only carry small amounts of discretionary spending funds in these wallets as they are more susceptible to loss or theft. Again, what is more convenient for you is more convenient for a malicious actor as well. Your phone is also susceptible to malware and should not be considered sufficiently safe for storing large amounts of funds.
Phishing Attacks
If you have crypto then you are an ideal target for phishing scams. Facebook and Twitter are just two of many avenues that hackers scour for potential victims. It has become common to see fake crypto exchange emails or ICO fundraising confirmations circulating such as the example below.
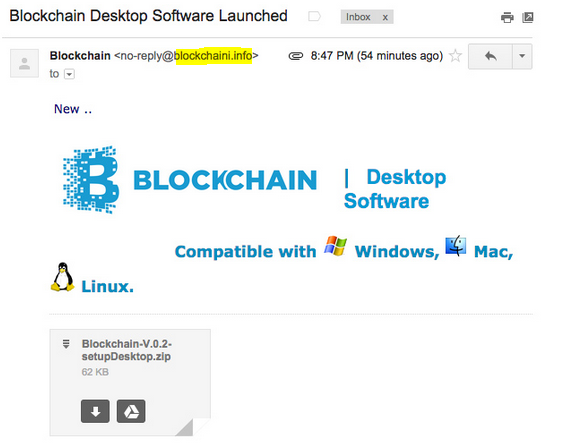
Phishing email impersonating Blockchain.info. Note send address & logo irregularity.
It is best to NEVER open suspicious attachments or provide credentials through email and to always closely inspect the logo, wording and send address of any emails received that pertain to financial accounts or that request sensitive information.
When in doubt, navigate to the legitimate exchange or web service that the email supposedly originated from and contact their support team to inquire on the validity of what you received before taking further action.
Clean Hardware
This brings us to the general best practices portion of this guide. Malware is everywhere on the internet and regardless of your attention to detail, sooner or later you are likely to fall victim to some type of malicious software. As such, it is best to have active antivirus subscriptions on your devices and to run periodic scans. I personally like to run Malwarebytes and Roguekiller on my PC once each week and have background scans on my phone that run each automatically.
Malwarebytes' homepage
Generally speaking Windows is the least secure OS, primarily due to the fact that it is the oldest and most pervasive OS in use today. Many security conscious techies tend to prefer Linux or iOS for this reason.
Secure Crypto Storage
If you don’t hold the private keys, you don’t own your money!
This category is how most people have been compromised and lost money in crypto. How? Primarily, by treating an exchange (Coinbase, Binance, Bittrex, Poloniex etc.) as a wallet to store their crypto assets in.
Mt. Gox, Bitfinex, BitGrail and Coincheck are just four out of a handful of crypto exchanges that have been hacked in the past 5 years, with the cumulative amount stolen exceeding $1 billion USD. While some users of these exchanges have been ameliorated to an extent, many are still suffering from the partial or even total loss of crypto funds that they held on these exchanges at the time of the hacks.
Our advice is to hold crypto on hardware and back it up using a steel wallet.
The Billfodl is a steel wallet that backs up your recovery phrase, protecting it from fire and flood.
If you wish to trade on exchanges, only do so with funds that you are potentially willing to forfeit entirely should either the exchange or your individual account become compromised.
A few of our recommended hardware wallet manufacturers are Ledger and trezor. You can find our more detailed wallet reviews here . As with all hardware/software, please ensure that your device firmware is kept up to date, as patches are pushed out continuously to address security concerns.
The Subject of Secure storage is something we cover in much greater depth in the next Bonus Chapter
Summary
Security on the web is akin to game of whack-a-mole and your level of security will likely scale accordingly with the amount of sensitive data (or crypto assets) that you are protecting.
While there is no such thing as an ‘unhackable’ system, there are valuable steps that you can take to drastically reduce your likelihood of compromise.
Always remember to:
Use complex and unique passwords
Create a separate/dedicated email account for crypto services
Use two-factor authentication
Store most (if not all) of your funds on hardware wallets
Be wary of phishing emails
Good luck and stay safe!
Bonus Chapter 2
Bitcoin Cold Storage
Cold storage
Unlike paper money, there more than a few options available for keeping your bitcoin secure.
Whether you're trading cryptocurrencies on a daily basis or you're a long-term bitcoin investor, cold storage can be a useful tool for keeping your crypto safe.
Understanding the Basics of the Bitcoin Wallet
In order to get a handle on what cold storage actually is, it's important to review the fundamentals of the "bitcoin wallet." In the same way that you can use a traditional wallet to store your paper currency, you can use a bitcoin wallet to store your bitcoin in digital form.
In other words, you can think of your bitcoin wallet as your personal bitcoin mailing address.
This might sound like having a bank account, but it's actually quite different.
Instead of needing to trust a third party to keep your cryptocurrency secure, you can use a bitcoin wallet as your sole gateway to the decentralized network. There's no need to ask a branch manager for permissions when you want to transfer bitcoin, there aren't any annoying forms to fill out, and transfers happen within minutes.
Bitcoin wallets can be used to:
Pay for items with bitcoin by transferring your payment to merchants who accept cryptocurrency.
Receive bitcoin deposits from customers, friends, or relatives.
Maintain your financial privacy by making anonymous purchases.
What is Bitcoin cold storage?
As you can see, bitcoin wallets are incredibly useful. All of this begs the question, however, of how many different types of bitcoin wallets there actually are.
Generally speaking, Bitcoin wallets come in two main types:
Hot wallets
The phrase "hot wallet" refers to any bitcoin wallet that requires the internet to function properly. Hot wallets derive their name from the fact that they need electricity to work. If the power goes out, then so does your hot wallet.
For example the popular mobile wallet BRD is an example of a hot wallet.

BRD is a widely used mobile "hot" wallet
Cold wallets
Not only do cold wallets work without an active internet connection, but many cold wallets don't even need a computer. Cold wallets have several similarities to traditional physical wallets, but they also have a few differences.
For example, the Ledger Nano X and Nano S are the most popular cold wallets on the market.

titans of the hardware wallet field
Is "Cold Storage" Different Than Using A Cold Wallet?
In general, "cold storage" refers to any bitcoin storage device that does not require electricity. A cold storage device can be a physical box, a piece of paper, or a list of numbers and letters that you keep in your head.
"Hot storage," as you may have guessed, is simply the analogous generalization for storage devices that require an internet connection.
Thus, hot wallets are an example of hot storage devices, and cold wallets are an example of cold storage devices.
The Major Differences Between Cold Storage And Hot Storage
hot vs cold storage
In contrast to hot storage, cold storage provides:
Increased security protections
A reliable way to keep your bitcoin offline
An easy way to transport your bitcoin between your various wallets
What are the different types of bitcoin cold storage wallets?
When it comes to choosing a cold storage wallet that can help keep your bitcoin secure, the most popular choices tend to be:
Hardware wallets
Hardware wallets include USB PayPals and other digital storage devices that you can use offline. Typically the private key to coins is never exposed to the internet because the device itself is air gapped.
COMPARISON
Ledger Nano X
RELEASED: 2019
PRICE: $119
Ledger Nano S
RELEASED: 2016
PRICE: $59
TREZOR T
RELEASED: 2018
PRICE: $159
TREZOR One
SCREEN:
RELEASED: 2013
PRICE: $59
Steel Backups
The steel wallet is literally a piece of indestructible stainless steel that you can use to carry your bitcoin private keys or backups in. This makes it an excellent choice if you're concerned about losing paper or live in an area with lots of flooding, fires or earthquakes.
You can checkout how they work in the video below: https://www.youtube.com/watch?v=BuynQ7aIW0c
Steel wallets are interesting because they can act as both a "paper wallet" or as a backup for any kind of Bitcoin wallet in case yours is lost, stolen, or destroyed. Almost any cryto holder can benefit from one of these steel wallets regardless of how they choose to Store their coins.
STEEL WALLETS
Billfodl
Highest grade steel wallet
125% money back guarantee
Lots of accessories to up your security
Free shipping if you spend $75 or more
Cryptosteel
First steel wallet
Multiple types of steel wallets available
Free shipping on orders of $150 or more
Cryptotag
Made from titanium
Must manually stamp in letters
Paper wallets
If you're concerned about malicious computer hackers getting access to your wallet, then a paper wallet is one of your best options.

