
Hello! The phone is something that is always with you. She knows what you say in your sleep, knows what you did for 5 minutes. She knows more than you do.
The device itself is not intended for anonymity, but we will try to create "isolation". Our goal is to set up the device so that not a single byte goes to the Internet without your consent. We will discuss how to remove Google, which sends 100 requests to its servers per minute (and no, I'm not kidding, this is really true). Alternatives to remote applications, data encryption, changing device settings, etc.
- Getting Root rights
- Disabling Google Services
- Basically it is done this way:
- List of services that I disabled without consequences:
- Deleting system garbage
- Method via ADB
- Method via SD MAIN
- We check the result of the work
- PlayMarket Alternatives
- How do I pay via NFC without Google Pay?
- Alternative to dialers
- Setting up your browser
- Canvas Blocker
- Useragent Switcher
- FoxyProxy
- uBlock Origin
- VERY IMPORTANT TIP
- Telegram Messenger
- Complete traffic routing via TOR
- Data Encryption
- Disabling access to the microphone and camera
- Summing up the results of the work
Getting Root rights
Root rights = full control over the device. With their help, we can remove what is not removed and get a lot of benefits, which I will discuss later. The receiving instructions for each phone are different, so I don't want to give you any advice on this, so as not to cause the death of your device. I'm not a professional in such matters, and I recommend turning to open sources. During my first rooting, I had to restore the device from the "brick" mode 3 times, this was due to the unpopularity of the device model, but do not worry, there should be no problems with the conditional Xiaomi (the most popular brand in the CIS). Check reviews from sources. With my Realme, it was something like this, you will have a similar process:
multiple commands in adb -> install one-time recovery with one command -> install Magisk (root rights manager) with one command -> formatting
Disabling Google Services
As I mentioned at the beginning, this is the main spy in our device. It is sewn into almost all phones by default, but we will replace it. For proper removal, you must use the "ADB AppControl" program and get "Developer Mode".
Basically it is done this way:
Settings → About Phone → Version → Build Number → Tap 10 times.
After that, visit the "For Developers" tab and enable "USB Debugging".
By the way, we can also use this utility to remove the "system garbage" that comes with the phone. I will list the services that can be disabled, nothing happened to my phone (Realme) and the functionality is preserved.
The app has a graphical interface and I don't see any point in reviewing it. There is a convenient search engine in the upper-right corner, enter the names of applications that I left below. After that, right-click "Disable", everything is as simple and clear as possible, example below.
Please note that you must disable it! Do not delete these apps, if something goes wrong, you can enable them back in the program. Do this at your own risk, everyone has different phones and I can't say that everything will work fine after that!
List of services that I disabled without consequences:
- Print Service Recommendation Service, Android Device Setup, Accessibility, Google Play Services, Market Reviews, Google Speech Services, Digital Wellbeing, Google Services Framework, Google Partner Setup, Location History, Google Keep Notes, Google One Time Init, Carrier Services, Google Assistant, Google Files, Assistant, Calendar, YouTube, Maps, Photos, Lens, GPay, Google, Gmail.
Deleting system garbage
Almost all Android devices "fight off" their low price by embedding ads in their shell, which threatens our privacy. We have two options: use the same one ADB AppControl or third-party. apks on your phone. I will show you two methods, so choose what is more convenient for you.
Method via ADB
We search for "unwanted" applications using the corresponding button (see screenshot), select the verification level: Basic. After scanning, we will see what can be deleted in two clicks. I also advise you to enter the query: "partner" in the search, it will show you the installers of partner companies that we will not need in the device.
Method via SD MAIN
This is a third-party application that can also find applications that we don't need. It's paid, but I'll leave a link to the crack. It requires ROOT permissions and can be used as a "system cleaner".
The best solution is to use these two applications, so as not to miss out on some small detail that may play a big role in the future.
Disable sending errors and so on.
Shells can legally send your complete device data and actions to their servers.
Obviously, we are not going to share it with them, so we repeat the steps below:
go to settings - > privacy -> uncheck all the boxes associated with "testing, errors" , etc.