A very common Bitcoin paper wallet
WARNING
Setting up a paper wallet is for HIGHLY advanced users only. There are many ways to get a paper wallet wrong - all of which can result in a total loss of funds. Proceed at your own risk.
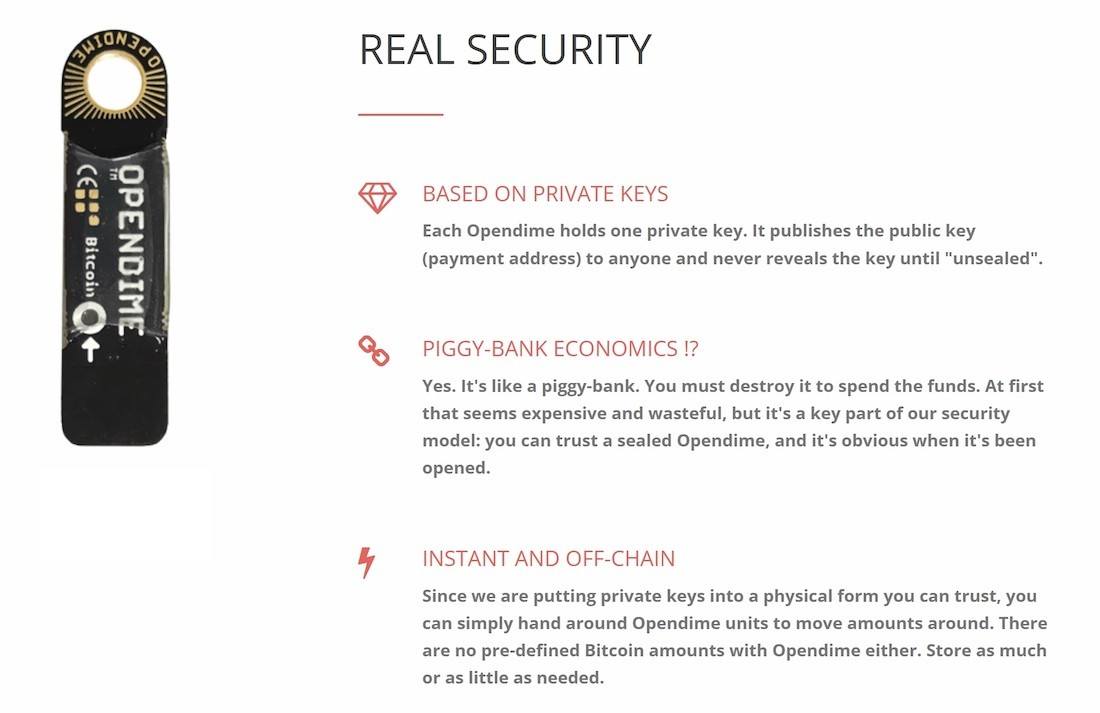
OpenDime
As the world's first bitcoin credit PayPal, the OpenDime device lets you spend your bitcoin balance in the same way that you would use a traditional credit card.
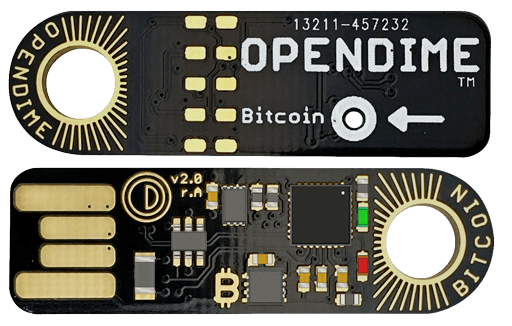
An OpenDime - front and back
The open dime is very much like a Bitcoin piggy bank. You can add as much bitcoin to it as you want and as many times as you want, however you can only spend from it once. At that point, the private key is exposed and the funds are no longer safe on the hardware. Because of this, its best to send all the coins to a new address once you are ready to use them.
For a great review and walkthrough on how the open dimes are used, watch this video: https://www.youtube.com/watch?v=1eJp99yAf_M
Comparing The Most Popular Cold Storage Wallets
So now you know of all the different options when it comes to choosing between cold storage wallets. Let's compare them all to each other to see which one would be best for you.
Paper Wallets Vs. Hardware Wallets
Technically speaking, hardare wallets fall somewhere in between a traditional hot wallet and a pure cold storage device.
With hardware wallets, the private key is stored digitally on a microchip, like a hot wallet. But that chip is never exposed to an internet connection.

Nano X Construction and Anatomy
Hardware wallets can be a bit easier to carry around and make transacitons with, but they are also subject to data degradation risks. This is why many users pair them with a steel wallet as a backup.
Paper Wallets Vs. Steel Wallets

Billfodl protects your coins from fires, floods, and even atomic blasts
When it comes to state-of-the-art bitcoin cold storage, steel backups are definitely ahead of the curve. Steel wallets provide the convenience of the paper wallet with the portability of the hardware wallet, but they also come with some added security features that make them worth looking into.
Steel wallets have two primary uses:
They can be used to backup any kind of hardware or software wallet. Typically these wallets spit out a 12 to 24 word phrase you can use to get your coins back if your main wallet is lost, stolen, or destroyed.
They can be used as a more sturdy version of a paper wallet. After you have generated your paper wallet, you can recreate the private key in the steel wallet using the provided tiles. Afterward you can keep the paper Wallet with the steel wallet and if there is ever a fire or a flood, you have a copy of the paper wallet that will survive.
In the video below, you can see Billfodl (the most popular steel wallet) get put through several tests. It even survivied an explosion using 600 gallons of jet fuel https://www.youtube.com/watch?v=bm-pm_ERYIA
Paper wallets and steel wallets are both protected from hardware data degredation, however the ink on the paper can disintegrate or run if it gets wet or too hot. Steel wallets are also protected from this risk.
Paper Wallets Vs. OpenDime
The OpenDime is basically a cross between a hardware wallet and a steel wallet. If you're partial to the idea of carrying a paper bitcoin wallet, then OpenDime can be another viable option. Like hardware wallets, open dimes are subject to data degredation over time.
On the other hand, paper wallets use regular paper to reduce the chance of your coins being hacked. Paper wallets keep your public and private keys on a plain sheet of paper, but they can also be modified to include a QR code to transfer data back and forth between your other cold storage devices.
Closing Thoughts
In summary, bitcoin cold storage is an effective way to keep your cryptocurrency from falling into their wrong hands. Even though it can be easy to end up feeling overwhelmed when you consider all of the cold storage options available, there's no reason to limit yourself to just one wallet type.
One of bitcoin's best features is that it's easily divisible, so you can allocate a portion of your holdings to several different cold storage devices at once.
Most cryptocurrency users keep some bitcoin in cold storage and some in a hot wallet to have some funds that are ready to use.
Whichever way you choose to allocate your bitcoin, make sure to keep security at the forefront of your plan.
Bonus Chapter 3
How to Make a Paper Wallet
Cold storage
Ever been curious about how to make a paper wallet?
Or does the thought of making one intimidate you?
Is it even safe to make one?
Let's find out in this detailed guide on how to create a Bitcoin paper wallet.
Creating a Paper Wallet - The Quick Way
1. Navigate to BitAddress.org. BitAddress is an open source program for creating Bitcoin paper wallets.
2. Move your mouse around the screen or enter random letters and numbers into the textbox to add randomness to the wallet creation.
This randomness is called entropy and will help ensure your keys are secure and resistant to brute force cracking.
3. Once you reach 100%, BitAddress will present you with a public key, a private key, and a QR code for each. To get a printable version, select Paper Wallet. You can create any number of wallets you like.

4. To add an extra layer of security by encrypting the private key, check the BIP38 box and enter a password. To conduct a transaction you will need the private key AND the password to the wallet from which you are sending funds. You can recognize a private key that has been encrypted by its first two characters, which will usually be 6P.
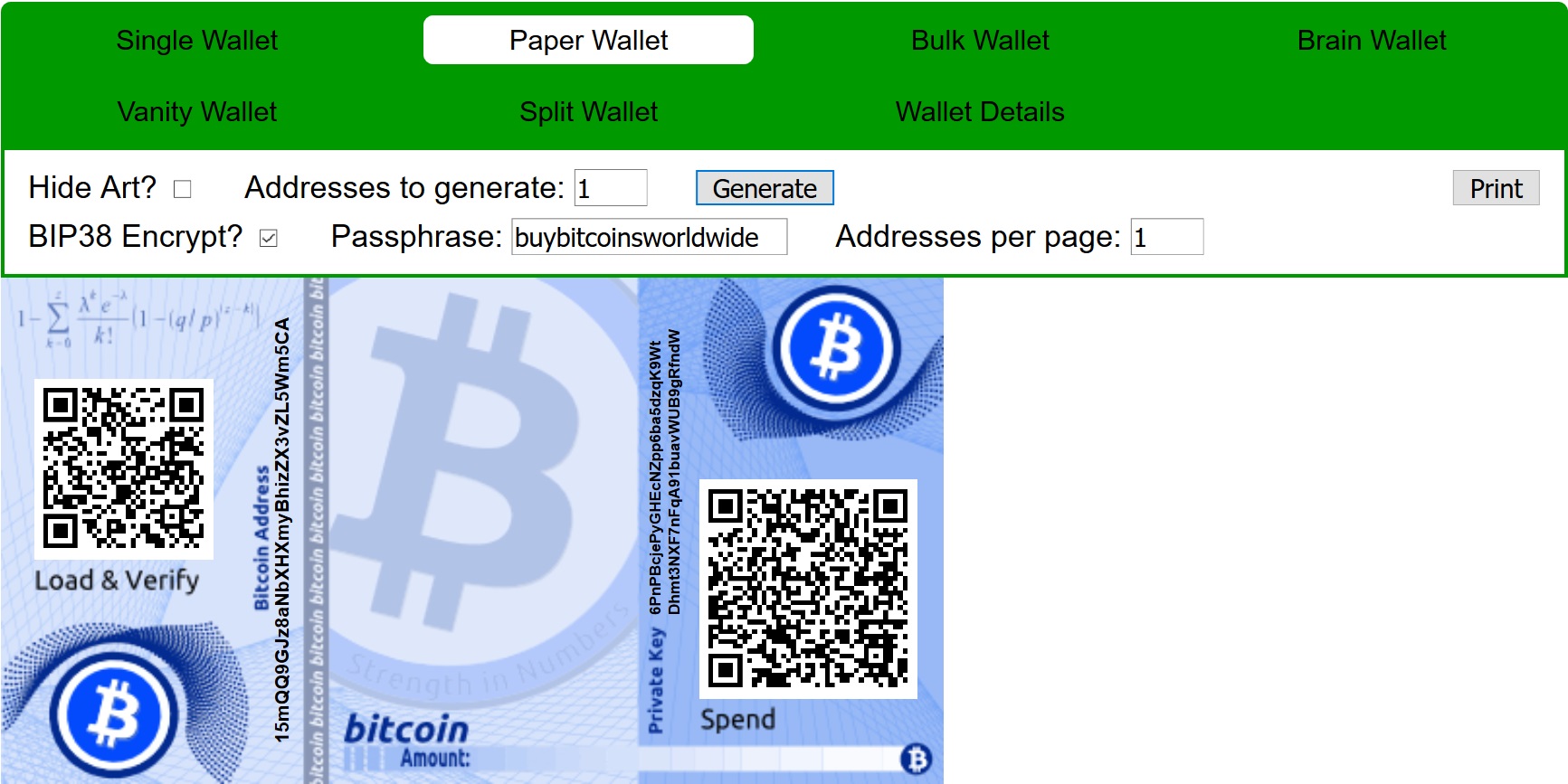
Print your wallet(s).

A BIP38 wallet encrypted with the password *buybitcoinsworldwide*.
That’s the quick and easy way to create paper wallets online using BitAddress. However, there are a number of security concerns to take into consideration:
Your computer could be infected with malware, which would allow an attacker to see your freshly generated private keys, giving them full access to any funds you then load onto the wallet.
The website itself could also be compromised. You are trusting BitAddress not to view and record the private keys that you generate.
Lastly, printers have their own memory where the file containing your private keys could be stored. For this reason, do not use a shared printer to print your paper wallet.
Creating a Paper Wallet - The Secure Way
To securely create a paper wallet we will follow the steps outlined above, but take a couple of additional measures to address the security flaws.
This video outlines goes through the process, and each step is listed below for you to follow along.
https://www.youtube.com/watch?v=VTsHeiBhPIM
1. Download the offline version of BitAddress from its GitHub repository https://github.com/pointbiz/bitaddress.org/archive/master.zip. Here you will find the paper wallet generator’s open source code. Save this to a USB drive.

2. Next, you’ll need a secure computer. Ideally this would be an airgapped computer that has never seen the internet and never will. Alternatively, booting off a live installer will avoid most security issues.
This guide https://ubuntu.com/tutorials/tutorial-create-a-usb-PayPal-on-windows#1-overview explains how to create a bootable USB drive off of which you can run Ubuntu, a popular Linux distribution. A Windows or Mac virtual machine will work in a pinch.

3. Extract the zip file on the USB and open the bitaddress.org HTML file. You’ll be taken to an offline version of the website.
4. Follow the same steps as detailed above, using your mouse and/or keyboard to create entropy, choosing the number of wallets you wish to create, and adding BIP38 encryption if desired.
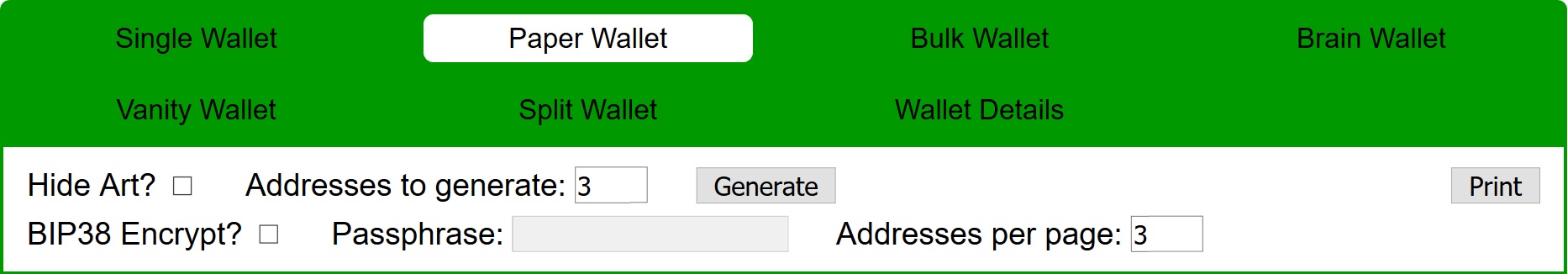
5. Connect to a printer with a wired connection, not Wi-Fi, and print your wallet(s). You could also avoid any potential issues with printer security by writing out your public and private keys.