Different shells have their own nuances on this topic, so sit for 10 minutes, set up your phone normally, and clean up the phone on the way. Alternatively, turn to the Internet to learn about the "pitfalls" of your shell, usually there are even videos on such topics. We also disable system updates, it pings its servers every hour and can negatively affect our rooted device in the event of an update. I'll simplify your work and leave you some normal videos on this topic.
Disable background processes and their access to the Internet.
Each system has something that absolutely cannot be deleted, so we will proceed differently — disable such applications from accessing the network and working in the background. First, go to the "For developers" tab, find the parameters as shown in the screenshot below. Duplicate exactly my settings.
After that, we can restrict access to the network. We are looking for banal applications like "Settings, Check for updates, Gallery, Phone, Launcher" and in general everything that the system has installed. Go to the application management menu and uncheck "Network access". If your phone doesn't have this functionality, you can do it in adb.
On my phone, it works something like this:
Settings: I couldn't send data, camera, can you fill in for me?
Camera: now, I'll check the network, in case there's an error..
/ / Pings its server to see if it's working. //
Therefore, you should not allow access to something that the app doesn't need.Camera: Oh! And I have access. What data did you want to send?
If you can do this, set "Save Traffic". This will prevent background apps from accessing the Internet. Cons: instant messengers will send messages with a delay or not at all.
We check the result of the work
Download PacketCapture (an application that looks at all traffic) and start the debugging process. We need to leave the phone in this position for an hour to see if there are any bugs in the system that use the Internet without our knowledge. If they are found, we turn off the network for them, if not, we continue reading further. When working properly, you should not have any background requests. Every time you install new apps, don't forget to disable working in the background and disable passive traffic. With this, we'll finish the privacy stage, move on to setting up surfing, Google alternatives, and deeper utilities for anonymizing our device.
PlayMarket Alternatives
The network is full of analogues that offer even hacked versions of applications at once, I will highlight only the main ones:
Don't forget to disable their background work!
- AppGalary is an official app store created for Huawei phones, but it works on other brands.
- Uptdown App Store - there are quacks of games and programs. A large assortment, there is almost everything.
- APK Done is a poor app, but there are a lot of quacks. I do not advise downloading, it is better to make a shortcut to the site on the desktop.
How do I pay via NFC without Google Pay?
The answer is simple. Use analogs. There is a wallet from Huawei that works with many banks. You can cut out the card chip and put it under the case / just use the card in a physical copy. And it is better not to use them at all, they store your digital footprint in the form of movements at least. Switch to cash and feel safe, so your fiat will not be blocked by some bank that accuses you of unjustified income.
Alternative to dialers
On the new Andoid put a dialer from Google, which does not even allow recording a conversation: / Fix it! There is such an application as TruePhone, a real combat device that will even show the tower of the city from which you are being called. Naturally, there is a call recording, blacklist and other settings. The interface is fully editable, and you can create your own design.
I used this dialer until I managed to install the original one from Realme (UI 2.0), it is very pleasant in the interface and has similar functions, it only gets on the RealmeUI shell.
If you have a phone of this brand — put it, you will not find a better one.
Setting up your browser
I spent a very long time choosing a browser that can be configured for anonymity. I've had months of using real feces behind me, because I couldn't find anything better. Fortunately, just recently I was able to discover the best browser in my opinion that works on the basis of Firefox. Its advantage is that it supports extensions that are not available on official versions. Name: Iceraven. It is open source on the GitHub platform, supports 120fps, and will be used by us on an ongoing basis. In the initial configuration, we must disable the parameters with sending data for testing. The next step is to install extensions. Go to the appropriate tab and search for "Canvas Blocker", "FoxyProxy", "Useragent Switcher", and"uBlock Origin". Now I will explain what is responsible for what.
Canvas Blocker
Dynamically change the settings of our device every time the page is refreshed. Linking our digital footprint will be extremely difficult. During the initial configuration, specify the strictest mode of operation. This did not affect the display of sites in any way, but it hid the parameters much better.
Useragent Switcher
It is used to change the user agent, and you can automatically update it every minute. For example: sites will see that you are using Windows and the Amigo browser, when in fact we have Android and Iceraven.