That’s it, you have now generated one or many paper wallets that you can use for cold storage of Bitcoin. If you used a live OS to generate your keys, be sure to exit out of it and reboot so all traces are erased from the computer’s memory. If you used an airgapped computer, it’s best that it never be connected to the internet.
You can safely share your public key, also known as the wallet address, and use a blockchain explorer such as blockstream.info to check the wallet’s balance.
Spending Coins on a Paper Wallet
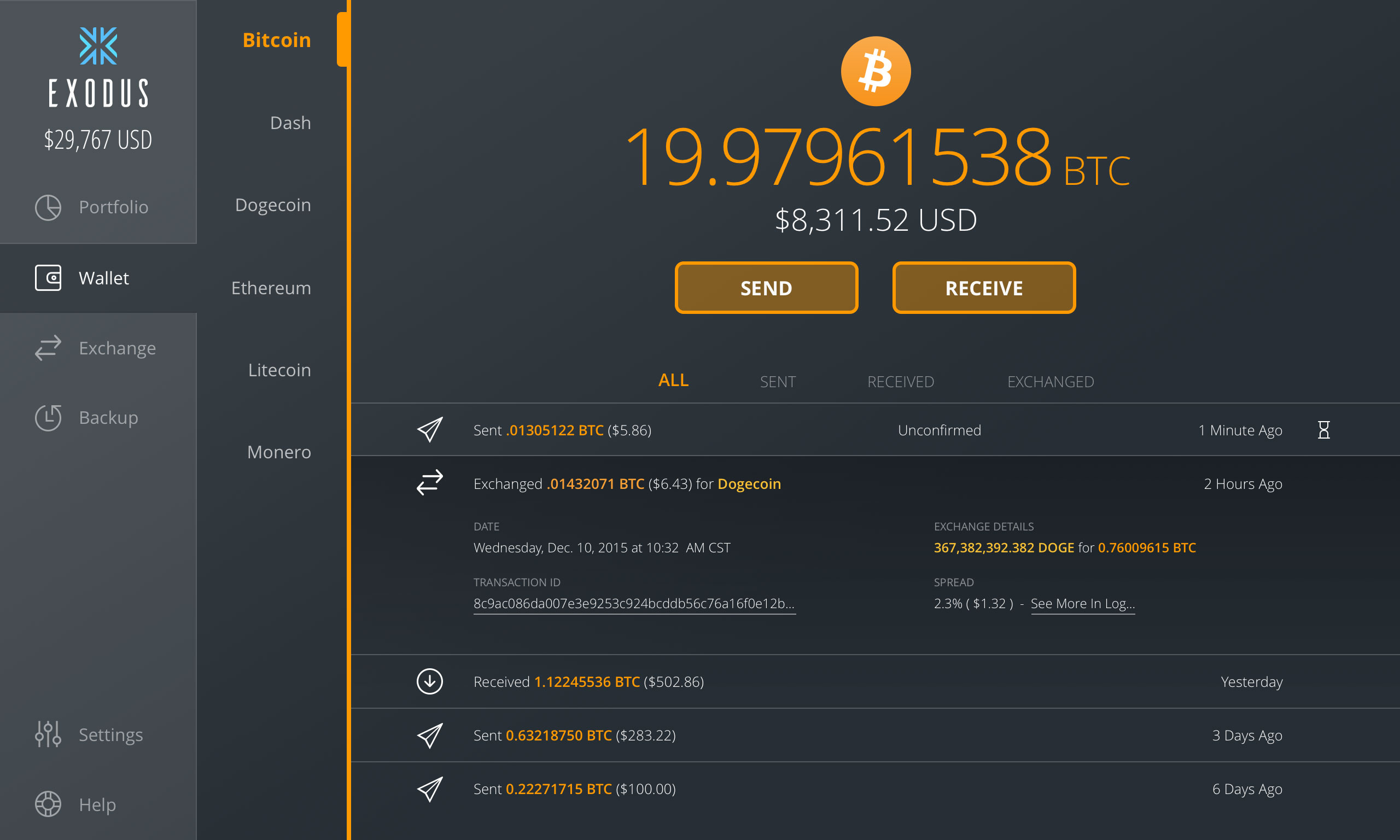
To send funds from your paper wallet, you will need to import or sweep your private key into a wallet client. Importing a private key simply adds it to the list of keys in your software wallet, preserving its unique address. This means that if someone got their hands on your paper wallet, they could still take control of the Bitcoin on it. Sweeping a private key transfers the funds associated with it to a new or existing address. This leaves the paper wallet empty.
You can import or sweep your private key into the software wallet by scanning the QR code with your webcam or typing out the private key.
WARNING
As mentioned above, both of these options run the risk of exposing your private key to any keylogger or malware, which is why you should never reuse paper wallets.
Once the Bitcoin is in your software wallet, you can send it as you would any other transaction.
QUICK TIP
If importing a private key, note that if *any* amount of Bitcoin is spent using the software wallet, the paper wallet will be *completely* emptied. The Bitcoin network spends the entire balance of a private key and sends any leftover amount – the change – to a newly-generated private key in the software wallet.
Bonus Chapter 4
Bitcoin Wallet Frequently Asked Questions
Many of you may still have lots of questions about wallets and how to keep your bitcoin secure.
We update the chapter below any time we get a new question from our readers, so odds are we have answered almost any question you could think of below.
What are Bitcoin Wallets?
Bitcoin Wallets let us send, receive and store Bitcoin.
Wallets secure funds by guarding our private keys. These private keys act as the proof of ownership for our Bitcoins. As such, a Bitcoin wallet is like a safety deposit box for Bitcoins.
What is a private key?
If a Bitcoin wallet is like a safety deposit box for our Bitcoins, then our private key is like the key to the safety deposit box. The only difference is that, in the real world, you could break open a safety deposit box without the key. However, in Bitcoin, there is no way to break open the wallet without the key. It is impossible.
Therefore, keeping your private key secret is the most important thing you must do to keep your Bitcoins secure.
What is a Bitcoin address?
A Bitcoin address is like an account number, just better. The address denotes which wallet the coins should be sent to. Like a bank account number, where the difference lies in the wallets having multiple addresses. These can be customized by including payment request information such as an amount and a date of expiration.
What are Steel Bitcoin wallets?
Steel wallets are made to store your backup seed. If you store your seed on paper, it could get burned in a fire or destroyed in a flood. Steel wallets protect against all of these threats by creating an indestructible backup for your seed.
How do I add coins to a Bitcoin Wallet?
First, acquire some Bitcoins. Go through an exchange in your country, ask an acquaintance to share, or use Buybitcoinworldwide.com if you want as seamless of an experience as possible. The purchased coins can then be sent to your wallet by specifying one of its addresses.
Some wallets, particularly online ones, also let you buy coins. Keep in mind that these come with larger exchange margins which are best left alone.
How do I open a Bitcoin account?
To some readers this might seem like a weird question. Truth is, people coming from a financial or business background are likely to expect Bitcoin to be a direct alternative to our current financial system. This is not the case.
You don’t need a Bitcoin account. There is no such thing really. You just need a wallet. The only accounts you might encounter are online wallets that are separated into various accounts via a user system.
Any common mistakes to be careful of?
First of all, don’t rest your money in an exchange wallet. Keep your coins in an environment where you have complete control.
Secondly, don’t keep all of your coins in one place. You’ll be crushed if you lose access to a wallet with all of your funds.
Thirdly, double check the target address. Bitcoin transactions cannot be reversed, so don’t lose your coins forever to a stranger!
How many backups of my seed should I create?
We recommend keeping at least two backups of your seed in multiple locations.
You can also laminate your seed to protect against water damage or any other damage.
Keeping your seeds in fire proof safes can help protect in the event that the storage location is burned down.
Another option is to put your seed into metal manually using stamps, or using Billfodl.
What happens if someone finds my 24 word seed?
Unless you’re using a 25th word, someone who finds your 24 word seed can sweep your entire wallet.
Should I take a picture of the seed with my phone as a backup?
NO, NO, and NO!
The seeds generated by hardware wallets are meant to be written down only. By taking a picture of your seed with an internet connected phone, you put your entire wallet on a device that is connected to the internet and easier for hackers to get into. Please do not do this!
Is it ok to buy hardware wallets on ebay or amazon?
We always recommend to order directly from a hardware manufacturer or authorized reseller. This is because someone can buy a hardware wallet, tamper with it, and sell it used. They could program it to steal any bitcoins or add a back door.
Most hardware wallets add some special kind of tape on the packaging to try to make any tampering more noticeable. This is another reason we recommend only ordering from the hardware wallet company or reseller, and not from a website like eBay.
What happens if the hardware wallet company goes out of business?
If Sony went out of business tomorrow, you would still be able to play your playstation with mostly no issues. Hardware wallets are the same. You do not need a company to remain in business in order to continue using your hardware wallet. You would, however, need to run your own node in order to send and receive transaction.
Let’s say you use TREZOR with TREZOR’s myTREZOR wallet. TREZOR goes out of business and no longer supports myTREZOR wallet and it gets shut down.
You could, in just a few minutes, download Electrum on your computer. Once installed, you’d setup your TREZOR and all of your transaction history and balance would get imported and be exactly the same. This is because Electrum will use the same 24-word seed you generated with TREZOR on setup.
Do these hardware wallets work for Ethereum?
Yes, all of these wallets work with Ethereum, Litecoin and many other coins.
Do these hardware wallets work with Coinbase?
One of the most frequent questions we get asked is how Coinbase works with hardware wallets.
It’s a trick question!
Coinbase does not work directly with hardware wallets. You should, however, send bitcoins from Coinbase directly to your hardware wallet once you buy. Never store bitcoins on Coinbase or any other exchange for long periods of time.
(c) https://www.buybitcoinworldwide.com/wallets/
Hint:
There's no "one size fits all" wallet. Wallets come on different platforms with different features.
If you want the best possible wallet, keep reading...
Chapters
CHAPTER 1 What is a Wallet?
CHAPTER 2 Wallet Types
CHAPTER 3 Hardware Wallets
CHAPTER 4 Hot Wallets
CHAPTER 5 Banks vs. Wallets
CHAPTER 6 Theft and Scams
Our Top Picks
Best Wallet For
Best for Security Ledger Nano X
Secure storage for any cryptocurrency
The Ledger Nano X is the newest crypto hardware wallet, and is very easy to use. It connects to iOS, Android & desktop computers.
Best for Mobile ZenGo
Easy to use iOS & Android wallet
ZenGo is an easy-to-use iOS and Android Bitcoin & crypto wallet. Start within 20 seconds.
Best for Desktop Electrum
Simple yet powerful desktop wallet
Electrum is a Bitcoin-only wallet that has been around since 2011. It's easy to use, but has advanced features.
Chapter 1
What is a Bitcoin & Cryptocurrency Wallet?
A Bitcoin/cryptocurrency wallet is the first step to using Bitcoin or crypto.
Why?
A “wallet” is basically the equivalent of a bank account. It allows you to receive bitcoins and other coins, store them, and then send them to others.
You can think of a wallet as your personal interface to the Bitcoin network, similar to how your online bank account is an interface to the regular monetary system.
Wallets contain private keys; secret codes that allow you to spend your coins.
In reality, it’s not coins that need to be stored and secured, but the private keys that give you access to them.
In short:
A crypto or Bitcoin wallet is simply an app, website, or device that manages private keys for you.

Ledger Live makes it easy to send and receive Bitcoins to your Ledger Nano X
This guide will show you how to create a wallet and pick the best one.
Types of Bitcoin Wallets
There are a few different types of Bitcoin wallets used today, and each of them come with their own tradeoffs between security and convenience:
We'll cover this in full detail in chapter two (up next), but put simply there are wallets for holding your everyday spending money (hot wallets) and there are wallets for your long term savings (cold wallets). There are even several types of both hot and cold wallets.
An Exchange is Not a Wallet
Again, we will cover this is more detail in Chapter five below, but its worth stating here as well that your Bitcoin "bank" or exchange accounts that do hold Bitcoin are NOT wallets.

Coinbase app does not let you hold you own keys, therefore it is not a wallet.
If that is confusing, don't worry - it will all make sense by the time we are done here.
This is not to say that bitcoin banks are inherently bad.
It is simply important to remember that whoever controls the private keys controls the bitcoin attached to those keys. A misunderstanding of this point has led to hundreds of millions of US dollars being lost in the past, so it’s important to understand this key difference in how Bitcoin private keys can be stored.
For now, just know that private keys are what you need to protect if you want to keep your bitcoin safe from hackers, user error, and other possible issues.
Chapter 2
Types of Bitcoin & Crypto Wallets
Now let's discuss the types of wallets and why you might want to use one kind over another.
By the end of this chapter, you should have a good idea of which wallet is right for you.
Hardware Wallets
The Ledger Nano S is one example of a hardware wallet.
A hardware wallet is a physical electronic device, built for the sole purpose of securing crypto coins.
The core innovation is that the hardware wallet must be connected to your computer, phone, or tablet before coins may be spent.
The two most popular and best Bitcoin and cryptocurrency hardware wallets are:
- Ledger Nano X
- TREZOR T
Hardware wallets are a good choice if you’re serious about security and convenient, reliable Bitcoin & crypto storage.
Hardware wallets keep private keys separate from vulnerable, internet-connected devices.
Your all-important private keys are maintained in a secure offline environment on the hardware wallet, fully protected even should the device be plugged into a malware-infected computer.

Malware should be no match for your hardware wallet.
As bitcoins and cryptocurrencies are digital, cyber-criminals could, potentially, target your computer’s “software wallet” and steal them by accessing your private key.
Generating and storing private keys offline using a hardware wallet ensures that hackers have no way to reach your coins.
Hackers would have to steal the hardware wallet itself, but even then, it can be protected with a PIN code.
Don’t worry about your hardware wallet getting stolen, lost or damaged either; so long as you create a secret backup code, you can always retrieve your coins.
Think of a hardware wallet like your own underground steel vault. If you own a significant amount of bitcoin or crypto, you should strongly consider getting one!
Why are hardware wallets good?
Easiest way to securely store bitcoins and other coins
Easy to backup and secure
Less margin for error; setup is easy even for less technical users
Multiple hardware wallets can be used together for extra security
Why are hardware wallets bad?
They're not free!
They can be challenging for new users to understand
Hot Wallets
Hot wallets are wallets that run on internet connected devices like a computer, mobile phone, or tablet.
Private keys are secret codes. Because hot wallets generate your private keys on an internet connected device, these private keys can’t be considered 100% secure.
Think of a hot wallet like your wallet today: you use it to store some cash, but not your life savings. Hot wallets are great if you make frequent payments, but not a good choice for the secure storage of bitcoins.
Why are hot wallets good?
Easiest way to store small amounts of bitcoin and crypto
Convenient; spending and receiving payments is easy and fast
Some hot wallets allow access to funds across multiple devices
Why are hot wallets bad?
Not safe for the secure storage of large amounts of bitcoins and crypto
You might forget about the application being installed on your phone
Which Wallet is Best for You?
Why are you using Bitcoin & Crypto?
Investing or saving? Then a hardware wallet will keep your coins safe.
Otherwise, a software wallet will send and receive bitcoins & crypto just fine. Best of all, software wallets are free.

Blockstream Green is one of the most secure mobile wallets out there.
Each wallet has pros and cons, and different wallets are built to solve different problems.
Some wallets may be geared towards security, while some wallets may be more focused on ease-of-use.
Your specific needs should determine the wallet you use, as there is no “best bitcoin wallet”.
How to Add Funds to a Bitcoin Wallet
Most wallets don't give you the ability to buy and sell bitcoin. So, if you want funds in your wallet you'll need to purchase on an exchange and send the coins to your wallet.
We've listed some popular exchanges below:
Popular Exchanges
Coinmama
Works in almost all countries
Highest limits for buying bitcoins with a credit card
Reliable and trusted broker
eToro
Supports Bitcoin, Ethereum & 15 other coins
Start trading fast; high limits
Your capital is at risk.
This ad promotes virtual cryptocurrency investing within the EU (by eToro Europe Ltd. and eToro UK Ltd.) & USA (by eToro USA LLC); which is highly volatile, unregulated in most EU countries, no EU protections & not supervised by the EU regulatory framework. Investments are subject to market risk, including the loss of principal.
Below, we've listed wallets you can buy or download. We suggest using the wallets listed or doing research before buying or downloading any wallet.
Each day, new Bitcoin scam wallets are added to the Google Play Store and Apple app store that are designed to steal peoples' bitcoins.
We only list wallets that have published and open-sourced their code.
Chapter 3
Hardware Wallets: Keep Your Coins Safe
Hardware wallets aren't free.
But the price can be worth it if you own a significant amount of coins.
A hardware wallet will protect a few hundred in bitcoin/crypto just as effectively as a few million.
The three most popular hardware wallets: KeepKey, Ledger Nano S, and Trezor.
How Hardware Wallets Work
Hardware wallets are secure, offline devices. They store your private keys offline so they can't be hacked.
This means you can even use one on a malware infected computer.
Why A Hardware Wallet with a Screen is Important
In the table below, you'll notice we show which hardware wallets have screens.
Screens provide extra security by verifying and displaying important wallet details. Since the hardware wallet is nearly impossible to hack, its screen is more trustworthy than data displayed on your computer.
Bitcoin & Crypto Hardware Wallet Comparison
Check the table below for a quick comparison. Note:
We also did a detailed comparison of the three main ones: Ledger Nano S, Trezor, and KeepKey.
COMPARISON
Ledger Nano X
RELEASED: 2019
PRICE: $119
Ledger Nano S
RELEASED: 2016
PRICE: $59
TREZOR T
RELEASED: 2018
PRICE: $159
TREZOR One
RELEASED: 2013
PRICE: $59
Best Bitcoin Hardware Wallet Overviews
Ledger Nano X
The Ledger Nano X is Ledger's newest hardware wallet. The main benefit is that it has bluetooth, making it the first hardware wallet that connects with iOS devices. It's more secure than using just an app on your phone, because all transactions are signed with the Nano X.
Ledger Nano S
The Ledger Nano S is the cheapest of the three hardware wallets with a screen; it costs about $59. Ledger, one of the most well-known Bitcoin security companies, released the device in August 2016.
TREZOR T
The TREZOR Model-T is a second generation Bitcoin/crypto hardware wallet manufactured by SatoshiLabs. The TREZOR line debuted in 2014 with the TREZOR One and has remained one of the most popular cryptocurrency cold storage solutions to date.
TREZOR One
TREZOR launched in August 2014 as the first Bitcoin hardware wallet, offering secure bitcoin storage plus the ability to spend with the convenience of a hot wallet. TREZOR is a small, thumb-sized device.
Chapter 4
Hot Wallets
Best hot wallet
Just a quick refresher:
Hot wallets are Bitcoin wallets that run on internet connected devices like a computer, mobile phone, or tablet.
As hot wallets generate private keys on an internet connected device, these private keys can’t be considered 100% secure.
Think of a hot wallet like your wallet today: you use it to store some cash, but not your life savings. Hot wallets are great if you make frequent payments, but not a good choice for the secure storage of bitcoins.
Desktop wallets are downloaded and installed on your computer. If privacy is your main concern, the Bitcoin core wallet is a good option since it does not rely on third parties for data.
Electrum
Electrum is a light weight Bitcoin wallet for Mac, Linux, and Windows. Electrum was created in November 2011. The main features of Electrum are: support for hardware wallets (such as TREZOR, Ledger Nano and KeepKey), and secure Bitcoin storage using an offline computer. Electrum is a good option for both beginners and advanced users.
Blockstream Green
Blockstream Green is a powerful Bitcoin wallet for iOS, Android, and Desktop. It's very easy to use and can be setup in a few minutes.
iOS and iPhone Bitcoin Wallets
Apple banned Bitcoin wallets from the App Store in February 2014, but reversed its decision a few months later. Luckily, there are now plenty of options for iOS users.
BRD
We consider BRD, along with Copay (below), as the best bitcoin wallet for iPhone. It’s open source and gives the user full control over their private keys. It also has a clean interface which makes the sending and receiving of bitcoins a pleasurable and super-simple process.
Edge
Edge is an easy to use Bitcoin wallet for iPhone and Android. Its familiar login feature makes using the app a breeze for people new to bitcoin. The wallet also creates automatic backups, so you don't have to worry about the technicalities of performing manual wallet backups.
Blockstream Green
Blockstream Green is a powerful Bitcoin wallet for iOS, Android, and Desktop. It's very easy to use and can be setup in a few minutes.
Aqua
Aqua is a new non-custodial, singlesig wallet made by Blockstream as a way to offer a more newb friendly wallet than Blockstream Green. It's incredibly simple to use and supports liquid assets as well.
Android Bitcoin Wallets
There is a large selection of Android wallets. Since Bitcoin wallets were originally banned by Apple, developers spent much of their time developing for Android.
BRD
BRD, the great iPhone Bitcoin wallet, recently released an Android wallet. It offers the user control of private keys, an easy to use interface, and passcode support.
Edge
Edge is an easy to use Bitcoin wallet for iPhone and Android. Its familiar login feature makes using the app a breeze for people new to bitcoin. The wallet also creates automatic backups, so you don't have to worry about the technicalities of performing manual wallet backups.
Blockstream Green
Blockstream Green is a powerful Bitcoin wallet for iOS, Android, and Desktop. It's very easy to use and can be setup in a few minutes.
Bitcoin Wallet
Bitcoin Wallet, or “Schildbach Wallet”, was the first mobile Bitcoin wallet. Bitcoin Wallet is more secure than most mobile Bitcoin wallets, because it connects directly to the Bitcoin network. Bitcoin Wallet has a simple interface and just the right amount of features, making it a great wallet and a great educational tool for Bitcoin beginners.
Chapter 5
Bitcoin Banks: $10 Billion Lost in Hacks
Bitcoin Banks
One last thing to keep in mind when it comes to bitcoin wallets is that there is a difference between a wallet and a bank.
Some Bitcoin users view Coinbase as a Bitcoin wallet, but companies like this operate much more like banks.
Remember:
The private keys are what users need to protect to safely use the Bitcoin network without getting robbed. When you hand someone else control over your private keys, you are essentially making a deposit at that financial institution – much like a deposit at any bank.
Don't store coins on exchanges! Bitcoin users have lost over $10 billion worth of bitcoins in exchange hacks and scams. Control your own private keys.
This is not to say that bitcoin banks are inherently bad. Companies like Coinbase have done wonders for bringing more users into the ecosystem. It is simply important to remember that whoever controls the private keys controls the bitcoin attached to those keys.