FoxyProxy
The name speaks for itself. It is used to set up a proxy directly in the browser. Add your own proxy and specify the "To All Sites" parameter. After that, all links that open through the browser will automatically hide your primary IP address. In conjunction with the extension above, we literally completely hide the settings of our phone for all pages on the Internet
uBlock Origin
One of the most popular tools for blocking ads and much more. In fact, an analog of ADBlock. Install it and forget it, it will definitely not be superfluous.
VERY IMPORTANT TIP
As I described a little earlier, do not install those applications that are needed at one time / have a web version. Make site shortcuts on the desktop, the differences are minimal. Most applications are just web-based. a page that we can get without downloading to the device.
Site -> Three points -> Install. Practical, private.
Telegram Messenger
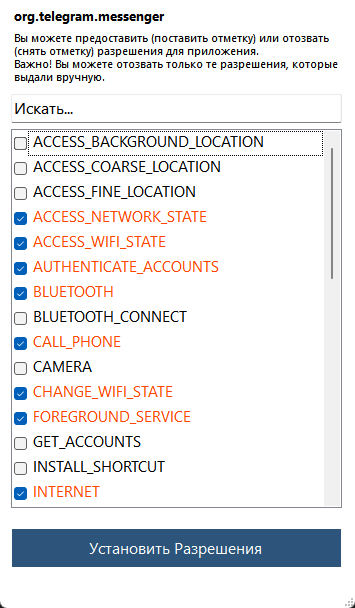
I will not explain that Telegram should not be installed on your device, you can see for yourself what data this "anonymous" messenger requires for its work, and I have an article on the topic of anonymous registration & use, be sure to check it out (see the screen, I attached less than half of the permissions)..
We will use the WEB version of this miracle using a TOR connection.
Thus, we can avoid problems if he decides to change his mind about the alleged "non-disclosure of information to state bodies". Download TOR to your phone and log in to web.telegram.org in older versions of the browser, you can create an application shortcut directly on the desktop. We can use it just like a regular client, but without using our IP address and real fingerprints. This method is suitable when you need to keep in touch at a" gray " job.
Complete traffic routing via TOR
Are you going to do something bad? Your option. Orbot is an app that will redirect all traffic on your device via TOR. You can change the location by clicking one button. Your IP address will be safe.
Do not forget to use it in conjunction with the already configured Iceraven browser, which we discussed above. After that, the sites can't identify us. In the "output node" role, you can use the proxy that we installed via FoxyProxy, so we will secure a clean IP. This will not save you from working with apps that you have installed on your device. At the moment, there is nothing normal for full substitution, only within the browser. But this is not a problem, most of the services can be used in web mode.
Data Encryption
I must say right away that we are unlikely to be able to fully encrypt the device, but it is easy to create cryptographic containers! We can store information in cryptographic containers that only we can access. Using the EDS application, we can set the following encryption formats: TrueCrypt, VeraCrypt, LUKS, EncFs. My advice: choose between Vera/True. We can put a browser, Orbot, and anything else we want in it. To get started, you need to download the. apk from the app store. After opening, click on the plus sign and create a new container. From the settings: size 6GB. Algorithm: SHA-512. I advise you not to touch everything else (except for the encryption format, of course). Enter a strong password, ideally 16 characters. This completes the setup process, which is simple and reliable.
In practice, everything is easy, everyone will understand.
Disabling access to the microphone and camera
Expand the notification curtain completely and click on the button shown in the screenshot below. We will open a set with "Quick use", which contains the "Camera access" and "Microphone Access" buttons, which were not activated at first. Drag them to the Quick Access toolbar and use them for their intended purpose. I did tests, it's really safe. Even if you try to make a call using the built-in dialer, the microphone will not work until you turn it on. Useful thing, enabled 24/7.
Summing up the results of the work
Let's see what all our work has led to: not a single byte goes to the network without your consent, your traffic is completely covered by the TOR connection.
No one can access the microphone / camera until you change the setting.
Our phone does not listen to Google and we managed to replace it with dignity. The browser has a dynamic fingerprint that will be extremely difficult to link to you. All web traffic passes through a proxy. Battery consumption has decreased by a factor of 2, for sure. Our phone now has an automatic call recording function. We optimized performance and increased memory by removing system garbage. We have full access to the phone and are ready for my next article with hackerphone, where we will turn our device into a powerful tool.