The Mt. Gox exchange was subject to the largest exchange hack in history, losing 850,000 Bitcoins.
A misunderstanding of this point has led to billions of US dollars being lost in the past, so it’s important to understand this critical difference in how Bitcoin private keys can be stored.
Understanding how bitcoin wallets work is an important aspect of safely using this new technology. Bitcoin is still in its early years of development and wallets will become much more user-friendly in time.
In the near future, certain devices may eventually come with pre-installed wallets that interact with the blockchain without the user’s knowledge.
For now, it’s vital to keep in mind that the private keys are what you need to protect if you want to keep your bitcoin safe from hackers, user error, and other possible issues.
Chapter 6
Theft and Scams
Bitcoin theft
No matter which wallet you choose, remember:
Our bitcoins are only safe if the private key was generated securely, remains a secret, and--most importantly--is controlled only by YOU!
Let's learn about what happens when this isn't the case.
Here are two examples where users got ripped off by leaving bitcoins in the care of a third party:
The Bitfinex hack, in which users lost $70 million
The failure of Mt Gox, in which users lost $450 million or more
To avoid theft, scams, and any other loss of funds, follow these three basic principles:
Generate your private keys in a secure, offline environment. (Except if using trivial amounts, in which cases keys may be created in a hot wallet).
Create backups of your private keys. This helps to protect against the loss of your bitcoins due to hard drive failure or some other problem or accident. Ideally you should have a duplicate set of backups kept off-site to protect against the possibility of fire, robbery, etc.
Encrypt wallets to provide additional security. This helps prevent the physical theft of your funds in the event that your device or hardware wallet is stolen.
Securing your bitcoins properly is the most important step for any Bitcoin user.
With Bitcoin you have the privilege - but also the responsibility - to safeguard your own money. There have been countless scams related to Bitcoin that could have been prevented had people not entrusted others with their bitcoins.
It’s a good rule of thumb to never trust anyone else with your money.
Ledger Nano X
Ledger Nano S
TREZOR T
TREZOR One
Bonus Chapter 1
Cryptocurrency Security Advice
Whether your on an exchange or using a wallet, this section will give you some tips on how to secure your cryptocurrency in ways you may not have seen before.
From changing your mobile network to encrypting your internet connection - these tips are actionable and easy to implement quickly.
The migration of value into the digital realm brings with it new challenges in terms of best security practices. As with any unit of value, there is always someone, somewhere that seeks to extract this value for their own ends, whether it be through coercion, social manipulation or brute force.
This guide is intended to provide a broad overview of the best practices for securing your crypto assets. While most of these steps are not mandatory, following them will greatly increase your financial security and peace of mind in the crypto world.
Passwords — Complexity & Re-Use
Starting from the ground up, password complexity and re-use are two major pain points that many average users do not consider adequately. As you can see by this list, average password complexity still leaves a lot to be desired. The less complex your password is, the more susceptible to hack your account is. If you use the same passwords, or even slight variations of the same passwords across multiple accounts, your chances of compromise are greatly increased.
So what can you do? Fortunately the fix for this is relatively easy. Use randomly generated 14 character+ passwords and never re-use the same password. If this seems daunting to you, consider leveraging a password manager such as LastPass or Dashlane that will assist in password generation and storage.

Lastpass is a our favorite password generator and manager.
You can find out if any accounts associated with you have ever been compromised here as well as using this tool https://howsecureismypassword.net to test just how strong variations of your passwords may be (*do not use your real password on here, only similarly structured variations).
Dedicated Email Accounts
Almost every online service/exchange requires some type of email account association during the activation process. If you are like most people, you will probably use your default email that you’ve had for years, and perhaps add a bit more complex password for the account itself for good measure.
In most cases however, all a hacker needs is access to your emails in order to reset account passwords that may be tied to it. It’s as simple as navigating to the website/exchange and clicking the ‘forgot password’ link to begin the process. So, if you are like most people and have an email address that has been active for years, with a weak login password, your chances of being hacked are much higher.
For the above reasons, do yourself a favor and create a new/dedicated email address for use with your crypto accounts. Services like ProtonMail and Tutanota are free and offer end to end encryption without sacrificing usability (mobile app availability etc.). If you decide to PayPal with Gmail, consider activating the Advanced Protection Program that Google offers.

Proton Mail offers email with end-to-end encryption.
Usa a VPN
A virtual private network (or VPN) is simply a must for everyone today, but especially cryptocurrency users.
Why?
As we surf the internet, there are unfrotuantely a lot of eyes on us at all times. One very big set of eyes watching us is our internet service provider (or 'ISP'). They see and hear everything we do on the internet. And they often share that information with third parties. But our ISP and its friends are not the only people watching. Anyone using the same wifi network that we are using can also see what we are up to online.
A VPN solves this problem. When we use a VPN, our computer's IP address is not connecting to any website directly. Instead we are communicating to another IP address over an encrypted connection. Then that IP address makes website requests on our behalf and send us back that data. This helps keep onlookers onto our connection locked out so that only one party knows what we are doing (the VPN).

It's therefore important that you choose a vpn service with a great track record.
The reason VPNs are important for cryptocurrency users especially is that we use Bitcoin to keep as much data hidden as possible. However, when we expose our IP address, we might give away that our IP address is connected to someone who owns and uses cryptocurrency, merely because of the websites we visit.
Long story short: everyone should be using a VPN regardless of whethor or not they use Bitcoin. It's for your own safety.
VPN
NordVPN
Special support for Malaysia, Nigeria, Singapore, South Africa
SEPA & credit card supported
Trusted exchange
Surfshark
Users claim fast speed from wide range of servers all around the world
Compatible with nearly any OS
ExpressVPN
Allows for Netflix
Users claim fast speed
Has apps for nearly any platform
Two-Factor Authentication
We typically recommend setting up two-factor authentication (2FA) for any and every account that offers it, even if the service is not crypto related. All 2FA does is require a second means of confirmation that you are who you say you are when logging into accounts. Most typically this is in the form of something you know (password) and something you own (SMS code sent to phone).
While SMS is still the most common form of 2FA offered by online services, it is unfortunately the least secure. The following general use 2FA methods are ranked from most secure to least:
FIDO U2F — This is a physical device that plugs into a USB port and requires a physical button touch to generate a unique 2FA access code. It is preferable because a hacker would need to have the device in their physical possession in order to access your account. Most hacks occur remotely which makes this our top 2FA choice (albeit not a panacea).

Yubikey is the most popular hardware second factor
Google Authenticator — An app that resides on your mobile device and cycles through one-time use access tokens. If you go this route, be sure to save your backup code that is provided at initial setup. If you don’t have this and your phone is lost or broken then you have no way to get these code settings back. While not as good as a yubikey, it's still better than SMS two factor.
Authy — Similar to Google Authenticator but potentially less secure as you can re-access the codes from an alternate mobile device if your main one is lost or broken (this feature can be disabled but is active by default). While this may seem more ideal, what is more convenient for you is also more convenient for those who may be trying to hack you.
SMS — Codes send to your cell phone through text message. Better than no 2FA at all, but susceptible to social engineering SIM attacks. Interestingly, SMS 2FA security holes did not come to light until the popularity of Bitcoin began to grow.
Google Fi
Speaking of SIM attacks, there is one way to avoid them.
Services like Google Fi offer an alternative to traditional mobile phone contracts that are not only more flexible but also more secure.
With Google Fi, you can prevent any changes from occuring on your account without providing a second authentication factor. And because there are no SIM cards in a Google Fi plan, there are also no SIM attacks. This makes it impossible for attackers to hijack your text-messages and take over your accounts.
Currently, Google Fi is the only mobile phone service in the US that offers 2FA. So if you intend on taking your security serously in this area, Google Fi is the only way to do it if you live in the United States.

Google Fi features
Another nice perk of Google Fi is that its easy to change your phone number whenever you want. This feature alone also increases your security since many of our phone numbers have been leaked before and can be used to access other accounts online. If your leaked phone number is no longer active, you are a little more protected.
Mobile Crypto Wallets
Mobile app wallets such as Mycelium, BRD, Samourai, Cryptonator, etc. should be treated similarly to how you may treat your physical wallet/purse.

Samourai's homepage
You only carry small amounts of discretionary spending funds in these wallets as they are more susceptible to loss or theft. Again, what is more convenient for you is more convenient for a malicious actor as well. Your phone is also susceptible to malware and should not be considered sufficiently safe for storing large amounts of funds.
Phishing Attacks
If you have crypto then you are an ideal target for phishing scams. Facebook and Twitter are just two of many avenues that hackers scour for potential victims. It has become common to see fake crypto exchange emails or ICO fundraising confirmations circulating such as the example below.

Phishing email impersonating Blockchain.info. Note send address & logo irregularity.
It is best to NEVER open suspicious attachments or provide credentials through email and to always closely inspect the logo, wording and send address of any emails received that pertain to financial accounts or that request sensitive information.
When in doubt, navigate to the legitimate exchange or web service that the email supposedly originated from and contact their support team to inquire on the validity of what you received before taking further action.
Clean Hardware
This brings us to the general best practices portion of this guide. Malware is everywhere on the internet and regardless of your attention to detail, sooner or later you are likely to fall victim to some type of malicious software. As such, it is best to have active antivirus subscriptions on your devices and to run periodic scans. I personally like to run Malwarebytes and Roguekiller on my PC once each week and have background scans on my phone that run each automatically.

Malwarebytes' homepage
Generally speaking Windows is the least secure OS, primarily due to the fact that it is the oldest and most pervasive OS in use today. Many security conscious techies tend to prefer Linux or iOS for this reason.
Secure Crypto Storage
If you don’t hold the private keys, you don’t own your money!
This category is how most people have been compromised and lost money in crypto. How? Primarily, by treating an exchange (Coinbase, Binance, Bittrex, Poloniex etc.) as a wallet to store their crypto assets in.
Mt. Gox, Bitfinex, BitGrail and Coincheck are just four out of a handful of crypto exchanges that have been hacked in the past 5 years, with the cumulative amount stolen exceeding $1 billion USD. While some users of these exchanges have been ameliorated to an extent, many are still suffering from the partial or even total loss of crypto funds that they held on these exchanges at the time of the hacks.
Our advice is to hold crypto on hardware and back it up using a steel wallet.

The Billfodl is a steel wallet that backs up your recovery phrase, protecting it from fire and flood.
If you wish to trade on exchanges, only do so with funds that you are potentially willing to forfeit entirely should either the exchange or your individual account become compromised.
A few of our recommended hardware wallet manufacturers are Ledger and trezor. You can find our more detailed wallet reviews here . As with all hardware/software, please ensure that your device firmware is kept up to date, as patches are pushed out continuously to address security concerns.
The Subject of Secure storage is something we cover in much greater depth in the next Bonus Chapter
Summary
Security on the web is akin to game of whack-a-mole and your level of security will likely scale accordingly with the amount of sensitive data (or crypto assets) that you are protecting.
While there is no such thing as an ‘unhackable’ system, there are valuable steps that you can take to drastically reduce your likelihood of compromise.
Always remember to:
Use complex and unique passwords
Create a separate/dedicated email account for crypto services
Use two-factor authentication
Store most (if not all) of your funds on hardware wallets
Be wary of phishing emails
Good luck and stay safe!
Bonus Chapter 2
Bitcoin Cold Storage
Cold storage
Unlike paper money, there more than a few options available for keeping your bitcoin secure.
Whether you're trading cryptocurrencies on a daily basis or you're a long-term bitcoin investor, cold storage can be a useful tool for keeping your crypto safe.
Understanding the Basics of the Bitcoin Wallet
In order to get a handle on what cold storage actually is, it's important to review the fundamentals of the "bitcoin wallet." In the same way that you can use a traditional wallet to store your paper currency, you can use a bitcoin wallet to store your bitcoin in digital form.
In other words, you can think of your bitcoin wallet as your personal bitcoin mailing address.
This might sound like having a bank account, but it's actually quite different.
Instead of needing to trust a third party to keep your cryptocurrency secure, you can use a bitcoin wallet as your sole gateway to the decentralized network. There's no need to ask a branch manager for permissions when you want to transfer bitcoin, there aren't any annoying forms to fill out, and transfers happen within minutes.
Bitcoin wallets can be used to:
Pay for items with bitcoin by transferring your payment to merchants who accept cryptocurrency.
Receive bitcoin deposits from customers, friends, or relatives.
Maintain your financial privacy by making anonymous purchases.
What is Bitcoin cold storage?
As you can see, bitcoin wallets are incredibly useful. All of this begs the question, however, of how many different types of bitcoin wallets there actually are.
Generally speaking, Bitcoin wallets come in two main types:
Hot wallets
The phrase "hot wallet" refers to any bitcoin wallet that requires the internet to function properly. Hot wallets derive their name from the fact that they need electricity to work. If the power goes out, then so does your hot wallet.
For example the popular mobile wallet BRD is an example of a hot wallet.

BRD is a widely used mobile "hot" wallet
Cold wallets
Not only do cold wallets work without an active internet connection, but many cold wallets don't even need a computer. Cold wallets have several similarities to traditional physical wallets, but they also have a few differences.
For example, the Ledger Nano X and Nano S are the most popular cold wallets on the market.

titans of the hardware wallet field
Is "Cold Storage" Different Than Using A Cold Wallet?
In general, "cold storage" refers to any bitcoin storage device that does not require electricity. A cold storage device can be a physical box, a piece of paper, or a list of numbers and letters that you keep in your head.
"Hot storage," as you may have guessed, is simply the analogous generalization for storage devices that require an internet connection.
Thus, hot wallets are an example of hot storage devices, and cold wallets are an example of cold storage devices.
The Major Differences Between Cold Storage And Hot Storage
hot vs cold storage
In contrast to hot storage, cold storage provides:
Increased security protections
A reliable way to keep your bitcoin offline
An easy way to transport your bitcoin between your various wallets
What are the different types of bitcoin cold storage wallets?
When it comes to choosing a cold storage wallet that can help keep your bitcoin secure, the most popular choices tend to be:
Hardware wallets
Hardware wallets include USB PayPals and other digital storage devices that you can use offline. Typically the private key to coins is never exposed to the internet because the device itself is air gapped.
COMPARISON
Ledger Nano X
RELEASED: 2019
PRICE: $119
Ledger Nano S
RELEASED: 2016
PRICE: $59
TREZOR T
RELEASED: 2018
PRICE: $159
TREZOR One
SCREEN:
RELEASED: 2013
PRICE: $59
Steel Backups
The steel wallet is literally a piece of indestructible stainless steel that you can use to carry your bitcoin private keys or backups in. This makes it an excellent choice if you're concerned about losing paper or live in an area with lots of flooding, fires or earthquakes.
You can checkout how they work in the video below: https://www.youtube.com/watch?v=BuynQ7aIW0c
Steel wallets are interesting because they can act as both a "paper wallet" or as a backup for any kind of Bitcoin wallet in case yours is lost, stolen, or destroyed. Almost any cryto holder can benefit from one of these steel wallets regardless of how they choose to Store their coins.
STEEL WALLETS
Billfodl
Highest grade steel wallet
125% money back guarantee
Lots of accessories to up your security
Free shipping if you spend $75 or more
Cryptosteel
First steel wallet
Multiple types of steel wallets available
Free shipping on orders of $150 or more
Cryptotag
Made from titanium
Must manually stamp in letters
Paper wallets
If you're concerned about malicious computer hackers getting access to your wallet, then a paper wallet is one of your best options.

A very common Bitcoin paper wallet
WARNING
Setting up a paper wallet is for HIGHLY advanced users only. There are many ways to get a paper wallet wrong - all of which can result in a total loss of funds. Proceed at your own risk.
OpenDime
As the world's first bitcoin credit PayPal, the OpenDime device lets you spend your bitcoin balance in the same way that you would use a traditional credit card.

An OpenDime - front and back
The open dime is very much like a Bitcoin piggy bank. You can add as much bitcoin to it as you want and as many times as you want, however you can only spend from it once. At that point, the private key is exposed and the funds are no longer safe on the hardware. Because of this, its best to send all the coins to a new address once you are ready to use them.
For a great review and walkthrough on how the open dimes are used, watch this video: https://www.youtube.com/watch?v=1eJp99yAf_M
Comparing The Most Popular Cold Storage Wallets
So now you know of all the different options when it comes to choosing between cold storage wallets. Let's compare them all to each other to see which one would be best for you.
Paper Wallets Vs. Hardware Wallets
Technically speaking, hardare wallets fall somewhere in between a traditional hot wallet and a pure cold storage device.
With hardware wallets, the private key is stored digitally on a microchip, like a hot wallet. But that chip is never exposed to an internet connection.

Nano X Construction and Anatomy
Hardware wallets can be a bit easier to carry around and make transacitons with, but they are also subject to data degradation risks. This is why many users pair them with a steel wallet as a backup.
Paper Wallets Vs. Steel Wallets

Billfodl protects your coins from fires, floods, and even atomic blasts
When it comes to state-of-the-art bitcoin cold storage, steel backups are definitely ahead of the curve. Steel wallets provide the convenience of the paper wallet with the portability of the hardware wallet, but they also come with some added security features that make them worth looking into.
Steel wallets have two primary uses:
They can be used to backup any kind of hardware or software wallet. Typically these wallets spit out a 12 to 24 word phrase you can use to get your coins back if your main wallet is lost, stolen, or destroyed.
They can be used as a more sturdy version of a paper wallet. After you have generated your paper wallet, you can recreate the private key in the steel wallet using the provided tiles. Afterward you can keep the paper Wallet with the steel wallet and if there is ever a fire or a flood, you have a copy of the paper wallet that will survive.
In the video below, you can see Billfodl (the most popular steel wallet) get put through several tests. It even survivied an explosion using 600 gallons of jet fuel https://www.youtube.com/watch?v=bm-pm_ERYIA
Paper wallets and steel wallets are both protected from hardware data degredation, however the ink on the paper can disintegrate or run if it gets wet or too hot. Steel wallets are also protected from this risk.
Paper Wallets Vs. OpenDime
The OpenDime is basically a cross between a hardware wallet and a steel wallet. If you're partial to the idea of carrying a paper bitcoin wallet, then OpenDime can be another viable option. Like hardware wallets, open dimes are subject to data degredation over time.

On the other hand, paper wallets use regular paper to reduce the chance of your coins being hacked. Paper wallets keep your public and private keys on a plain sheet of paper, but they can also be modified to include a QR code to transfer data back and forth between your other cold storage devices.
Closing Thoughts
In summary, bitcoin cold storage is an effective way to keep your cryptocurrency from falling into their wrong hands. Even though it can be easy to end up feeling overwhelmed when you consider all of the cold storage options available, there's no reason to limit yourself to just one wallet type.
One of bitcoin's best features is that it's easily divisible, so you can allocate a portion of your holdings to several different cold storage devices at once.
Most cryptocurrency users keep some bitcoin in cold storage and some in a hot wallet to have some funds that are ready to use.
Whichever way you choose to allocate your bitcoin, make sure to keep security at the forefront of your plan.
Bonus Chapter 3
How to Make a Paper Wallet
Cold storage
Ever been curious about how to make a paper wallet?
Or does the thought of making one intimidate you?
Is it even safe to make one?
Let's find out in this detailed guide on how to create a Bitcoin paper wallet.
Creating a Paper Wallet - The Quick Way
1. Navigate to BitAddress.org. BitAddress is an open source program for creating Bitcoin paper wallets.
2. Move your mouse around the screen or enter random letters and numbers into the textbox to add randomness to the wallet creation.
This randomness is called entropy and will help ensure your keys are secure and resistant to brute force cracking.
3. Once you reach 100%, BitAddress will present you with a public key, a private key, and a QR code for each. To get a printable version, select Paper Wallet. You can create any number of wallets you like.

4. To add an extra layer of security by encrypting the private key, check the BIP38 box and enter a password. To conduct a transaction you will need the private key AND the password to the wallet from which you are sending funds. You can recognize a private key that has been encrypted by its first two characters, which will usually be 6P.

Print your wallet(s).

A BIP38 wallet encrypted with the password *buybitcoinsworldwide*.
That’s the quick and easy way to create paper wallets online using BitAddress. However, there are a number of security concerns to take into consideration:
Your computer could be infected with malware, which would allow an attacker to see your freshly generated private keys, giving them full access to any funds you then load onto the wallet.
The website itself could also be compromised. You are trusting BitAddress not to view and record the private keys that you generate.
Lastly, printers have their own memory where the file containing your private keys could be stored. For this reason, do not use a shared printer to print your paper wallet.
Creating a Paper Wallet - The Secure Way
To securely create a paper wallet we will follow the steps outlined above, but take a couple of additional measures to address the security flaws.
This video outlines goes through the process, and each step is listed below for you to follow along.
https://www.youtube.com/watch?v=VTsHeiBhPIM
1. Download the offline version of BitAddress from its GitHub repository https://github.com/pointbiz/bitaddress.org/archive/master.zip. Here you will find the paper wallet generator’s open source code. Save this to a USB drive.

2. Next, you’ll need a secure computer. Ideally this would be an airgapped computer that has never seen the internet and never will. Alternatively, booting off a live installer will avoid most security issues.
This guide https://ubuntu.com/tutorials/tutorial-create-a-usb-PayPal-on-windows#1-overview explains how to create a bootable USB drive off of which you can run Ubuntu, a popular Linux distribution. A Windows or Mac virtual machine will work in a pinch.

3. Extract the zip file on the USB and open the bitaddress.org HTML file. You’ll be taken to an offline version of the website.

4. Follow the same steps as detailed above, using your mouse and/or keyboard to create entropy, choosing the number of wallets you wish to create, and adding BIP38 encryption if desired.

5. Connect to a printer with a wired connection, not Wi-Fi, and print your wallet(s). You could also avoid any potential issues with printer security by writing out your public and private keys.

That’s it, you have now generated one or many paper wallets that you can use for cold storage of Bitcoin. If you used a live OS to generate your keys, be sure to exit out of it and reboot so all traces are erased from the computer’s memory. If you used an airgapped computer, it’s best that it never be connected to the internet.
You can safely share your public key, also known as the wallet address, and use a blockchain explorer such as blockstream.info to check the wallet’s balance.
Spending Coins on a Paper Wallet

To send funds from your paper wallet, you will need to import or sweep your private key into a wallet client. Importing a private key simply adds it to the list of keys in your software wallet, preserving its unique address. This means that if someone got their hands on your paper wallet, they could still take control of the Bitcoin on it. Sweeping a private key transfers the funds associated with it to a new or existing address. This leaves the paper wallet empty.
You can import or sweep your private key into the software wallet by scanning the QR code with your webcam or typing out the private key.
WARNING
As mentioned above, both of these options run the risk of exposing your private key to any keylogger or malware, which is why you should never reuse paper wallets.
Once the Bitcoin is in your software wallet, you can send it as you would any other transaction.
QUICK TIP
If importing a private key, note that if *any* amount of Bitcoin is spent using the software wallet, the paper wallet will be *completely* emptied. The Bitcoin network spends the entire balance of a private key and sends any leftover amount – the change – to a newly-generated private key in the software wallet.
Bonus Chapter 4
Bitcoin Wallet Frequently Asked Questions
Many of you may still have lots of questions about wallets and how to keep your bitcoin secure.
We update the chapter below any time we get a new question from our readers, so odds are we have answered almost any question you could think of below.
What are Bitcoin Wallets?
Bitcoin Wallets let us send, receive and store Bitcoin.
Wallets secure funds by guarding our private keys. These private keys act as the proof of ownership for our Bitcoins. As such, a Bitcoin wallet is like a safety deposit box for Bitcoins.
What is a private key?
If a Bitcoin wallet is like a safety deposit box for our Bitcoins, then our private key is like the key to the safety deposit box. The only difference is that, in the real world, you could break open a safety deposit box without the key. However, in Bitcoin, there is no way to break open the wallet without the key. It is impossible.
Therefore, keeping your private key secret is the most important thing you must do to keep your Bitcoins secure.
What is a Bitcoin address?
A Bitcoin address is like an account number, just better. The address denotes which wallet the coins should be sent to. Like a bank account number, where the difference lies in the wallets having multiple addresses. These can be customized by including payment request information such as an amount and a date of expiration.
What are Steel Bitcoin wallets?
Steel wallets are made to store your backup seed. If you store your seed on paper, it could get burned in a fire or destroyed in a flood. Steel wallets protect against all of these threats by creating an indestructible backup for your seed.
How do I add coins to a Bitcoin Wallet?
First, acquire some Bitcoins. Go through an exchange in your country, ask an acquaintance to share, or use Buybitcoinworldwide.com if you want as seamless of an experience as possible. The purchased coins can then be sent to your wallet by specifying one of its addresses.
Some wallets, particularly online ones, also let you buy coins. Keep in mind that these come with larger exchange margins which are best left alone.
How do I open a Bitcoin account?
To some readers this might seem like a weird question. Truth is, people coming from a financial or business background are likely to expect Bitcoin to be a direct alternative to our current financial system. This is not the case.
You don’t need a Bitcoin account. There is no such thing really. You just need a wallet. The only accounts you might encounter are online wallets that are separated into various accounts via a user system.
Any common mistakes to be careful of?
First of all, don’t rest your money in an exchange wallet. Keep your coins in an environment where you have complete control.
Secondly, don’t keep all of your coins in one place. You’ll be crushed if you lose access to a wallet with all of your funds.
Thirdly, double check the target address. Bitcoin transactions cannot be reversed, so don’t lose your coins forever to a stranger!
How many backups of my seed should I create?
We recommend keeping at least two backups of your seed in multiple locations.
You can also laminate your seed to protect against water damage or any other damage.
Keeping your seeds in fire proof safes can help protect in the event that the storage location is burned down.
Another option is to put your seed into metal manually using stamps, or using Billfodl.
What happens if someone finds my 24 word seed?
Unless you’re using a 25th word, someone who finds your 24 word seed can sweep your entire wallet.
Should I take a picture of the seed with my phone as a backup?
NO, NO, and NO!
The seeds generated by hardware wallets are meant to be written down only. By taking a picture of your seed with an internet connected phone, you put your entire wallet on a device that is connected to the internet and easier for hackers to get into. Please do not do this!
Is it ok to buy hardware wallets on ebay or amazon?
We always recommend to order directly from a hardware manufacturer or authorized reseller. This is because someone can buy a hardware wallet, tamper with it, and sell it used. They could program it to steal any bitcoins or add a back door.
Most hardware wallets add some special kind of tape on the packaging to try to make any tampering more noticeable. This is another reason we recommend only ordering from the hardware wallet company or reseller, and not from a website like eBay.
What happens if the hardware wallet company goes out of business?
If Sony went out of business tomorrow, you would still be able to play your playstation with mostly no issues. Hardware wallets are the same. You do not need a company to remain in business in order to continue using your hardware wallet. You would, however, need to run your own node in order to send and receive transaction.
Let’s say you use TREZOR with TREZOR’s myTREZOR wallet. TREZOR goes out of business and no longer supports myTREZOR wallet and it gets shut down.
You could, in just a few minutes, download Electrum on your computer. Once installed, you’d setup your TREZOR and all of your transaction history and balance would get imported and be exactly the same. This is because Electrum will use the same 24-word seed you generated with TREZOR on setup.
Do these hardware wallets work for Ethereum?
Yes, all of these wallets work with Ethereum, Litecoin and many other coins.
Do these hardware wallets work with Coinbase?
One of the most frequent questions we get asked is how Coinbase works with hardware wallets.
It’s a trick question!
Coinbase does not work directly with hardware wallets. You should, however, send bitcoins from Coinbase directly to your hardware wallet once you buy. Never store bitcoins on Coinbase or any other exchange for long periods of time.
(c) https://www.buybitcoinworldwide.com/wallets/